


|
||
|
||
The Acronis Threat Research Unit (TRU) recently discovered a massive malvertising campaign leveraging apps users commonly install on their computers. Dubbed “TamperedChef,” users were tricked into downloading malicious scripts via clever social engineering ruses. The scripts automatically executed their payloads that resulted in nefarious actions, including establishing and selling remote access for profit, stealing and monetizing sensitive credentials and healthcare data, preparing compromised systems for future ransomware deployment, and engaging in opportunistic espionage by exploiting access to high-value targets.
The researchers identified 58 IoCs comprising URLs and subdomains. We extracted 58 unique domains from the IoCs and weeded out those that were legitimate with the help of the WhoisXML API MCP Server. This step left us with 46 domains for further analysis. Our in-depth investigation led to these discoveries:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our foray deep into the DNS by querying the 46 domains identified as IoCs on First Watch Malicious Domains Data Feed. We discovered that 28 of them were deemed likely to turn malicious upon registration, that is, between 155 and 335 days before they were dubbed as IoCs on 19 November 2025. Take a look at more details below.
| DOMAIN IoC | FIRST WATCH DATE | NUMBER OF DAYS PRIOR TO REPORT DATE |
|---|---|---|
| opfktvbbb0d5pphzlc[.]com | 19 December 2024 | 335 |
