


|
||
|
||
For many across the globe, Christmas represents a joyous time of celebration and giving. But it can also be a time for worry, especially for those unfortunate enough to get scammed while doing their holiday shopping.
This year, we scoured the DNS for domains and subdomains that contained the text string christmas to identify potentially harmful properties and other connected artifacts.
Jumping off a list of 22,923 christmas domains obtained on 26 November 2024 from First Watch Malicious Domains Data Feed, our in-depth DNS investigation found:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
As mentioned earlier, we began our foray into the DNS in search of Christmas-themed threats by obtaining 22,923 domains containing the string christmas that are either already or likely to turn malicious in the future.
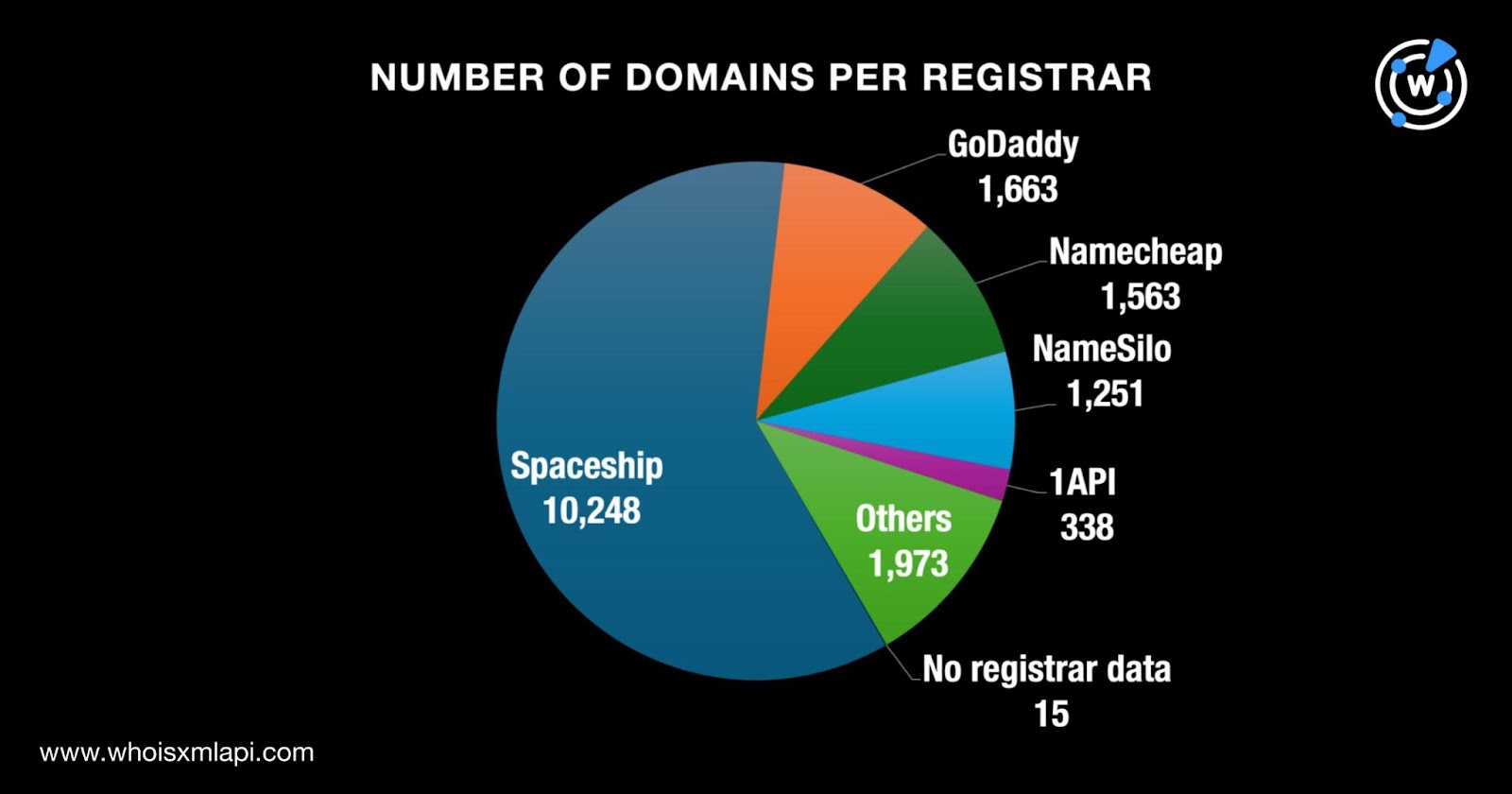
We queried the 22,923 christmas domains on Bulk WHOIS Lookup and found that only 17,051 had current WHOIS records. Take a look at our specific findings below.
