


|
||
|
||
BlueNorroff struck again last October, this time setting its sights on tech company execs, venture capitalists, and Web3 developers.
The actors zoomed in on tech company execs’ and venture capitalists’ macOS devices via GhostCall. They approached victims on Telegram and similar platforms, luring them with potential investments. Targets were invited to Zoom meetings, and once the call ensued, they were tricked into updating Zoom with a malicious script that downloaded a malicious ZIP file. As a result, the victims lost secret files, including crypto wallet information, keychain data, package managers, and infrastructure setups. They also lost details related to cloud and DevOps platforms, along with their notes, API keys for OpenAI, collaboration application data, and credentials stored in browsers, messengers, and Telegram.
In GhostHire, the attackers went after Web3 developers, tricking them into downloading and executing a GitHub repository containing malware disguised as a skill assessment test for recruitment. It did not matter what OS the targets used, the malware worked regardless. Like GhostCall, GhostHire stole sensitive information, including videos and profile images.
Securelist reported that GhostCall and GhostHire were interrelated in that they shared the same infrastructure and identified 39 domains as IoCs. After checking via the WhoisXML API MCP Server using the prompt “Check the domains using WHOIS API, Website Categorization API, and Threat Intelligence API to determine if any of them are legitimate,” we found out that all of them were suspicious or downright malicious. As such, all of them figured in our analysis that led to these discoveries:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our inquiry into GhostCall and GhostHire by looking more closely at the IoCs. We used both external and internal data to do that.
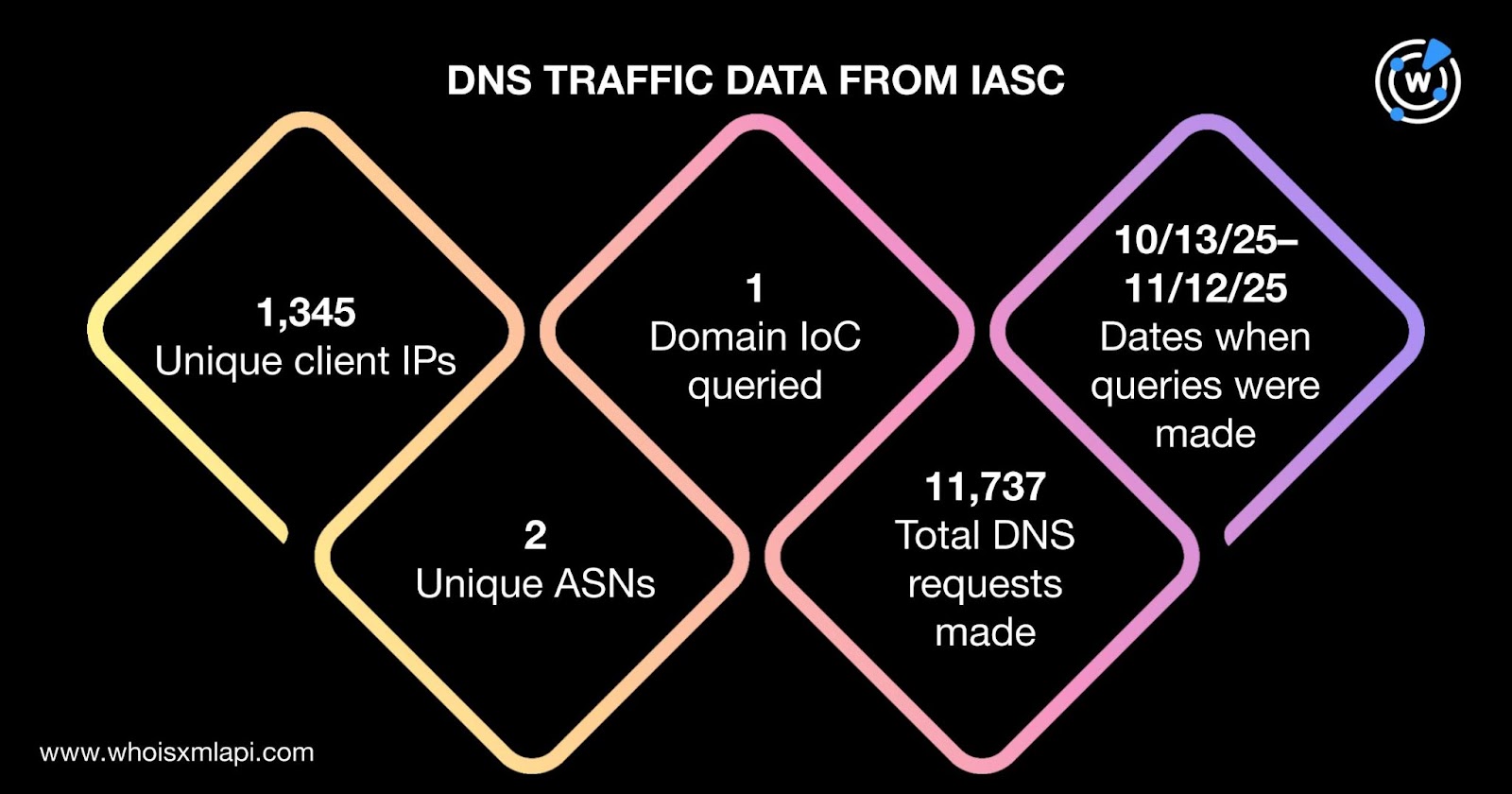
Sample network traffic data from the IASC showed that 1,345 unique client IP addresses under two distinct ASNs communicated with one of the domains identified as IoCs via 11,737 DNS requests made between 13 October and 12 November 2025.
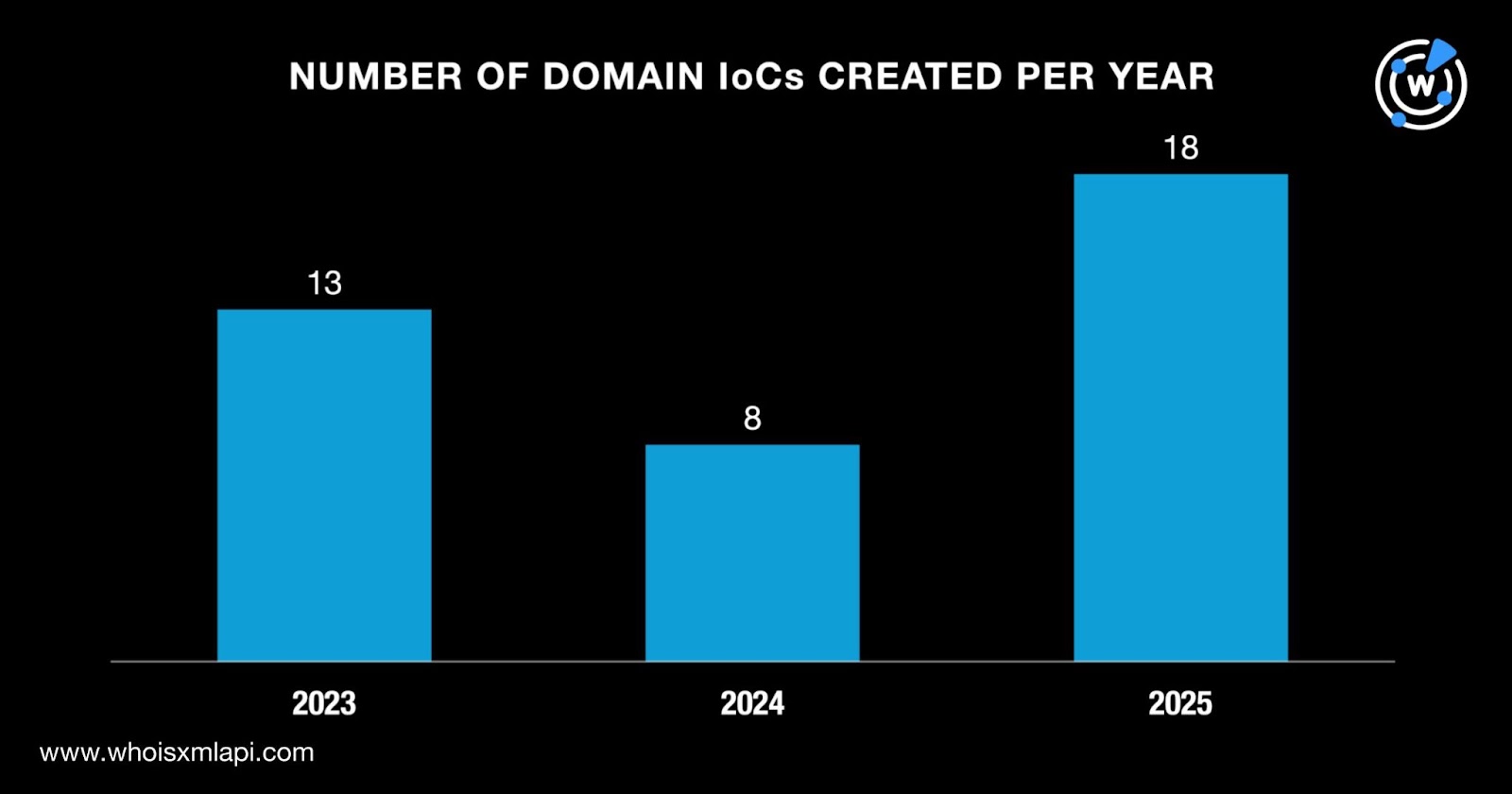
To gather more information, we queried the 39 domains identified as IoCs on First Watch Malicious Domains Data Feed and discovered that 11 of them were deemed likely to turn malicious 266—723 days before they were dubbed as such on 28 October 2025. Take a look at the details for five examples below.
