

 AT&T’s CEO plays down the threat of satellite cellular, citing bandwidth and coverage limits. Yet growing interest in rural and IoT applications suggests the technology could still claim valuable niches in the wireless market.
AT&T’s CEO plays down the threat of satellite cellular, citing bandwidth and coverage limits. Yet growing interest in rural and IoT applications suggests the technology could still claim valuable niches in the wireless market.
 At the 20th Internet Governance Forum in Lillestrøm, Norway, the UN Internet Governance Forum's dynamic coalition Internet Standards, Security and Safety (IS3C) released its new report on post-quantum policies. This report presents the findings of a collaborative study undertaken by IS3C and the French domain name registry Afnic and examines the critical need for Post-Quantum Cryptography (PQC) to achieve greater security in the ever-expanding global IoT landscape.
At the 20th Internet Governance Forum in Lillestrøm, Norway, the UN Internet Governance Forum's dynamic coalition Internet Standards, Security and Safety (IS3C) released its new report on post-quantum policies. This report presents the findings of a collaborative study undertaken by IS3C and the French domain name registry Afnic and examines the critical need for Post-Quantum Cryptography (PQC) to achieve greater security in the ever-expanding global IoT landscape.
 Sixty years ago, Paul Baran and Sharla Boehm at The RAND Corporation released a seminal paper that would fundamentally reshape the cyber world forever more. Their paper, simply known as Memorandum RM -- 1303, described how specialized computers could be used to route digital communications among a distributed universe of other computers. It set the stage for a flood of endless developments that resulted in the interconnected world of everything, everywhere, all the time.
Sixty years ago, Paul Baran and Sharla Boehm at The RAND Corporation released a seminal paper that would fundamentally reshape the cyber world forever more. Their paper, simply known as Memorandum RM -- 1303, described how specialized computers could be used to route digital communications among a distributed universe of other computers. It set the stage for a flood of endless developments that resulted in the interconnected world of everything, everywhere, all the time.
 IoT devices have ingrained themselves into almost every aspect of modern life. From home assistants to industrial machinery, it's hard to find a device that isn't connected to a network and gathering data. Despite widespread adoption, IoT cybersecurity compliance remains surprisingly low. A big reason for this is the unique challenges IoT devices pose to operators.
IoT devices have ingrained themselves into almost every aspect of modern life. From home assistants to industrial machinery, it's hard to find a device that isn't connected to a network and gathering data. Despite widespread adoption, IoT cybersecurity compliance remains surprisingly low. A big reason for this is the unique challenges IoT devices pose to operators.
 For four days in Southern France, cybersecurity experts from a broad array of different countries and sectors gathered for the annual ETSI Security Conference. The event undertaken by one of the world's major industry information-communication (ICT) standards organisations was intended to take stock of the state of cybersecurity and trends.
For four days in Southern France, cybersecurity experts from a broad array of different countries and sectors gathered for the annual ETSI Security Conference. The event undertaken by one of the world's major industry information-communication (ICT) standards organisations was intended to take stock of the state of cybersecurity and trends.
 Several weeks ago, the Federal Communications Commission (FCC) embarked on one of the most far-reaching regulatory gambits in its 90-year history. It is formally known as a Notice of Proposed Rulemaking in the matter of Cybersecurity Labeling for Internet of Things, Docket 23 -- 239. The FCC offers ICT product developers the use of its FCC trademarked cyber trust mark placed on their products in exchange for accepting open-ended Commission cybersecurity jurisdiction...
Several weeks ago, the Federal Communications Commission (FCC) embarked on one of the most far-reaching regulatory gambits in its 90-year history. It is formally known as a Notice of Proposed Rulemaking in the matter of Cybersecurity Labeling for Internet of Things, Docket 23 -- 239. The FCC offers ICT product developers the use of its FCC trademarked cyber trust mark placed on their products in exchange for accepting open-ended Commission cybersecurity jurisdiction...
 A significant segment of the IoT ecosystem, the Internet of Medical Things (IoMT), is projected to grow at a compounded annual growth rate of 23.7 percent (forecast period: 2022 -- 2032). This fast growth is indicative of how rapidly IoTM is integrating into modern society, which has understandably attracted the attention of regulators. The widespread use of IoTM devices means that their malfunction or dysfunction can affect the health and lives of many.
A significant segment of the IoT ecosystem, the Internet of Medical Things (IoMT), is projected to grow at a compounded annual growth rate of 23.7 percent (forecast period: 2022 -- 2032). This fast growth is indicative of how rapidly IoTM is integrating into modern society, which has understandably attracted the attention of regulators. The widespread use of IoTM devices means that their malfunction or dysfunction can affect the health and lives of many.
 The Australian Signals Directorate (ASD) has issued a new set of guidelines warning about the security risks posed by the use of 5G technology in so-called Smart Cities. The ASD's concerns align with those of the Five Eyes security alliance, which has warned that the interconnected nature of a fully connected city makes it vulnerable to cyberattacks.
The Australian Signals Directorate (ASD) has issued a new set of guidelines warning about the security risks posed by the use of 5G technology in so-called Smart Cities. The ASD's concerns align with those of the Five Eyes security alliance, which has warned that the interconnected nature of a fully connected city makes it vulnerable to cyberattacks.
