


|
||
|
||
The Socket Threat Research Team recently uncovered 175 malicious npm packages threat actors used in the widespread Beamglea phishing campaign. They targeted more than 135 industrial, technology, and energy companies worldwide. As of 9 October 2025, the packages have been downloaded more than 26,000 times.
The researchers identified 16 indicators of compromise (IoCs) comprising four subdomains, three domains, and nine email addresses. After extracting the domains from the subdomains, we had seven domains left, along with nine email addresses, to further analyze. Our DNS deep dive led to these findings:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
While we did not plan to use the four subdomains for our new artifact hunt, we still sought out more information on them. We thus used the WhoisXML API MCP Server to gather said information. The prompt “Get all data for cfn.fejyhy.com, cfn.fenamu.com, cfn.jackpotmastersdanske.com, and cfn.notwinningbutpartici.com” enabled us to determine that:
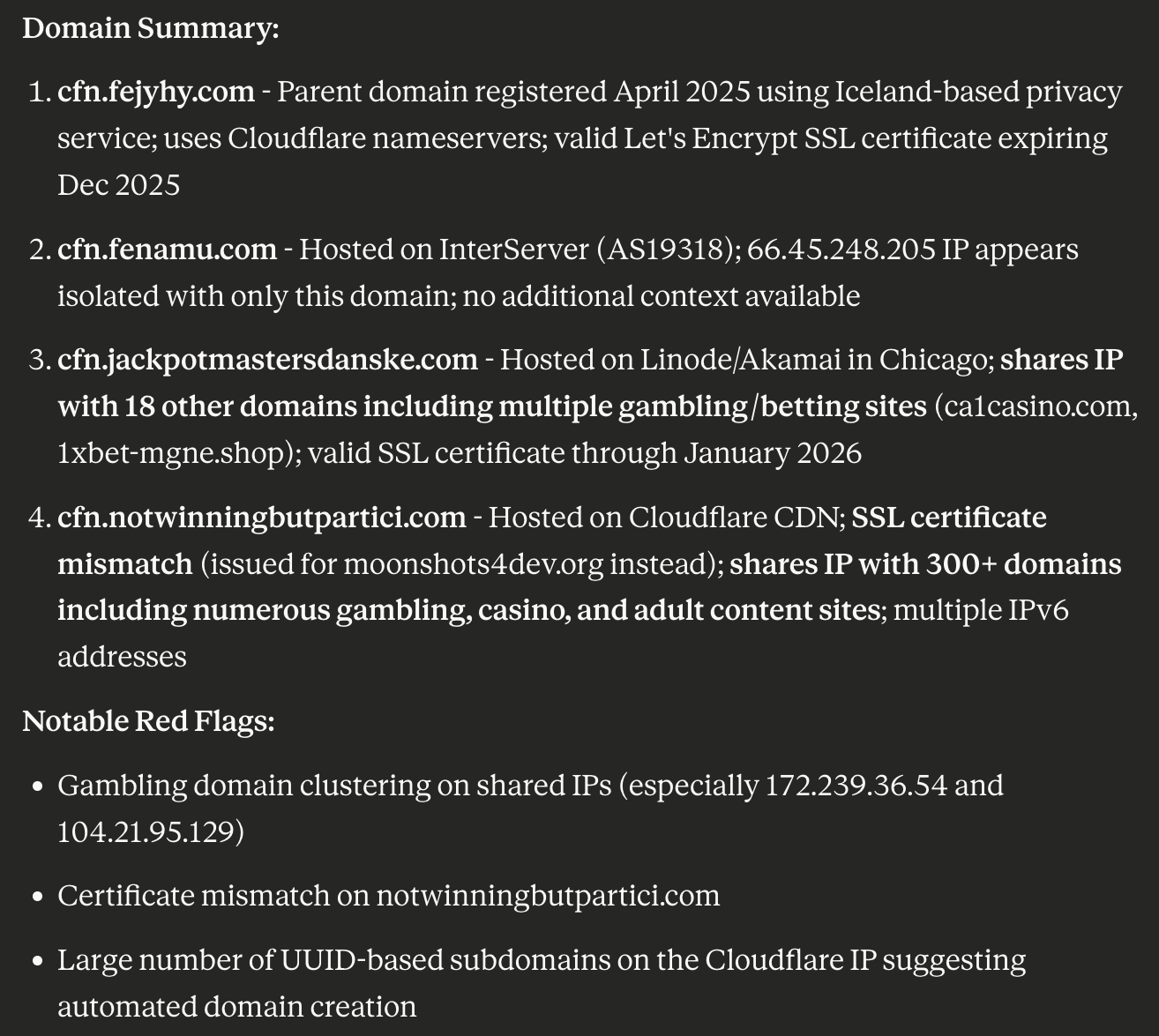
Next, we queried the seven domains identified as IoCs on First Watch Malicious Domains Data Feed and found out that two of them appeared on the feed 176—219 days before being reported as such on 9 October 2025. Take a look at the specifics below.
