


|
||
|
||
Trend Micro analyzed what they dubbed as the “TAOTH Campaign,” which primarily targeted users across Eastern Asia. The attackers used fake software update, cloud storage, and login pages to distribute malware and collect sensitive information. Their victimology and decoy documents revealed a focus on high-value targets, including dissidents, journalists, researchers, and technology/business leaders in China, Taiwan, Hong Kong, Japan, South Korea, and overseas Taiwanese communities.
The report “TAOTH Campaign Exploits End-of-Support Software to Target Traditional Chinese Users and Dissidents” identified two domains, four subdomains, and five IP addresses as indicators of compromise (IoCs).
We further investigated eight IoCs comprising three domains and five IP addresses, which led to these discoveries:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
Given that some of the domains identified as IoCs did not seem to be inherently malicious (i.e., legitimate but compromised), we sought to verify their ownership details aided by the WhoisXML API MCP Server.
First, we extracted the domains from the list of IoCs. We used the prompt “Use WHOIS API, Website Categorization API, Threat Intelligence API to determine if sogouzhuyin.com, amazonaws.com, auth-web.com, onedrive365-jp.com (i.e., some of which were extracted from subdomains identified as IoCs) are malicious.”
The query results informed us that while only one—auth-web[.]com—was indeed malicious, two others were suspicious at the very least based on their ages (i.e., relatively new), WHOIS details (i.e., privacy protection usage), and naming pattern (i.e., potentially mimicking legitimate domains).

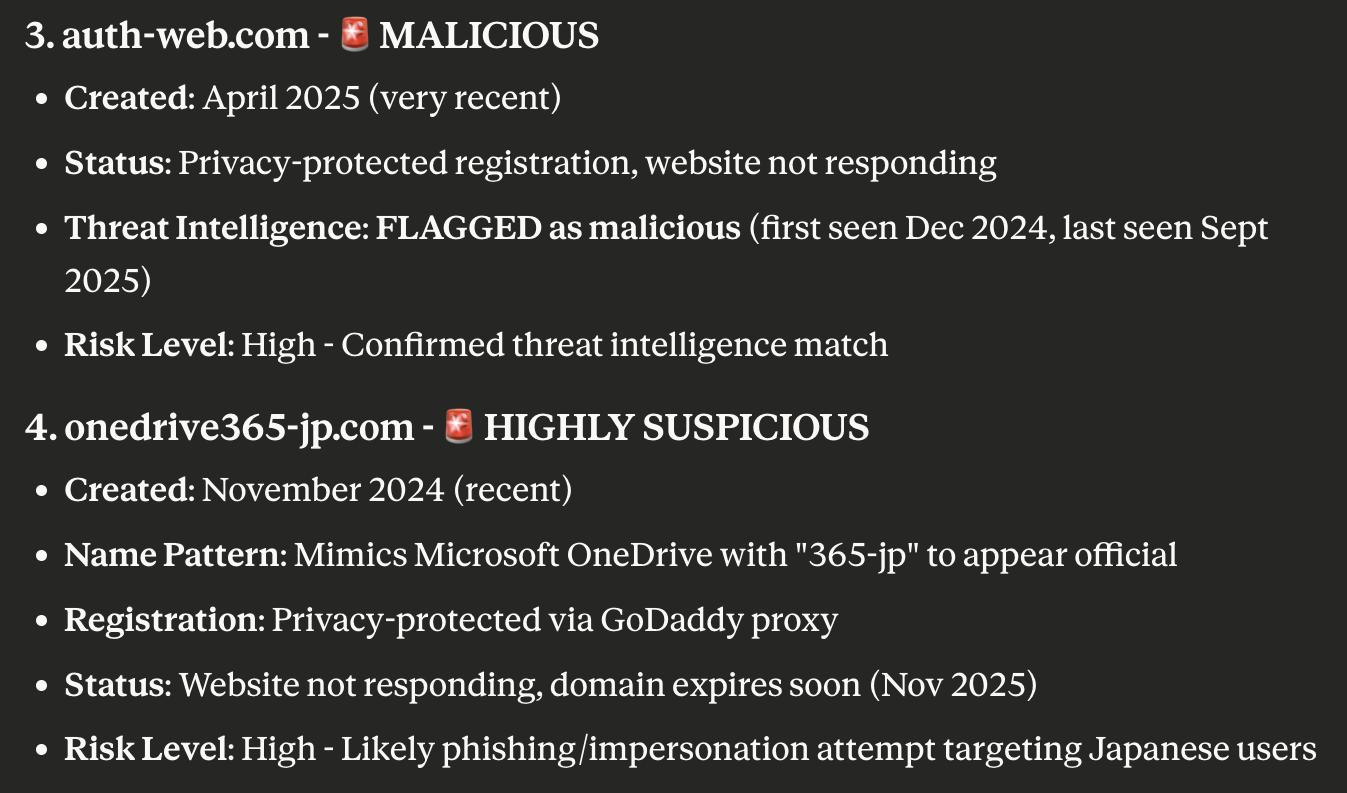
The results thus left us with three domains—sogouzhuyin[.]com, auth-web[.]com, and onedrive365-jp[.]com—for our analysis. Hence, we limited our investigation to only eight of the 11 IoCs Trend Micro identified.
