


|
||
|
||
MITRE has named nine new groups, responsible for attacks related to the most abused vulnerabilities from August to October 2025. They identified six Enterprise groups, two Mobile groups, and one ICS group.
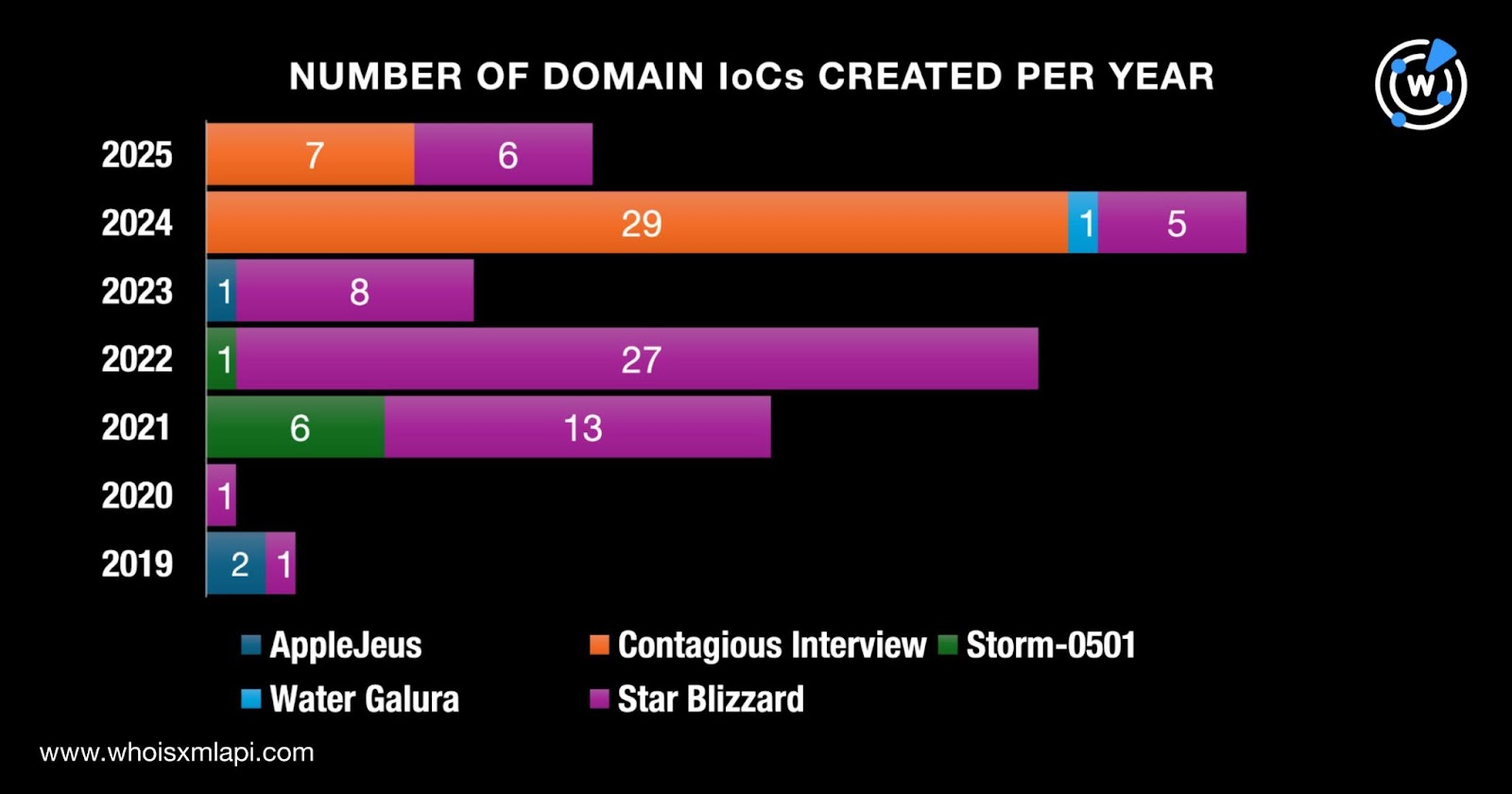
We compiled 126 domains as IoCs for five groups—AppleJeus, Contagious Interview, Storm-0501, Water Galura, and Star Blizzard. However, upon further checking via the WhoisXML API MCP Server, only 108 of the domains identified as IoCs were deemed suspicious or outright malicious. Take a look at more details below.
