


|
||
|
||
Nearly 1 million individuals’ information was stolen and exposed when threat actors launched a BlackSuit ransomware attack on 10 April 2024. The investigation revealed that the compromised data included the victims’ Social Security numbers (SSNs), birthdays, and insurance claim information.
Data breach notifications were sent in the last week of August. Around that time, specifically on 27 August 2024, the Cybersecurity and Infrastructure Security Agency (CISA) also updated its BlackSuit ransomware advisory. Their latest STIX file contains 91 indicators of compromise (IoCs) comprising 14 domain names, five subdomains, and 72 IP addresses. The agency also revealed that Blacksuit is a rebranded version of the Royal ransomware, a threat group that targeted healthcare organizations and demanded ransom payments ranging from US$250,000 to US$2 million.
The WhoisXML API research team pivoted off these cyber resources to expand the list of IoCs and uncover relevant threat artifacts. The analysis led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
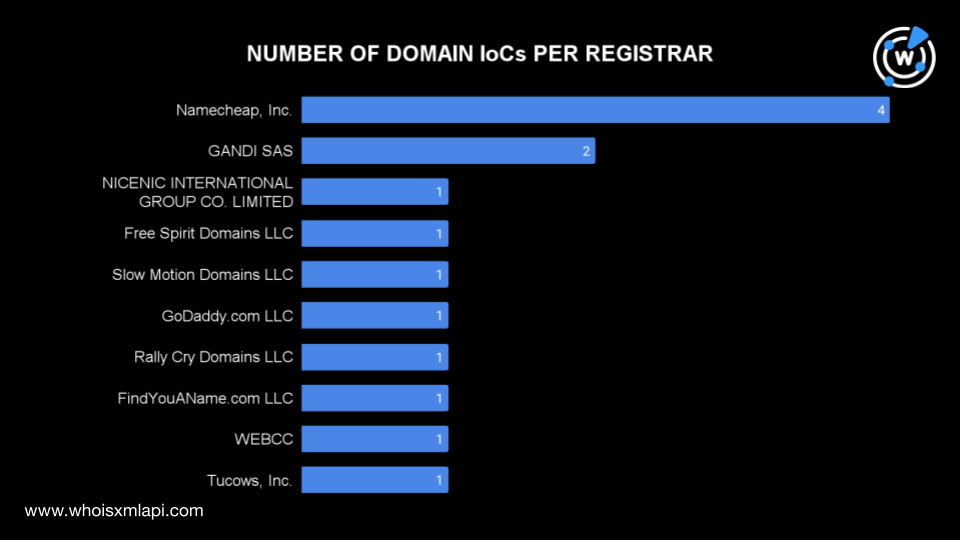
To learn more about the published IoCs, we first ran the 15 domains, comprising the 14 domain names identified as IoCs and one domain extracted from the subdomain IoCs, on Bulk WHOIS Lookup. We found that one domain IoC did not have current WHOIS data and thus was excluded from the analysis.
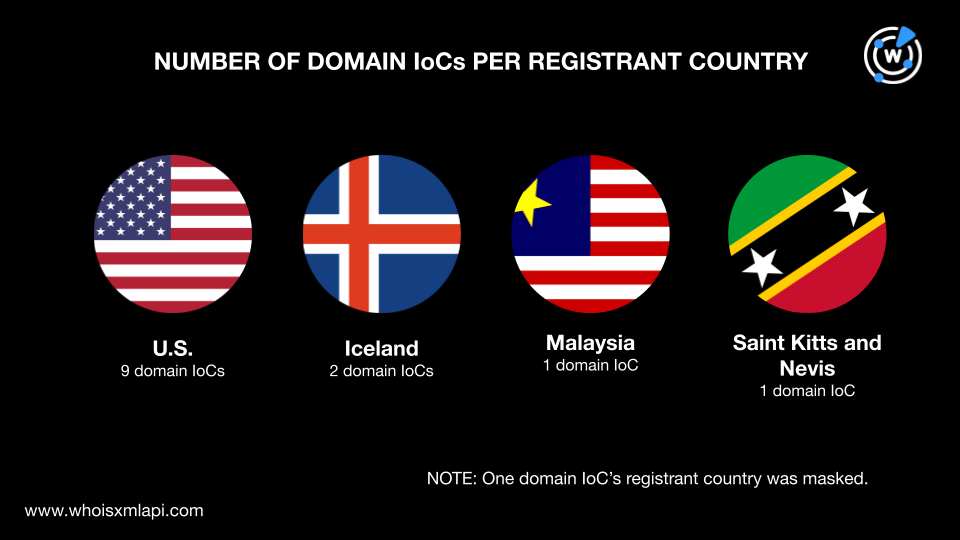