Next up, we sought to learn more about the eight IoCs.
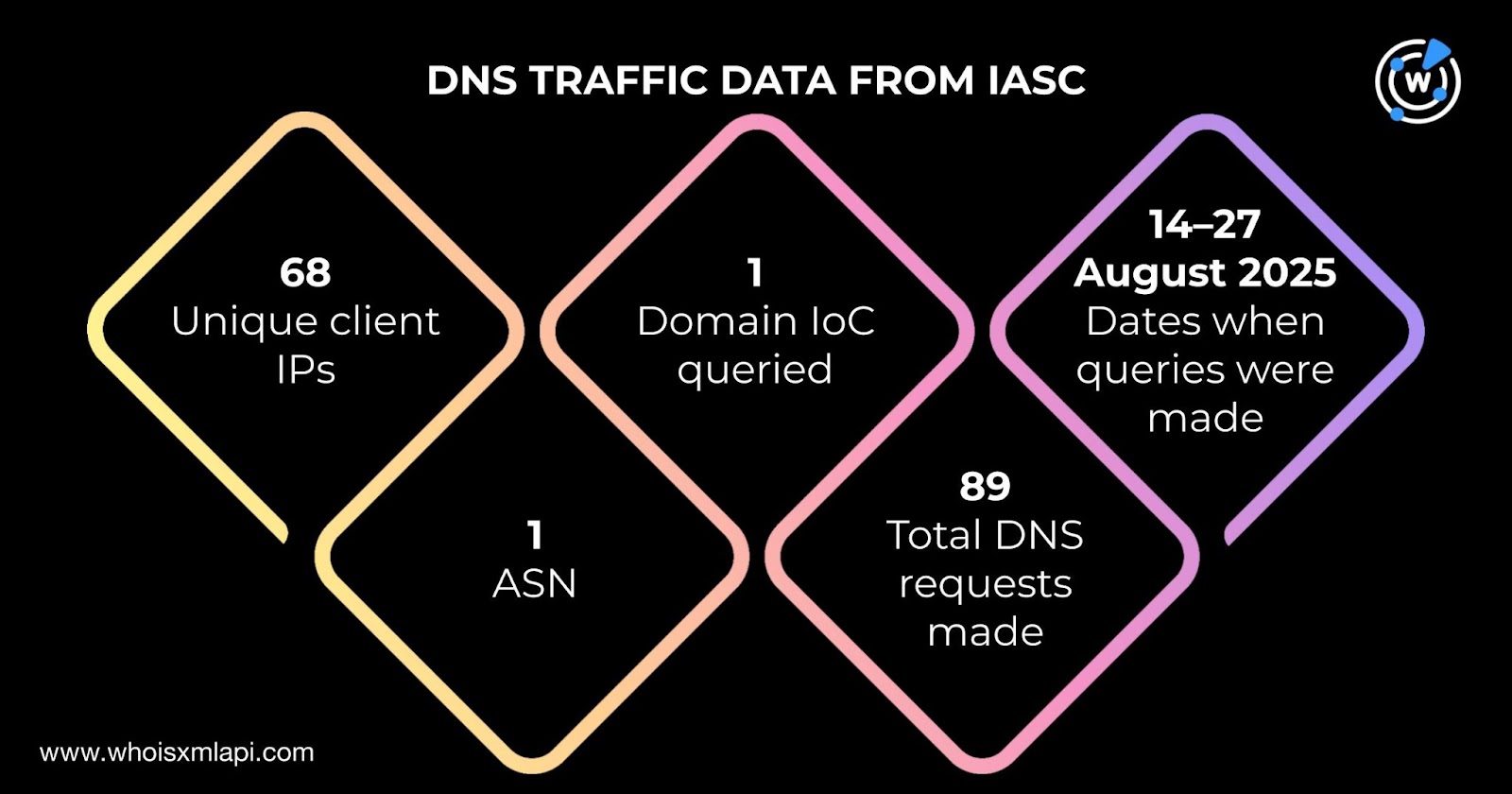
First, we obtained sample DNS traffic data from IASC regarding the three domains identified as IoCs. We learned that 68 unique client IP addresses under one Autonomous System number (ASN) communicated with one domain IoC—auth-web[.]com—via 89 DNS queries made on 14—27 August 2025.