| GROUP | NUMBER OF ORIGINAL DOMAIN IoCs | NUMBER OF IoCs ANALYZED |
|---|---|---|
| AppleJeus | 4 | 3 |
| Contagious Interview | 39 | 36 |
| Storm-0501 | 13 | 7 |
| Water Galura | 1 | 1 |
| Star Blizzard | 69 | 61 |
We limited our investigation to these domains, along with the 31 IP addresses tagged as IoCs for four groups (UNC3886, Water Galura, MuddyWater, and the Lazarus Group) and five email addresses for the Medusa Group.
Our in-depth analysis led to these discoveries:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our investigation by looking more closely at the 108 domains, 31 IP addresses, and five email addresses identified as IoCs. Here are more details on the number of IoCs per group.
| GROUP | NUMBER OF DOMAIN IoCs | NUMBER OF IP IoCs | NUMBER OF EMAIL IoCs |
|---|---|---|---|
| AppleJeus | 3 | 0 | 0 |
| Contagious Interview | 36 | 0 | 0 |
| Medusa Group | 0 | 0 | 5 |
| Storm-0501 | 7 | 0 | 0 |
| UNC3886 | 0 | 8 | 0 |
| Water Galura | 1 | 5 | 0 |
| MuddyWater | 0 | 3 | 0 |
| Star Blizzard | 61 | 0 | 0 |
| Lazarus Group | 0 | 15 | 0 |
| TOTAL | 108 | 31 | 5 |
First, we consulted First Watch Malicious Domains Data Feed, to determine if any of the 108 domains identified as IoCs were deemed likely to turn malicious upon registration. Two domains connected to Contagious Interview appeared on the feed 10 days before being dubbed as IoCs. Take a look at more details below.
| DOMAIN IoC | FIRST WATCH DATE | REPORTING DATE | NUMBER OF DAYS DEEMED MALICIOUS PRIOR TO REPORTING |
|---|---|---|---|
| complexassess[.]com | 6 January 2025 | 16 January 2025 | 10 |
| intro-crypto-assess[.]com | 6 January 2025 | 16 January 2025 | 10 |
Next, we queried the 108 domains identified as IoCs on WHOIS API, and Domain Info API, and found out that:
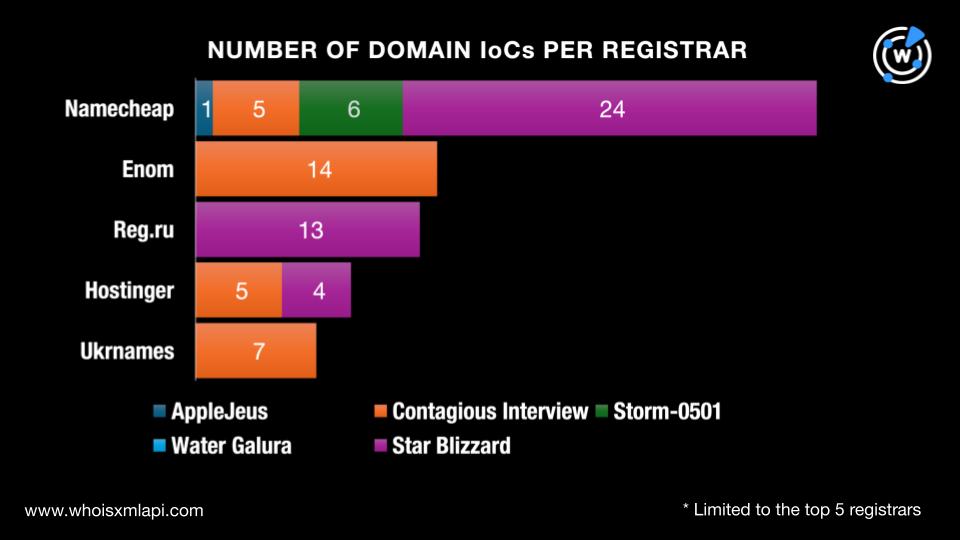
They were split among 23 registrars topped by Namecheap, which accounted for 36 domains. Enom took second place with 14 domains, followed by Reg.ru with 13. Take a look at the breakdown by group below.
