

 Poland thwarted a large-scale cyberattack on its energy grid without disruption, offering a rare case study in critical infrastructure resilience, decentralised energy governance, and the balancing act between openness and digital security.
Poland thwarted a large-scale cyberattack on its energy grid without disruption, offering a rare case study in critical infrastructure resilience, decentralised energy governance, and the balancing act between openness and digital security.
 eco's topDNS initiative and AV-Test are publishing monthly reports to help ISPs detect and mitigate DNS abuse by analysing malware, phishing, and PUA trends, creating a long-term data foundation for industry-wide transparency.
eco's topDNS initiative and AV-Test are publishing monthly reports to help ISPs detect and mitigate DNS abuse by analysing malware, phishing, and PUA trends, creating a long-term data foundation for industry-wide transparency.
 Cybercriminals live by the tenet "If it ain't broke, don't fix it." They'll use the same tactics repeatedly until they no longer work, then switch things up. That's why CISOs and their security teams maintain constant vigilance. Underscoring this, recent analysis of global DNS activity found that new domains continue to be a major tactic for bad actors.
Cybercriminals live by the tenet "If it ain't broke, don't fix it." They'll use the same tactics repeatedly until they no longer work, then switch things up. That's why CISOs and their security teams maintain constant vigilance. Underscoring this, recent analysis of global DNS activity found that new domains continue to be a major tactic for bad actors.
 Satellites make it possible for governments to provide essential services, such as national defense, navigation, and weather forecasting. Private ventures use satellites to offer highly desired services that include video program distribution, telecommunications, and Internet access. The Russian launch of a satellite, with nuclear power and the likely ability to disable satellites, underscores how satellites are quite vulnerable to both natural and manmade ruin.
Satellites make it possible for governments to provide essential services, such as national defense, navigation, and weather forecasting. Private ventures use satellites to offer highly desired services that include video program distribution, telecommunications, and Internet access. The Russian launch of a satellite, with nuclear power and the likely ability to disable satellites, underscores how satellites are quite vulnerable to both natural and manmade ruin.
 In this article, I present an overview of a series of 'proof-of-concept' studies looking at the application of domain-name entropy as a means of clustering together related domain registrations, and serving as an input into potential metrics to determine the likely level of threat which may be posed by a domain.
In this article, I present an overview of a series of 'proof-of-concept' studies looking at the application of domain-name entropy as a means of clustering together related domain registrations, and serving as an input into potential metrics to determine the likely level of threat which may be posed by a domain.
 OpenXDR is one of the most cost-effective SIEM alternatives that help businesses detect and mitigate threats within hectic modern architectures. A single cyber incident impacts every aspect of a business -- from system downtime, revenue losses, and reputation damage to disrupted operations.
OpenXDR is one of the most cost-effective SIEM alternatives that help businesses detect and mitigate threats within hectic modern architectures. A single cyber incident impacts every aspect of a business -- from system downtime, revenue losses, and reputation damage to disrupted operations.
 While threat actors can use any domain across thousands of top-level domains (TLDs), they often have favorites. For instance, you may be familiar with Spamhaus's 10 most-abused TLDs for spamming. WhoisXML API researchers recently built on this list by analyzing 40,000 newly registered domains (NRDs) that sported some of the listed unreputable TLDs. We called this study "DNS Abuse Trends: Dissecting the Domains Under the Most-Abused TLDs."
While threat actors can use any domain across thousands of top-level domains (TLDs), they often have favorites. For instance, you may be familiar with Spamhaus's 10 most-abused TLDs for spamming. WhoisXML API researchers recently built on this list by analyzing 40,000 newly registered domains (NRDs) that sported some of the listed unreputable TLDs. We called this study "DNS Abuse Trends: Dissecting the Domains Under the Most-Abused TLDs."
 Subdomains help organizations sort different sections of their websites neatly. Looking at the subdomains of some websites, for example, we usually see subdomains like shop[.]domain[.]com and blog[.]domain[.]com, which help users navigate the sites efficiently. But we couldn't help but notice subdomains that might be revealing a lot about a company's Internet infrastructure and resources.
Subdomains help organizations sort different sections of their websites neatly. Looking at the subdomains of some websites, for example, we usually see subdomains like shop[.]domain[.]com and blog[.]domain[.]com, which help users navigate the sites efficiently. But we couldn't help but notice subdomains that might be revealing a lot about a company's Internet infrastructure and resources.
 Cyber attackers are very skilled at infiltration. They'd find ways into a house through cracks and holes that the homeowner doesn't know about. Analogically speaking, that's what the new cyber attack group dubbed "Hafnium" did when they identified several zero-day Microsoft Exchange vulnerabilities to get into target networks. With thousands of users for every Microsoft Exchange server, the attack has far-reaching implications. First, it establishes the presence of a new threat actor group in town. What else could they be up to?
Cyber attackers are very skilled at infiltration. They'd find ways into a house through cracks and holes that the homeowner doesn't know about. Analogically speaking, that's what the new cyber attack group dubbed "Hafnium" did when they identified several zero-day Microsoft Exchange vulnerabilities to get into target networks. With thousands of users for every Microsoft Exchange server, the attack has far-reaching implications. First, it establishes the presence of a new threat actor group in town. What else could they be up to?
 A recent survey conducted by the Neustar International Security Council confirmed the heightened interests on domain name system (DNS) security. The survey reveals that over three-quarters of cybersecurity professionals anticipate increases in DNS attacks, especially with more people shopping online amid the pandemic. Yet, close to 30% have reservations about their ability to respond to these attacks.
