


|
||
|
||
The beginning of the month of June, according to CleanINTERNET, marked the emergence of several zero-day attacks targeting vulnerable MOVEit servers to exfiltrate confidential data. MOVEit Transfer is a managed file transfer software that supports file and data exchange. The MOVEit vulnerability gives attackers access to a database and possibly infer information about its structure and content.
Since then, researchers from various security companies published reports tying the MOVEit bug’s exploitation to CLOP ransomware attacks. The WhoisXML API research team obtained a list of 139 indicators of compromise (IoCs) that was then subjected to further analysis using our DNS tools.
Our deep dive into the MOVEit vulnerability-CLOP ransomware IoCs found:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
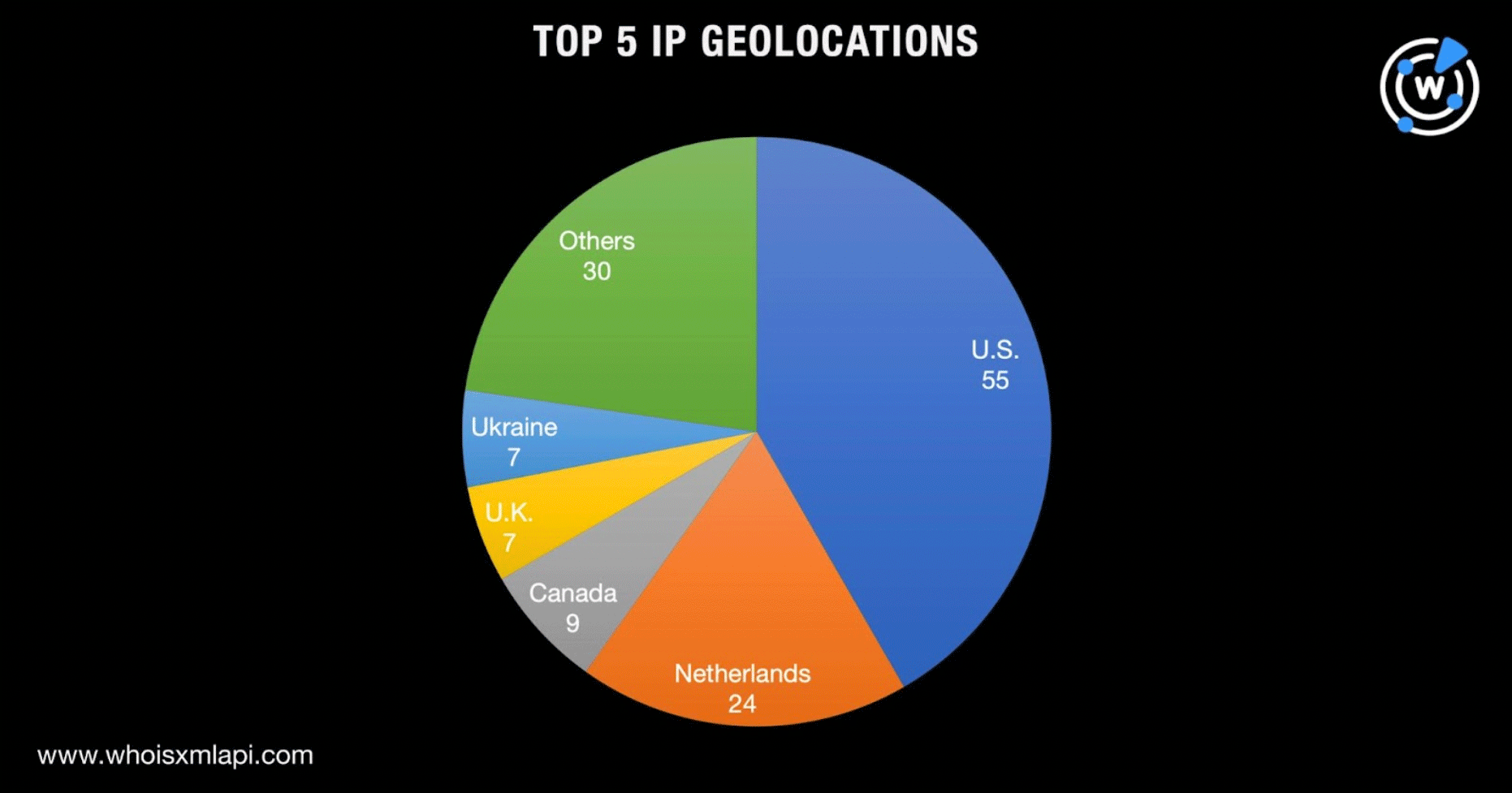
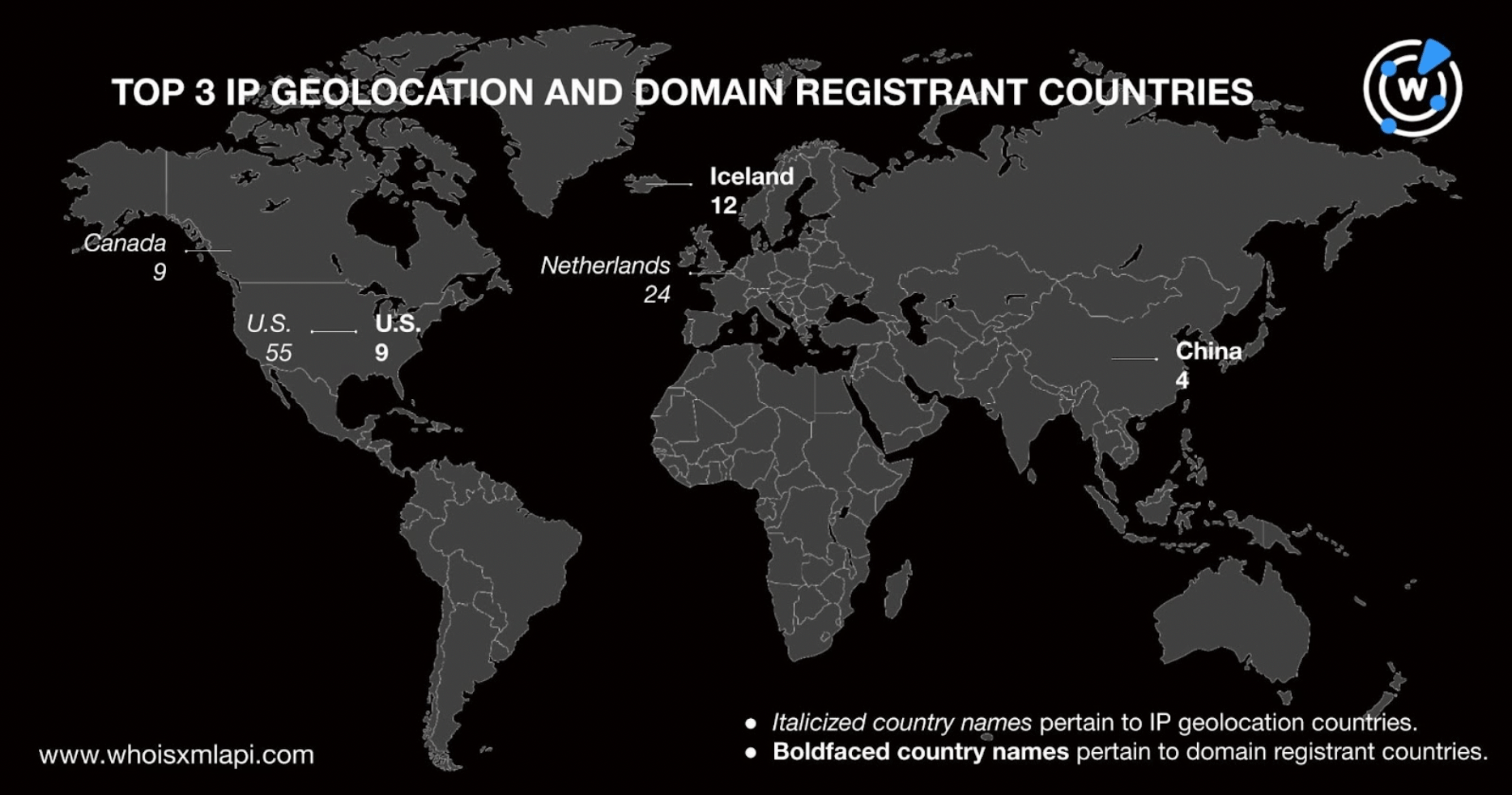
In-depth reports on MOVEit-enabled CLOP ransomware attacks identified 132 IP addresses as IoCs. A bulk IP geolocation lookup for them showed that they were spread across 16 countries led by the U.S., which accounted for 55 of the IP addresses, followed by the Netherlands (24 IP addresses), Canada (nine IP addresses), and the U.K. and Ukraine (seven IP addresses each).