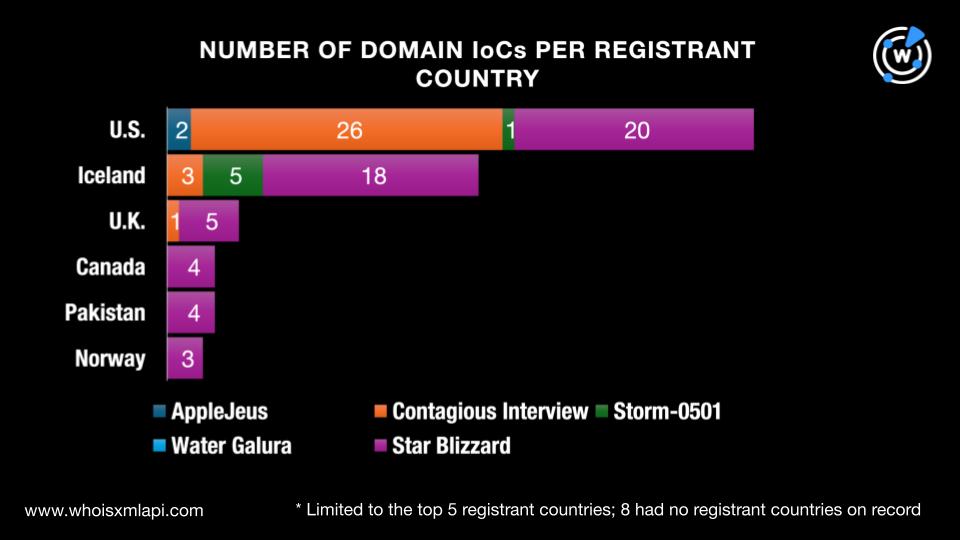
While eight domains did not have registrant countries on record, the remaining 100 were registered in 12 countries. The top 3 countries were the U.S. with 49 domains, Iceland with 26, and the U.K. with six. Here is a detailed breakdown per group.
A DNS Chronicle API, query for the 108 domains identified as IoCs showed that 97 had historical domain-to-IP resolutions. Together, they posted 2,022 resolutions over time starting on 5 February 2017 (i.e., recorded for Star Blizzard IoC cloud-docs[.]com). Take a look at more information for five examples below.
| GROUP | DOMAIN IoC | NUMBER OF RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE |
|---|---|---|---|---|
