

 Exploding internet traffic and AI demand are driving a rapid upgrade in fibre transport lasers, from early one gigabit systems to 400, 800 and even 1.6 terabit links reshaping backbone capacity worldwide as networks scale.
Exploding internet traffic and AI demand are driving a rapid upgrade in fibre transport lasers, from early one gigabit systems to 400, 800 and even 1.6 terabit links reshaping backbone capacity worldwide as networks scale.
 As governments assert internet sovereignty, global networks are quietly fracturing. Data localisation, sovereign cloud rules and political risk are forcing companies to redesign technology stacks once built for a borderless internet.
As governments assert internet sovereignty, global networks are quietly fracturing. Data localisation, sovereign cloud rules and political risk are forcing companies to redesign technology stacks once built for a borderless internet.
 A critique of ICANN's multi-stakeholder model argues that its accountability record, revealed through more than a dozen IRP disputes, shows structural failures that should caution policymakers seeking institutional blueprints for governing artificial intelligence systems globally.
A critique of ICANN's multi-stakeholder model argues that its accountability record, revealed through more than a dozen IRP disputes, shows structural failures that should caution policymakers seeking institutional blueprints for governing artificial intelligence systems globally.
 Efforts to combat online piracy are pushing courts to weaponise the Internet's naming system. Turning DNS operators into enforcement agents may deliver quick takedowns, but risks collateral damage, jurisdictional conflict and long-term fragmentation of the Internet.
Efforts to combat online piracy are pushing courts to weaponise the Internet's naming system. Turning DNS operators into enforcement agents may deliver quick takedowns, but risks collateral damage, jurisdictional conflict and long-term fragmentation of the Internet.
 Hidden on telecom balance sheets, legacy IPv4 address space is emerging as a monetizable asset. Leasing underutilized blocks can generate recurring cash flow that helps fund AI infrastructure, modernization, and network investment without increasing debt.
Hidden on telecom balance sheets, legacy IPv4 address space is emerging as a monetizable asset. Leasing underutilized blocks can generate recurring cash flow that helps fund AI infrastructure, modernization, and network investment without increasing debt.
 Despite steady expansion of fibre networks, the cost of building them is rising. New survey data show labour-heavy construction, higher aerial costs and persistent inflation pressures likely to push deployment expenses higher in 2026.
Despite steady expansion of fibre networks, the cost of building them is rising. New survey data show labour-heavy construction, higher aerial costs and persistent inflation pressures likely to push deployment expenses higher in 2026.
 ICANN's proposed overhaul of root server governance would empower a new council to revoke America's operator status, risking a clash with a resurgent Trump administration and potentially imperiling the multistakeholder model that underpins the internet's core infrastructure.
ICANN's proposed overhaul of root server governance would empower a new council to revoke America's operator status, risking a clash with a resurgent Trump administration and potentially imperiling the multistakeholder model that underpins the internet's core infrastructure.
 A debate over aligning internet and AI governance reveals stark differences in origin, incentives and power. While lessons from ICANN's multi-stakeholder model endure, AI's corporate dominance and geopolitical rivalry demand new, bottom-up approaches.
A debate over aligning internet and AI governance reveals stark differences in origin, incentives and power. While lessons from ICANN's multi-stakeholder model endure, AI's corporate dominance and geopolitical rivalry demand new, bottom-up approaches.
 Generative AI has turned brand impersonation from a nuisance into an industrial-scale threat, eroding trust. As ICANN's 2026 round approaches, DotBrand domains promise a structural fix to spoofing that strategies failed to deliver in 2012.
Generative AI has turned brand impersonation from a nuisance into an industrial-scale threat, eroding trust. As ICANN's 2026 round approaches, DotBrand domains promise a structural fix to spoofing that strategies failed to deliver in 2012.
 An FCC ruling in a dispute between Comcast and Appalachian Power clarifies pole attachment cost rules, but exposes how regulatory delays and uncooperative utilities can slow fiber deployment and raise costs for broadband providers.
An FCC ruling in a dispute between Comcast and Appalachian Power clarifies pole attachment cost rules, but exposes how regulatory delays and uncooperative utilities can slow fiber deployment and raise costs for broadband providers.
 As geopolitical tensions expose the fragility of subsea cables, Low Earth Orbit satellites and the QUIC protocol promise a more resilient internet by diversifying routes, preserving session continuity, and redefining control over global data flows.
As geopolitical tensions expose the fragility of subsea cables, Low Earth Orbit satellites and the QUIC protocol promise a more resilient internet by diversifying routes, preserving session continuity, and redefining control over global data flows.
 India's AI summit promised a Global South rethink of digital governance. Instead, a weak declaration and Delhi's accession to America's Pax Silica exposed widening power asymmetries, leaving countries like Brazil outside the real circuitry of control.
