

Cybersecurity |
Sponsored by |

|
 A six year study of Global 2000 firms finds progress on email authentication but worrying gaps elsewhere. Despite rising DMARC adoption, falling DNS redundancy and uneven regional uptake leave companies exposed to domain based attacks.
A six year study of Global 2000 firms finds progress on email authentication but worrying gaps elsewhere. Despite rising DMARC adoption, falling DNS redundancy and uneven regional uptake leave companies exposed to domain based attacks.
 ICANN invites proposals for its DNSSEC and Security Workshop at the ICANN85 Community Forum in March 2026, offering a platform for global experts to share insights on DNS, routing security, and emerging threats.
ICANN invites proposals for its DNSSEC and Security Workshop at the ICANN85 Community Forum in March 2026, offering a platform for global experts to share insights on DNS, routing security, and emerging threats.
 A 2026 outlook charts Internet governance between fear and hope, tracking cyber conflict, digital trade and taxation, shrinking rights, and global AI rivalry, while asking whether multistakeholder cooperation can still steer the network toward stability.
A 2026 outlook charts Internet governance between fear and hope, tracking cyber conflict, digital trade and taxation, shrinking rights, and global AI rivalry, while asking whether multistakeholder cooperation can still steer the network toward stability.
 Internet governance is shifting from participatory forums to security-driven mandates. As authority accelerates ahead of legitimacy, technical systems face growing instability and operators absorb the risks of politically motivated control.
Internet governance is shifting from participatory forums to security-driven mandates. As authority accelerates ahead of legitimacy, technical systems face growing instability and operators absorb the risks of politically motivated control.
 As Internet governance fragments in 2026, authority shifts from open, multistakeholder forums to state-led security regimes, legal instruments, and alliance-based cooperation, challenging longstanding institutions and reshaping global norms through enforcement rather than consensus.
As Internet governance fragments in 2026, authority shifts from open, multistakeholder forums to state-led security regimes, legal instruments, and alliance-based cooperation, challenging longstanding institutions and reshaping global norms through enforcement rather than consensus.
 Despite deep geopolitical divides, the WSIS+20 outcome document was adopted by consensus, preserving a multistakeholder vision for the digital future while deferring controversial issues to a time more conducive to progress.
Despite deep geopolitical divides, the WSIS+20 outcome document was adopted by consensus, preserving a multistakeholder vision for the digital future while deferring controversial issues to a time more conducive to progress.
 The ICC's new cyber policy reframes Internet infrastructure as crucial to prosecuting atrocities, prompting DNS operators and network providers to grapple with emerging obligations around evidence, neutrality, and cooperation in international justice.
The ICC's new cyber policy reframes Internet infrastructure as crucial to prosecuting atrocities, prompting DNS operators and network providers to grapple with emerging obligations around evidence, neutrality, and cooperation in international justice.
 ICANN is finalising a policy to curb DNS abuse, aiming to preserve internet stability while defending freedom of expression. With regulatory pressure mounting, the multistakeholder model faces a critical test.
ICANN is finalising a policy to curb DNS abuse, aiming to preserve internet stability while defending freedom of expression. With regulatory pressure mounting, the multistakeholder model faces a critical test.
 Google's lawsuit against the Lighthouse phishing syndicate exposes the industrial scale of cybercrime, highlighting how criminals exploit easy access to digital infrastructure to scam millions. The broader supply chain enabling such operations demands urgent reform.
Google's lawsuit against the Lighthouse phishing syndicate exposes the industrial scale of cybercrime, highlighting how criminals exploit easy access to digital infrastructure to scam millions. The broader supply chain enabling such operations demands urgent reform.
 As artificial intelligence integrates into public infrastructure, it introduces new layers of systemic risk. Policymakers must shift focus from AI's potential to its exposure, applying governance models that reflect these emerging, compound vulnerabilities.
As artificial intelligence integrates into public infrastructure, it introduces new layers of systemic risk. Policymakers must shift focus from AI's potential to its exposure, applying governance models that reflect these emerging, compound vulnerabilities.
 To prepare DNS security for a post-quantum future, Verisign and partners are testing new cryptographic strategies that balance security, performance, and feasibility, especially through the novel Merkle Tree Ladder mode for managing large signatures.
To prepare DNS security for a post-quantum future, Verisign and partners are testing new cryptographic strategies that balance security, performance, and feasibility, especially through the novel Merkle Tree Ladder mode for managing large signatures.
 As AI notetakers become common in virtual meetings, concerns grow over data privacy, potential misuse, and the risks of unknowingly sharing sensitive corporate information with unseen third parties beyond organizational control.
