


|
||
|
||
Companies today manage hundreds or even thousands of domain names that support their organization, their visitors from different countries, and their brands and trademarks. They register misspelling of their names as a defensive strategy to protect their brand from online fraud, or from losing traffic to simple user typos.
So why should CISOs care?
Global businesses rely on the internet for everything—websites, email, authentication, voice over IP (VoIP), and more. It’s part of an organization’s external attack surface and needs to be continuously monitored for cybercrime attacks and fraud. As cyber risks continue to increase, organizations and cyber insurers face greater challenges in quantifying them and addressing their capacity for harm. Every day, we learn about new developments involving supply chain attacks, ransomware, and phishing attacks, along with additional layers of complexity in terms of what coverage they require and how to stop them.
Zero Trust models must extend beyond business systems, applications, and devices, and include a company’s domain ecosystem as a real vulnerability to the attacks noted below. The following two domain security threats enable these attacks:
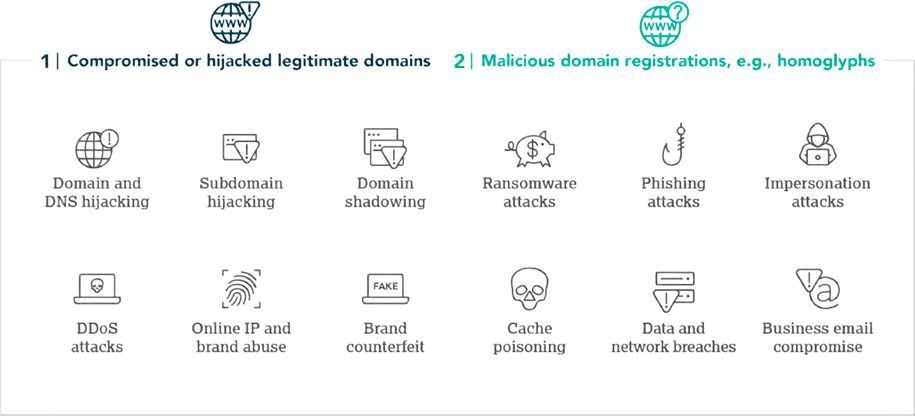
In CSC’s annual Domain Security report, it was noted that with the risks of not having domain security in place potentially leading to phishing or ransomware attacks, and many other cyberthreats, it would be prudent for an organizations overall security posture to have better implementation of domain security measures.
Every business depends on a series of suppliers and vendors. These relationships form supply chains that can become increasingly complex, leaving organizations exposed to even more risk. Companies should conduct a yearly security review on the companies they work with—including their domain registrar(s). Conducting a security audit each year lets organizations have insight into how they are maturing, developing, and adjusting.
Also, when it comes to the complexities of the domain registrar ecosystem, vendor selection matters. Companies can select an enterprise-class registrar that specializes in working with corporations and brand owners that require advanced business practices, capabilities, expertise, and support staff in relation to domain and DNS management as well as security, brand and fraud protection, data governance and cyber security. They also offer defense-in-depth safeguards, along with DNS redundancy to provide a backup DNS to boost resiliency.