India's AI summit promised a Global South rethink of digital governance. Instead, a weak declaration and Delhi's accession to America's Pax Silica exposed widening power asymmetries, leaving countries like Brazil outside the real circuitry of control.
 At Munich's twin security gatherings, leaders warned that cyber conflict, transatlantic rifts and weaponised AI are pushing the rules-based order into a perilous transition, where deterrence falters, norms erode and digital sovereignty trumps multistakeholder ideals.
At Munich's twin security gatherings, leaders warned that cyber conflict, transatlantic rifts and weaponised AI are pushing the rules-based order into a perilous transition, where deterrence falters, norms erode and digital sovereignty trumps multistakeholder ideals.
 Project Jake invites global DNS stakeholders to test JADDAR, a privacy-respecting framework for secure access to registration data, aiming to reduce regulatory fragmentation and modernise domain governance through collaborative, policy-aligned engineering solutions.
Project Jake invites global DNS stakeholders to test JADDAR, a privacy-respecting framework for secure access to registration data, aiming to reduce regulatory fragmentation and modernise domain governance through collaborative, policy-aligned engineering solutions.
A three-decade natural experiment suggests America's centralized regulatory review fostered far greater wealth creation than Europe's precautionary principle, raising stark questions about whether importing EU-style AI rules would undermine US innovation and prosperity.
 As the 2026 gTLD round opens, applicants face an overlooked geopolitical hazard: what happens if the registry or RIR underpinning their domain collapses under sanctions or war, leaving contracts stranded and accountability elusive.
As the 2026 gTLD round opens, applicants face an overlooked geopolitical hazard: what happens if the registry or RIR underpinning their domain collapses under sanctions or war, leaving contracts stranded and accountability elusive.
As policymakers search for an IAEA for AI, lessons from ICANN and internet governance loom large, raising questions about multistakeholder legitimacy, mission creep, technical fragmentation and whether AI demands sector-specific regulation rather than grand global architectures.
 At NANOG 96, the AI boom dominated discussions as firms race to build gigawatt-scale data centres packed with advanced GPUs, liquid cooling, and lossless networks, raising fears of overinvestment, neglected security priorities, and a looming infrastructure bubble.
At NANOG 96, the AI boom dominated discussions as firms race to build gigawatt-scale data centres packed with advanced GPUs, liquid cooling, and lossless networks, raising fears of overinvestment, neglected security priorities, and a looming infrastructure bubble.
 America has declared its intent to win the 6G race, casting next-generation wireless as vital to security and growth. Yet standards are global, vendors multinational, and the rhetoric looks like spectrum lobbying than technological rivalry.
