

 The UnregisteredGems.com series of articles explores a range of techniques to filter and search through the universe of unregistered domain names, in order to find examples which may be compelling candidates for entities looking to select a new brand name (and its associated domain). The previous instalment of the series looked at the categorisation of candidate names according to the phonetic characteristics of its constituent consonants, using a simple one-to-one mapping between each consonant and a corresponding phonetic group.
The UnregisteredGems.com series of articles explores a range of techniques to filter and search through the universe of unregistered domain names, in order to find examples which may be compelling candidates for entities looking to select a new brand name (and its associated domain). The previous instalment of the series looked at the categorisation of candidate names according to the phonetic characteristics of its constituent consonants, using a simple one-to-one mapping between each consonant and a corresponding phonetic group.
 The cybersecurity landscape in 2024 has been characterised by unprecedented complexity and rapidly evolving threats, presenting significant challenges for organisations across all sectors. As the digital attack surface expands and threat actors employ increasingly sophisticated techniques, domain security has emerged as a critical component of a robust cybersecurity strategy.
The cybersecurity landscape in 2024 has been characterised by unprecedented complexity and rapidly evolving threats, presenting significant challenges for organisations across all sectors. As the digital attack surface expands and threat actors employ increasingly sophisticated techniques, domain security has emerged as a critical component of a robust cybersecurity strategy.
 In today's interconnected world, your business's online identity is increasingly more vulnerable than ever. With the rapid advancement of AI and 6G technologies, cyber threats are evolving at an alarming rate, making it critical to protect your brand's digital presence. How can businesses proactively safeguard their online identity in this changing landscape?
In today's interconnected world, your business's online identity is increasingly more vulnerable than ever. With the rapid advancement of AI and 6G technologies, cyber threats are evolving at an alarming rate, making it critical to protect your brand's digital presence. How can businesses proactively safeguard their online identity in this changing landscape?
 The domain name system (DNS) is vital for businesses as it facilitates customer access to online services and resources. Strategic DNS management plays a pivotal role in cybersecurity, safeguarding against threat vectors and ensuring secure global connectivity across online channels including apps, email, websites, application programming interfaces (APIs) and more.
The domain name system (DNS) is vital for businesses as it facilitates customer access to online services and resources. Strategic DNS management plays a pivotal role in cybersecurity, safeguarding against threat vectors and ensuring secure global connectivity across online channels including apps, email, websites, application programming interfaces (APIs) and more.
 Domain name monitoring - that is, the detection of domains with names containing a brand-term (or other string) of interest - is a very well-established element of brand protection services. Branded domain names are of key importance to brand owners (as the basis for business-critical infrastructure (i.e. 'core' domain names), and as part of a 'tactical' portfolio of strategic and defensive registrations), but also to infringers, who can utilise domains as a means of impersonation, passing off, claimed affiliation, or traffic direction and monetisation.
Domain name monitoring - that is, the detection of domains with names containing a brand-term (or other string) of interest - is a very well-established element of brand protection services. Branded domain names are of key importance to brand owners (as the basis for business-critical infrastructure (i.e. 'core' domain names), and as part of a 'tactical' portfolio of strategic and defensive registrations), but also to infringers, who can utilise domains as a means of impersonation, passing off, claimed affiliation, or traffic direction and monetisation.
 I recently appeared on the 419 Consulting podcast to discuss the European Union's NIS 2.0 Directive and its impact on the domain name ecosystem. I encourage all TLD registries, domain name registration service providers, and DNS operators to listen to the recording of that session which Andrew Campling has made available.
I recently appeared on the 419 Consulting podcast to discuss the European Union's NIS 2.0 Directive and its impact on the domain name ecosystem. I encourage all TLD registries, domain name registration service providers, and DNS operators to listen to the recording of that session which Andrew Campling has made available.
 As a member of the ROW Planning Committee, I am writing this post on behalf of the Committee and welcome all community members to join us on June 4th. We are celebrating ROW's 10th anniversary! A decade of collaboration and inspiration! Thank you to the incredible community that has fueled this journey!
As a member of the ROW Planning Committee, I am writing this post on behalf of the Committee and welcome all community members to join us on June 4th. We are celebrating ROW's 10th anniversary! A decade of collaboration and inspiration! Thank you to the incredible community that has fueled this journey!
