


|
||
|
||
Using resumes to fake job applications is not a novel social engineering lure for run-of-the-mill phishing campaigns. But utilizing the same tactic to launch a targeted attack isn’t that common.
The threat actor known as “TA4557,” who has been active since 2018, recently made waves with the lure, however, aided by the backdoor that has been dubbed “more_eggs.” How does it work? In short, the malware is delivered via resumes. The threat actor asks recipients to click a link to the applicant’s personal website, jumpstarting the infection until the final payload—credential theft—is achieved.
The DFIR Report identified 14 domain names and three IP addresses as more_eggs indicators of compromise (IoCs). The WhoisXML API research team expanded this list and uncovered connected artifacts, namely:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
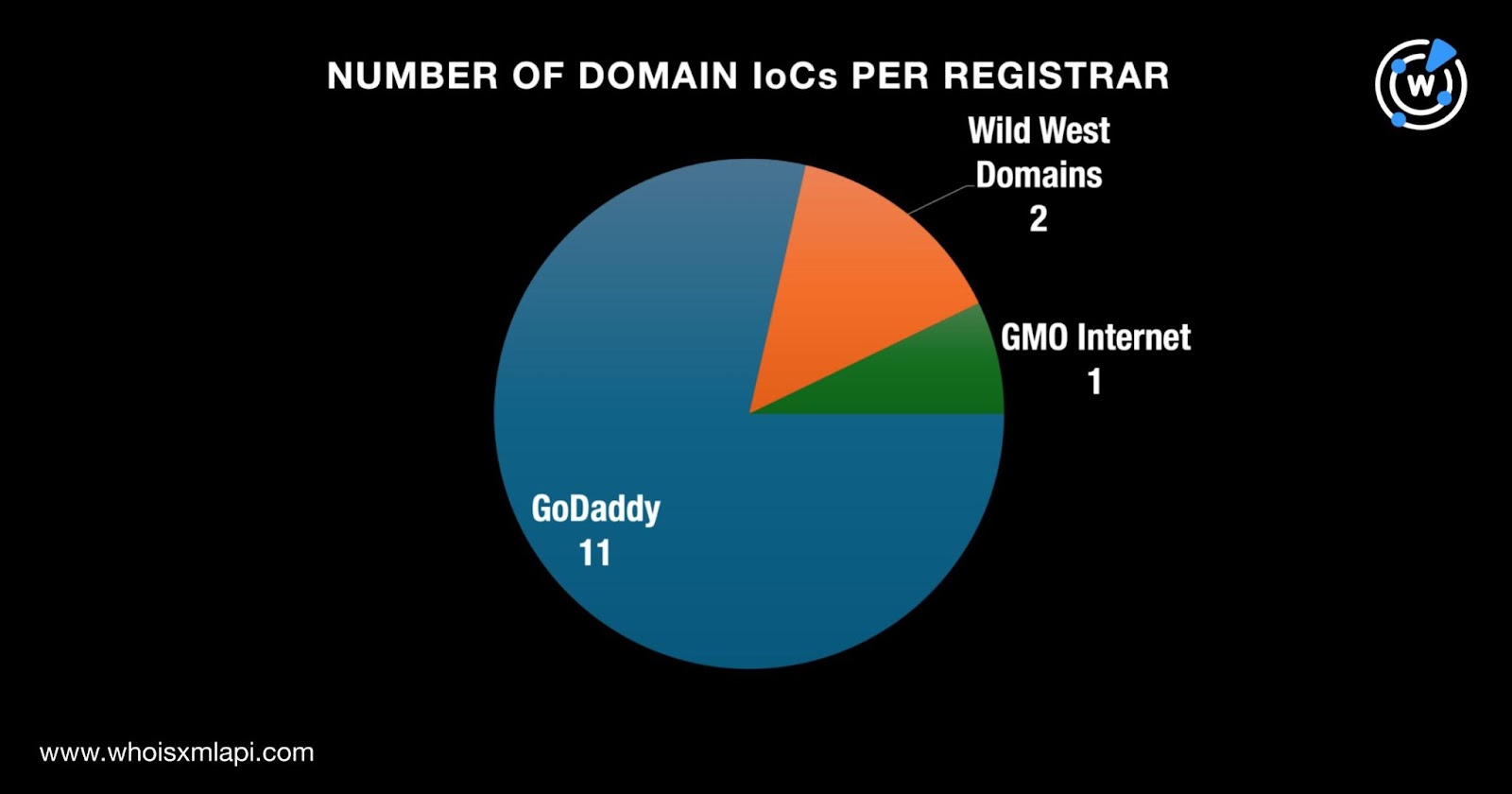
First off, we sought to find more information on the 17 IoCs that have already been identified beginning with a bulk WHOIS lookup for the 14 domains tagged as IoCs. The results revealed that:
They were created between 1997 and 2024, possibly inferring TA4557’s penchant for older domains. Specifically, three domains were created in 2021, while one each was created in 1997, 1999, 2003, 2008, 2010, 2012, 2016, 2018, 2019, 2020, and 2024.

We also queried the 14 domains tagged as IoCs on DNS Chronicle API and found that they have had 871 IP resolutions over time. The first resolution dates ranged from 7 October 2019 and 19 March 2024. Take a look at five examples below.
| DOMAIN IoC | FIRST RESOLUTION DATE | LAST RESOLUTION DATE | NUMBER OF IP RESOLUTIONS |
|---|---|---|---|
| annetterawlings[.]com | 10/18/19 | 10/2/24 | 37 |
| howasit[.]com | 11/8/19 | 1/30/24 | 35 |
| johnshimkus[.]com | 10/10/19 | 12/30/22 | 66 |
| markqualman[.]com | 11/19/21 | 11/27/24 | 74 |
| shehasgone[.]com | 3/19/24 | 10/18/24 | 6 |
Next, we queried the three IP addresses tagged as IoCs on Bulk IP Geolocation Lookup and found that:

We also queried the three IP addresses tagged as IoCs on DNS Chronicle API and found that they have had 460 domain resolutions over time. The first resolution dates ranged from 4 October 2019 to 17 November 2020. The IP address IoC 172[.]96[.]139[.]82, for instance, first resolved tx[.]cyrex[.]io on 17 November 2020.
Our search for more_eggs-connected artifacts started with a WHOIS History API query for the 14 domains tagged as IoCs. The results showed that 13 of them had 40 email addresses in their historical WHOIS records after duplicates were filtered out. 19 of the 40 email addresses turned out to be public.
A Reverse WHOIS API query for the 19 public email addresses revealed that four appeared in the current WHOIS records of 35 email-connected domains after filtering out duplicates and the domain IoCs.
Next, we queried the 14 domains tagged as IoCs on DNS Lookup API and found that 13 of them resolved to 11 IP addresses after removing duplicates that are not found on the original IoC list.
A Threat Intelligence API query for the 11 additional IP addresses revealed that three of them have already figured in malicious campaigns. The IP address 199[.]59[.]243[.]227, for instance, has seemingly been involved in phishing, command and control (C&C), generic threats, malware distribution, attacks, and suspicious activities.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byIPv4.Global

Sponsored byRadix

Sponsored byCSC
