

 SpaceX has filed a plan to place more than a million satellites in low Earth orbit, recasting data centres as spaceborne infrastructure while testing regulators, safety, competition and the line between vision and paper ambition.
SpaceX has filed a plan to place more than a million satellites in low Earth orbit, recasting data centres as spaceborne infrastructure while testing regulators, safety, competition and the line between vision and paper ambition.
 ICANN invites proposals for its DNSSEC and Security Workshop at the ICANN85 Community Forum in March 2026, offering a platform for global experts to share insights on DNS, routing security, and emerging threats.
ICANN invites proposals for its DNSSEC and Security Workshop at the ICANN85 Community Forum in March 2026, offering a platform for global experts to share insights on DNS, routing security, and emerging threats.
 AT&T’s CEO plays down the threat of satellite cellular, citing bandwidth and coverage limits. Yet growing interest in rural and IoT applications suggests the technology could still claim valuable niches in the wireless market.
AT&T’s CEO plays down the threat of satellite cellular, citing bandwidth and coverage limits. Yet growing interest in rural and IoT applications suggests the technology could still claim valuable niches in the wireless market.
 CaribNOG and PCH have renewed their partnership to boost the Caribbean's Internet resilience, expanding technical capacity, advancing inclusive training, and strengthening the people and systems essential for recovery as islands rebuild after Hurricane Melissa.
CaribNOG and PCH have renewed their partnership to boost the Caribbean's Internet resilience, expanding technical capacity, advancing inclusive training, and strengthening the people and systems essential for recovery as islands rebuild after Hurricane Melissa.
 The hiQ ruling erased legal protections against commercial scraping, leaving infrastructure providers to absorb escalating costs. Without federal action defining data misappropriation, a free-rider AI economy could undermine open networks, investment, and long-term data integrity.
The hiQ ruling erased legal protections against commercial scraping, leaving infrastructure providers to absorb escalating costs. Without federal action defining data misappropriation, a free-rider AI economy could undermine open networks, investment, and long-term data integrity.
 The Internet has evolved from a scarcity-driven system into one defined by abundance, reshaping infrastructure, governance, and economic models while challenging long-held assumptions about addressing, network roles, and the future of protocol design.
The Internet has evolved from a scarcity-driven system into one defined by abundance, reshaping infrastructure, governance, and economic models while challenging long-held assumptions about addressing, network roles, and the future of protocol design.
 Over two years of war, Israel has decimated Gaza's ICT infrastructure, crippling connectivity, impeding emergency response, and isolating civilians from the digital world, while cementing long-standing control over telecommunications under the guise of national security.
Over two years of war, Israel has decimated Gaza's ICT infrastructure, crippling connectivity, impeding emergency response, and isolating civilians from the digital world, while cementing long-standing control over telecommunications under the guise of national security.
 Private DNS data lakes consolidate fragmented logs into a centralised platform, improving visibility, security, and compliance. They enable advanced analytics, strengthen threat detection, and help organisations optimise network performance in increasingly complex IT environments.
Private DNS data lakes consolidate fragmented logs into a centralised platform, improving visibility, security, and compliance. They enable advanced analytics, strengthen threat detection, and help organisations optimise network performance in increasingly complex IT environments.
 Earlier this week, Poland’s new President, Karol Nawrocki, vetoed amendments to the Act on Assistance to Citizens of Ukraine, provoking debate over critical satellite connectivity. Deputy Prime Minister and Minister of Digital Affairs Krzysztof Gawkowski warned that the veto “de facto switched off Starlink for Ukraine,” potentially disrupting connectivity for hospitals, schools, and government operations.
Earlier this week, Poland’s new President, Karol Nawrocki, vetoed amendments to the Act on Assistance to Citizens of Ukraine, provoking debate over critical satellite connectivity. Deputy Prime Minister and Minister of Digital Affairs Krzysztof Gawkowski warned that the veto “de facto switched off Starlink for Ukraine,” potentially disrupting connectivity for hospitals, schools, and government operations.