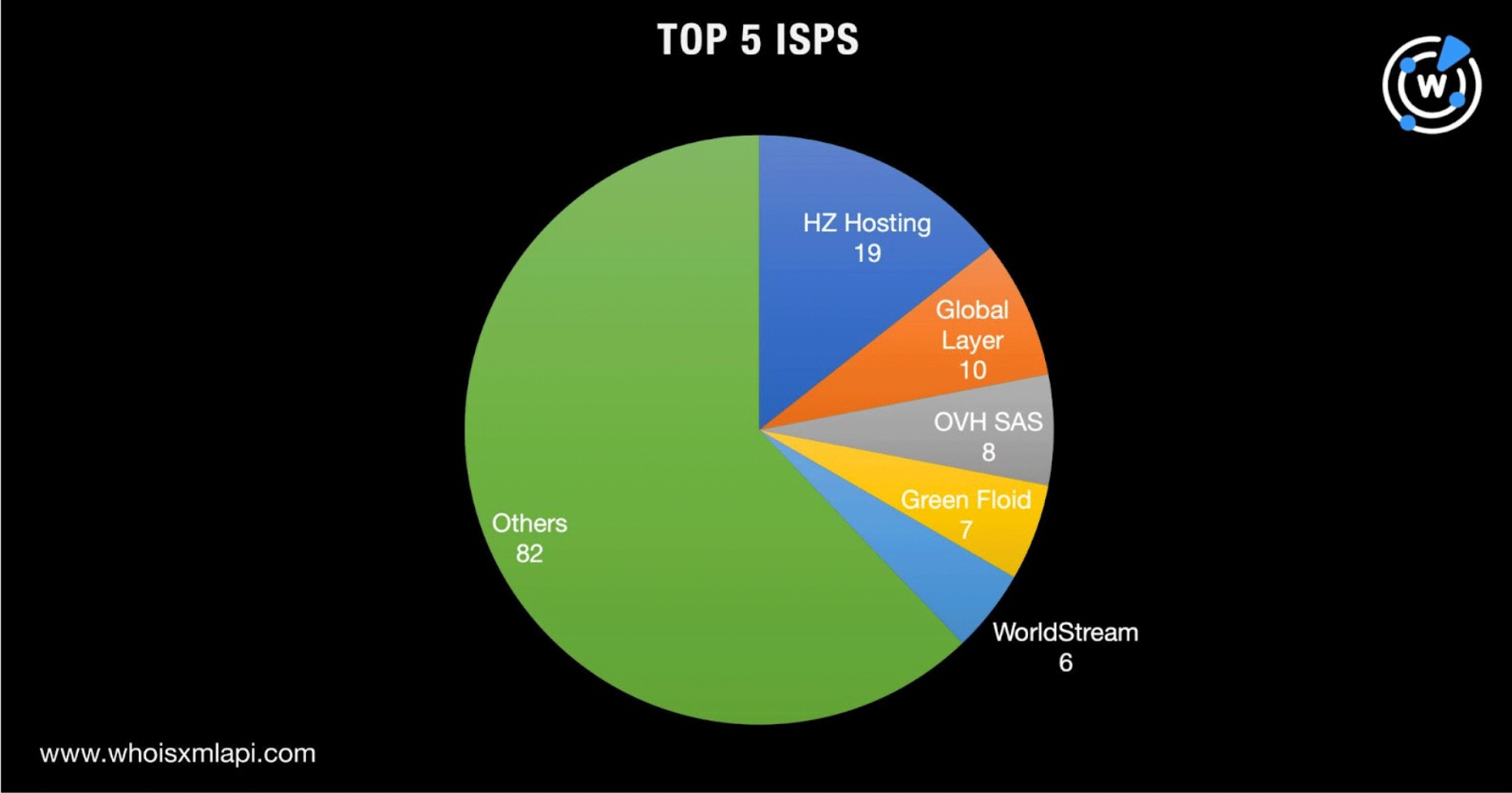
The IoCs were also distributed among 50 ISPs led by HZ Hosting, which accounted for 19 of the IP addresses. Global Layer (10 IP addresses), OVH SAS (eight IP addresses), Green Floid (seven IP addresses), and WorldStream (six IP addresses) rounded out the top 5 ISPs.