Nine domain IoCs were registered in the U.S. and two in Iceland. Malaysia and Saint Kitts and Nevis accounted for one domain IoC each.
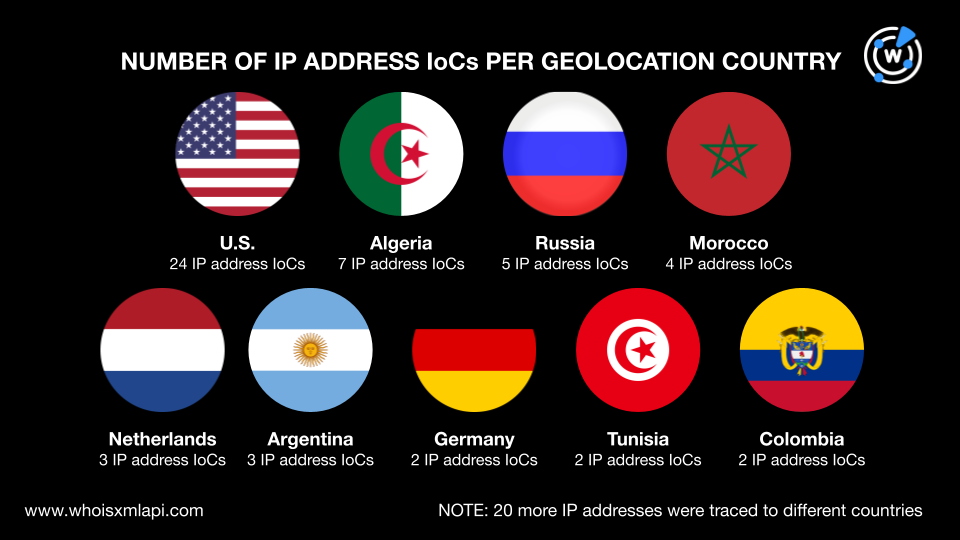
Next, we ran a bulk IP geolocation lookup for the 72 IP addresses identified as IoCs and found that:
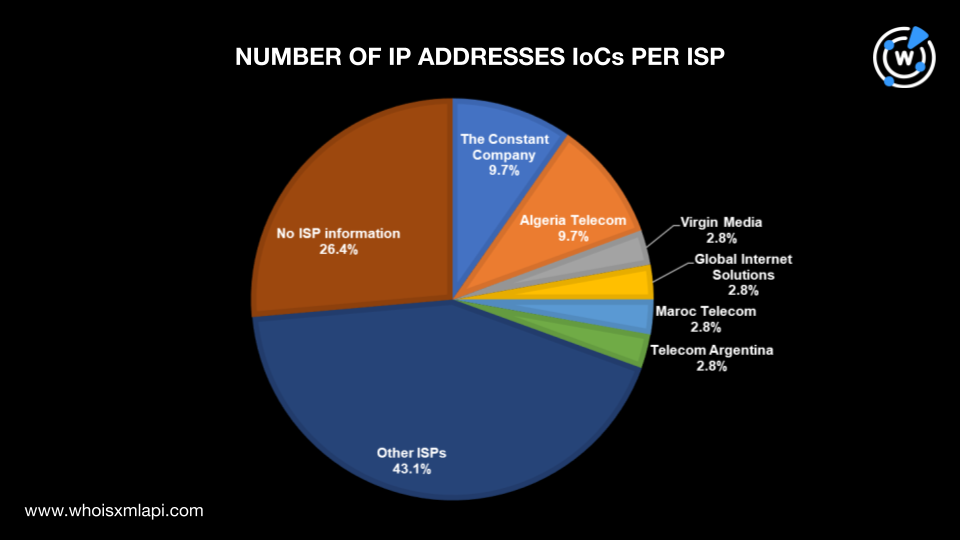
The Constant Company and Algeria Telecom administered seven IP addresses each, while Virgin Media, Global Internet Solutions, Maroc Telecom, and Telecom Argentina administered two IP addresses each. Thirty-one other ISPs accounted for one IP address IoC each, while 19 IP addresses did not have current ISP information.
To proactively hunt for potential BlackSuit-related threats, we queried the 14 domain IoCs and one subdomain IoC root domain on WHOIS History API. The results showed that they had 31 email addresses in their historical WHOIS records, five of which were public.
Jumping off the five public email addresses, our Reverse WHOIS API queries led to the discovery of 112 email-connected domains after removing duplicates and the IoCs.
We then ran the 14 domain IoCs and five subdomain IoCs on DNS Lookup and found out that while four did not have active IP resolutions, the remaining 15 resolved to 10 IP addresses not on the original IoC list.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byDNIB.com

Sponsored byCSC

Sponsored byIPv4.Global

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byVerisign

Sponsored byRadix
