


|
||
|
||
The Center for Internet Security (CIS) just named the top 10 malware of Q3 2025 and identified 31 domains as IoCs for five of them. After weeding out legitimate domains from their list with the help of the WhoisXML API MCP Server, we were left with 26 domains for our study. Take a look at the breakdown below.
| RANK | MALWARE | THREAT TYPE | NUMBER OF DOMAIN IoCs ORIGINALLY IDENTIFIED | NUMBER OF DOMAIN IoCs ANALYZED |
|---|---|---|---|---|
| 1 | SocGholish | Downloader | 8 | 6 |
| 3 | Agent Tesla | RAT | 2 | 1 |
| 5 | ZPHP | Downloader | 9 | 7 |
| 7 | Gh0st | RAT | 4 | 4 |
| 9 | Lumma Stealer | Infostealer | 8 | 8 |
| TOTAL | 31 | 26 |
Note that three of the top 10 malware of Q2 2025—SocGholish, Agent Tesla, and ZPHP—remained part of this quarter’s list. While SocGholish and Agent Tesla kept their top 1 and 3 rankings, respectively, ZPHP dropped from Q2’s top 2 to this quarter’s top 5.
Our in-depth analysis of five of the top malware for Q3 led to these discoveries:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our in-depth investigation by checking if any of the 26 domains tagged as IoCs appeared on First Watch Malicious Domains Data Feed. We discovered that two of them were deemed likely to turn malicious as soon as they were registered, between 150 and 598 days before they were dubbed as IoCs on 14 November 2025. Here are more details.
| MALWARE | DOMAIN IoC | DATE SEEN ON FIRST WATCH | NUMBER OF DAYS BEFORE REPORT DATE |
|---|---|---|---|
| Gh0st | xmcxmr[.]com | 26 March 2024 | 598 |
| SocGholish | emeraldpinesolutions[.]com | 17 June 2025 | 150 |
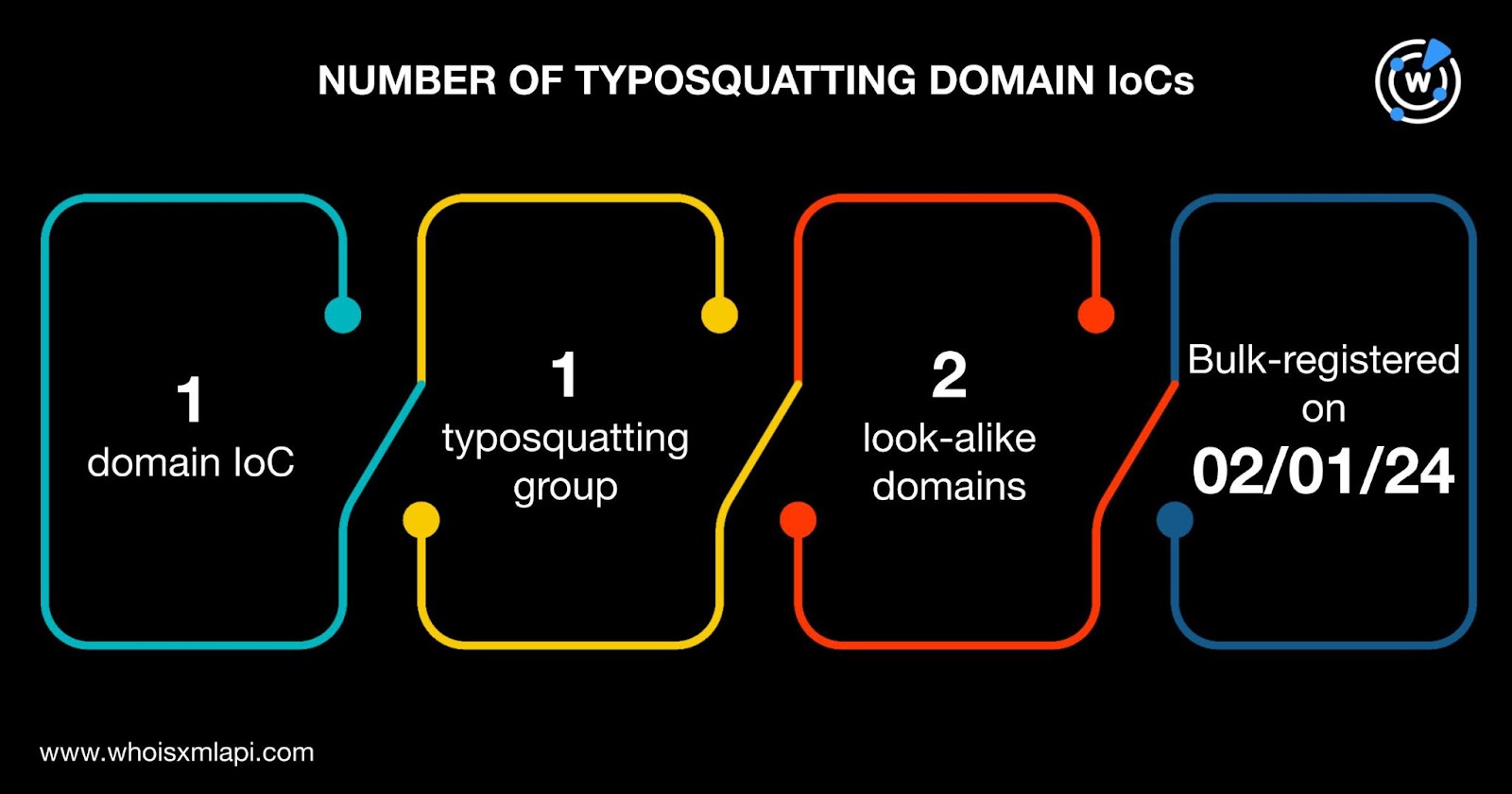
We also searched for the 26 domains identified as IoCs on Typosquatting Data Feed and discovered that one of them—trendings[.]top—was bulk-registered with two look-alikes—trendingg[.]shop and trendingon[.]store—on 1 February 2024.
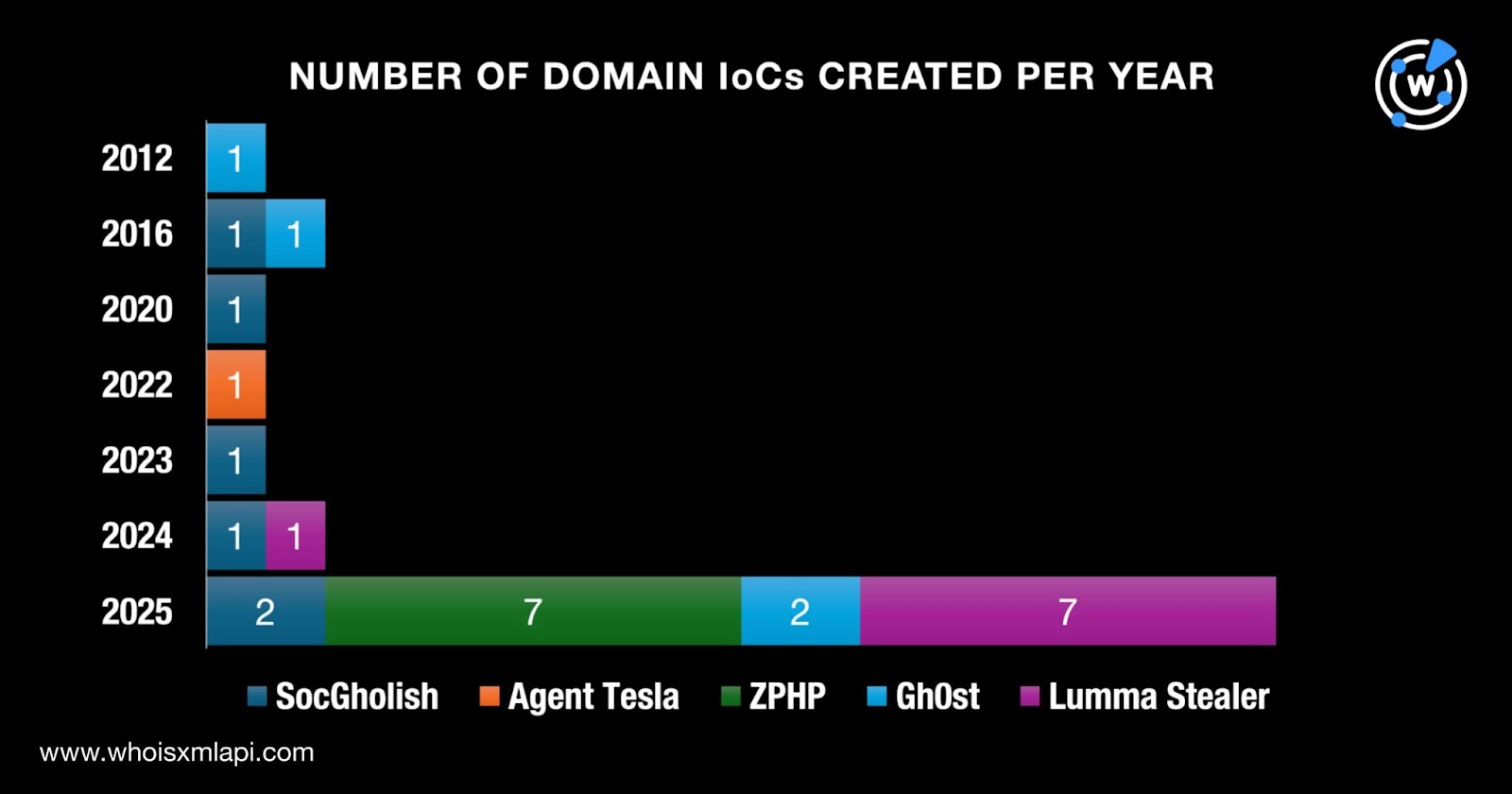