America has declared its intent to win the 6G race, casting next-generation wireless as vital to security and growth. Yet standards are global, vendors multinational, and the rhetoric looks like spectrum lobbying than technological rivalry.
 Under ICANN's ICP-2 framework, RIR emergency operations extend beyond technical redundancy to encompass legal relocation, policy divergence and geopolitical risk, exposing tensions between operational resilience and national sovereignty in safeguarding global internet governance.
Under ICANN's ICP-2 framework, RIR emergency operations extend beyond technical redundancy to encompass legal relocation, policy divergence and geopolitical risk, exposing tensions between operational resilience and national sovereignty in safeguarding global internet governance.
 Iranians Outsmart Internet Blackout to Broadcast Airstrikes
Iranians Outsmart Internet Blackout to Broadcast Airstrikes
After US and Israeli strikes, Iran imposed a near-total internet blackout, yet citizens used satellite links and decentralized tools to share footage, undermining state control and exposing a growing contest over information in wartime. more
 Iran Expands Digital Dragnet After Crushing Protests
Iran Expands Digital Dragnet After Crushing Protests
After quelling nationwide protests, Iran has intensified its use of digital surveillance, deploying phone tracking, facial recognition and online monitoring to identify, intimidate and detain dissenters through a vast state-controlled communications infrastructure. more
 David J. Farber, Early Architect of the Internet, Dies at 91
David J. Farber, Early Architect of the Internet, Dies at 91
David J. Farber, a pioneering computer scientist and mentor to key architects of the Internet Protocol, has died at 91, leaving a legacy that helped transform isolated machines into the global network underpinning modern communication. more
Despite the long-anticipated exhaustion of IPv4 addresses, the Internet continues to function through clever workarounds, market transfers, and cautious optimism, while IPv6 adoption remains slow and the future of global connectivity appears uncertain. more
Iran is finalizing a nationwide internet isolation system that would allow authorities to disconnect from the global web, as protests continue and external equipment sources, including Huawei, remain shrouded in secrecy. more
Iran's regime has all but nullified, for the most part, Elon Musk's Starlink satellite network using advanced jamming, legal threats, and raids, turning a promising tool for protestors into a cautionary tale of digital authoritarianism. more
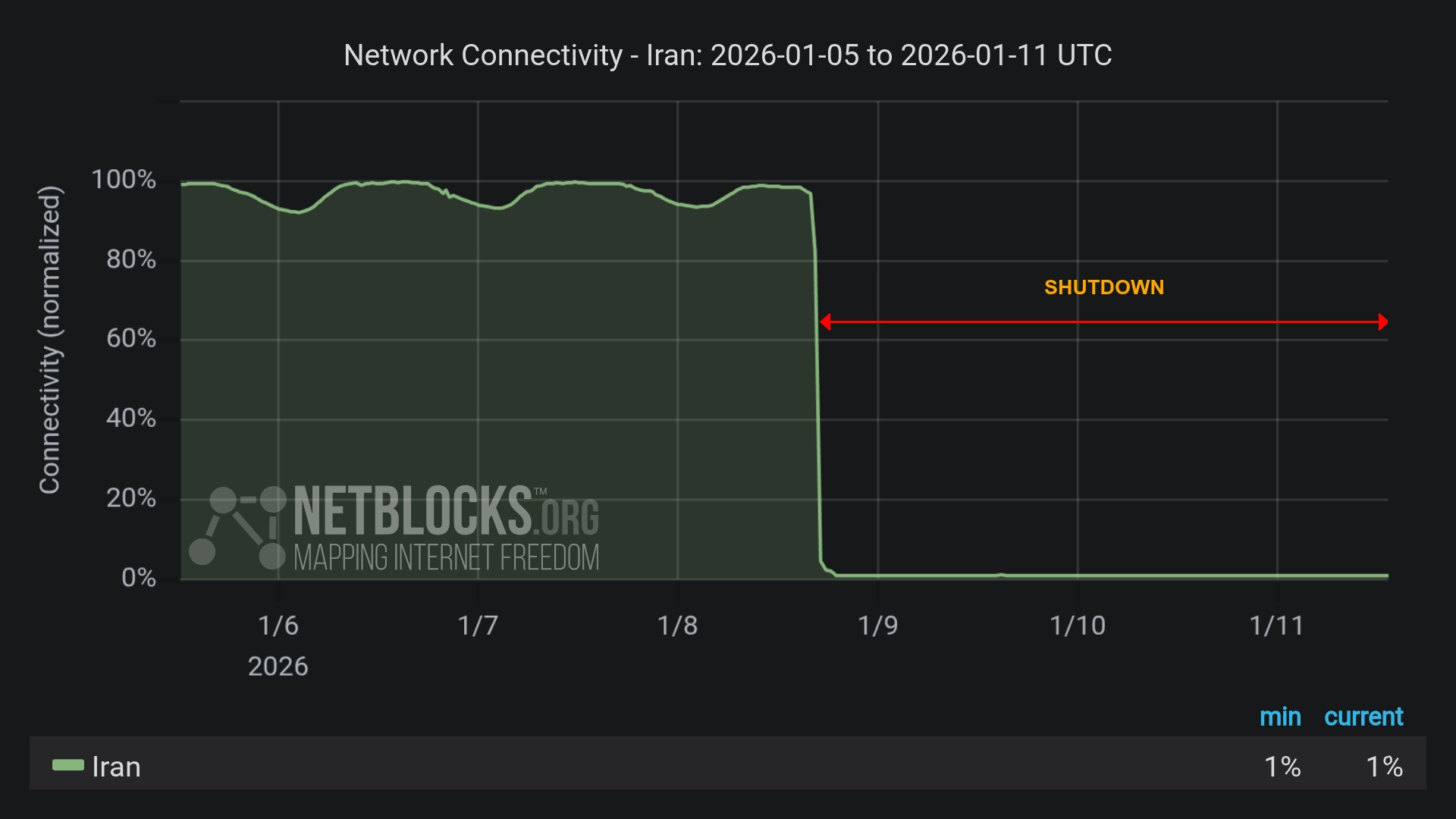 Iran Cuts Off Internet Nationwide as Regime Disrupts Even Starlink Amid Expanding Protests
Iran Cuts Off Internet Nationwide as Regime Disrupts Even Starlink Amid Expanding Protests