| DOMAIN IoC | FIRST WATCH DATE | NUMBER OF DAYS BEFORE THE REPORTING DATE |
|---|---|---|
| notwinningbutpartici[.]com | 4 March 2025 | 219 |
| fejyhy[.]com | 16 April 2025 | 176 |
After that, we queried the seven domains identified as IoCs on WHOIS API and discovered that:
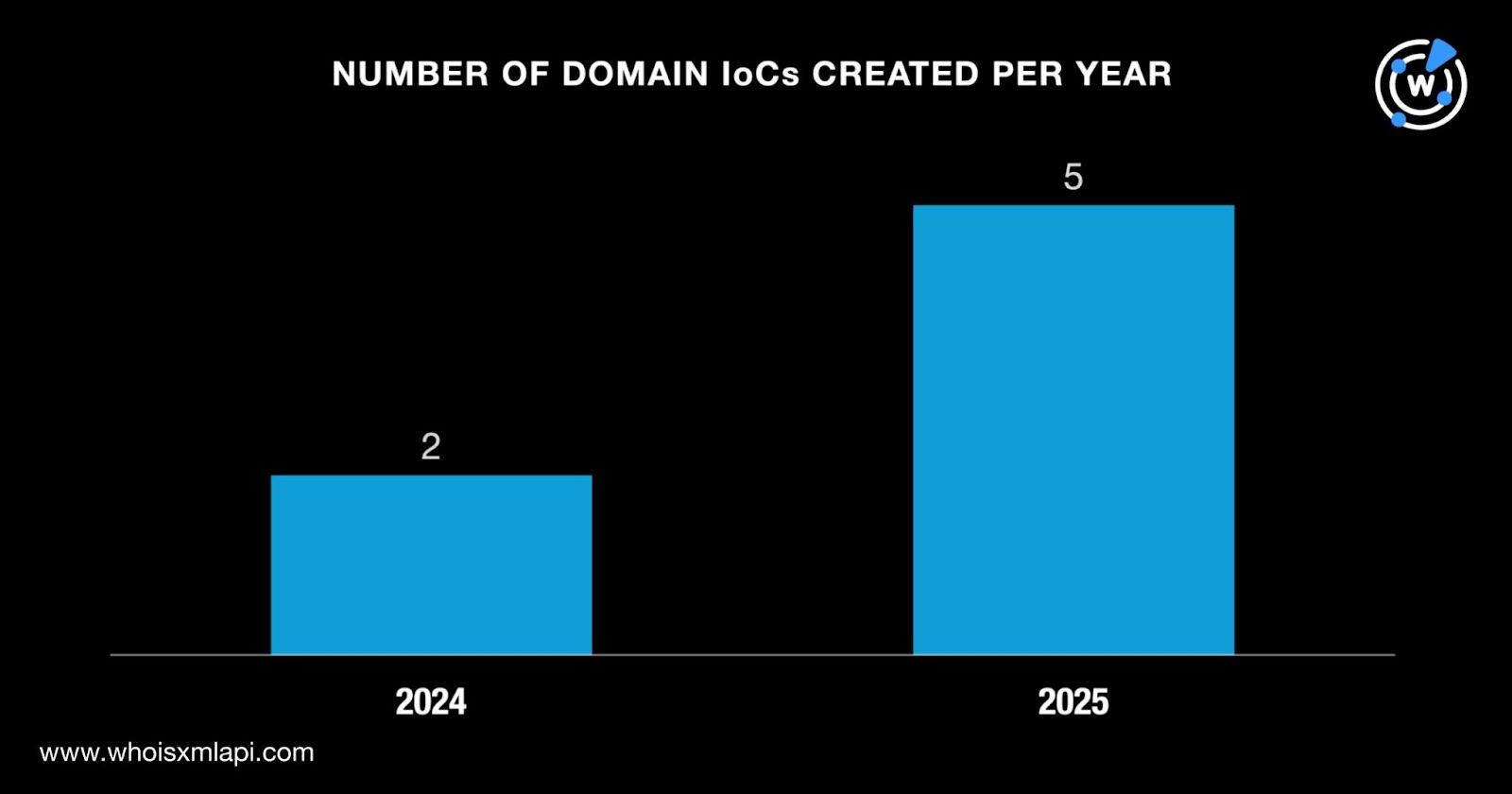
They were split among four registrars led by Namecheap, which accounted for four domains. One domain each was administered by MozDomains, NameSilo, and PDR.