| DOMAIN IoC | FIRST WATCH DATE | NUMBER OF DAYS PRIOR TO 28 OCTOBER 2025 |
|---|---|---|
| instant-update[.]online | 3 November 2023 | 725 |
| urgent-update[.]cloud | 3 November 2023 | 725 |
| autoupdate[.]online | 5 November 2023 | 723 |
| security-update[.]xyz | 5 November 2023 | 723 |
| systemupdate[.]cloud | 5 November 2023 | 723 |
We also checked if any of the 39 domains identified as IoCs were bulk-registered with look-alikes via Typosquatting Data Feed and found out that six—system-update[.]xyz, systemupdate[.]cloud, autoupdate[.]online, autoupdate[.]xyz, flashstore[.]sbs, and ms-live[.]us—were part of five typosquatting groups with three domains each. Note that autoupdate[.]online and autoupdate[.]xyz were part of the same group. And they were registered between 22 October 2023 and 6 September 2025. Here are more details.
| DOMAIN IoC | NUMBER OF LOOK-ALIKES | REGISTRATION DATE |
|---|---|---|
| system-update[.]xyz | 2 | 22 October 2023 |
| systemupdate[.]cloud | 2 | 6 November 2023 |
| autoupdate[.]online | 2(including another IoC autoupdate[.]xyz) | 6 November 2023 |
| autoupdate[.]xyz | 2(including another IoC autoupdate[.]online) | 6 November 2023 |
| flashstore[.]sbs | 2 | 28 May 2025 |
| ms-live[.]us | 2 | 6 September 2025 |
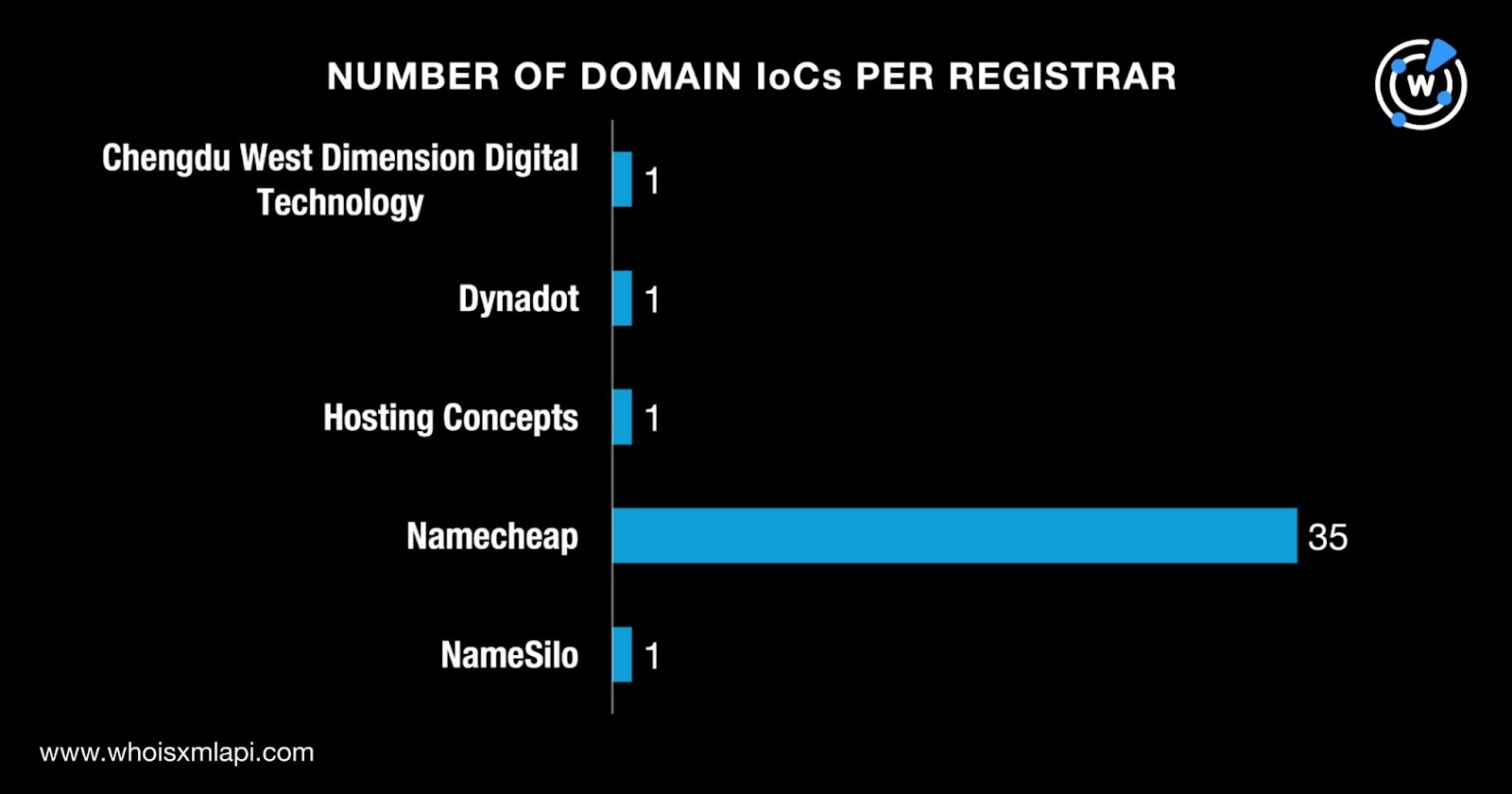
Next, we queried the 39 domains identified as IoCs on WHOIS API and found out that only 28 had current WHOIS records. However, Domain Info API did allow us to fill in the details for the remaining 11 domains. The results showed that:
They were administered by five registrars led by Namecheap, which accounted for 35 domains. One domain each fell under the purview of Chengdu West Dimension Digital Technology, Dynadot, Hosting Concepts, and NameSilo.
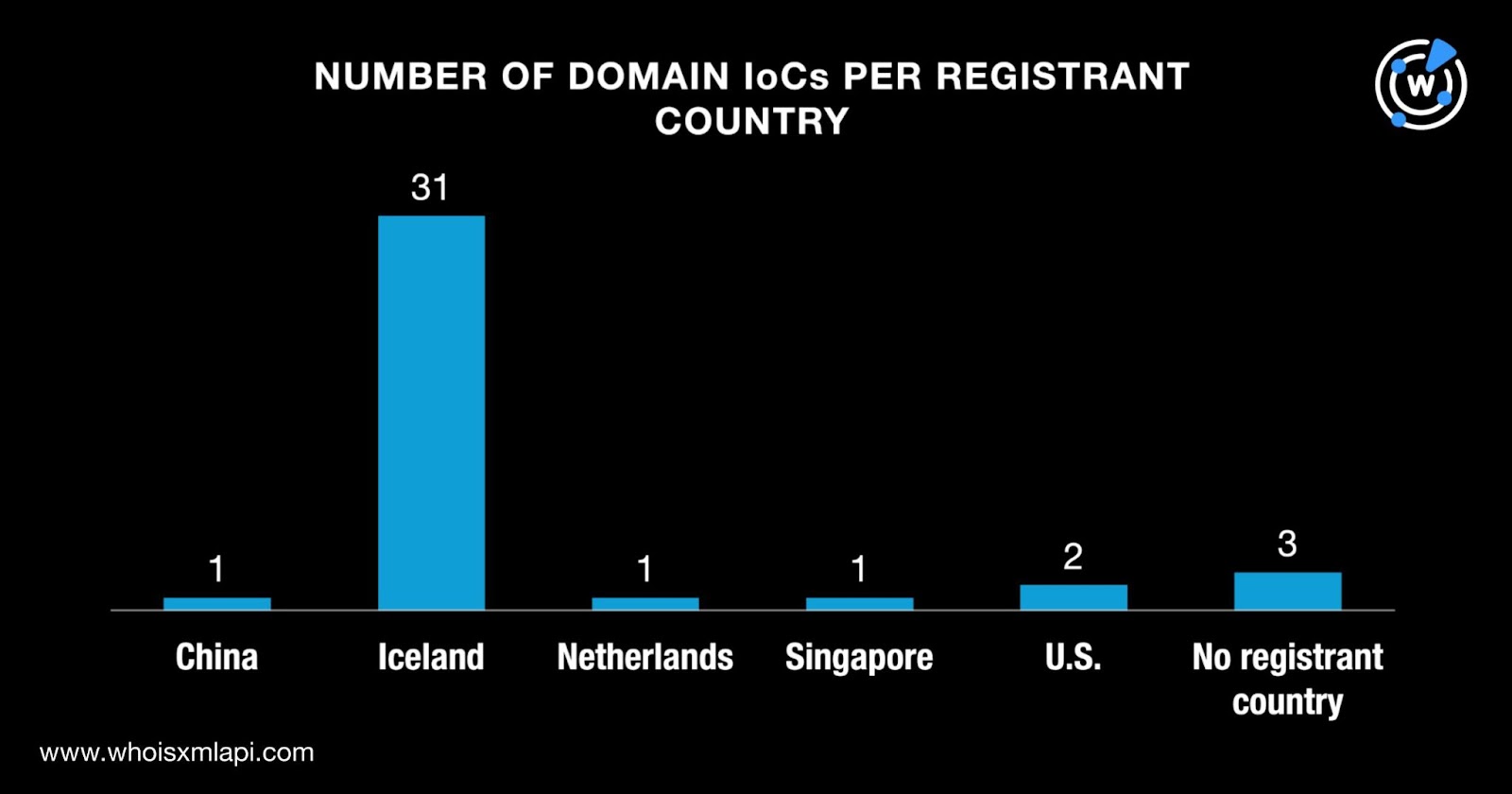
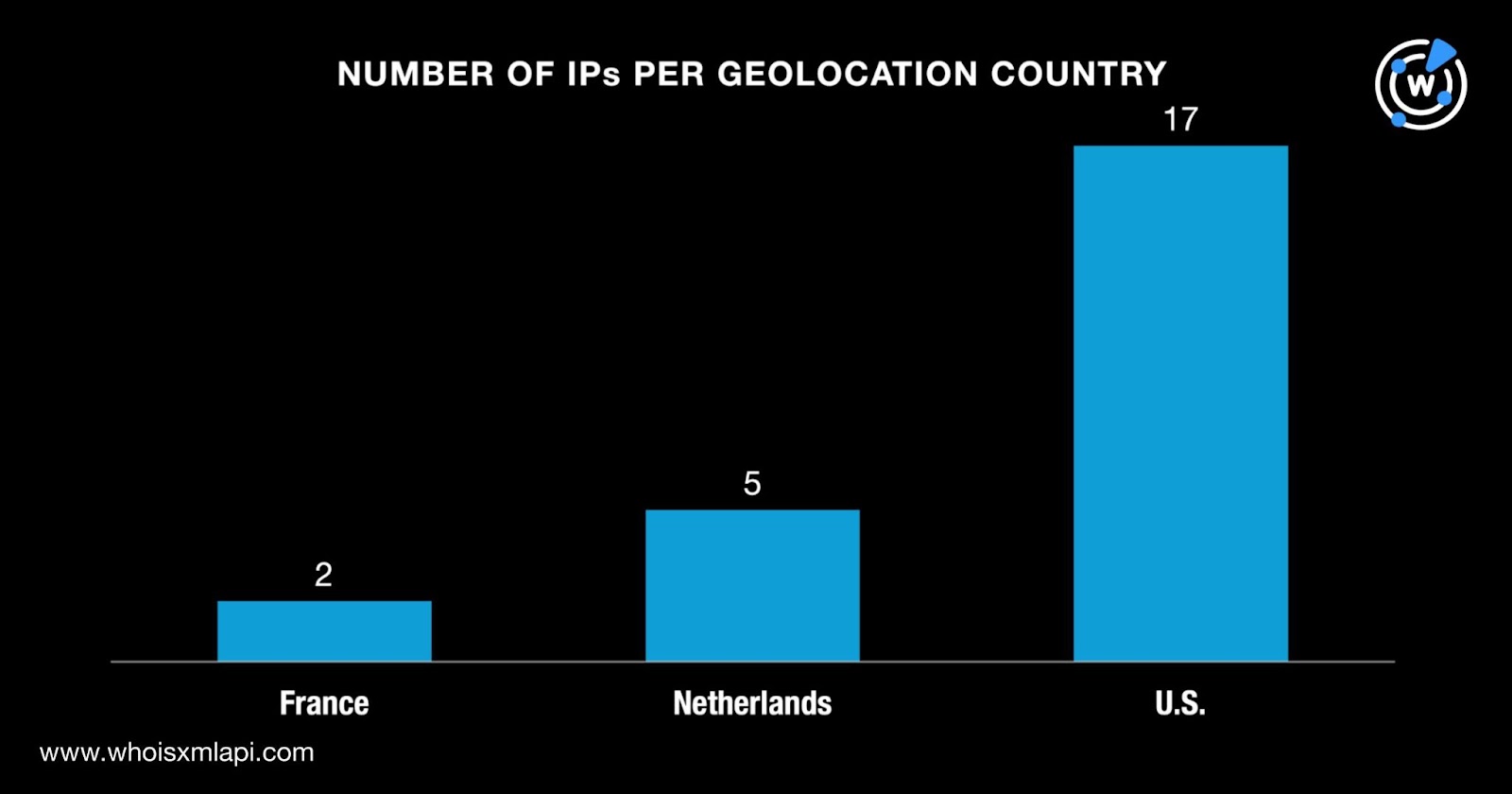