Next, we queried the 26 domains identified as IoCs on WHOIS API and filled out missing information aided by Domain Info API. We found out that:
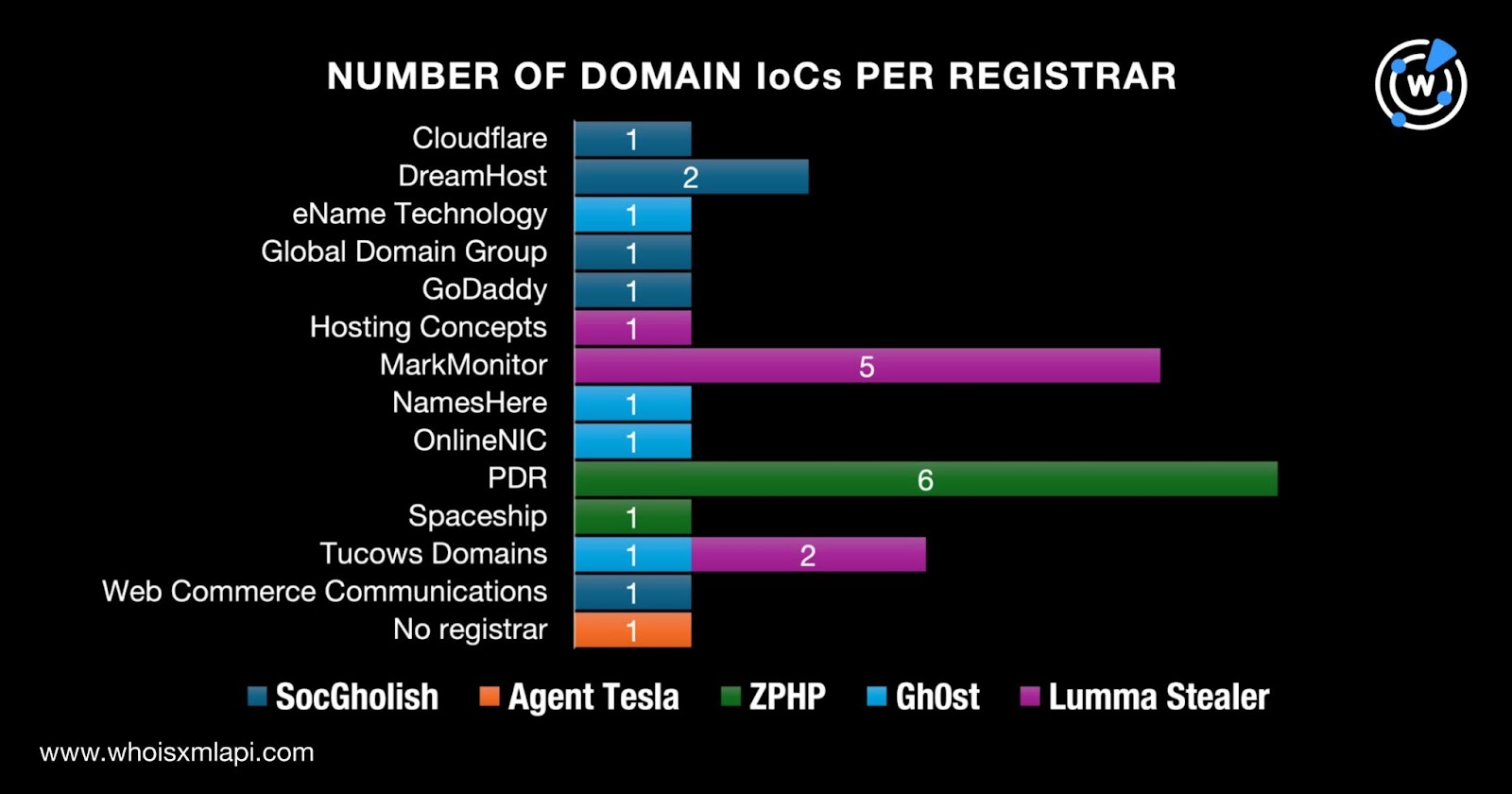
While one domain did not have registrar data in its current WHOIS record, the remaining 25 were distributed among 13 registrars. Six domains were administered by PDR; five by MarkMonitor; three by Tucows Domains; two by DreamHost; and one each by Cloudflare, eName Technology, the Global Domain Group, GoDaddy, Hosting Concepts, NamesHere, OnlineNIC, Spaceship, and Web Commerce Communications.
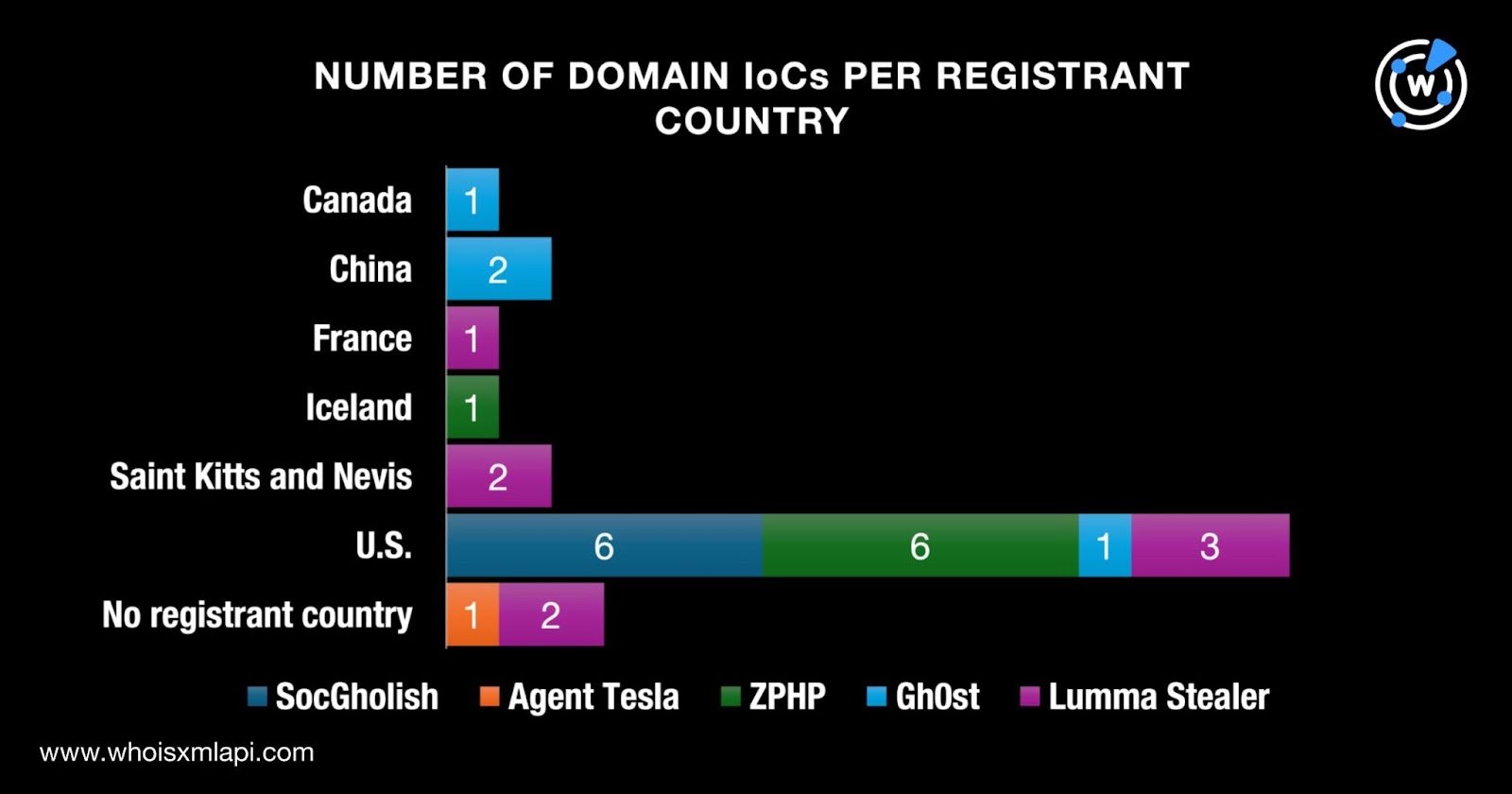
While three domains did not have registrant country data on record, the remaining 23 were registered in six countries. A total of 16 domains were registered in the U.S.; two each in China and Saint Kitts and Nevis; and one each in Canada, France, and Iceland.
We also obtained additional information on the 26 domains tagged as IoCs from DNS Chronicle API. The results showed that 25 of them posted a total of 2,564 historical