


|
||
|
||
As if we didn’t have a long enough list of problems to worry about, Lumen researchers at its Black Lotus Labs recently released a blog that said that it knows of three U.S. ISPs and one in India was hacked this summer. Lumen said the hackers took advantage of flaws in software provided by Versa Networks being used to manage wide-area networks.
The hacks were described as zero-day hacks, which describe a software or hardware vulnerability that is unknown to the vendor and for which no patch or other fix is immediately available—a vendor has zero days to prepare a patch when a vulnerability is exploited. While developers have a goal of delivering products with no vulnerability, virtually all software and hardware contain bugs of some sort.
Lumen said it is moderately confident that the attacks originated from a group known as Volt Typhoon, a Chinese state-sponsored set of hackers. This is the group that U.S. intelligence officials said had been trying to penetrate and hack American ports. Lumen describes the attacks as highly significant.
CISA (the Cybersecurity & Infrastructure Security Agency) leads the effort to protect the country against malicious hackers. The agency’s mission is to “lead the national effort to understand, manage, and reduce risk to our cyber and physical infrastructure.”
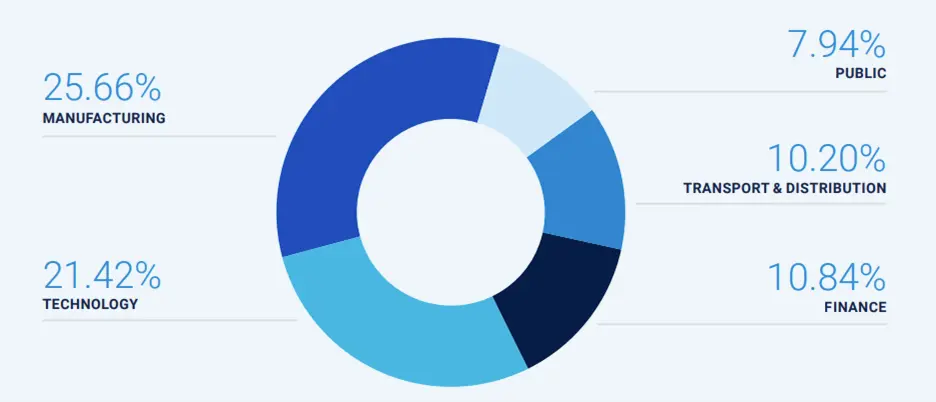
Unfortunately, the U.S. is in the bullseye for ransomware attacks. The following chart, which comes from NTT Data shows the industries that are the targets of hacking in 2024. Manufacturing has overtaken the technology sector as the most attacked, while the financial sector has climbed to third.
Hackers constantly change tactics to stay ahead of the effort to block them. In 2024, there was a decline in banking trojans, which was offset by a rise in info-stealers and penetration-testing tools.
The big concern in the security industry is that hackers are starting to deploy AI to aid in hacks. AI is particularly useful in finding vulnerable code that is buried in lengthy software programs. AI is likely going to be used as a tool to develop a custom approach to hack any given entity.
I know it sounds like old and trite advice, but ISPs need to adopt robust cybersecurity systems to try to keep most hackers out of your network and software.
Sponsored byWhoisXML API

Sponsored byRadix

Sponsored byCSC

Sponsored byVerisign

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byIPv4.Global