While three of the domains did not have registrant countries on record, the remaining 36 were split among five countries. Thirty-one domains were registered in Iceland; two in the U.S.; and one each in China, the Netherlands, and Singapore.
A DNS Chronicle API query for the 39 domains identified as IoCs revealed that 36 had 1,034 historical domain-to-IP resolutions over time. The domain writeup[.]live posted the oldest resolution on 17 August 2018. Here are details for five examples.
| DOMAIN IoC | NUMBER OF RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE |
|---|---|---|---|
| web071zoom[.]us | 179 | 21 April 2025 | 30 October 2025 |
| writeup[.]live | 126 | 17 August 2018 | 29 October 2025 |
| real-update[.]xyz | 113 | 12 April 2019 | 13 July 2025 |
| filedrive[.]online | 108 | 20 October 2019 | 7 July 2023 |
| secondshop[.]online | 66 | 1 October 2020 | 29 October 20/25 |
We began our search for new artifacts by querying the 39 domains identified as IoCs on WHOIS History API and discovered that 25 had email addresses in their historical WHOIS records. In fact, they had 29 unique email addresses, four of which turned out to be public addresses.
While none of the four public email addresses were found in other domains’ current WHOIS records based on the results of a Reverse WHOIS API query, they did show up on the historical WHOIS records of four email-connected domains after duplicates and those already tagged as IoCs were filtered out.
A Threat Intelligence API query for the four email-connected domains revealed that three were already considered malicious. An example would be sidezoom[.]us, which was used to distribute malware.
Next, we queried the 39 domains identified as IoCs on DNS Lookup API and discovered that 21 actively resolved to 24 unique IP addresses.
When queried on Threat Intelligence API, we found out that 21 of the IP addresses have already been weaponized for various attacks. Here are five examples.