 Anybody that uses more than one brand of Internet of Things (IoT) device in the home understands that there is no standard way to connect to these devices. Each manufacturer chooses from a range of different protocols to communicate with and control its devices, such as BLE, LoRa, LTE-M, NB-IoT, SigFox, ZigBee, and others.
Anybody that uses more than one brand of Internet of Things (IoT) device in the home understands that there is no standard way to connect to these devices. Each manufacturer chooses from a range of different protocols to communicate with and control its devices, such as BLE, LoRa, LTE-M, NB-IoT, SigFox, ZigBee, and others.
 In a recent blog post, Amazon invited developers to test drive its gigantic IoT network. This network has been labeled 'Sidewalk' and was created by tying together all of Amazon's wireless devices like Amazon Echos and Ring cameras. Amazon claims this huge wireless network now covers 90% of U.S. households. Amazon created the network by transmitting Bluetooth and 900 MHz LoRa signals from its various devices.
In a recent blog post, Amazon invited developers to test drive its gigantic IoT network. This network has been labeled 'Sidewalk' and was created by tying together all of Amazon's wireless devices like Amazon Echos and Ring cameras. Amazon claims this huge wireless network now covers 90% of U.S. households. Amazon created the network by transmitting Bluetooth and 900 MHz LoRa signals from its various devices.
Last Saturday marked the 53rd anniversary of the Internet. While the vast majority of its five billion users have been online for less than a decade, the Internet was taken into use on October 29th, 1969, when two computers connected to the ARPANET exchanged a message. Although the Internet has been around for a while, it remained below most people's radar until the late 1990s when the dot com boom started.
 OARC held its fall meeting in Belgrade on October 22 and 23. Here are my impressions of some of the presentations from that meeting... UI, UX, and the Registry/Registrar Landscape - One of the major reforms introduced by ICANN in the world of DNS name management was the separation of registry and registrar functions. The intent was to introduce competition into the landscape by allowing multiple registries to enter names into a common registry.
OARC held its fall meeting in Belgrade on October 22 and 23. Here are my impressions of some of the presentations from that meeting... UI, UX, and the Registry/Registrar Landscape - One of the major reforms introduced by ICANN in the world of DNS name management was the separation of registry and registrar functions. The intent was to introduce competition into the landscape by allowing multiple registries to enter names into a common registry.
 The Internet hints at the much larger possibilities of open connectivity in enabling discoveries such as the web but for the physical world. The ideas themselves go to a deeper level of thinking about how we build systems and how we can enable the future. This post is aimed at people building systems and devices which can be interconnected to create systems and meta-devices.
The Internet hints at the much larger possibilities of open connectivity in enabling discoveries such as the web but for the physical world. The ideas themselves go to a deeper level of thinking about how we build systems and how we can enable the future. This post is aimed at people building systems and devices which can be interconnected to create systems and meta-devices.
 It is time to recognize the Internet as a public good - freely available like other basic infrastructures such as roads and sidewalks. In 1989 Tim Berners-Lee created the World Wide Web by taking advantage of open connectivity available among universities and research institutions. Today we see that same open connectivity within corporations, in our homes, and on university campuses.
It is time to recognize the Internet as a public good - freely available like other basic infrastructures such as roads and sidewalks. In 1989 Tim Berners-Lee created the World Wide Web by taking advantage of open connectivity available among universities and research institutions. Today we see that same open connectivity within corporations, in our homes, and on university campuses.
 As the name indicates, the Internet of Things (IoT) should be an extension of the Internet. However, in reality, most IoT applications are Siloed infrastructures. We will analyse the main challenges in the IoT and explain how an Internet registry could be evolved to provide a secure and privacy integrated Identity and access management service for IoT.
As the name indicates, the Internet of Things (IoT) should be an extension of the Internet. However, in reality, most IoT applications are Siloed infrastructures. We will analyse the main challenges in the IoT and explain how an Internet registry could be evolved to provide a secure and privacy integrated Identity and access management service for IoT.