As AI notetakers become common in virtual meetings, concerns grow over data privacy, potential misuse, and the risks of unknowingly sharing sensitive corporate information with unseen third parties beyond organizational control.
 eco's topDNS initiative and AV-Test are publishing monthly reports to help ISPs detect and mitigate DNS abuse by analysing malware, phishing, and PUA trends, creating a long-term data foundation for industry-wide transparency.
eco's topDNS initiative and AV-Test are publishing monthly reports to help ISPs detect and mitigate DNS abuse by analysing malware, phishing, and PUA trends, creating a long-term data foundation for industry-wide transparency.
 As ICANN prepares to expand the domain name space, calls grow for a public-law framework to govern the DNS root, ensuring global equity, transparency, and accountability in managing the Internet's core infrastructure.
As ICANN prepares to expand the domain name space, calls grow for a public-law framework to govern the DNS root, ensuring global equity, transparency, and accountability in managing the Internet's core infrastructure.
 Private DNS data lakes consolidate fragmented logs into a centralised platform, improving visibility, security, and compliance. They enable advanced analytics, strengthen threat detection, and help organisations optimise network performance in increasingly complex IT environments.
Private DNS data lakes consolidate fragmented logs into a centralised platform, improving visibility, security, and compliance. They enable advanced analytics, strengthen threat detection, and help organisations optimise network performance in increasingly complex IT environments.
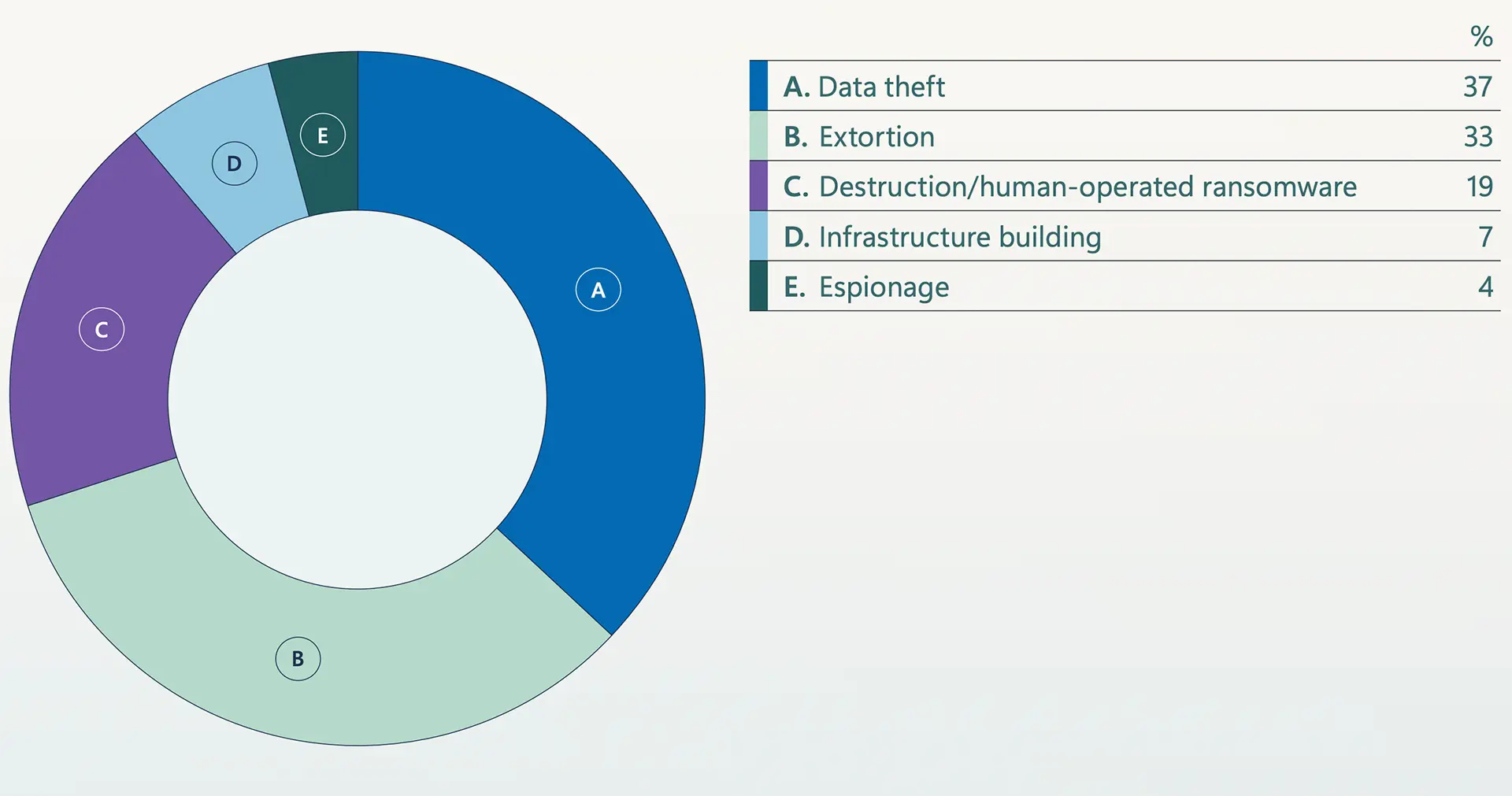 Microsoft Warns Extortion Drives Majority of Attacks Amid AI Escalation, Identity Collapse, and Global Fragmentation