| IP ADDRESS | ASSOCIATED THREAT | DATES SEEN |
|---|---|---|
| 13[.]248[.]169[.]48 | Malware distribution Phishing Suspicious activity Spamming Generic threat Command and control (C&C) | 03/29/23–10/31/25 03/28/23–10/31/25 04/05/23–10/30/25 04/14/23–10/27/25 03/28/23–10/26/25 04/05/23–10/25/25 |
| 76[.]223[.]54[.]146 | Malware distribution Phishing Suspicious activity Spamming Generic threat C&C | 03/29/23–10/31/25 03/28/23–10/31/25 04/05/23–10/30/25 04/14/23–10/27/25 03/28/23–10/26/25 04/05/23–10/25/25 |
| 172[.]236[.]126[.]142 | Malware distribution Phishing Generic threat Suspicious activity | 10/16/25–10/31/25 10/15/25–10/31/25 10/16/25–10/30/25 10/16/25–10/24/25 |
| 172[.]236[.]126[.]145 | Phishing Malware distribution Generic threat Suspicious activity | 10/15/25–10/31/25 10/16/25–10/31/25 10/16/25–10/30/25 10/16/25–10/24/25 |
| 172[.]236[.]126[.]225 | Phishing Malware distribution Generic threat Suspicious activity | 10/15/25–10/31/25 10/16/25–10/31/25 10/16/25–10/30/25 10/16/25–10/24/25 |
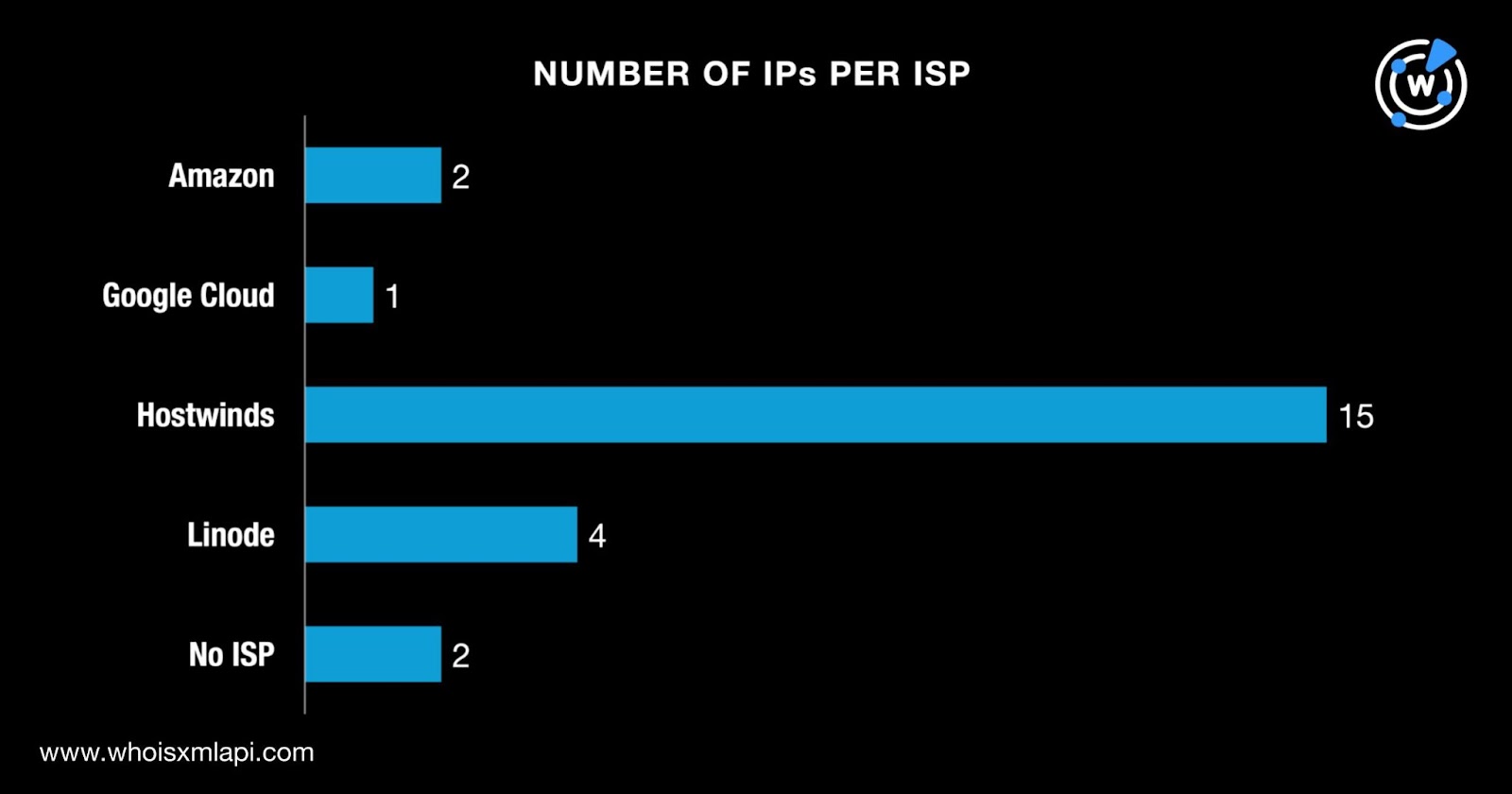
In a bid to gather more information about the 24 IP addresses, we queried them on Bulk IP Geolocation Lookup. The results showed that:
While two IP addresses did not have ISP data on record, the remaining 22 were distributed among four ISPs. Fifteen IP addresses were administered by Hostwinds, four by Linode, two by Amazon, and one by Google Cloud.