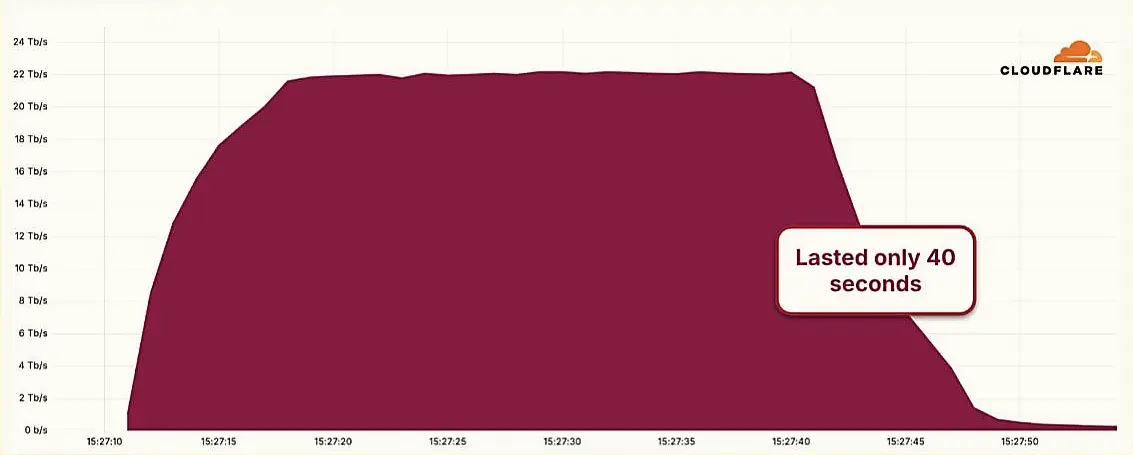 Hyper-Volumetric DDoS Attack Sets New Benchmark at 22.2 Tbps
Hyper-Volumetric DDoS Attack Sets New Benchmark at 22.2 Tbps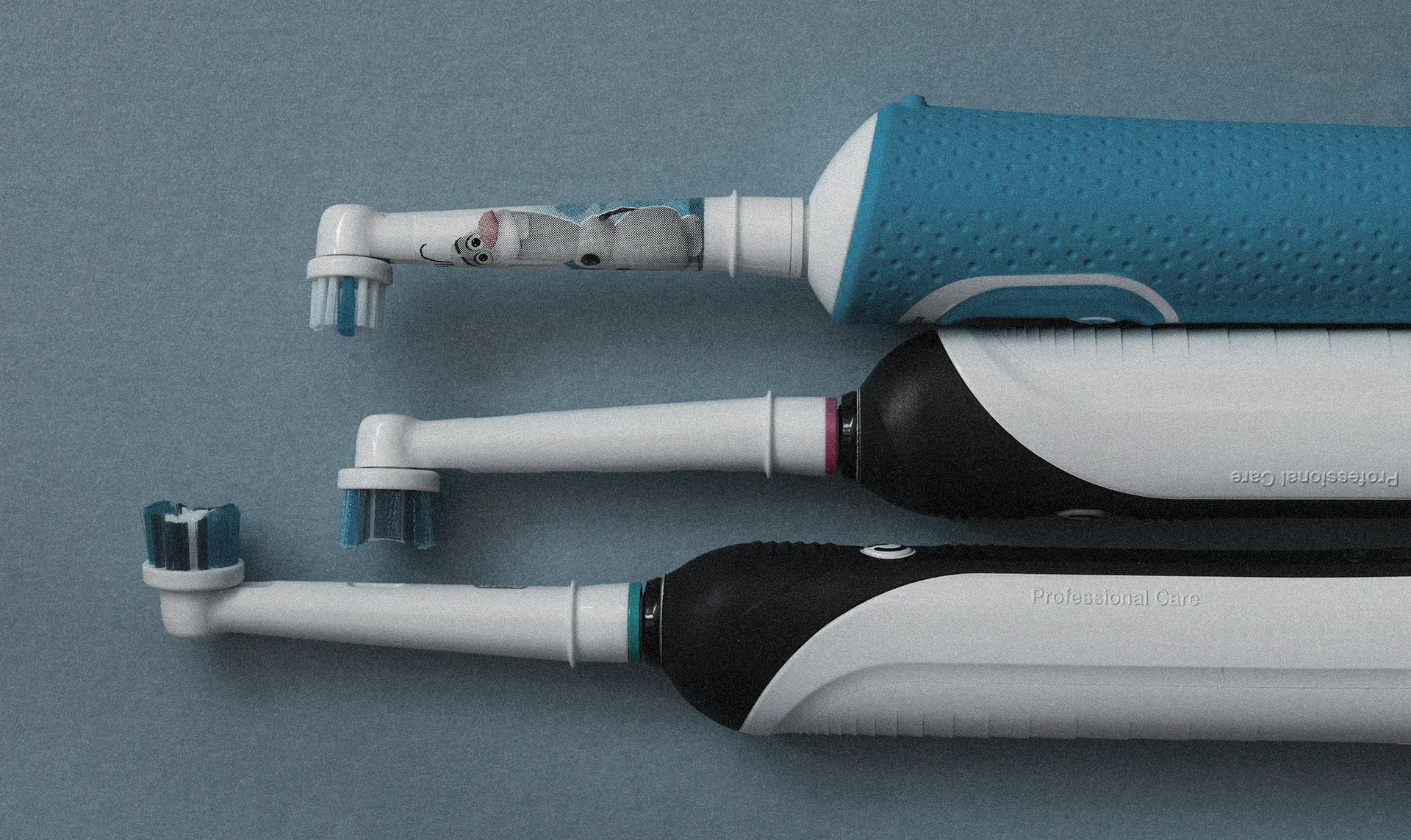 Millions of Smart Toothbrushes Hijacked in Cyberattack on Swiss Firm
Millions of Smart Toothbrushes Hijacked in Cyberattack on Swiss Firm UK Government Planning on New Laws for IoT Devices Including a Mandatory Security Labelling Scheme
UK Government Planning on New Laws for IoT Devices Including a Mandatory Security Labelling Scheme