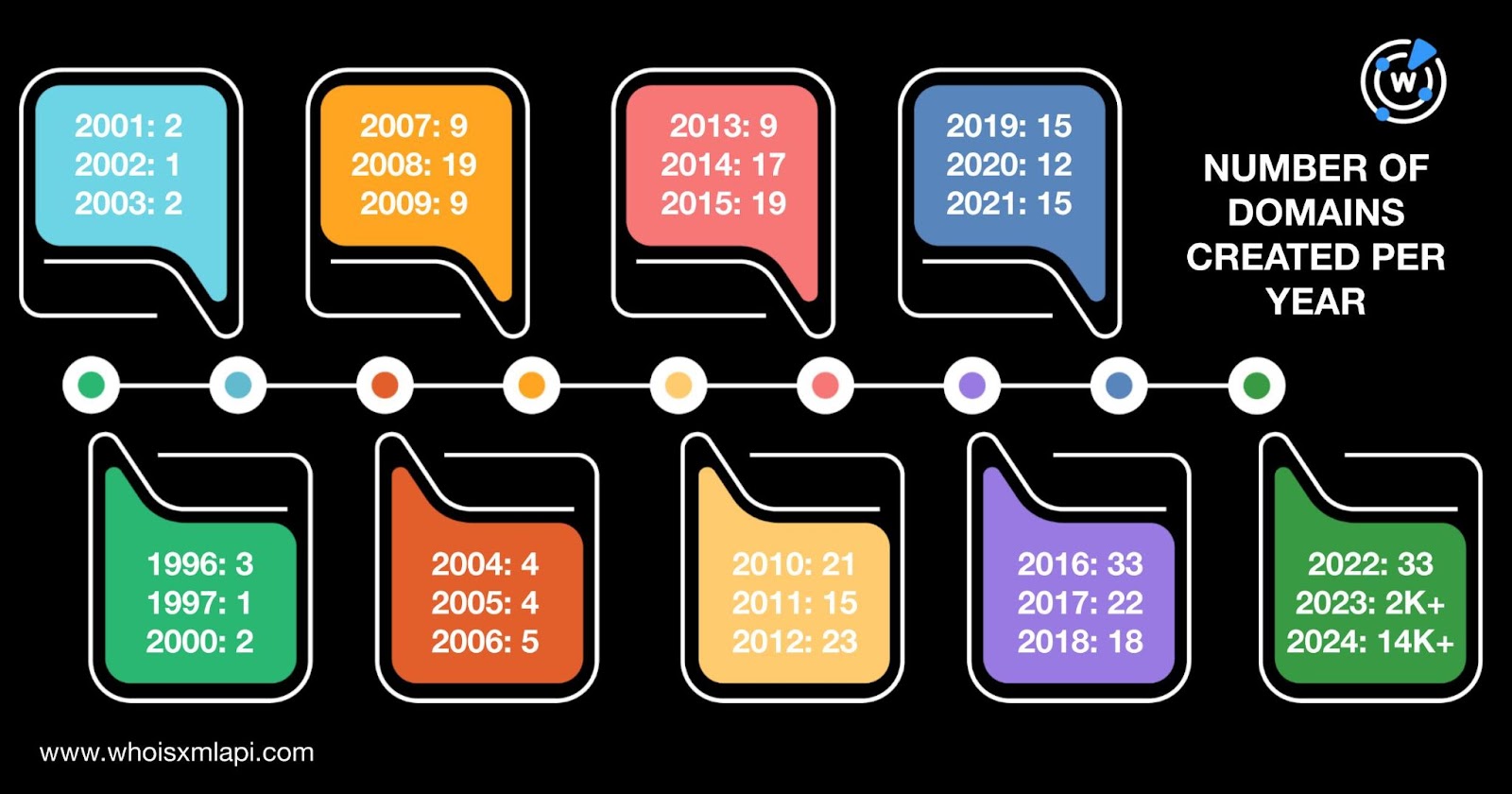
They were created between 1996 and 2024. Around 84% of the domains, however, were newly created, just this year.