Reverse IP lookups performed on the IoCs revealed that 17 of the 132 were dedicated IP addresses. Altogether, they hosted 34 domains, four of which were dubbed as malicious by a bulk malware check tool.
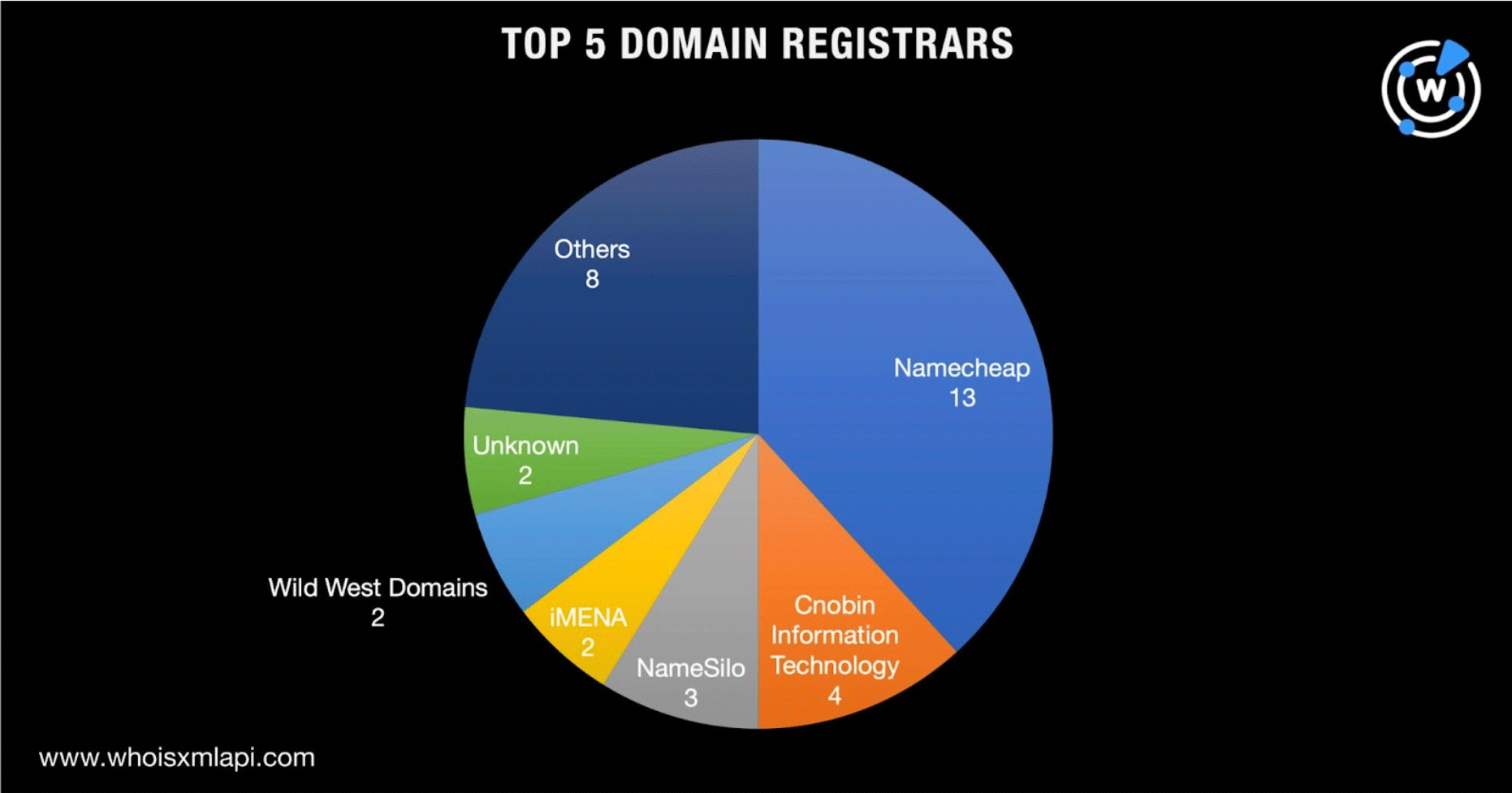
A bulk WHOIS lookup for the IP-connected domains showed that those with publicly available registrar information were spread across 14 registrars led by Namecheap, which accounted for 13 of the artifacts. Cnobin Information Technology (four domains), NameSilo (three domains), and iMENA and Wild West Domains (two domains each) completed the top 5.
One of the artifacts—tube-plant[.]com—had a publicly viewable personal registrant email address that investigators might wish to further pursue.
The artifacts with publicly available registrant countries cited Iceland as the top registrant country. The nation accounted for 12 of the IP-connected domains but didn’t appear as an IP geolocation country.