 This study analyzes the differences in domain name and IP address strategies among a number of current mainstream artificial intelligence (AI) service providers. We find that these technical choices not only reflect deployment decisions but also deep-seated corporate knowledge and capabilities in Internet infrastructure service provision, as well as brand positioning and market strategies.
This study analyzes the differences in domain name and IP address strategies among a number of current mainstream artificial intelligence (AI) service providers. We find that these technical choices not only reflect deployment decisions but also deep-seated corporate knowledge and capabilities in Internet infrastructure service provision, as well as brand positioning and market strategies.
 Networks are typically built to provide certain services at an expected scale. The rationale for this focused objective is entirely reasonable: to overachieve would be inefficient and costly. So, we build service infrastructure to a level of sufficient capability to meet expectations and no more. In ideal conditions, this leads to a widely deployed and highly efficient infrastructure that is capable of supporting a single service profile.
Networks are typically built to provide certain services at an expected scale. The rationale for this focused objective is entirely reasonable: to overachieve would be inefficient and costly. So, we build service infrastructure to a level of sufficient capability to meet expectations and no more. In ideal conditions, this leads to a widely deployed and highly efficient infrastructure that is capable of supporting a single service profile.
 The story of computing and communications over the past eighty years has been a story of quite astounding improvements in the capability, cost and efficiency of computers and communications. If the same efficiency improvements had been made in the automobile industry cars would cost a couple of dollars, would cost fractions of a cent to use for trips, and be capable of travelling at speeds probably approaching the speed of light!
The story of computing and communications over the past eighty years has been a story of quite astounding improvements in the capability, cost and efficiency of computers and communications. If the same efficiency improvements had been made in the automobile industry cars would cost a couple of dollars, would cost fractions of a cent to use for trips, and be capable of travelling at speeds probably approaching the speed of light!
 Dave Taht died on April 1st. I met him only recently, and never in person, but his passing saddens me. His technical work and evangelism have improved the Internet, and I will give some examples of his contributions to the Internet community and users, but I am sad because he was a good person -- idealistic, unselfish, open, and funny. I'll miss him. First, his contributions, then his values.
Dave Taht died on April 1st. I met him only recently, and never in person, but his passing saddens me. His technical work and evangelism have improved the Internet, and I will give some examples of his contributions to the Internet community and users, but I am sad because he was a good person -- idealistic, unselfish, open, and funny. I'll miss him. First, his contributions, then his values.
 The Christmas Goat attracted 809 unique AS numbers this year, with IPv6 usage led by the USA and Finland. Despite a rise to 39% IPv6 adoption, challenges like outdated routers persist. As this 15-year tradition concludes, the holiday Goat highlights the progress and hurdles of IPv6 integration.
The Christmas Goat attracted 809 unique AS numbers this year, with IPv6 usage led by the USA and Finland. Despite a rise to 39% IPv6 adoption, challenges like outdated routers persist. As this 15-year tradition concludes, the holiday Goat highlights the progress and hurdles of IPv6 integration.
 If you operate an Internet Exchange Point (IXP) or are interested in creating one, the Internet Society has a “Sustainable Peering Infrastructure” funding program that is open for applications until this Friday, September 6, 2024... Grant funds from USD $5,000 up to $50,000 are open to all regions and are available to assist in equipment purchases (switches, optic modules, servers, and routers), training, capacity building, and community development.
If you operate an Internet Exchange Point (IXP) or are interested in creating one, the Internet Society has a “Sustainable Peering Infrastructure” funding program that is open for applications until this Friday, September 6, 2024... Grant funds from USD $5,000 up to $50,000 are open to all regions and are available to assist in equipment purchases (switches, optic modules, servers, and routers), training, capacity building, and community development.