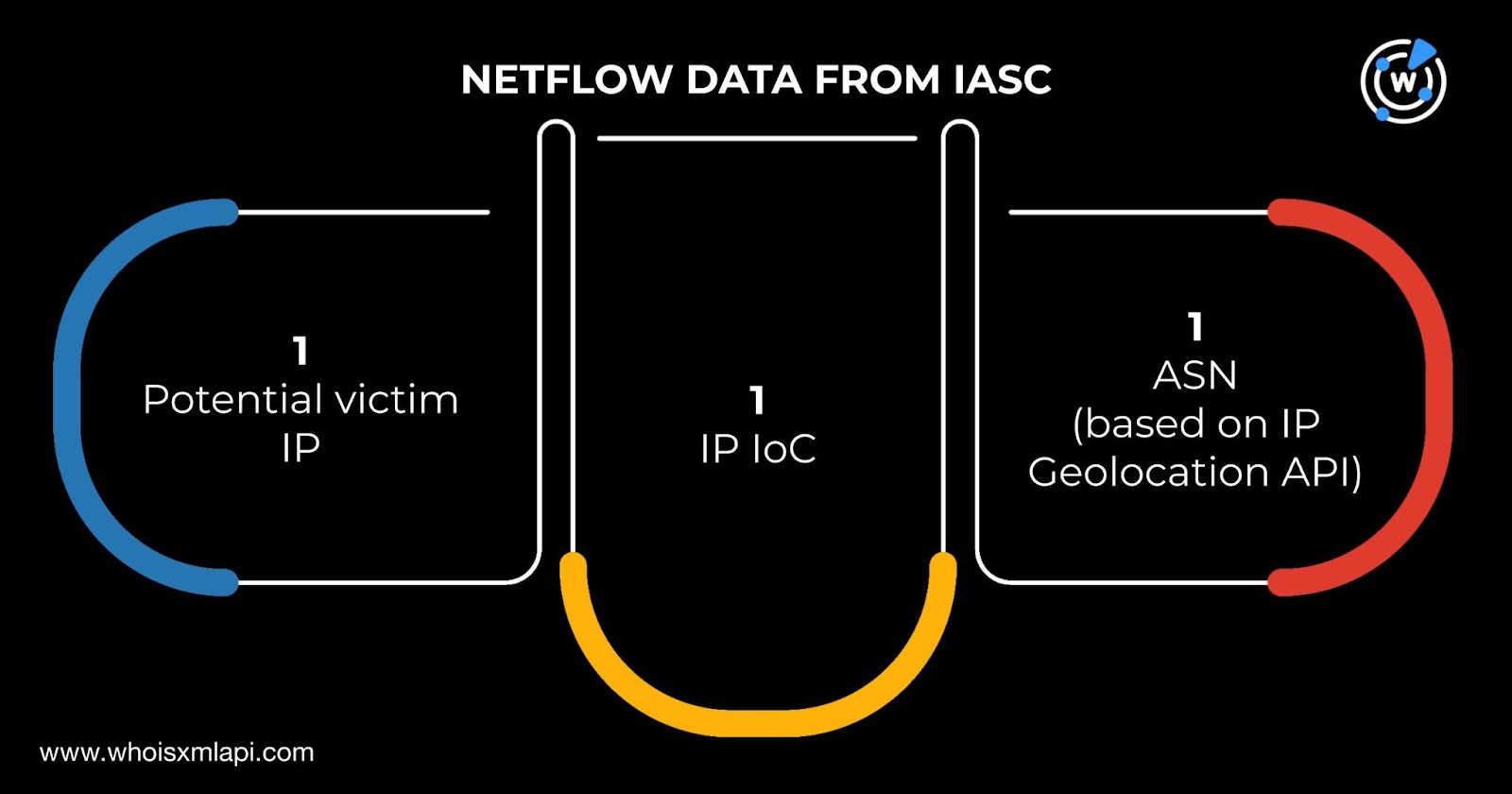
Next, we sought to uncover more information about the five IP addresses identified as IoCs. The sample IASC DNS traffic data showed that one potential victim IP address communicated with one IP IoC—45[.]32[.]117[.]177. An additional IP Geolocation API query for the victim IP revealed its corresponding ASN—18779, which belonged to Energy Group Networks (ISP).