| Star Blizzard | cloud-docs[.]com | 299 | 02/05/17 | 10/09/25 |
| Star Blizzard | doc-viewer[.]com | 15 | 06/09/17 | 07/07/17 |
| Star Blizzard | documents-cloud[.]com | 57 | 07/07/17 | 04/03/23 |
| Star Blizzard | cloud-storage[.]live | 43 | 10 December 2017 | 05/14/24 |
| Contagious Interview | vinterview[.]org | 107 | 03/12/18 | 03/07/25 |
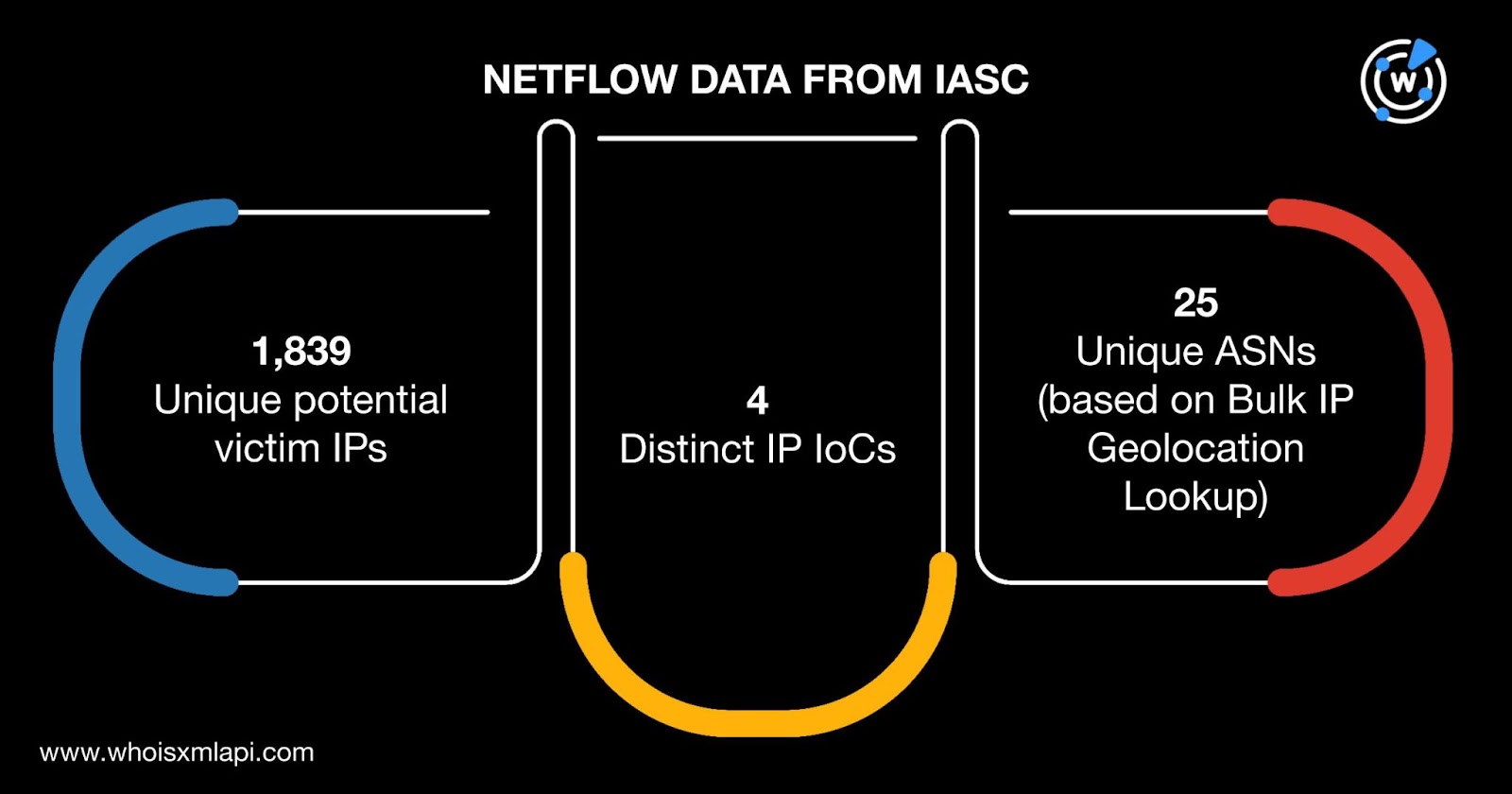
We then zoomed in on the 31 IP addresses identified as IoCs. Sample network traffic data from the IASC, revealed that from 9 September to 13 November 2025, 1,839 unique potential victim IP addresses communicated with four of them.
The 1,839 IP addresses fell under 25 ASNs according to the results of a Bulk IP Geolocation Lookup, query.