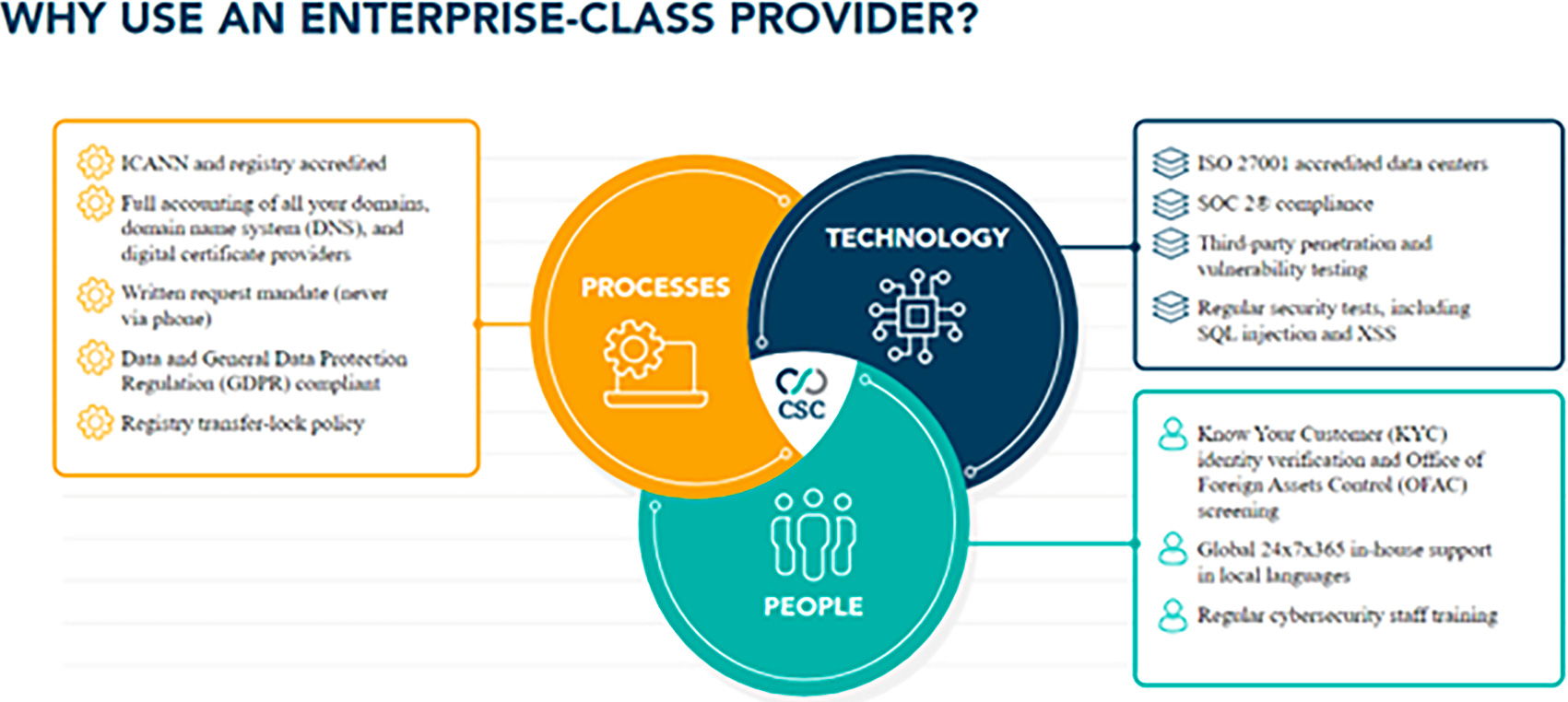
Other consumer-grade registrars offer very transactional relationships with their clients, and don’t go through the thorough review process an enterprise-class provider does. They don’t offer solutions to mitigate all the digital risks of domain spoofing, domain/DNS hijacking attacks, sub-domain takeovers, and phishing attacks.In addition to the lack of security, the hard truth is that consumer-grade domain registrars have been proliferating typosquatting, domain name auctioning services—often infringing upon other brand names—and name spinning services. These registrars monetize the goodwill brand owners have worked hard to establish, creating a revenue stream for themselves rather than protecting their clients.
Domain security is a critical component to help mitigate cyberattacks in the early stages—your first line of defense in your organization’s Zero Trust model. According to the Cybersecurity and Infrastructure Security Agency (CISA), most cyberattacks—including ransomware and business email compromise (BEC)—begin with phishing. Although losses due to ransomware now exceed billions annually, most ransomware protection and response measures don’t adequately address phishing risks in the early stages of an attack because they don’t include domain security measures to protect against the most common phishing attacks.
Bad actors are using company domain names for malicious attacks more than ever before. Research shows that phishing and related malware attacks most commonly occur from a compromised or hijacked legitimate domain name, a maliciously registered and confusingly similar domain name, or via email spoofing.
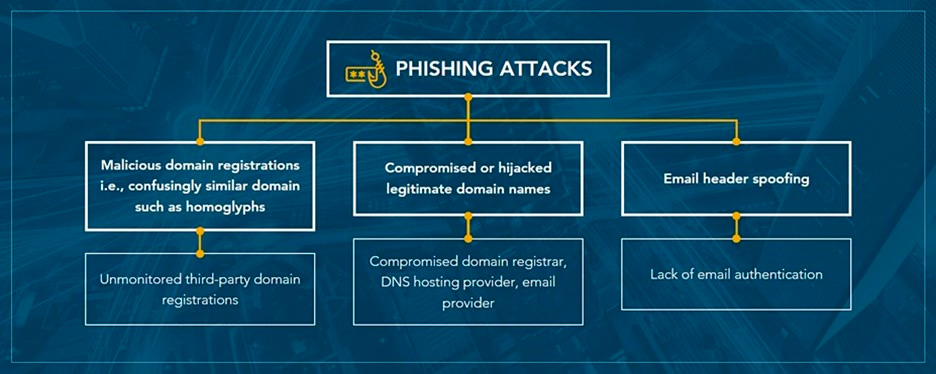
CSC’s 3D Domain Security and Enforcement service provide a multi-dimensional view of various threat vectors outside the firewall targeting specific domains. With corporations operating multiple brands, with hundreds or even thousands of domains within their portfolio, rapid detection and de-activation of confusingly similar domains imitating brands are crucial. The 3D product is powered by one of the largest data lakes associated with domain name-centric data, equipped with a correlation engine, machine learning, and clustering technology.
Sponsored byRadix

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byDNIB.com

Sponsored byCSC