 The U.S. Anticybersquatting Consumer Protection Act ("ACPA") is a federal law -- part of the Lanham Act that deals with trademarks and unfair competition. It says that a person can be liable if he or she registers a domain name that contains another's distinctive trademark with a bad faith intent to profit from that mark. One issue that has arisen over the years is whether registration that can give rise to liability means only the first time the domain name is registered, or whether it applies to the re-registration...
The U.S. Anticybersquatting Consumer Protection Act ("ACPA") is a federal law -- part of the Lanham Act that deals with trademarks and unfair competition. It says that a person can be liable if he or she registers a domain name that contains another's distinctive trademark with a bad faith intent to profit from that mark. One issue that has arisen over the years is whether registration that can give rise to liability means only the first time the domain name is registered, or whether it applies to the re-registration...
 I recently had the opportunity to speak on a podcast with Dave Bittner at CyberWire to discuss how .AI is giving cybercriminals a new avenue to take advantage of some of the largest companies in the world based on research findings from CSC's 2023 Domain Security Report. Below is a summary of the key points discussed during this podcast.
I recently had the opportunity to speak on a podcast with Dave Bittner at CyberWire to discuss how .AI is giving cybercriminals a new avenue to take advantage of some of the largest companies in the world based on research findings from CSC's 2023 Domain Security Report. Below is a summary of the key points discussed during this podcast.
 In the last year, the company that runs the Turkish Domain Registry has made many changes to how the extension is run. First, it has a brand new portal for registrars to interact with, liberalizing the extension .COM.TR, so registrants are no longer required to meet local presence rules, and it has launched a new dispute process to help brand holders recover domain names.
In the last year, the company that runs the Turkish Domain Registry has made many changes to how the extension is run. First, it has a brand new portal for registrars to interact with, liberalizing the extension .COM.TR, so registrants are no longer required to meet local presence rules, and it has launched a new dispute process to help brand holders recover domain names.
 The Internet Watch Foundation (IWF) leads the charge to combat child sexual abuse material (CSAM) online, and we at Public Interest Registry (PIR) are dedicated to supporting their efforts. We are honored to work with them across two important programs: Domain Alerts and TLD Hopping List. IWF services have been extremely successful in addressing CSAM on .ORG over the past five years
The Internet Watch Foundation (IWF) leads the charge to combat child sexual abuse material (CSAM) online, and we at Public Interest Registry (PIR) are dedicated to supporting their efforts. We are honored to work with them across two important programs: Domain Alerts and TLD Hopping List. IWF services have been extremely successful in addressing CSAM on .ORG over the past five years
 From the creation of DNSAI Compass ("Compass"), we knew that measuring DNS Abuse1 would be difficult and that it would be beneficial to anticipate the challenges we would encounter. With more than a year of published reports, we are sharing insights into one of the obstacles we have faced. One of our core principles is transparency and we've worked hard to provide this with our methodology.
From the creation of DNSAI Compass ("Compass"), we knew that measuring DNS Abuse1 would be difficult and that it would be beneficial to anticipate the challenges we would encounter. With more than a year of published reports, we are sharing insights into one of the obstacles we have faced. One of our core principles is transparency and we've worked hard to provide this with our methodology.
 It seems that every day, a new artificial intelligence (AI) capability emerges, posing exciting possibilities for technological advancements -- but also great potential to equal or greater risks. Cybercriminals have taken notice of this rapid surge in the popularity of AI technologies and are attempting to take advantage.
It seems that every day, a new artificial intelligence (AI) capability emerges, posing exciting possibilities for technological advancements -- but also great potential to equal or greater risks. Cybercriminals have taken notice of this rapid surge in the popularity of AI technologies and are attempting to take advantage.
 Domain names give your intellectual property visibility, as well as provide function for your company's infrastructure. Vital domain names are simply too important to be left exposed. To protect them, you can add extra layers of security to your digital brand with easy, secure, server-level protection in addition to multi-level locks that combat domain name system (DNS) hijacking and protect against unauthorized changes and deletions to your critical domain names.
Domain names give your intellectual property visibility, as well as provide function for your company's infrastructure. Vital domain names are simply too important to be left exposed. To protect them, you can add extra layers of security to your digital brand with easy, secure, server-level protection in addition to multi-level locks that combat domain name system (DNS) hijacking and protect against unauthorized changes and deletions to your critical domain names.