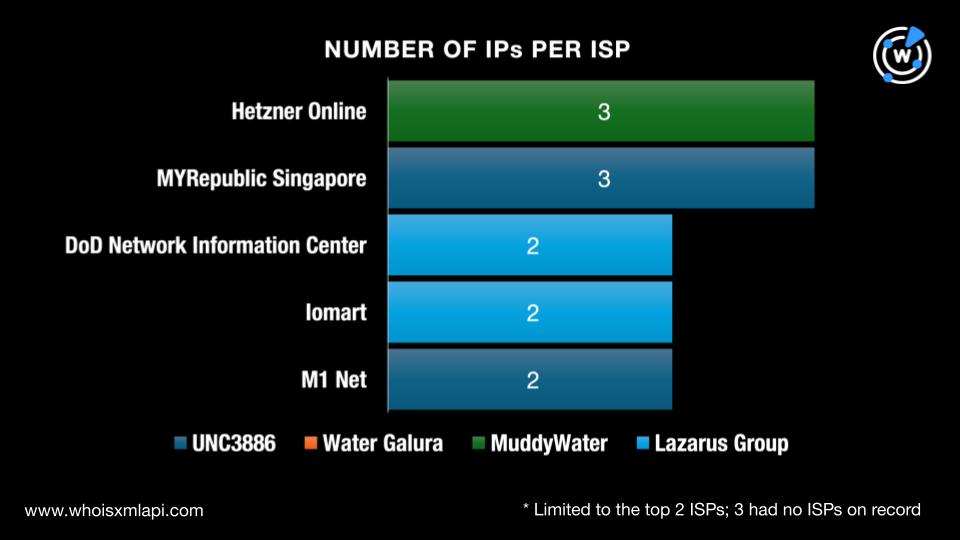
Next, we queried the 31 IP addresses identified as IoCs on Bulk IP Geolocation Lookup and found out that:
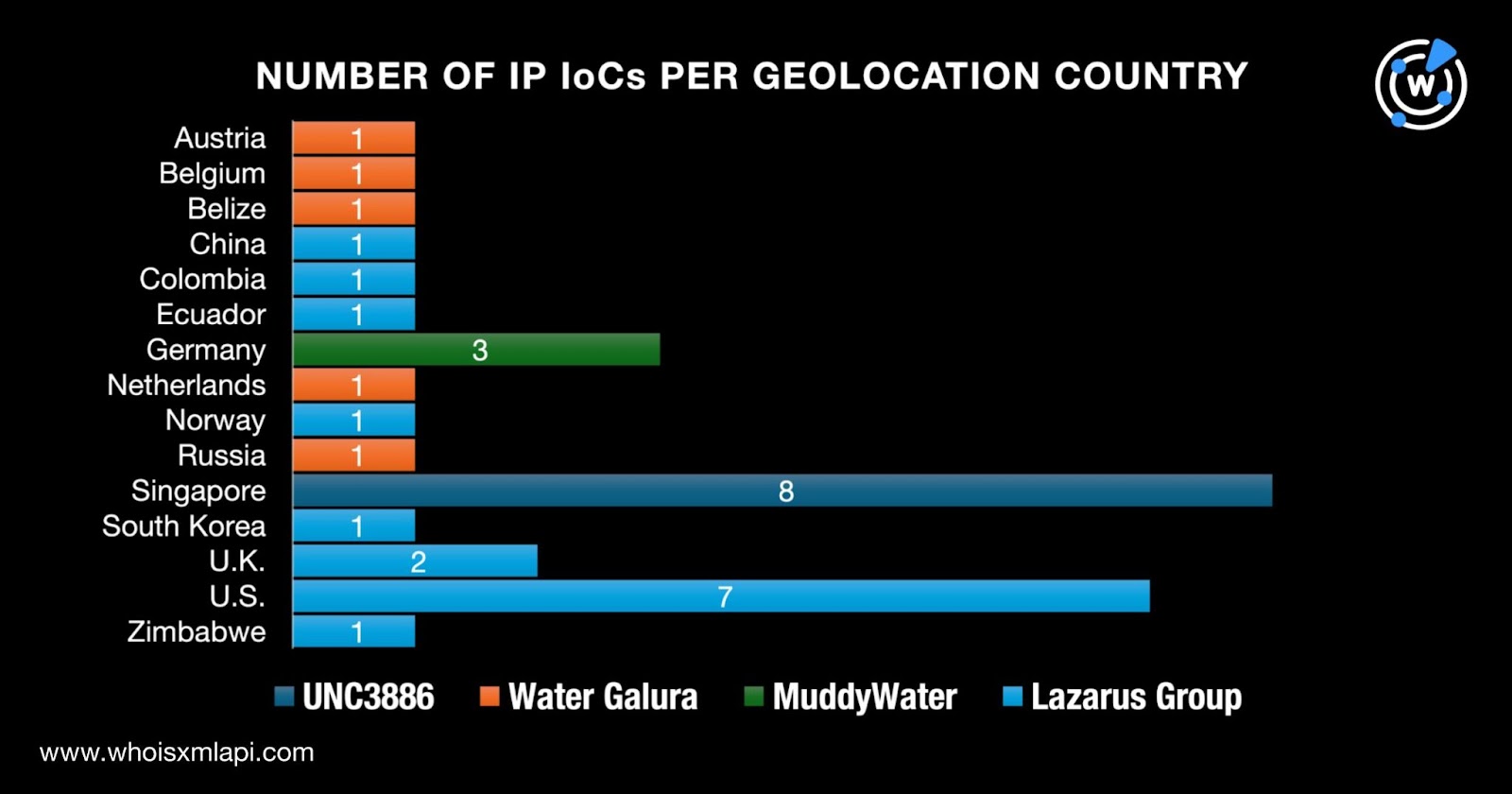
While three IP addresses did not have ISPs on record, the remaining 28 were administered by 21 ISPs. The top ISPs were Hetzner Online and MYRepublic Singapore, which tied in first place, accounting for three IP addresses each. Here is a volume breakdown by group.