Iran has imposed a sweeping internet blackout amid nationwide protests, disrupting even Starlink satellite service. The move marks a new level of digital repression, raising fears of an impending crackdown shielded from global view. more
ICANN will open applications for new top-level domains in April 2026, offering brands a rare chance to secure custom domain names to enhance trust, marketing flexibility, and long-term online security. more
As AI systems take on critical roles in telecommunications, global regulatory frameworks remain outdated and fragmented, leaving essential infrastructure vulnerable to novel risks that current laws on cybersecurity and data protection fail to address. more
The NANOG 95 conference spotlighted breakthroughs in fibre optics, wireless technology, routing security, and quantum computing, offering a forward-looking assessment of internet infrastructure and its vulnerabilities, as reported by APNIC's Geoff Huston. more
AWS is introducing Route 53 Accelerated Recovery to help organizations maintain DNS control during regional outages, offering a 60-minute recovery objective and sustained access to key API operations for critical updates and traffic management. more
 US Senators Move to Shield Undersea Internet Cables from Global Threats
US Senators Move to Shield Undersea Internet Cables from Global Threats
A bipartisan Senate bill seeks to strengthen U.S. oversight and global coordination to protect undersea fiber-optic cables, vital infrastructure increasingly targeted by geopolitical adversaries, natural disasters, and cyber or physical sabotage. more
Global eSIM connections are projected to reach 4.9 billion by 2030, driven by China's rapid adoption, new provisioning standards, and growing demand across smartphones, industrial devices, and the expanding Internet of Things ecosystem. more
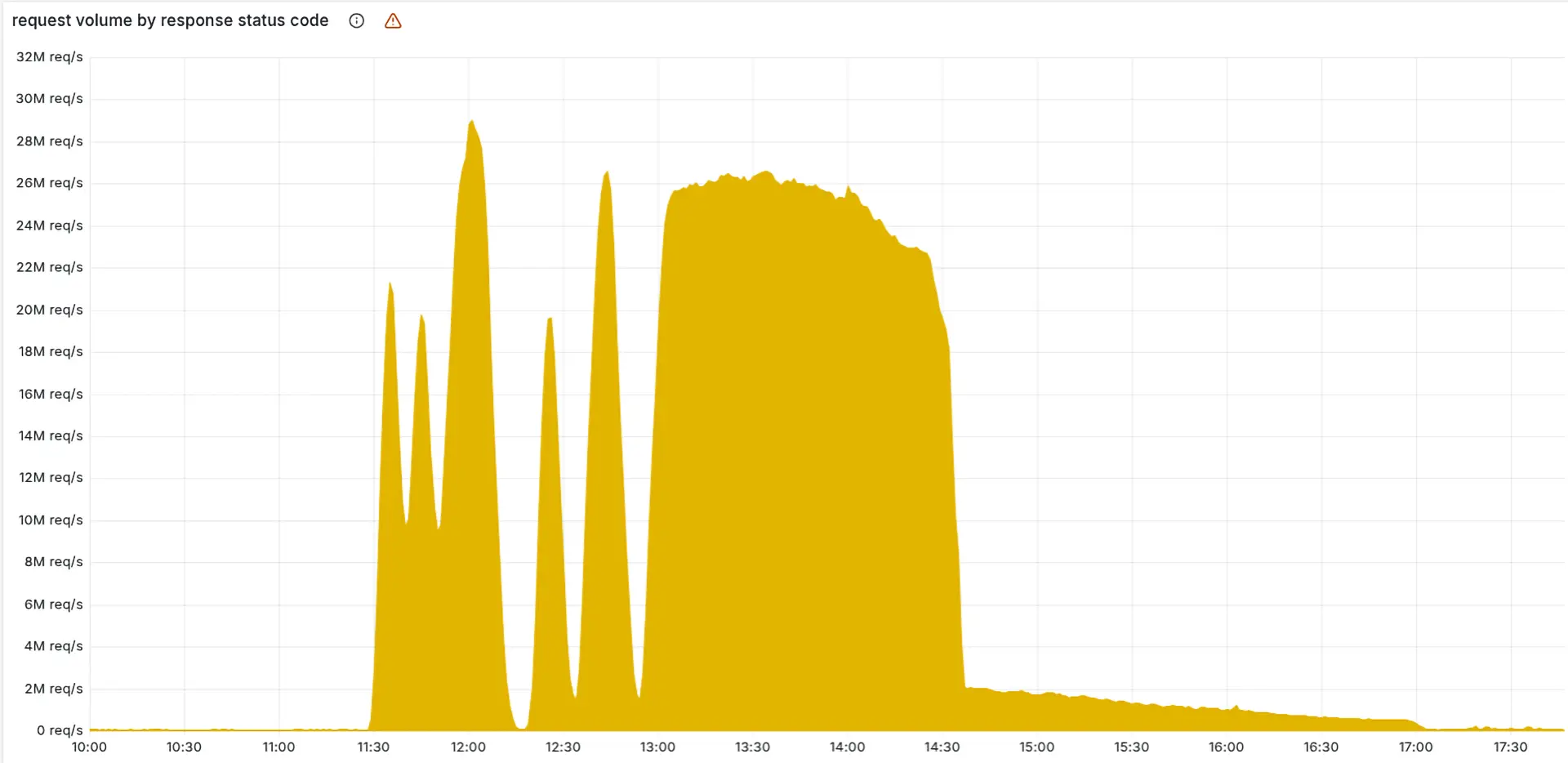 Configuration Chaos: Cloudflare Explains Major Outage in Detailed Post-Mortem
Configuration Chaos: Cloudflare Explains Major Outage in Detailed Post-Mortem
Cloudflare has detailed the cause of a global outage in a post-mortem report, revealing that a flawed internal database change -- not a cyberattack -- caused widespread service disruption across its network and customer systems. more
 Cloudflare Outage Highlights Internet’s Growing Single Points of Failure
Cloudflare Outage Highlights Internet’s Growing Single Points of Failure
Cloudflare's global outage caused cascading failures across the internet, reigniting concerns about the concentration of web infrastructure and the urgent need for more resilient, transparent systems to support critical online services. more
A Chinese-linked cyberattack exploited Anthropic's Claude AI to infiltrate global institutions with limited human input, prompting urgent calls for regulation and sparking debate over the growing autonomy of artificial intelligence in digital threats. more
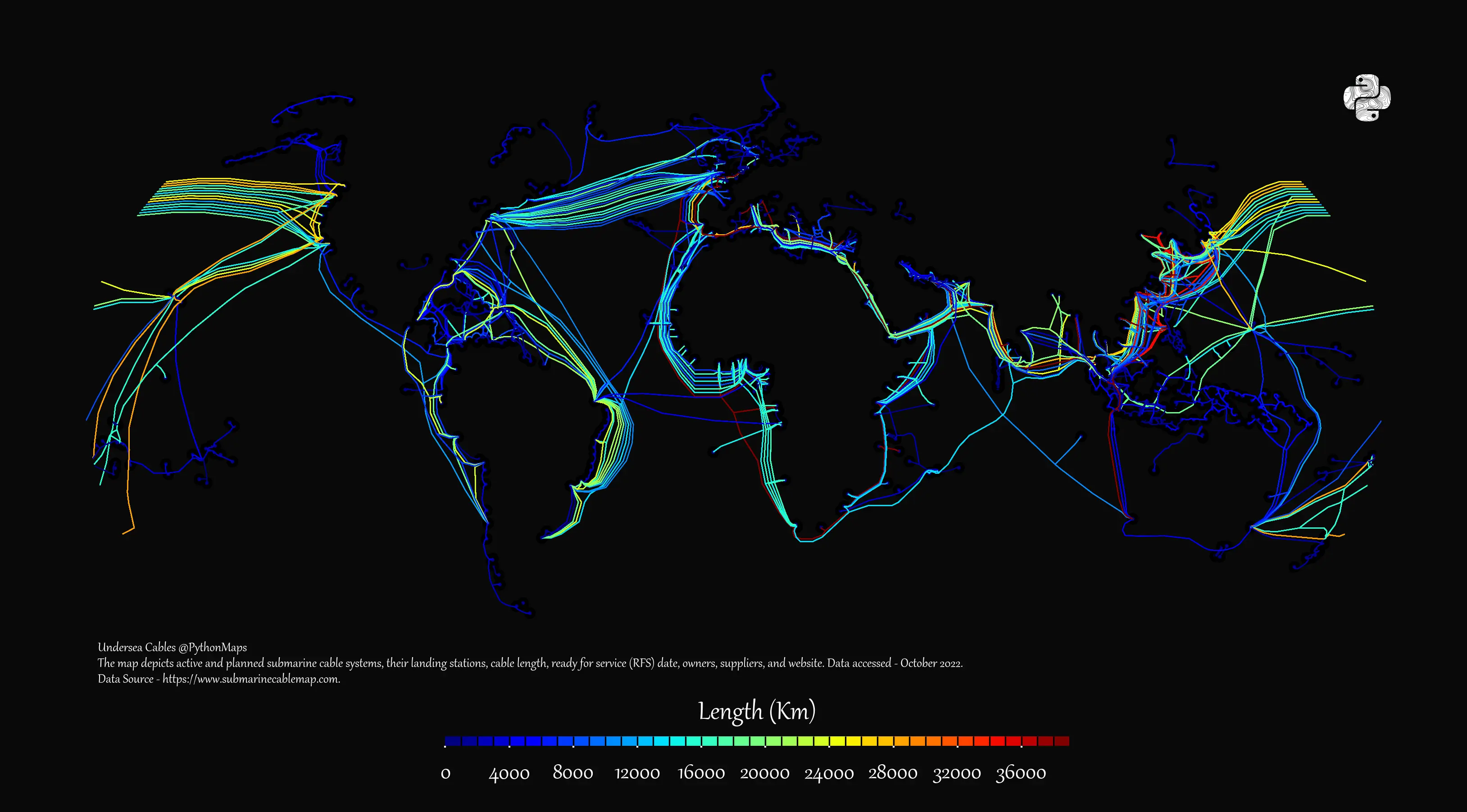 AI Boom Spurs Record Investment in Undersea Cables Amid Geopolitical and Security Concerns
