


|
||
|
||
The SideWinder advanced persistent threat (APT) group, also known as “T-APT-04” or “RattleSnake,” has been active since 2012. It launched attacks against military and government entities in Asia.
SecureList analyzed the inner workings of SideWinder in great depth and identified 100 domain names as indicators of compromise (IoCs) as of 15 October 2024. The WhoisXML API research team expanded the IoC list in a bid to uncover other potentially connected artifacts.
Our analysis led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
As per usual, we began our analysis by performing a bulk WHOIS lookup for the 100 domains identified as IoCs. We found out that only 83 had current WHOIS record details. Here is a breakdown of our findings for them.

The domain IoCs were seemingly registered in seven countries topped by the U.S., which accounted for 43 domain IoCs. Iceland came in second place with 21 domains. China took the third spot with seven IoCs. The Netherlands (six), New Zealand (three), Australia (two), and Japan (one) completed the list of registrant countries.

As the first step to expand the list of domain IoCs, we queried them on WHOIS History API. That led to the discovery of 45 email addresses, 15 of which were public.
Querying the 15 public email addresses on Reverse WHOIS API revealed that two could belong to domainers, given the high number of connected domains we found, leaving us with 13 email addresses for further analysis. These 13 public email addresses appeared in the current WHOIS records of six domains after duplicates and the IoCs were filtered out.
Next, we performed DNS lookups for the 83 domain IoCs and found that while 55 did not have active resolutions, 28 resolved to 22 unique IP addresses.
Threat Intelligence API showed that 20 of the 22 IP addresses were associated with various threats. Take a look at five examples below.
| MALICIOUS IP ADDRESS | ASSOCIATED THREAT TYPE |
|---|---|
| 13[.]248[.]252[.]114 | Attack Command and control (C&C) Generic Malware Phishing Suspicious |
| 172[.]67[.]208[.]176 | Malware |
| 23[.]235[.]163[.]147 | Generic Malware |
| 43[.]240[.]239[.]76 | C&C Generic Malware |
| 45[.]86[.]229[.]78 | Malware |
A bulk IP geolocation lookup for the 22 IP addresses revealed that:

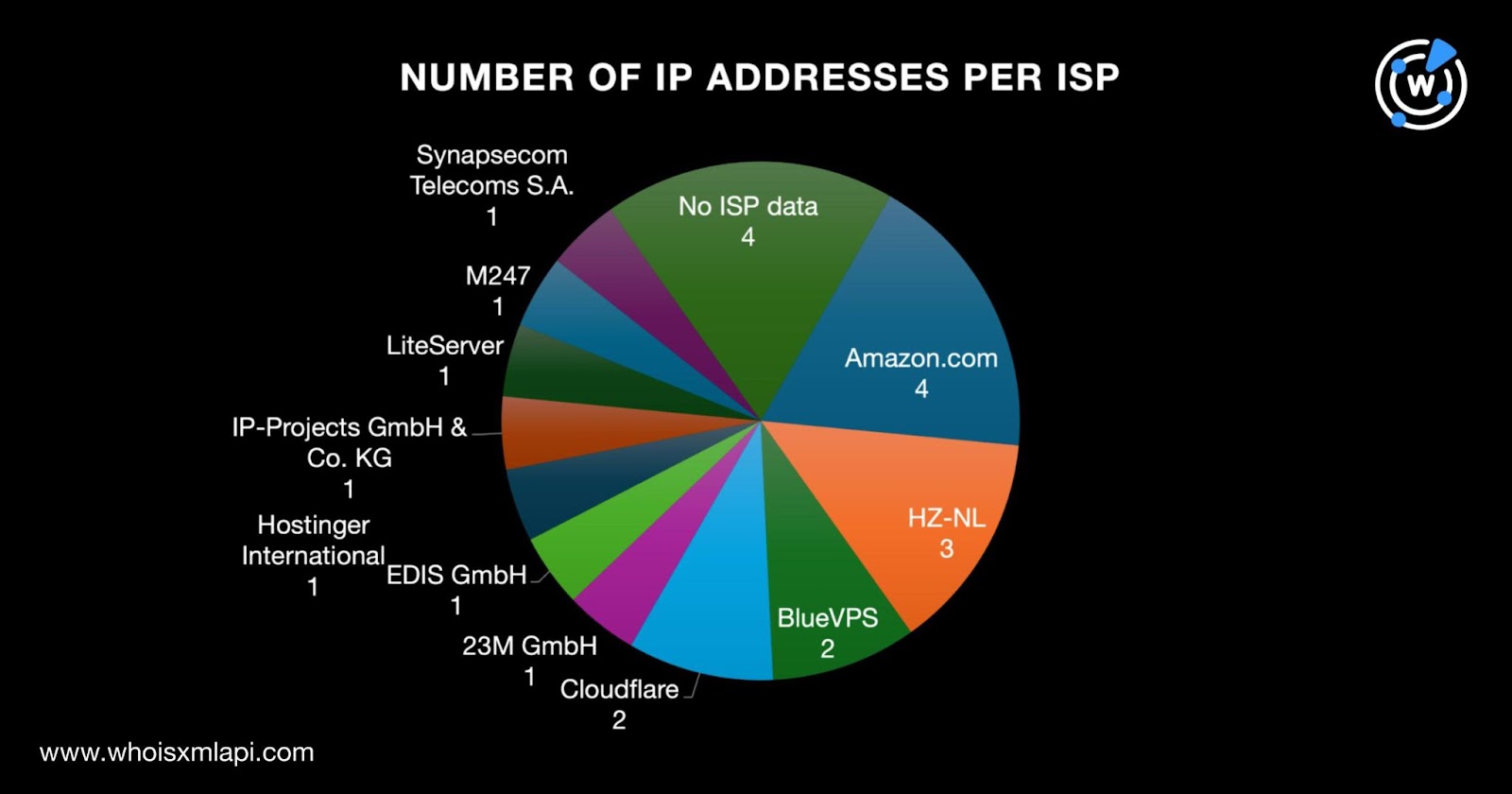
Eighteen of them were administered by 11 ISPs led by Amazon.com, which accounted for four IP addresses. The remaining ISPs were HZ-NL (three); BlueVPS and Cloudflare (two each); 23M GmbH, EDIS GmbH, Hostinger International, IP-Projects GmbH & Co., LiteServer, M247, and Synapsecom Telecoms S.A. (one each). Four IP addresses did not have ISP information.
As the next step, we dove deeper into the historical A records of the domain IoCs using DNS Chronicle Lookup and found that 81 domain IoCs resolved to 563 IP addresses with some overlaps between 4 October 2019 and 31 October 2024.
We looked more closely at one domain IoC in particular—alit[.]live—and found that it resolved to 21 IP addresses from 19 November 2021 to 31 October 2024. It seemingly changed from one IP address to another every seven days from 19 November 2021 to 4 February 2022. Then the number of days varied widely after that.

This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byCSC

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byRadix

Sponsored byIPv4.Global