 US Senators Move to Shield Undersea Internet Cables from Global Threats
US Senators Move to Shield Undersea Internet Cables from Global Threats Internet Visionaries Honored with Postel Service Award
Internet Visionaries Honored with Postel Service Award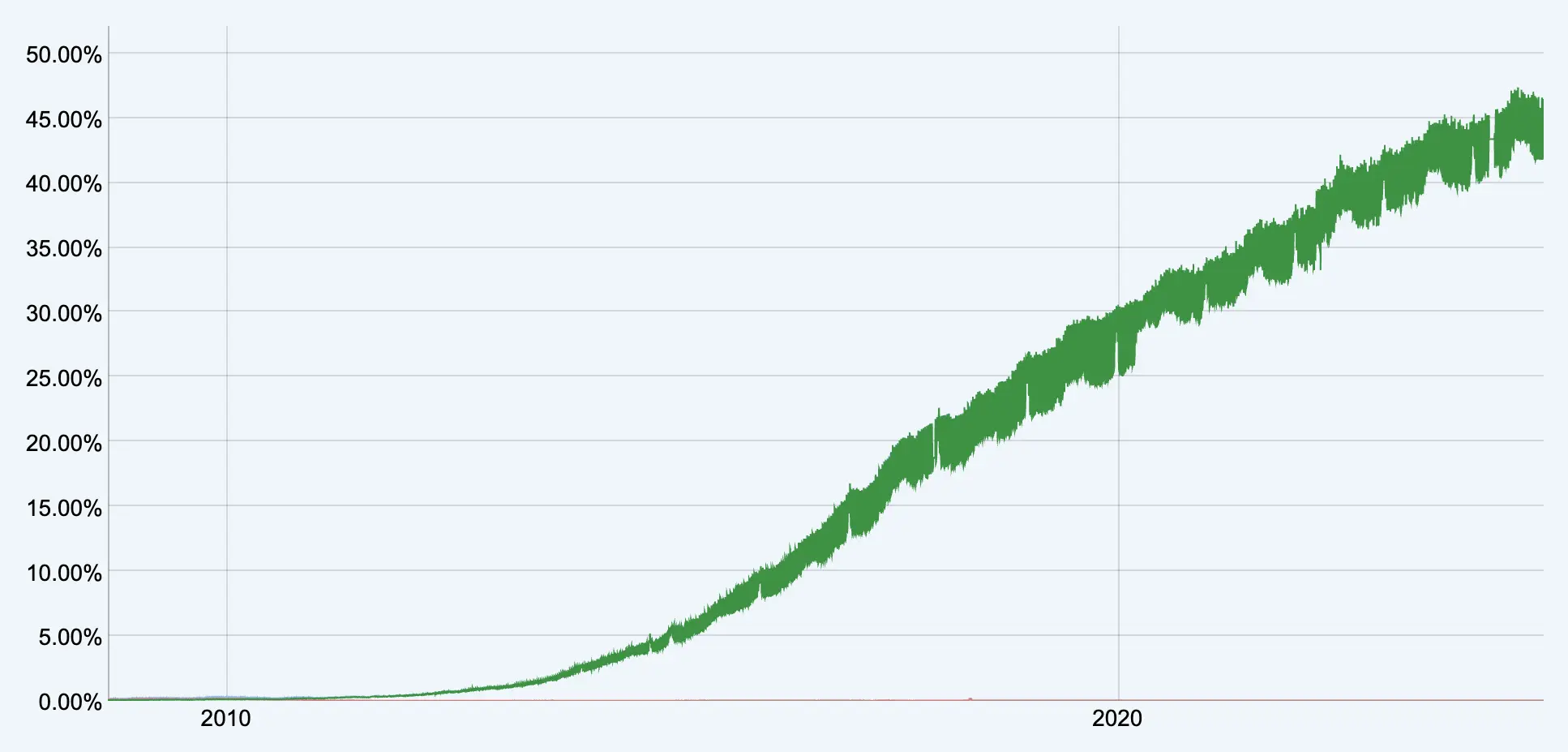 IPv6 Transition Stalls as Internet Moves Beyond IP Addresses
IPv6 Transition Stalls as Internet Moves Beyond IP Addresses Global IT Outage Disrupts Airlines, Businesses, and Hospitals
Global IT Outage Disrupts Airlines, Businesses, and Hospitals Vint Cerf Receives IEEE Medal of Honor
Vint Cerf Receives IEEE Medal of Honor