Earlier reports about MOVEit-enabled CLOP ransomware attacks also identified seven domains as IoCs. Two of them contained the string zoom—connectzoomdownload[.]com and zoom[.]voyage—but their current WHOIS records didn’t bear any similarity with that of zoom[.]com. Apart from not indicating their registrant organization, they were also under NameSilo management unlike zoom[.]com that indicated Zoom Video Communications, Inc. as registrant organization and MarkMonitor, Inc. as registrar.
We looked for other zoom-containing domains created since 1 January 2023 since both IoCs were created in December 2022 to find possibly related artifacts. We found 6,627 such web properties although none of the 6,609 with retrievable WHOIS records could be publicly attributed to Zoom based on the organization their registrants identified.
A bulk malware check for the string-connected domains also revealed that 56 have already been categorized as malware hosts. Of these, only one continued to host live content related to one of the biggest Russian banks and its investment platform. Despite its name, though, it doesn’t seem to have anything to do with the videoconferencing platform or viewing parts of the planet.
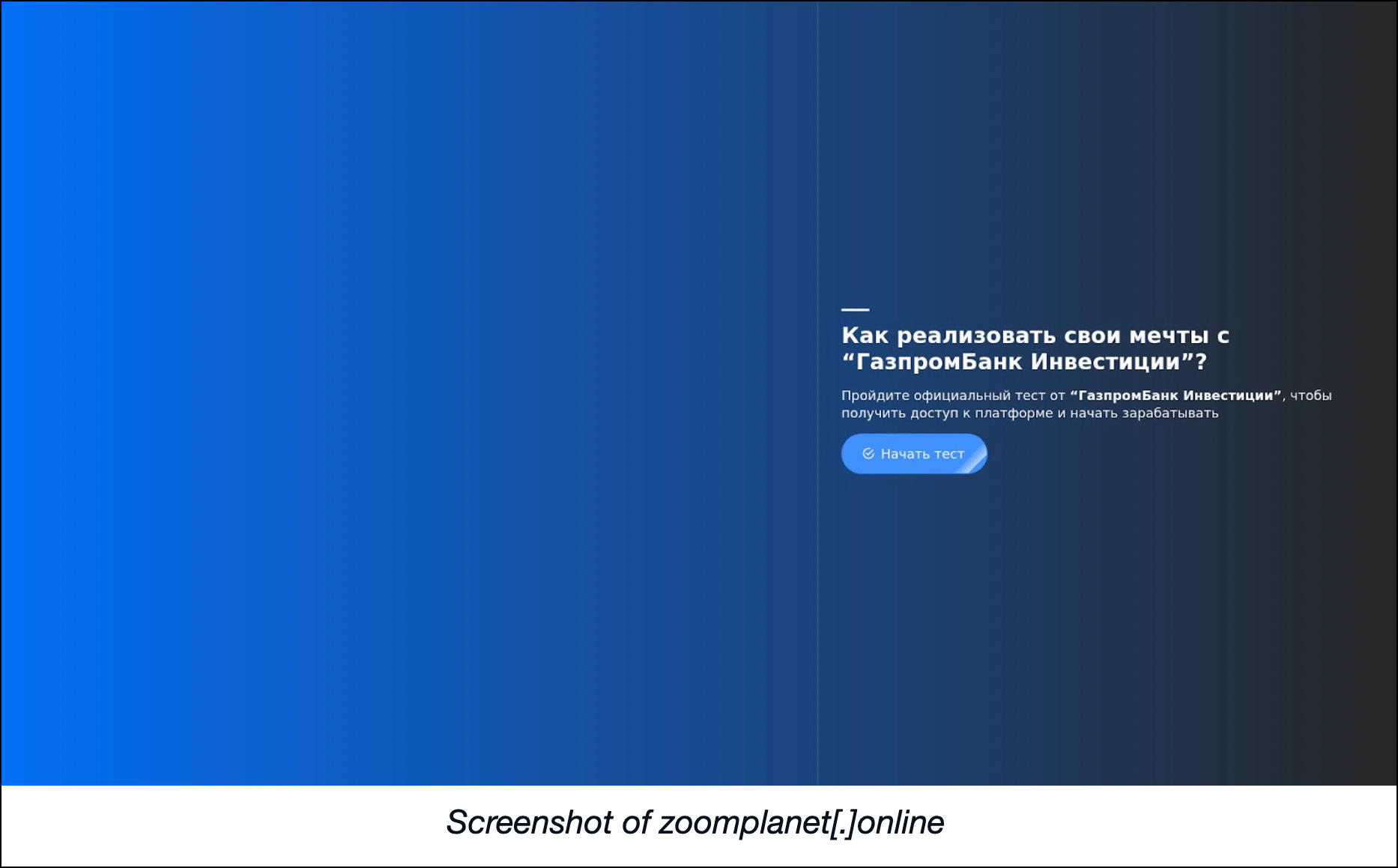
Screenshot of zoomplanet[.]online
The rest of the malicious string-connected domains were either unreachable, for sale, or led to error pages.
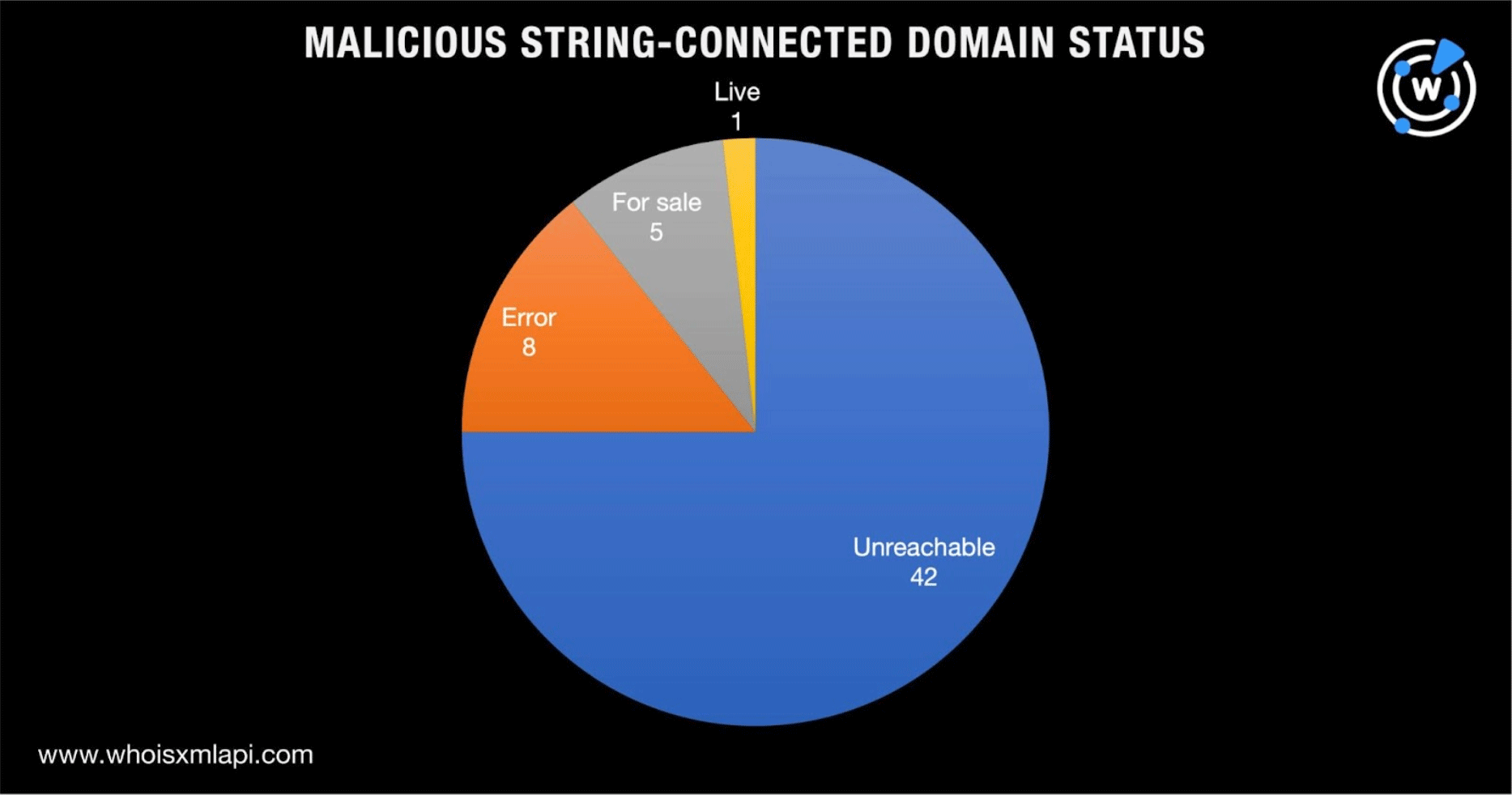
A bulk WHOIS lookup for the IoCs likewise showed that Cnobin Information Technology was their top registrar, accounting for four domains. In addition, six of them were created in 2022 while the remaining one was much older, created in 1996. Finally, four domain registrants indicated China as their country, followed by the U.S. (two domains) and Canada (one domain).
Next, the IoCs resolved to 10 unique IP addresses, four of which were already part of the published IoC lists. Two of the six remaining IP resolutions were dedicated addresses that played host to five domains. Four of them were identified as malicious based on a bulk malware check. While none of them continued to host live content, it’s interesting to note the appearance of the string microsoft in two of them.
WHOIS lookups for the two malicious IP-connected domains—microsoftclouddownload[.]com and mlcrosoft[.]life—showed they weren’t publicly attributable to the company. They were likely used in malicious campaigns targeting Microsoft product users. Note the presence of the string download in one of them as well akin to the domain connectzoomdownload[.]com that was identified as an IoC.
Our foray into the DNS for traces of MOVEit-connected CLOP ransomware attacks led to the discovery of more than 6,600 potentially connected web properties, domains and IP addresses alike.
Our deeper dive also uncovered 65 malicious connected artifacts that organizations can include in their blocklists to enable better cybersecurity.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byRadix

Sponsored byCSC

Sponsored byDNIB.com