 Companies today manage hundreds or even thousands of domain names that support their organization, their visitors from different countries, and their brands and trademarks. They register misspelling of their names as a defensive strategy to protect their brand from online fraud, or from losing traffic to simple user typos.
Companies today manage hundreds or even thousands of domain names that support their organization, their visitors from different countries, and their brands and trademarks. They register misspelling of their names as a defensive strategy to protect their brand from online fraud, or from losing traffic to simple user typos.
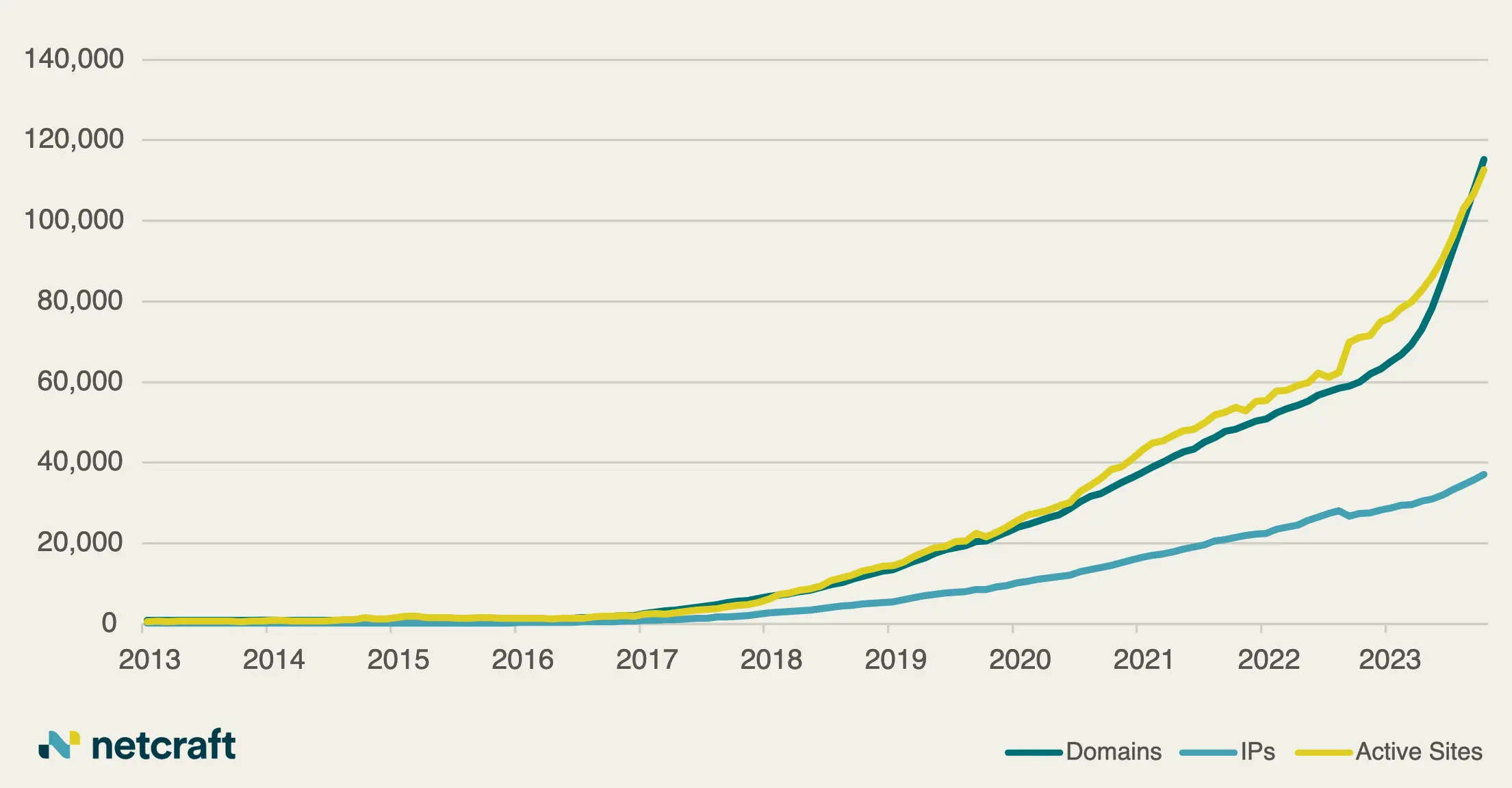 Rise in Cybercrime Exploiting Artificial Intelligence Hype Leads to Growing Threats Within the .ai Domain Space
Rise in Cybercrime Exploiting Artificial Intelligence Hype Leads to Growing Threats Within the .ai Domain Space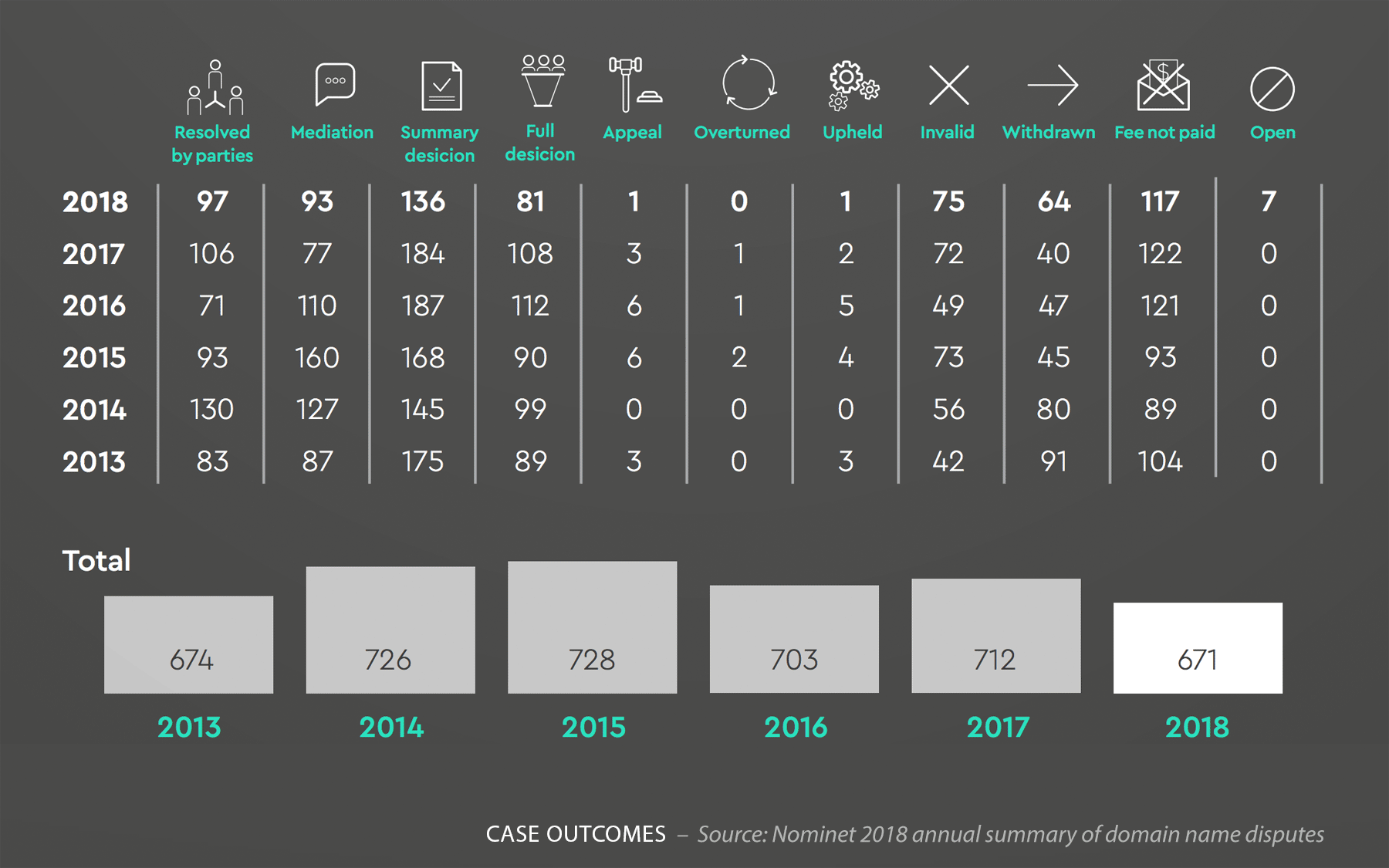 Nominet, the .UK Operator Says Its Domain Dispute Resolution Service Has Saved £180 Million to Date
Nominet, the .UK Operator Says Its Domain Dispute Resolution Service Has Saved £180 Million to Date