AI Boom Spurs Record Investment in Undersea Cables Amid Geopolitical and Security Concerns
As AI accelerates global data demand, tech giants are investing heavily in subsea cables. These critical networks face rising geopolitical scrutiny and security risks, reshaping the future of digital infrastructure and global connectivity. more
Alice Munyua criticises ICANN's support for a proposed African internet governance overhaul, arguing it undermines multistakeholder principles and sets a dangerous precedent of political interference in global internet infrastructure. more
Google's Threat Intelligence Group reveals that hackers are integrating AI models directly into malware, enabling live code mutation, stealthier operations, and dynamic payload execution while exploiting AI tools through deceptive prompts and underground marketplaces. more
 Verizon and AWS Expand Network Ties to Meet AI Data Demands
Verizon and AWS Expand Network Ties to Meet AI Data Demands
Verizon and AWS have deepened their collaboration to build dedicated fiber infrastructure, addressing the growing need for low-latency, high-capacity connectivity to support the rapid expansion of enterprise-scale artificial intelligence workloads. more
China is revising its cybersecurity laws to include faster reporting requirements and stricter oversight of AI-related incidents, reflecting growing concerns about national security and the unchecked expansion of digital infrastructure. more
A new IETF draft outlines critical limitations of DNS in supporting the Internet of Autonomous Things, highlighting challenges related to latency, mobility, security, and privacy, and proposing architectural improvements to meet evolving machine-driven demands. more
 Starlink Passes 10,000 Satellites, Expanding Global Internet Reach
Starlink Passes 10,000 Satellites, Expanding Global Internet Reach
SpaceX has launched over 10,000 Starlink satellites, solidifying its lead in low-Earth orbit internet infrastructure and accelerating a broader industry shift toward satellite-based broadband in underserved and remote regions worldwide. more
 Massive AWS Outage Disrupts Global Internet, Services Restored After DNS Failure
Massive AWS Outage Disrupts Global Internet, Services Restored After DNS Failure
A major Amazon Web Services outage briefly disrupted millions of websites, apps, and smart devices worldwide. The DNS-related failure exposed the internet's heavy dependence on a few cloud providers before full recovery was achieved. more
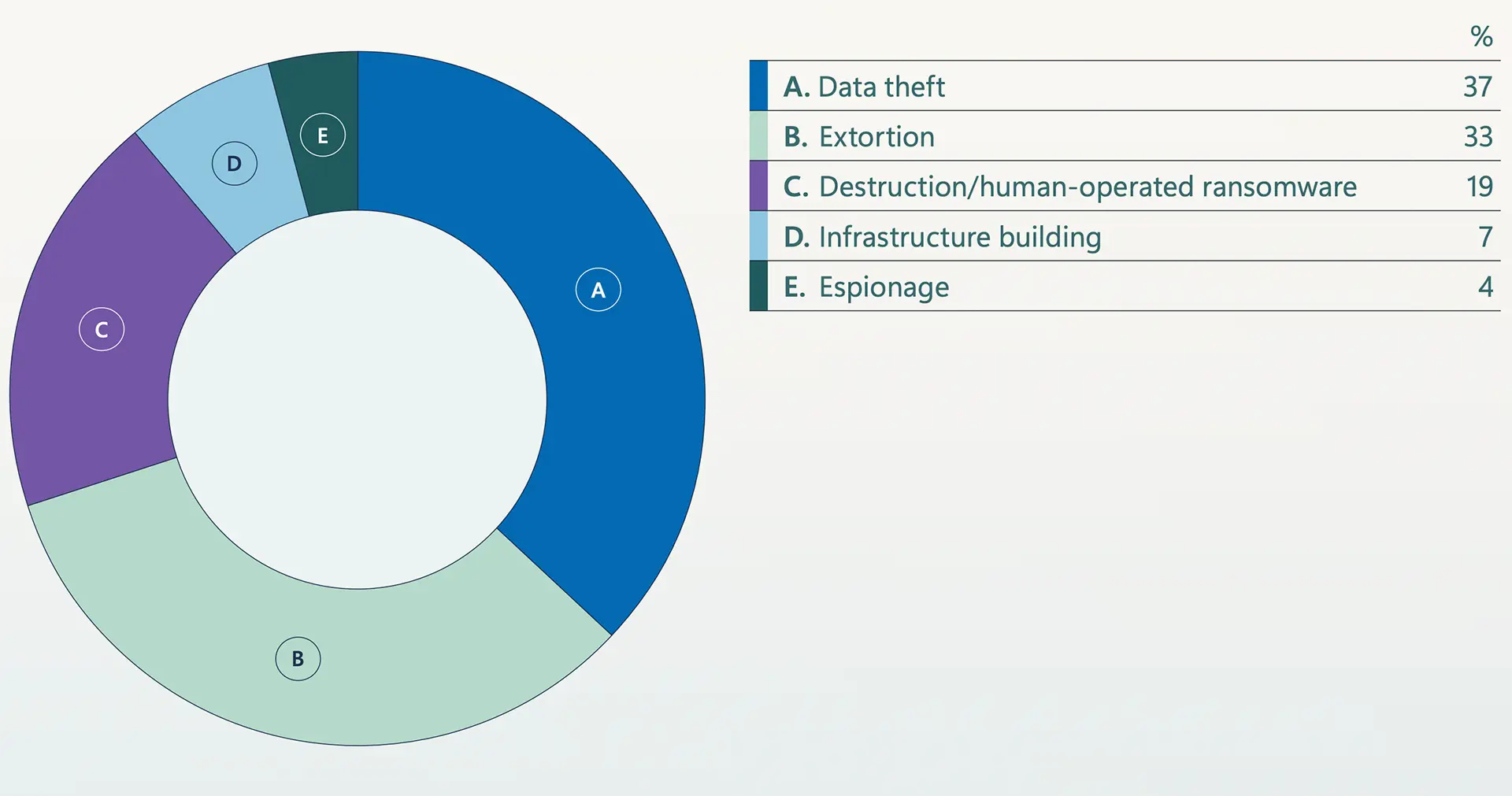 Microsoft Warns Extortion Drives Majority of Attacks Amid AI Escalation, Identity Collapse, and Global Fragmentation
Microsoft Warns Extortion Drives Majority of Attacks Amid AI Escalation, Identity Collapse, and Global Fragmentation
Microsoft's latest Digital Defense Report reveals how cybercriminals and nation-states are rapidly adopting AI to enhance attacks. With identity-based threats soaring, the company urges urgent modernization of security systems and global cooperation. more
Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byCSC

Sponsored byDNIB.com

Sponsored byRadix

 As authorities pursue Black Basta's alleged leader, new analysis of campaign indicators reveals sprawling infrastructure, thousands of linked domains, and persistent ransomware tactics that rely on phishing, known vulnerabilities, and double-extortion pressure. more
As authorities pursue Black Basta's alleged leader, new analysis of campaign indicators reveals sprawling infrastructure, thousands of linked domains, and persistent ransomware tactics that rely on phishing, known vulnerabilities, and double-extortion pressure. more
 An analysis of 46 DNS indicators tied to seven of Q4 2025's most prevalent malware families reveals early warning signals, coordinated campaigns and hundreds of connected artifacts, underscoring the predictive power of proactive threat intelligence. more
An analysis of 46 DNS indicators tied to seven of Q4 2025's most prevalent malware families reveals early warning signals, coordinated campaigns and hundreds of connected artifacts, underscoring the predictive power of proactive threat intelligence. more
 Radix reports a 96% surge in premium domain registrations in H2 2025, with strong renewal rates and rising demand across price tiers signalling that high-value digital assets are becoming core, long-term brand infrastructure. more
Radix reports a 96% surge in premium domain registrations in H2 2025, with strong renewal rates and rising demand across price tiers signalling that high-value digital assets are becoming core, long-term brand infrastructure. more
 As networks grow faster and more interconnected in 2026, they are also becoming more opaque and fragile, as outsourcing, blurred accountability and AI-driven threats expose deep weaknesses beneath expanding digital infrastructure. more
As networks grow faster and more interconnected in 2026, they are also becoming more opaque and fragile, as outsourcing, blurred accountability and AI-driven threats expose deep weaknesses beneath expanding digital infrastructure. more
 A sprawling ransomware campaign targeting Salesforce's SaaS supply chain topped 2025's breach rankings, exposing millions of records. Fresh DNS analysis uncovered 8,318 linked artifacts, revealing how overlooked indicators foreshadowed widespread, multisector disruption. more
A sprawling ransomware campaign targeting Salesforce's SaaS supply chain topped 2025's breach rankings, exposing millions of records. Fresh DNS analysis uncovered 8,318 linked artifacts, revealing how overlooked indicators foreshadowed widespread, multisector disruption. more
 As SSL lifecycles shrink and low-cost certificates proliferate, enterprises face mounting operational and security risks. A fragmented, manual approach is no longer sustainable; automation, vendor consolidation and stronger validation are becoming strategic imperatives. more