| effortlesspdf[.]com | 15 January 2025 | 308 |
| k2ioeasm874fnacr9x[.]com | 24 January 2025 | 299 |
| meg7xqos0m7h9urhr0[.]com | 24 January 2025 | 299 |
| 85etpt40zf7ht4yd1u[.]com | 27 January 2025 | 296 |
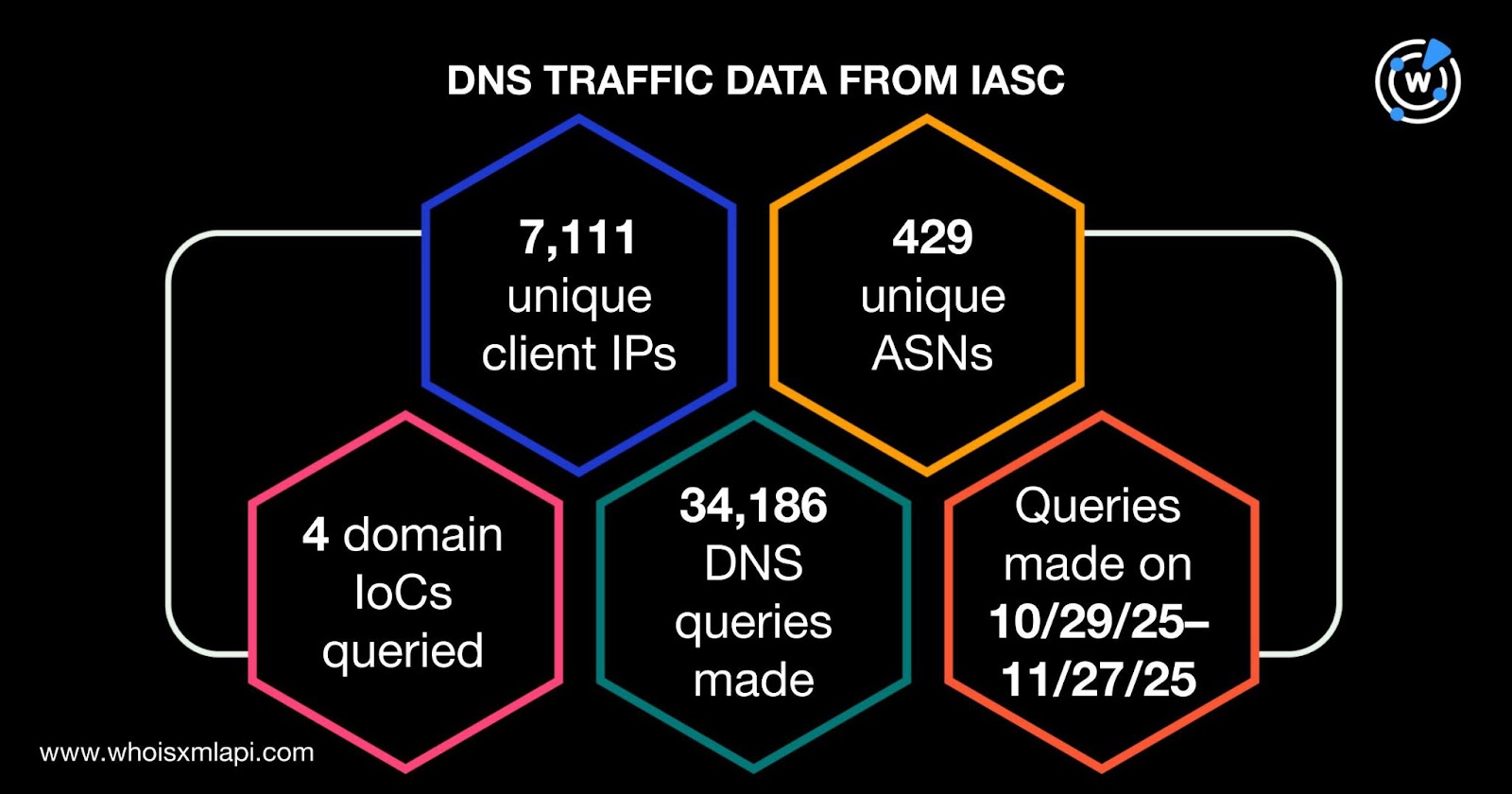
In addition, sample network traffic data from the IASC revealed that 7,111 unique client IP addresses under 429 distinct ASNs communicated with four of the domains tagged as IoCs. Altogether, they made 34,186 DNS queries between 29 October and 27 November 2025.
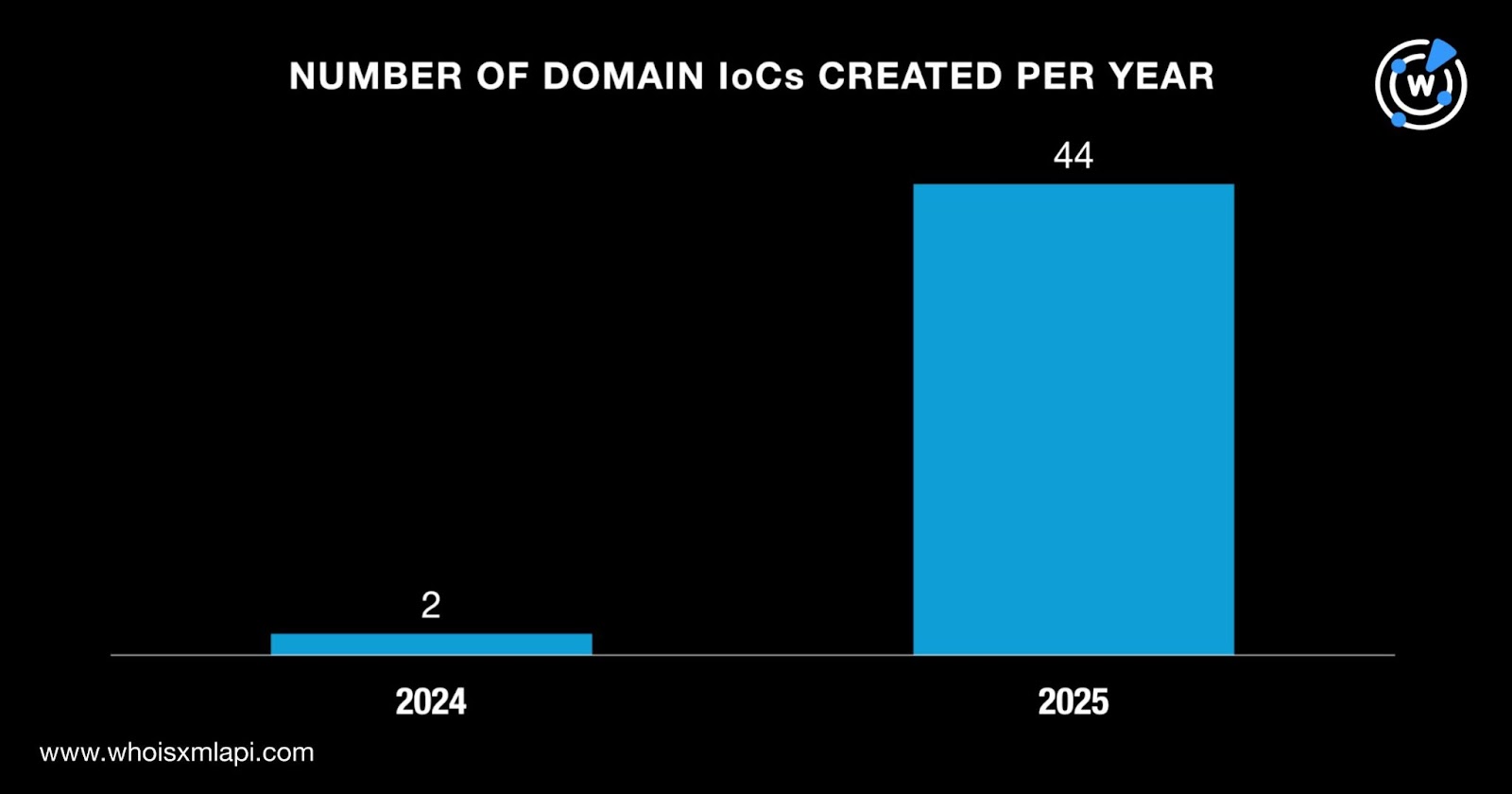
Next, we queried the 46 domains identified as IoCs on WHOIS API. We found out that:
A DNS Chronicle API query, meanwhile, for the 46 domains tagged as IoCs showed that 24 had historical domain-to-IP resolutions. The domains resolved to 438 IP addresses over time. These resolutions were recorded as far back as 5 February 2017 specifically by getallmanuals[.]com.
Interestingly, getallmanuals[.]com was created on 15 January 2025 according to its current WHOIS record but resolved to 184[.]168[.]221[.]38 as early as 15 January 2025. That could mean that getallmanuals[.]com’s domain registration expired and it was picked up again recently potentially by the actors behind TamperedChef. Here are more details about five other domains tagged as IoCs.
| DOMAIN IoC | NUMBER OF RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE |
|---|---|---|---|