A DNS Chronicle API query for the 31 IP addresses identified as IoCs revealed that 19 had historical IP-to-domain resolutions. In sum, they recorded 5,451 resolutions starting on 4 February 2017. Take a look at five examples below.
| GROUP | IP IoC | NUMBER OF RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE |
|---|---|---|---|---|
| Lazarus Group | 84[.]49[.]242[.]125 | 259 | 02/04/17 | 08/11/24 |
| MuddyWater | 148[.]251[.]204[.]131 | 1,000 | 02/05/17 | 11/22/24 |
| Lazarus Group | 112[.]175[.]92[.]57 | 3,000 | 02/05/17 | 04/28/17 |
| Lazarus Group | 128[.]200[.]115[.]228 | 258 | 02/05/17 | 08/12/24 |
| Lazarus Group | 81[.]94[.]192[.]147 | 29 | 02/06/17 | 05/20/17 |
After that, we zoomed in on the five email addresses identified as IoCs. Jake AI, checks using the prompt “What can you tell me about [email IoC]?”
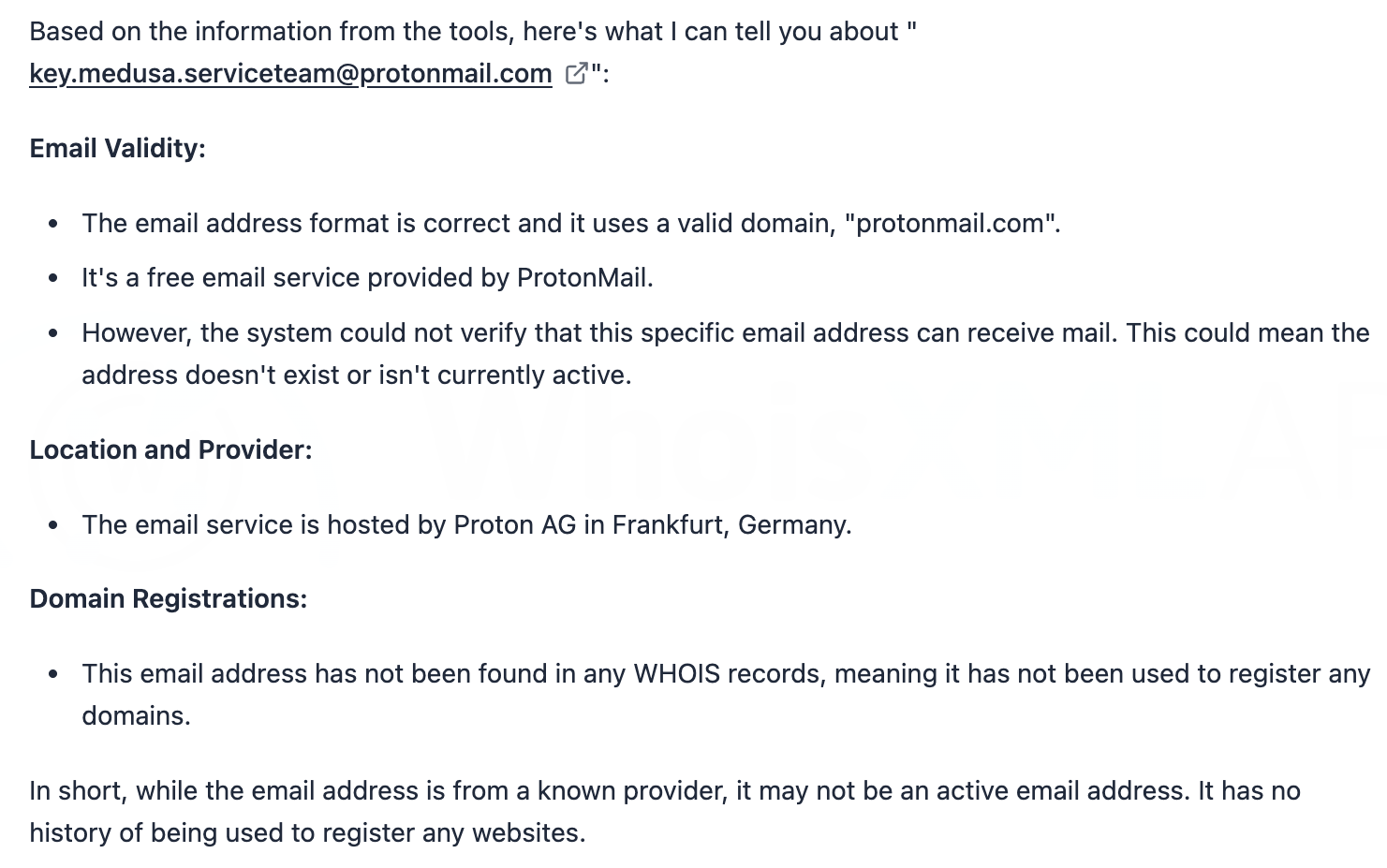
The results showed that while all five email addresses were valid, none seem to be currently active nor were used to register any domains. Take a look at the specifics below.
| EMAIL IoC | VALIDITY AND DETAILS | DOMAIN REGISTRATION USAGE |
|---|---|---|
| key[.]medusa[.]serviceteam@protonmail[.]com | Valid Free email Does not exist or inactive | Not used to register any domain |
| mds[.]svt[.]breach@protonmail[.]com | Valid Free email Does not exist or inactive | Not used to register any domain |
| mds[.]svt[.]mir2@protonmail[.]com | Valid Free email Does not exist or inactive | Not used to register any domain |
| medusa[.]support@onionmail[.]org | Valid Private email Does not exist or inactive | Not used to register any domain |
| MedusaSupport@cock[.]li | Valid Free and disposable email Does not exist or inactive | Not used to register any domain |
Given the details above, from here on out, the five email addresses identified as IoCs will not figure in the rest of our analysis.