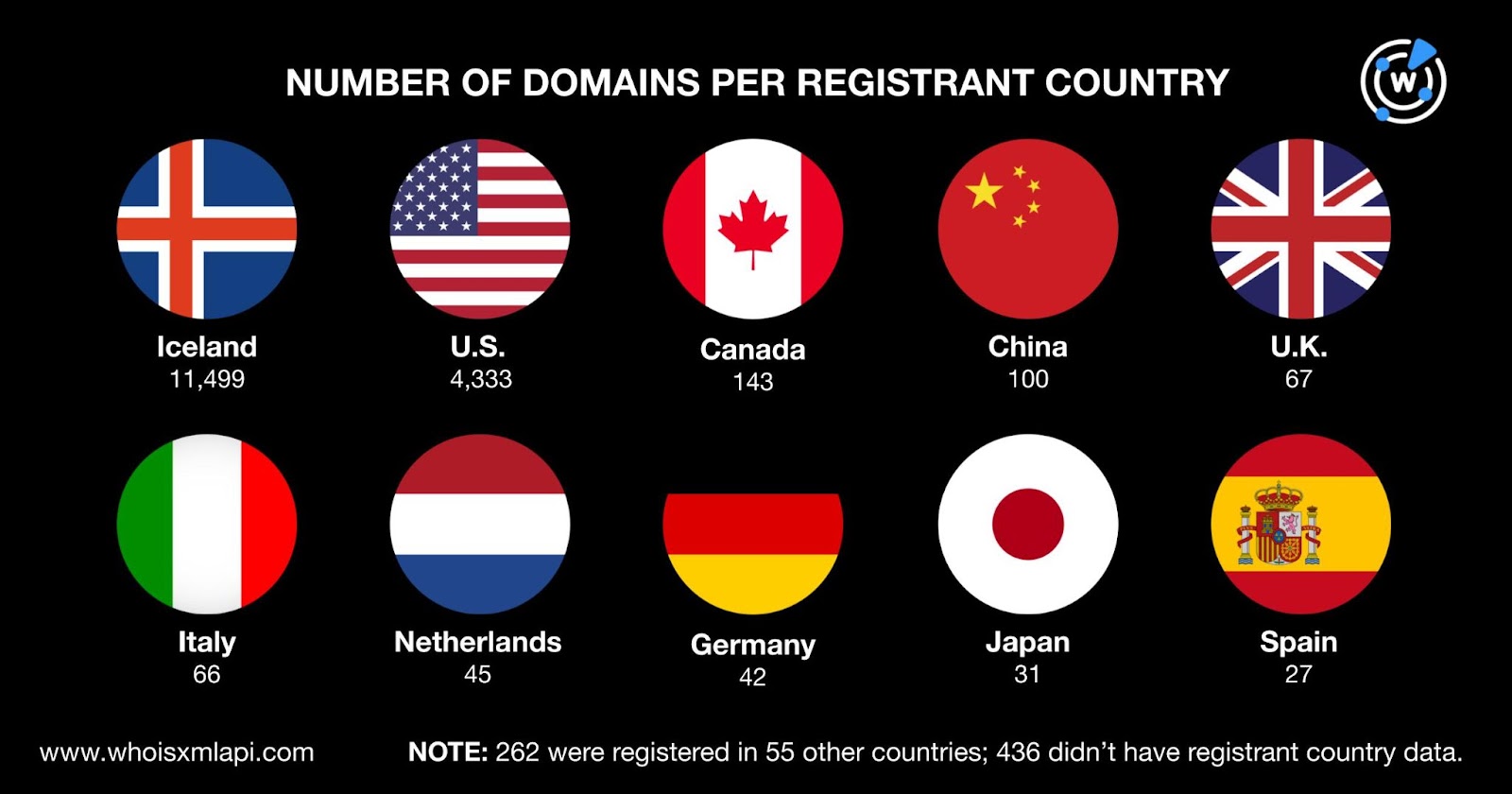
They were registered in 65 different countries led by Iceland, which accounted for 11,499 domains. The other top registrant countries were the U.S. with 4,333 domains; Canada with 143; China with 100; the U.K. with 67; Italy with 66; the Netherlands with 45; Germany with 42; Japan with 31; and Spain with 27. A total of 262 domains were registered in 55 other countries, while 436 didn’t have current registrant country data.
We then queried the 22,923 christmas domains on DNS Chronicle API and found that 17,188 had historical IP resolutions ranging from 1 to 20 per domain. In total, the 17,188 domains had 168,578 recorded events from 4 October 2019 to 8 November 2024. Take a look at five examples below.
| DOMAIN | START DATE | LAST DATE | NUMBER OF IP RESOLUTIONS |
|---|---|---|---|
| 12daysofchristmas[.]info | 29 February 2020 | 18 November 2024 | 105 |
| artificialchristmastreesale[.]co[.]uk | 11 July 2024 | 11 November 2024 | 5 |
| nashvillechristmasbus[.]com | 20 February 2020 | 12 October 2024 | 71 |
| yourfunny[.]christmas | 5 May 2024 | 13 October 2024 | 10 |
| zen[.]christmas | 25 December 2023 | 19 November 2024 | 12 |
After analyzing the sample of 22,923 christmas domains, we took a DNS deep dive for potentially connected artifacts.
Our bulk WHOIS lookup earlier provided 629 email addresses after duplicates were filtered out, 73 of which turned out to be public addresses. A query for the public email addresses on Reverse WHOIS API yielded 1,331 email-connected domains after duplicates and the original domains from First Watch Malicious Domains Data Feed were removed.
Next, we queried the 22,923 christmas domains on DNS Lookup API and found that they actively resolved to 3,229 unique IP addresses. A Threat Intelligence API query for the 3,229 IP addresses revealed that 2,529 of them have already been weaponized.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byVerisign

Sponsored byCSC

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byRadix

Sponsored byIPv4.Global