Microsoft Warns Extortion Drives Majority of Attacks Amid AI Escalation, Identity Collapse, and Global Fragmentation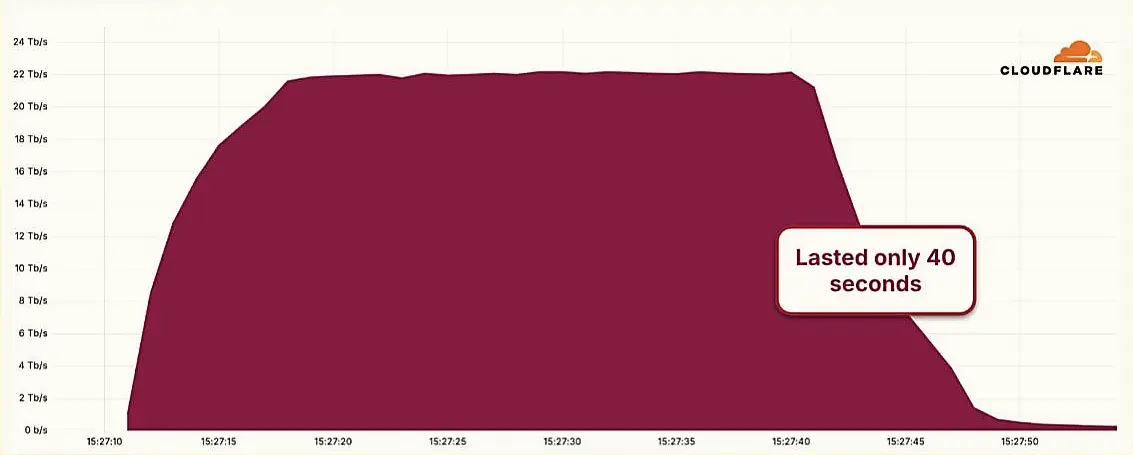 Hyper-Volumetric DDoS Attack Sets New Benchmark at 22.2 Tbps
Hyper-Volumetric DDoS Attack Sets New Benchmark at 22.2 Tbps European Airports Still Reeling from Ransomware Attack as Software Fix Nears
European Airports Still Reeling from Ransomware Attack as Software Fix Nears Chinese APT Groups Exploit Global Domains in Sweeping Cyber Campaign
Chinese APT Groups Exploit Global Domains in Sweeping Cyber Campaign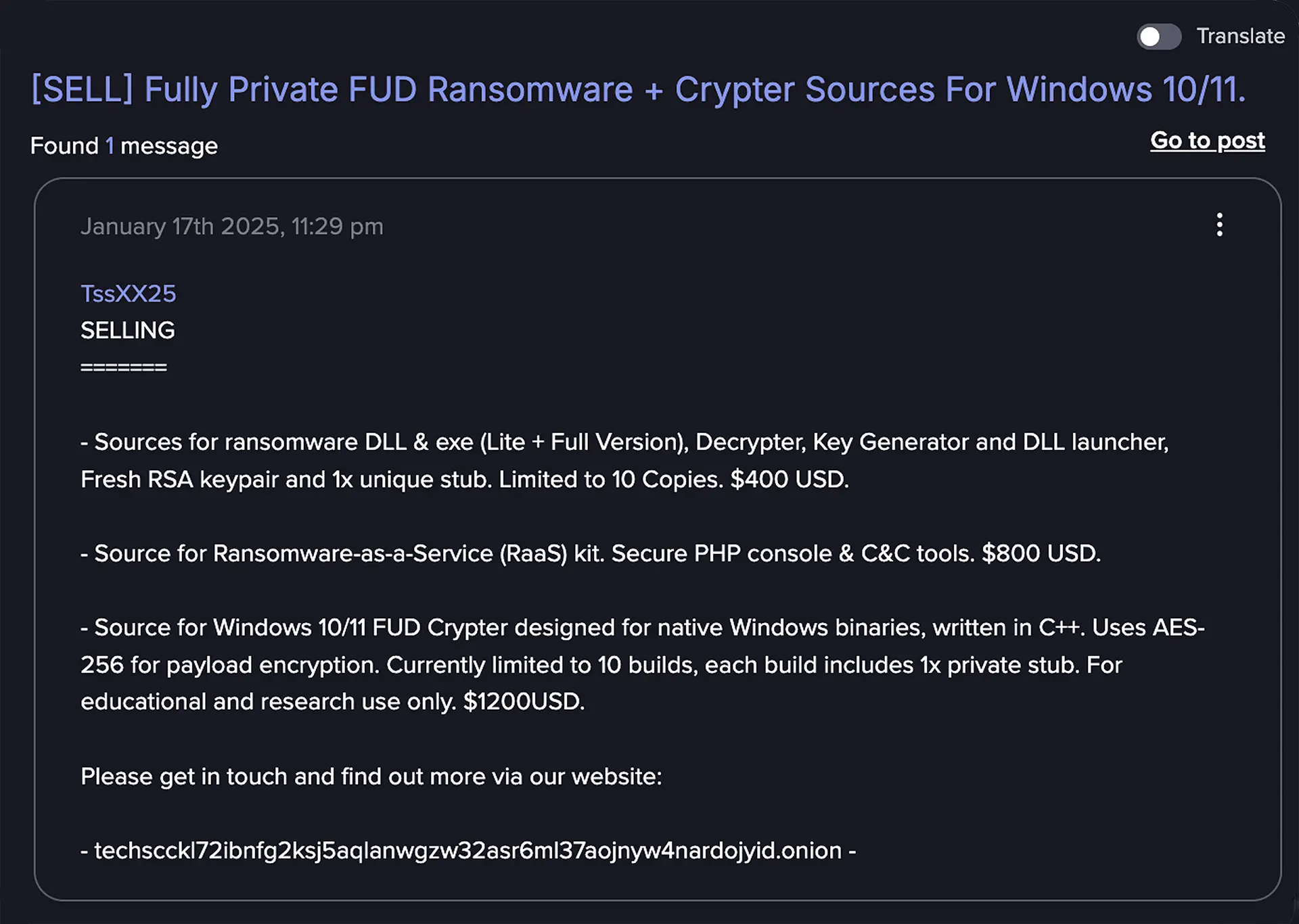 Advanced AI Is Reshaping the Cybercriminal Landscape at Alarming Speed
Advanced AI Is Reshaping the Cybercriminal Landscape at Alarming Speed FTC to Big Tech: Don’t Trade American Privacy for Foreign Demands
FTC to Big Tech: Don’t Trade American Privacy for Foreign Demands INTERPOL Leads Arrest of 1,209 Suspects in Pan-African Cybercrime Crackdown, Recovers $97 Million
INTERPOL Leads Arrest of 1,209 Suspects in Pan-African Cybercrime Crackdown, Recovers $97 Million Massive Iberian Power Outage Raises Cybersecurity Questions
Massive Iberian Power Outage Raises Cybersecurity Questions India Launches ‘.bank.in’ and ‘.fin.in’ Domains to Deter Financial Fraud
India Launches ‘.bank.in’ and ‘.fin.in’ Domains to Deter Financial FraudAddressing DNS abuse and maintaining a healthy DNS ecosystem are important components of Verisign's commitment to being a responsible steward of the internet. We continuously engage with the Internet Corporation for Assigned Names and Numbers (ICANN) and other industry partners to help ensure the secure, stable and resilient operation of the DNS. more