After learning more about the IoCs, we sought to uncover new artifacts connected to the featured groups. We first queried the 108 domains identified as IoCs on WHOIS History API, and discovered that 50 had email addresses in their historical WHOIS records. We found 191 unique email addresses in all.
Upon closer examination, we identified 18 public email addresses. We queried them on Reverse WHOIS API, and found out that while none of them appeared in current WHOIS records, 11 did show up on historical WHOIS records. We were, in fact, able to gather 78 email-connected domains after duplicates and those already tagged as IoCs were filtered out.
Threat Intelligence API, queries for the 78 email-connected domains revealed that 11 have already figured in various attacks. Here are five examples.
| MALICIOUS EMAIL-CONNECTED DOMAIN | ASSOCIATED THREAT | DATES SEEN |
|---|---|---|
| bsc-dash[.]us | Malware distribution | 07/23/25–11/07/25 |
| callapp[.]us | Malware distribution | 07/23/25–11/07/25 |
| callservice[.]us | Malware distribution | 02/05/25–11/07/25 |
| infuy[.]us | Malware distribution | 07/23/25–11/07/25 |
| linkedinservice[.]us | Malware distribution | 07/23/25–11/07/25 |
Next, we queried the 108 domains identified as IoCs on DNS Lookup API. We learned that 12 had active IP resolutions. Further scrutiny unveiled eight IP addresses after duplicates and those already tagged as IoCs were filtered out.
A Threat Intelligence API query for the eight additional IP addresses revealed that seven have already been weaponized for attacks.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website, or contact us, to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byRadix

Sponsored byWhoisXML API

Sponsored byCSC

Sponsored byIPv4.Global

Sponsored byVerisign
