


|
||
|
||
Trend Micro researchers recently uncovered a search engine optimization (SEO) manipulation campaign targeting users of Internet Information Services (IIS) with BadIIS. According to the researchers, the campaign is likely financially motivated since victims were redirected to illegal gambling websites. This campaign has already affected Asian countries like India, Thailand, and Vietnam although its impact can readily extend worldwide.
The in-depth investigation on BadIIS unveiled 51 indicators of compromise (IoCs) comprising 46 domains and five IP addresses. The WhoisXML API research team expanded the current list of IoCs and uncovered additional connected artifacts, including:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our analysis by looking more closely at the 51 BadIIS IoCs.
First, we queried the 46 domains identified as IoCs on Bulk WHOIS API and found that only 38 of them had current WHOIS records. Further scrutiny of these records showed that:
They were split among 11 registrars led by Gname.com, which accounted for 14 domains. GoDaddy took the second spot with nine domains. Dynadot came in third place with four domains. Namecheap accounted for three domains, followed by Metaregistrar had two. Finally, Alibaba Cloud Computing, eNom, MAFF, Realtime Register, 成都垦派科技有限公司, and 阿里巴巴云计算(北京)有限公司 accounted for one domain each.

Only 11 of the 38 domains with current WHOIS records had registrant country information. They were registered in four different countries led by the U.S., which accounted for five domains. China took the second spot with three domains. Iceland placed third with two domains. Finally, Vietnam accounted for one domain.

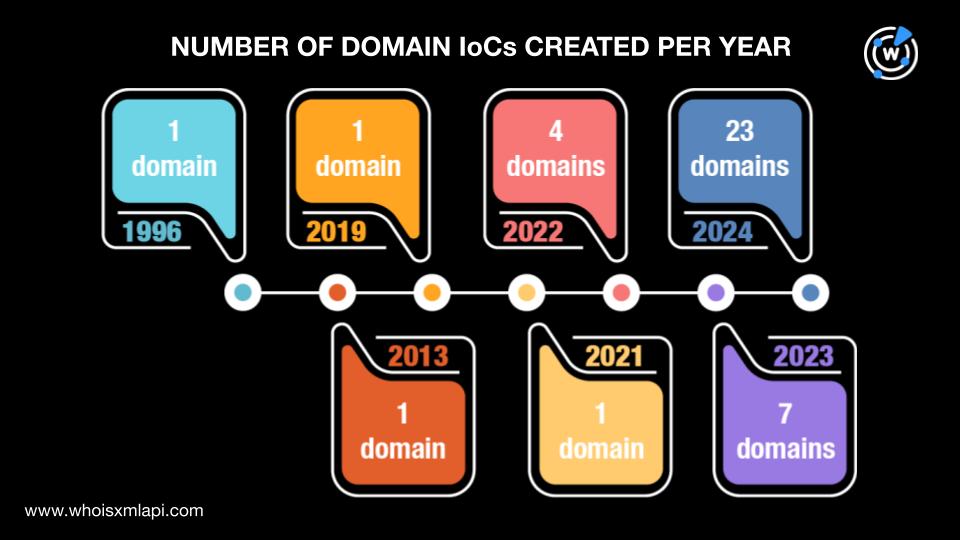
Next, a DNS Chronicle API query for the 46 domains tagged as IoCs revealed that only 38 of them had historical IP resolutions. In particular, the 38 domains recorded a total of 2,111 IP resolutions over time. The domain xxxx[.]com’s first recorded IP resolution occurred on 4 October 2019. The following table shows details about the DNS histories of five other domains.
| DOMAIN IoC | NUMBER OF IP RESOLUTIONS | FIRST IP RESOLUTION DATE |
|---|---|---|
| 668823[.]com | 9 | 17 September 2021 |
| brcknkblue[.]com | 12 | 2 July 2024 |
| dk8[.]land | 77 | 14 January 2022 |
| jumpiis8[.]com | 12 | 16 January 2024 |
| ruicaisiwang[.]com | 35 | 10 October 2019 |
We then looked further into the five IP addresses classified as IoCs beginning with a Bulk IP Geolocation Lookup query, which showed that:

Only four of the five IP addresses had ISP information. They were spread across three ISPs led by Cogent Communications, which administered two IP addresses. MultaCOM and XNNET managed one IP address each.

A DNS Chronicle API query for the five IP addresses identified as IoCs revealed that they all had domain resolutions. Specifically, they posted a total of 512 domain resolutions as of this writing. The IP address 156[.]229[.]134[.]13, for instance, posted the oldest domain resolution date—22 April 2020.
We began our hunt for more connected artifacts with a WHOIS History API query for the 46 domains tagged as IoCs. As it turns out, only 16 of them had email addresses in their historical WHOIS records. Specifically, the 16 domains had 92 email addresses after duplicates were filtered out. Only 28 of them, however, were public email addresses.
Next, we queried the 28 public email addresses on Reverse WHOIS API in a bid to uncover email-connected domains using current WHOIS records. We did not find any, unfortunately. So, we dug deeper and found that nine of them appeared in the historical WHOIS records of 738 email-connected domains after duplicates and those already classified as IoCs were filtered out.
A Threat Intelligence API query for the 738 email-connected domains showed two were already dubbed malicious. The domain gfqfoqz[.]cn, for instance, was associated with malware distribution.
We then queried the 46 domains classified as IoCs on DNS Lookup API and found that 25 of them actively resolved to 29 IP addresses after duplicates and those already identified as IoCs were filtered out.
A Threat Intelligence API query for the 29 additional IP addresses showed that 17 have already figured in malicious campaigns.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byRadix

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byDNIB.com

Sponsored byCSC