| usermanualsonline[.]com | 24 | 11 December 2024 | 30 September 2025 |
| effortlesspdf[.]com | 20 | 16 January 2025 | 20 November 2025 |
| getmanualviewer[.]com | 16 | 17 January 2025 | 28 October 2025 |
| k2ioeasm874fnacr9x[.]com | 1 | 27 January 2025 | 27 January 2025 |
| 85etpt40zf7ht4yd1u[.]com | 2 | 28 January 2025 | 29 January 2025 |
We started our search for new artifacts by querying the 46 domains identified as IoCs on WHOIS History API. All of them had email addresses in their historical WHOIS records. Specifically, they had 54 unique email addresses in their records. Further scrutiny revealed that four were public email addresses.
Next, we queried the four public email addresses on Reverse WHOIS API. While none of them appeared in any domain’s current WHOIS records, all did so in historical records. This step led to the discovery of 97 email-connected domains after duplicates and those already tagged as IoCs were filtered out.
Afterward, we queried the 46 domains identified as IoCs on DNS Lookup API, which revealed that 14 of them had active IP resolutions. All in all, the 14 domains resolved to 24 unique IP addresses.
A Threat Intelligence API query for the 24 IP addresses showed that 10 of them have already been weaponized for nefarious campaigns.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byRadix

Sponsored byCSC

Sponsored byWhoisXML API

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byIPv4.Global