A recent survey conducted by the Neustar International Security Council confirmed the heightened interests on domain name system (DNS) security. The survey reveals that over three-quarters of cybersecurity professionals anticipate increases in DNS attacks, especially with more people shopping online amid the pandemic. Yet, close to 30% have reservations about their ability to respond to these attacks.
 When a brand goes so far as to ask a domain name registrar for Whois (the registration contact details) of a potentially abusive domain name, there's likely a lot at stake. Most often, the request is prompted by consumer safety concerns, such as the risk to consumers posed by a malicious site. Other times, the demand has a simple goal: to have a dialog with the registrant about the use of trademarks or other intellectual property in order to avoid extreme action.
When a brand goes so far as to ask a domain name registrar for Whois (the registration contact details) of a potentially abusive domain name, there's likely a lot at stake. Most often, the request is prompted by consumer safety concerns, such as the risk to consumers posed by a malicious site. Other times, the demand has a simple goal: to have a dialog with the registrant about the use of trademarks or other intellectual property in order to avoid extreme action.
 Over the last few years, it's become clear that abuse of the Domain Name System -- whether in the form of malware, botnets, phishing, pharming, or spam -- threatens to undermine trust in the Internet. At Public Interest Registry, we believe that every new .ORG makes the world a better place. That means anything that gets in the way of that is a threat, and that includes DNS Abuse.
Over the last few years, it's become clear that abuse of the Domain Name System -- whether in the form of malware, botnets, phishing, pharming, or spam -- threatens to undermine trust in the Internet. At Public Interest Registry, we believe that every new .ORG makes the world a better place. That means anything that gets in the way of that is a threat, and that includes DNS Abuse.
 Cybercriminals are increasingly targeting Personally Identifiable Information (PII). The reason being "data is the new gold" in this digital world, and the more sensitive some data is, the more value it has. There is no more sensitive data than personally identifiable information because it contains enough information to identify you digitally. Examples of personally identifiable information include name, email, contact number, address, social security number, tax file number, banking or financial information, and more such data that helps identify you.
Cybercriminals are increasingly targeting Personally Identifiable Information (PII). The reason being "data is the new gold" in this digital world, and the more sensitive some data is, the more value it has. There is no more sensitive data than personally identifiable information because it contains enough information to identify you digitally. Examples of personally identifiable information include name, email, contact number, address, social security number, tax file number, banking or financial information, and more such data that helps identify you.
 As the world becomes more and more reliant on electronics, it's worth a periodic reminder that a large solar flare could knock out much of the electronics on earth. Such an event would be devastating to the Internet, satellite broadband, and the many electronics we use in daily life. A solar flare is the result of periodic ejections of matter from the sun into space. Scientists still aren't entirely sure what causes solar flares, but they know that it's somehow related to shifts in the sun's magnetic field.
As the world becomes more and more reliant on electronics, it's worth a periodic reminder that a large solar flare could knock out much of the electronics on earth. Such an event would be devastating to the Internet, satellite broadband, and the many electronics we use in daily life. A solar flare is the result of periodic ejections of matter from the sun into space. Scientists still aren't entirely sure what causes solar flares, but they know that it's somehow related to shifts in the sun's magnetic field.
 Clarivate has once again surveyed global business leaders about the importance of domain names to their organizations, including the role of domains as intellectual property (IP) assets. The 2020 survey followed up on our 2019 survey, revealing key year-over-year trends in how organizations manage, secure and budget for domain names. In this blog, we review key trends from the new report.
Clarivate has once again surveyed global business leaders about the importance of domain names to their organizations, including the role of domains as intellectual property (IP) assets. The 2020 survey followed up on our 2019 survey, revealing key year-over-year trends in how organizations manage, secure and budget for domain names. In this blog, we review key trends from the new report.
 Backlash Over Potential Firing of U.S. Election Cybersecurity’s Top Official
Backlash Over Potential Firing of U.S. Election Cybersecurity’s Top Official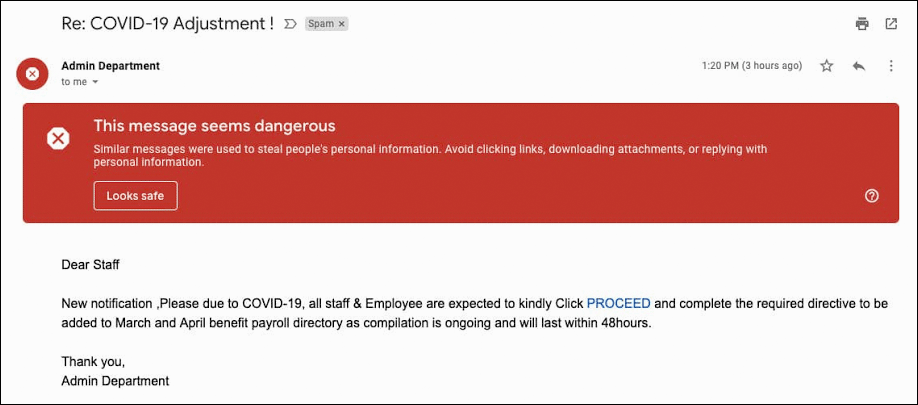 Google Reports 18 Million Daily COVID-19 Related Malware, Phishing Emails Per Day
Google Reports 18 Million Daily COVID-19 Related Malware, Phishing Emails Per Day Zoom Faces Class-Action Lawsuit, Accused of Overstating Its Privacy Standards
Zoom Faces Class-Action Lawsuit, Accused of Overstating Its Privacy Standards