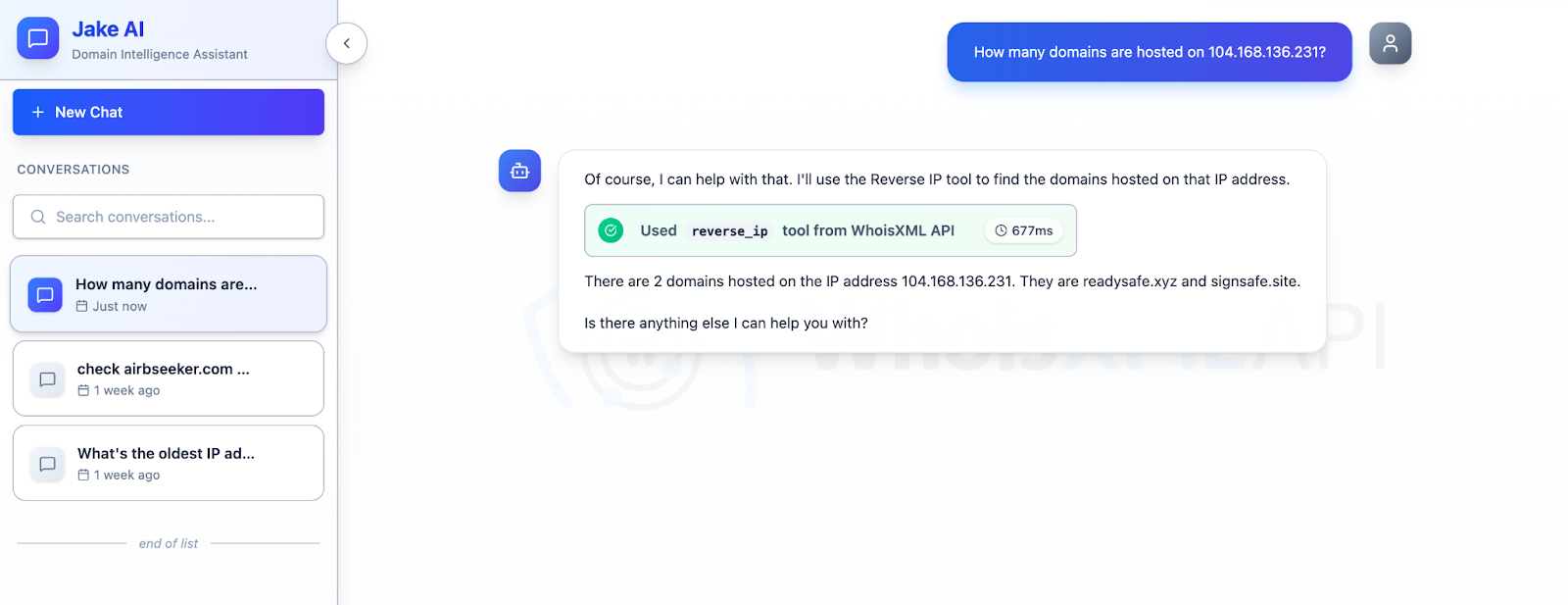
Next, we queried the 24 IP addresses on Jake AI to determine which could be dedicated hosts. We used the prompt “How many domains are hosted on 104.168.136.231?” for each IP address and discovered that 17 could be dedicated hosts.
Upon closer examination, the 17 possibly dedicated IP addresses hosted 16 IP-connected domains after duplicates, those already tagged as IoCs, and the email-connected domains were filtered out.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byWhoisXML API

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byRadix

Sponsored byCSC