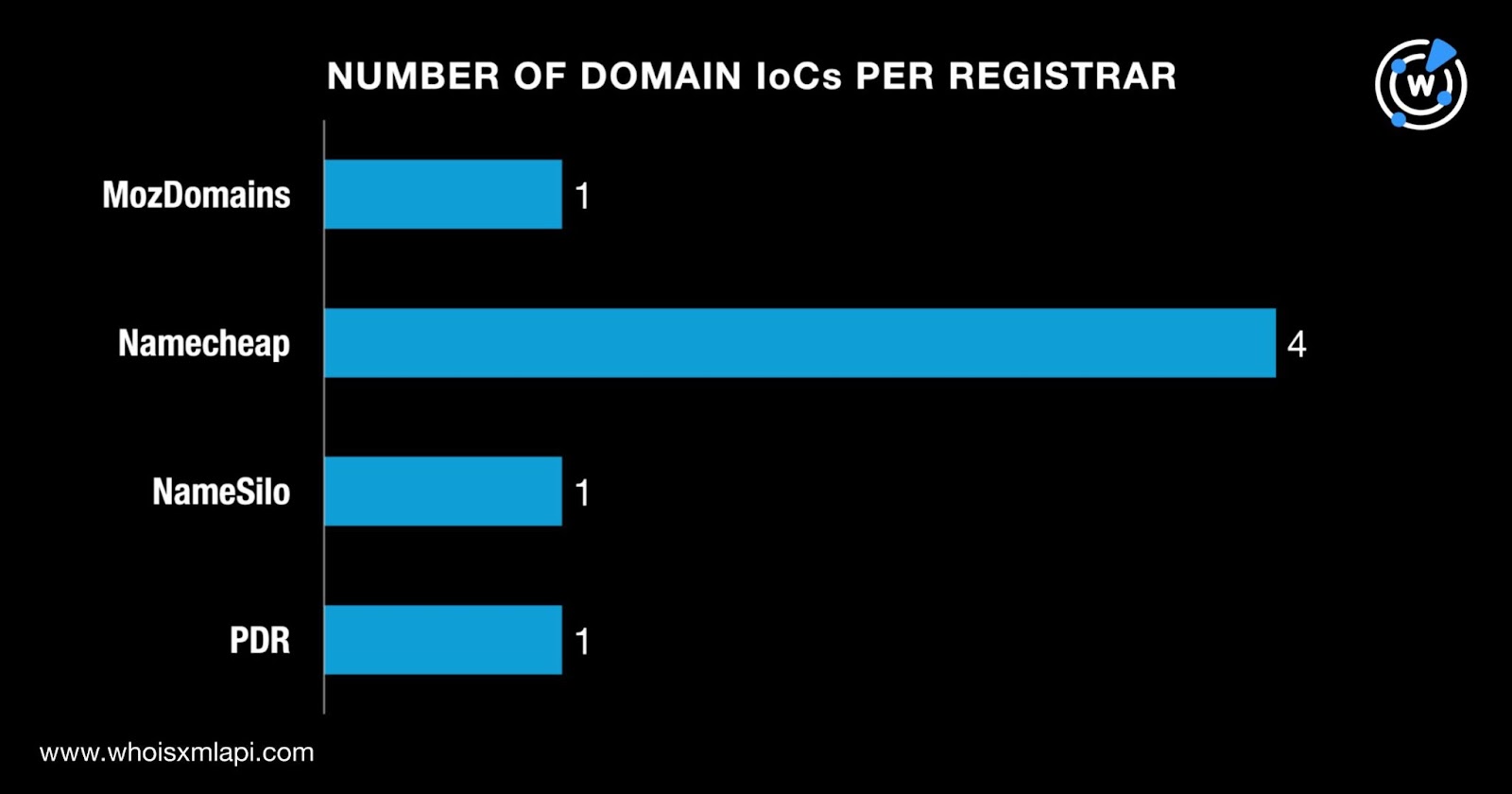
While one did not have a registrant country on record, four were registered in Iceland. One domain each, meanwhile, was registered in Peru and the U.S.
We then queried the seven domains identified as IoCs on DNS Chronicle API and found out that all had rich DNS histories. In particular, they had a total of 57 historical domain-to-IP resolutions. The domain villasmbuva[.]co[.]mz posted the oldest resolution date—14 February 2024. Its latest resolution was recorded on 2 October 2025. Here are details for three other domains.
| DOMAIN IoC | FIRST RESOLUTION DATE | LAST RESOLUTION DATE | NUMBER OF DOMAIN-TO-IP RESOLUTIONS |
|---|---|---|---|
| musicboxcr[.]com | 16 February 2024 | 22 August 2025 | 12 |
| notwinningbutpartici[.]com | 6 March 2025 | 19 October 2025 | 8 |
| jackpotmastersdanske[.]com | 14 March 2025 | 3 September 2025 | 12 |
To uncover more connected artifacts, we began by querying the seven domains identified as IoCs on WHOIS History API, which revealed that all of them had email addresses in their historical WHOIS records. They had 15 unique email addresses in all, two of which turned out to be public addresses.
Adding the nine email addresses to the two public email addresses we found, we now had 11 addresses for further analysis. We queried them on Reverse WHOIS API and found that while none of them appeared in other domains’ current WHOIS records, three did appear in historical records. This step led to the discovery of 344 email-connected domains after duplicates and those already tagged as IoCs were filtered out.
Using DNS Lookup API with elkendinsc[.]com, fejyhy[.]com, fenamu[.]com, jackpotmastersdanske[.]com, musicboxcr[.]com, notwinningbutpartici[.]com, and villasmbuva[.]co[.]mz as inputs showed that they all actively resolved to various IP addresses. Specifically, they resolved to five unique IP addresses after duplicates were removed.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byWhoisXML API

Sponsored byCSC