As SSL lifecycles shrink and low-cost certificates proliferate, enterprises face mounting operational and security risks. A fragmented, manual approach is no longer sustainable; automation, vendor consolidation and stronger validation are becoming strategic imperatives. more
 An IoC deep dive into QakBot, newly ranked among 2026's top malware threats, reveals sprawling infrastructure, recycled domains, and fresh artifacts, underscoring how phishing-led access campaigns continue to endanger email-reliant enterprises worldwide. more
An IoC deep dive into QakBot, newly ranked among 2026's top malware threats, reveals sprawling infrastructure, recycled domains, and fresh artifacts, underscoring how phishing-led access campaigns continue to endanger email-reliant enterprises worldwide. more
 As generative AI accelerates deepfakes, counterfeit domains, and brand impersonation, legal teams are struggling to keep pace. Detection speed has become critical, forcing companies into an AI-driven arms race to protect intellectual property and corporate trust. more
As generative AI accelerates deepfakes, counterfeit domains, and brand impersonation, legal teams are struggling to keep pace. Detection speed has become critical, forcing companies into an AI-driven arms race to protect intellectual property and corporate trust. more
 The fourth quarter of 2025 closed with 386.9 million domain name registrations across all top-level domains (TLDs), an increase of 22.7 million domain name registrations compared to the fourth quarter of 2024, according to the latest issue of the Domain Name Industry Brief Quarterly Report released Thursday at DNIB.com. more
The fourth quarter of 2025 closed with 386.9 million domain name registrations across all top-level domains (TLDs), an increase of 22.7 million domain name registrations compared to the fourth quarter of 2024, according to the latest issue of the Domain Name Industry Brief Quarterly Report released Thursday at DNIB.com. more
 In 2025, IPv4 address prices declined to decade lows, but market activity remained strong. Rising buyer participation and steady transaction volume signaled a resilient, well-functioning market entering 2026 with confidence. more
In 2025, IPv4 address prices declined to decade lows, but market activity remained strong. Rising buyer participation and steady transaction volume signaled a resilient, well-functioning market entering 2026 with confidence. more
What is a Dedicated IP VPN? A Dedicated IP VPN is a Virtual Private Network (VPN) service that provides users with a unique, static IP address assigned exclusively to them. Unlike a shared IP address, which is used by multiple users simultaneously, a dedicated IP is reserved for a single user, offering greater control and security over their online activities. more
Starlink provides high-speed, low-latency satellite internet, making it ideal for rural and remote areas lacking traditional broadband. Installation is user-friendly, and coverage continues to expand globally. However, the service is relatively expensive, and performance can be impacted by adverse weather. Overall, Starlink is a reliable choice for those without access to conventional internet options. more