domain-to-IP resolutions over time. The SocGholish domain ebuilderssource[.]com recorded the oldest resolution on 5 February 2017. Take a look at more details below.
| MALWARE | DOMAIN IoC | NUMBER OF RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE |
|---|---|---|---|---|
| SocGholish | ebuilderssource[.]com | 192 | 02/05/17 | 11/04/17 |
| Gh0st | vip5944[.]com | 251 | 02/07/17 | 09/27/25 |
| Gh0st | luyouxia[.]net | 259 | 04/17/17 | 10/16/25 |
| Gh0st | f3322[.]org | 159 | 04/15/18 | 08/13/21 |
| ZPHP | warpdrive[.]top | 59 | 08/03/19 | 03/22/25 |
We began our search for new artifacts by querying the 26 domains identified as IoCs on WHOIS History API. The results revealed that 16 of them had email addresses in their historical WHOIS records. We collated 45 unique email addresses in all. Further scrutiny showed that 17 of them were public email addresses.
Next, we queried the 17 public email addresses on Reverse WHOIS API. While none of them appeared in current WHOIS records, 16 showed up on historical records. That led to the discovery of 5,266 email-connected domains after duplicates and those already tagged as IoCs were filtered out.
A Threat Intelligence API query for the 5,266 email-connected domains revealed that 56 of them have already been weaponized for nefarious activities. Here are five examples.
| MALICIOUS EMAIL-CONNECTED DOMAIN | ASSOCIATED THREAT | DATES SEEN |
|---|---|---|
| dashboard-aave[.]us | Phishing Generic threat | 04/20/25–10/19/25 04/21/25–09/20/25 |
| help-opensea[.]us | Phishing Generic threat | 03/25/25–09/25/25 03/27/25–09/20/25 |
| id-verification-12912[.]us | Generic threat Phishing | 09/10/25–10/13/25 09/09/25 |
| information-id188322[.]com | Phishing Generic threat | 07/18/25–11/20/25 07/19/25–09/20/25 |
| progressdev[.]xyz | Malware distribution Generic threat | 10/06/25–11/20/25 09/06/25 |
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byRadix

Sponsored byWhoisXML API

Sponsored byCSC