Verisign just released its Q2 2018 DDoS Trends Report, which represents a unique view into the attack trends unfolding online, through observations and insights derived from distributed denial of service (DDoS) attack mitigations enacted on behalf of customers of Verisign DDoS Protection Services. more
Currently scheduled for October 11, 2018, the Internet Corporation for Assigned Names and Numbers (ICANN) plans to change the cryptographic key that helps to secure the internet's Domain Name System (DNS) by performing a Root Zone Domain Name System Security Extensions (DNSSEC) key signing key (KSK) rollover. more
Verisign has released its Q1 2018 DDoS Trends Report, which represents a unique view into the attack trends unfolding online, through observations and insights derived from distributed denial of service (DDoS) attack mitigations enacted on behalf of Verisign DDoS Protection Services, and security research conducted by Verisign Security Services. more
As DNS attacks grow in frequency and impact, organizations can no longer afford to overlook DNS security as part of their overall defense-in-depth strategy. As with IT security in general, no single tactic can address the entire DNS threat landscape or secure the complete DNS ecosystem. more
Verisign has released its Q4 2017 DDoS Trends Report, which represents a unique view into the attack trends unfolding online, through observations and insights derived from distributed denial of service (DDoS) attack mitigations enacted on behalf of Verisign DDoS Protection Services and security research conducted by Verisign Security Services. more
Cybercriminals recognize the value of DNS availability and look for ways to compromise DNS uptime and the DNS servers that support it. As such, DNS becomes an important point of security enforcement and a potential point in the Cyber Kill Chain for many cyber-attacks. more