ISPs can see that you are using a VPN, as they can detect encrypted traffic and the IP address of the VPN server. However, they cannot see the content of your data or the websites you visit while the VPN is active because the data is encrypted. This provides privacy for your online activities, though the fact that you're using a VPN itself is visible to the ISP. more
Satellite internet is a broadband service that connects users via signals transmitted between orbiting satellites and a satellite dish at the user's location. Unlike fiber or cable, it doesn't require physical infrastructure, making it essential in rural and remote areas. Although historically slower with higher latency, advancements like Low Earth Orbit (LEO) satellites have improved speed and reduced delays, enhancing overall performance. more
Yes, NordVPN still works with Netflix in 2024. It effectively bypasses geo-restrictions, unlocking libraries from major regions like the U.S., UK, Japan, and more. However, occasional issues like blocked servers or slow connections may arise. Troubleshooting, such as switching servers or using SmartPlay, typically resolves problems and maintains reliable access to Netflix. more
NordVPN offers two ways to try the service risk-free: a 7-day free trial for Android users and a 30-day money-back guarantee for all users. Both options allow full access to NordVPN's premium features. The trial requires payment details but can be canceled before charges occur. NordVPN provides superior security, performance, and global content access compared to free alternatives. more
NordVPN stands out for its unique double encryption, adding an extra layer of privacy. With blazing-fast servers in 60 countries, it's perfect for streaming, gaming, and bypassing geo-blocks. Its strict no-logs policy and advanced features like CyberSec ad-blocker make it a top choice for anyone seeking strong security and seamless performance. more
The best countries for VPN server locations include Switzerland, Iceland, and Panama for privacy, Germany, Japan, and the United States for fast connections, and the U.S., U.K., and Canada for streaming. These countries offer strong privacy laws, advanced infrastructure, and optimal performance for various online activities. more
VPNs are critical for remote work because they secure data by encrypting internet connections, protecting sensitive company information from cyberattacks. They also enable remote access to company networks, ensuring employees can work safely from any location while maintaining privacy and compliance with security policies. more
A VPN protects you by encrypting your internet connection, hiding your IP address, and routing your data through a secure server. This shields your online activities from hackers, trackers, and surveillance, ensuring privacy and security, especially on public Wi-Fi or when accessing sensitive information. more