


|
||
|
||
The Earth Minotaur threat group recently revived the MOONSHINE exploit kit, first discovered in 2019.
According to Trend Micro’s in-depth analysis, MOONSHINE had more than 55 servers in 2024 and has been updated with more exploits and functions compared with its 2019 version. Apart from targeting vulnerable instant messaging apps on Android devices, it also affects Chromium-based browsers installed on Windows computers. DarkNimbus, the backdoor MOONSHINE delivered, also had two variants that affected both Android and Windows devices. These facts point to making the latest Earth Minotaur attack a multiplatform threat.
The researchers identified 53 indicators of compromise (IoCs) associated with the attack comprising 44 domains extracted from URLs and nine IP addresses. The WhoisXML API research team expanded the list of IoCs and uncovered additional threat artifacts, including:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
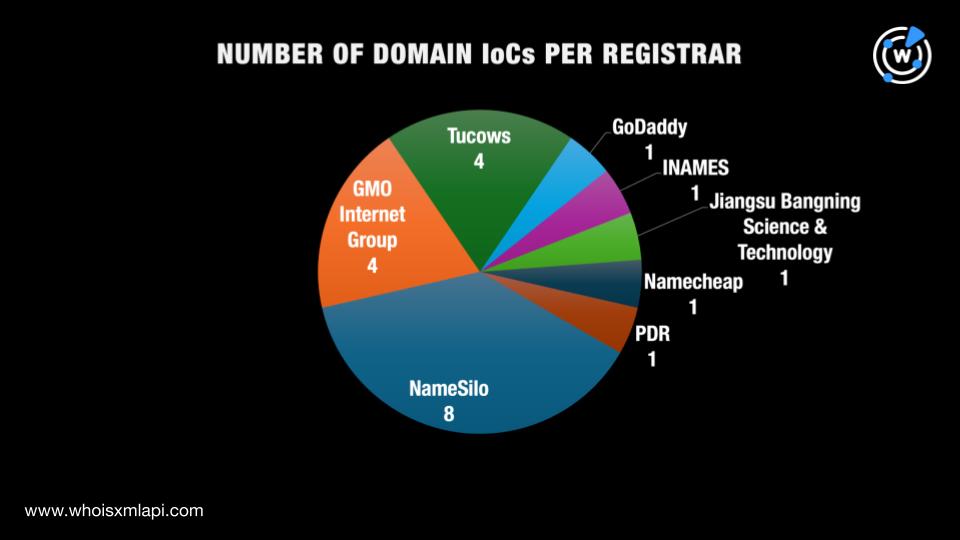
As our usual first step, we queried the 44 domains tagged as IoCs on WHOIS API and found that only 21 had current WHOIS records. Here’s a breakdown of their record details.
They were created between 2003 and 2024. Specifically, one domain each was created in 2003 and 2020, six in 2023, and 13 in 2024.

Only 19 domains had registrant countries. Ten were registered in the U.S., four in Japan, two in Saint Kitts and Nevis, and one each in Canada, China, and South Korea.

A DNS Chronicle API query for the 44 domains tagged as IoCs revealed that only 32 had historical IP resolutions. Altogether, they posted 371 IP resolutions over time. The IoC tibetonline[.]info recorded the earliest IP resolution date—13 October 2019. The following table shows the total number of IP resolutions and first and last IP resolution start dates for five other domain IoCs.
| DOMAIN IoC | TOTAL NUMBER OF IP RESOLUTIONS | FIRST IP RESOLUTION START DATE | LAST IP RESOLUTION START DATE |
|---|---|---|---|
| ansec[.]com | 43 | 18 October 2019 | 3 December 2024 |
| cloudvn[.]info | 38 | 29 August 2020 | 19 December 2024 |
| symantke[.]com | 29 | 8 May 2022 | 15 August 2024 |
| lodepot[.]com | 27 | 29 September 2021 | 12 December 2024 |
| ammffggo[.]com | 24 | 19 November 2021 | 2 June 2023 |
We then queried the nine IP addresses tagged as IoCs on Bulk IP Geolocation Lookup and found that:

Only eight had ISPs on record. They were administered by six ISPs led by Alibaba and China Telecom, which accounted for two IP addresses each. The four remaining IoCs were administered by BGP Network, China Mobile, RAKsmart, and Simcentric Solutions.

Our DNS Chronicle API query for the nine IP addresses tagged as IoCs revealed that only three had historical domain resolutions. Altogether, they posted 78 domain resolutions over time. The IP address 103[.]255[.]179[.]186 recorded the first domain resolution date—7 October 2019. The IoC 125[.]65[.]40[.]163, meanwhile, recorded a single first domain resolution date—11 November 2019.
We began our search for connected threat artifacts by querying the 44 domains tagged as IoCs on WHOIS History API and found that 35 of them had 64 email addresses in their historical WHOIS records. Nineteen were public email addresses.
A Reverse WHOIS API query for the 19 public email addresses showed that three could belong to domainers, while nine did not have other domain connections. The seven remaining public email addresses appeared in the current WHOIS records of 333 other domains after duplicates and those already identified as IoCs were filtered out.
Next, we queried the 44 domains tagged as IoCs on DNS Lookup API and found that seven actively resolved to eight IP addresses after duplicates and those already identified as IoCs were filtered out.
Threat Intelligence API queries for the eight additional IP addresses revealed that they were all malicious.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byVerisign

Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byCSC

Sponsored byWhoisXML API

Sponsored byDNIB.com
