


|
||
|
||
Remote access trojans (RATs) can be considered the malware of choice by the world’s most notorious advanced persistent threat (APT) groups. And there’s a good reason for that. They are hard to detect, making them ideal for lateral movement, and also difficult to get rid of.
Talos recently published a detailed analysis of one such tool dubbed “NetSupport RAT.” This particular RAT is a weaponized version of NetSupport Manager, a legitimate remote device administration tool that has been commercially available since 1989. Its malicious counterpart, on the other hand, has been around since 2023. To date, NetSupport RAT has been used in at least two massive campaigns.
Since then, security researchers have been tracking the RAT’s development and latest activities. An in-depth analysis of the tool involved in the latest campaign identified nine domain names as indicators of compromise (IoCs).
The WhoisXML API research team expanded the list of IoCs to identify other potentially connected artifacts, namely:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
As is our usual first step, we sought to find more information about the IoCs security researchers have already identified, specifically nine domain names.
A bulk WHOIS lookup for the nine domain IoCs revealed that:
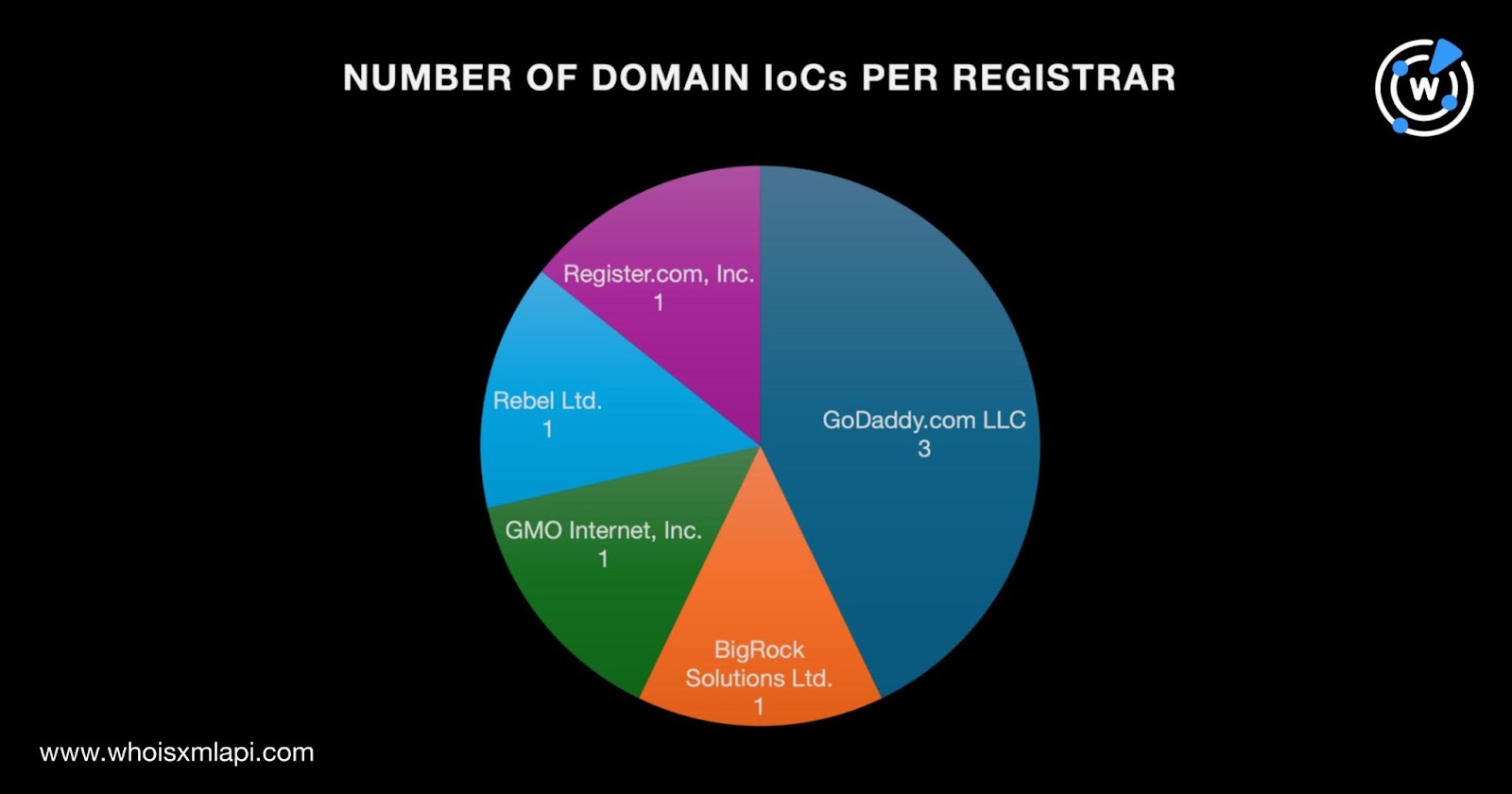
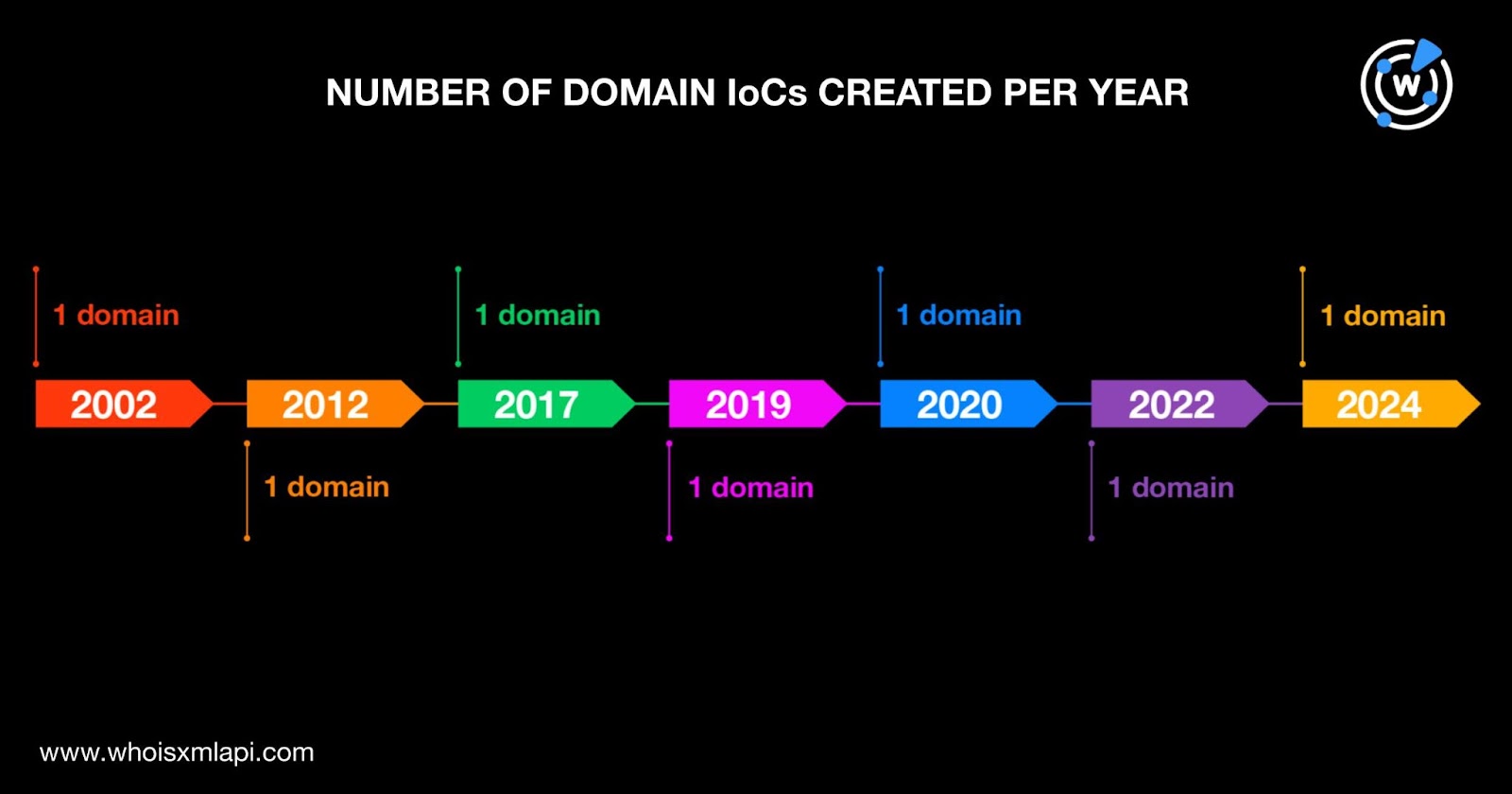
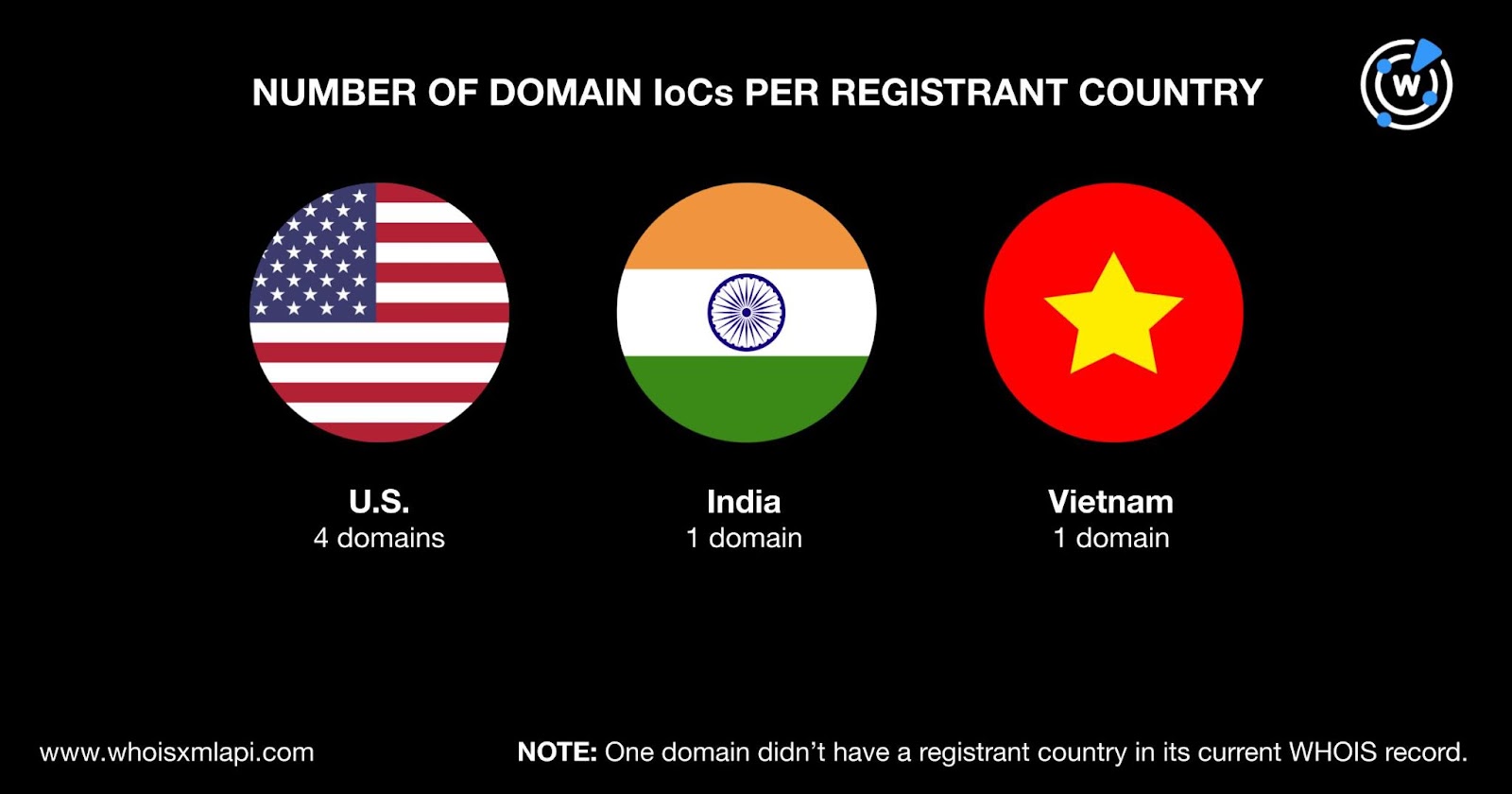
We began our hunt for connected artifacts by querying the seven domain IoCs on WHOIS History API. That led to the discovery of 12 email addresses in their historical WHOIS records after filtering out duplicates. Four were public email addresses.
Querying the four public email addresses on Reverse WHOIS API came next. The step revealed that only three of them appeared in the current WHOIS records of other domains. Specifically, we uncovered 17 email-connected domains after we filtered out duplicates and the IoCs.
To see if there were other email-connected domains, we queried the four public email addresses this time using Reverse WHOIS Search on the Domain Research Suite (DRS). That enabled us to find 222 domains whose historical WHOIS records contained the email addresses. Note that the number excluded duplicates, the IoCs, and the domains with the email addresses in their current WHOIS records.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byRadix

Sponsored byCSC

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byDNIB.com