Next, we gathered data from our intelligence sources starting with the First Watch Malicious Domains Data Feed. We learned that one of the domains identified as IoCs—onedrive365-jp[.]com—was dubbed likely to turn malicious 281 days (i.e., on 20 November 2024, the day it was created) before it was reported as such on 28 August 2025.
We then queried the three domains identified as IoCs on WHOIS API and found out that they all had current WHOIS records. In addition, we discovered that:
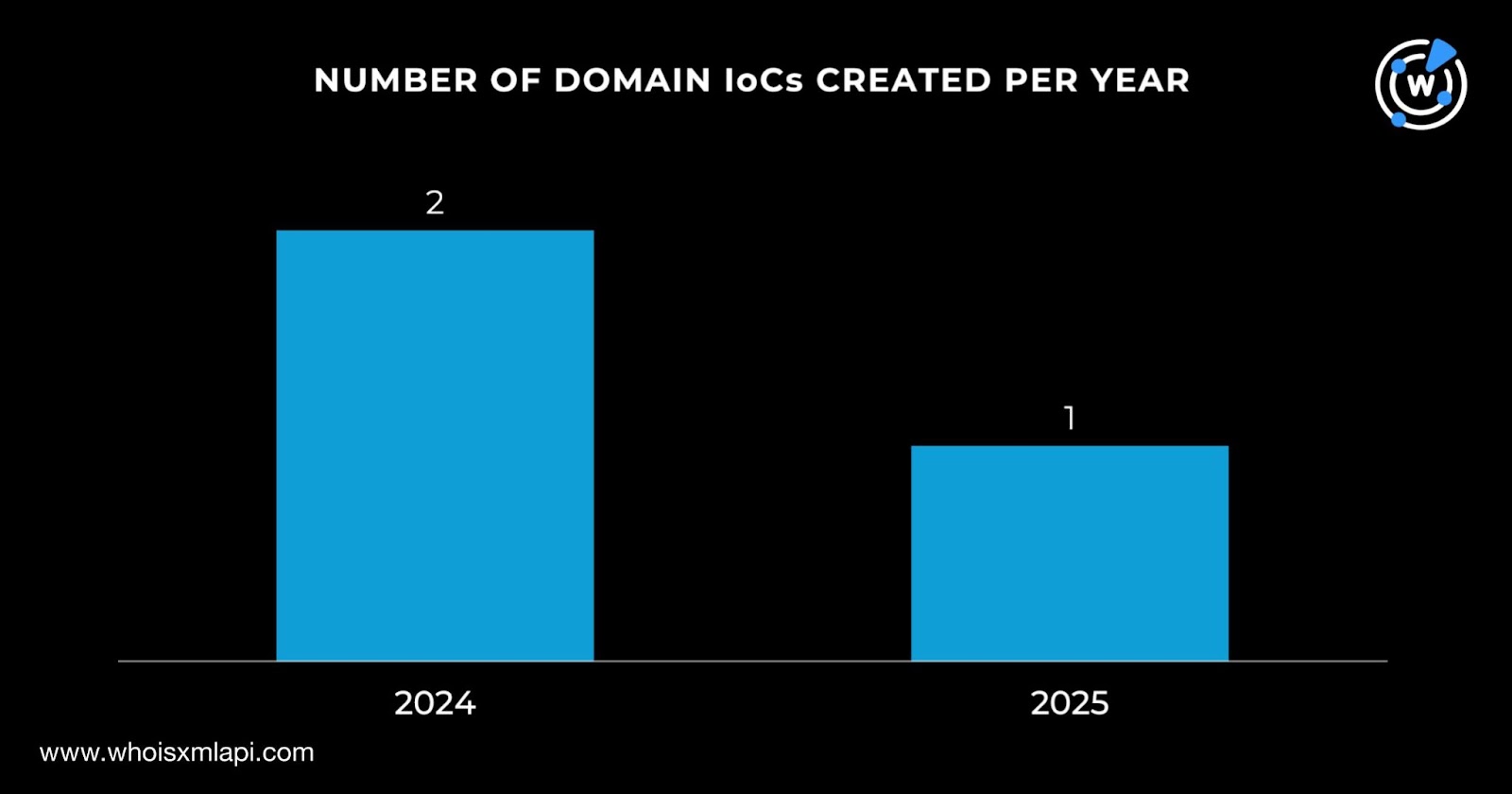
Each domain was administered by a different registrar, namely, DropCatch, GoDaddy, and NameSilo.
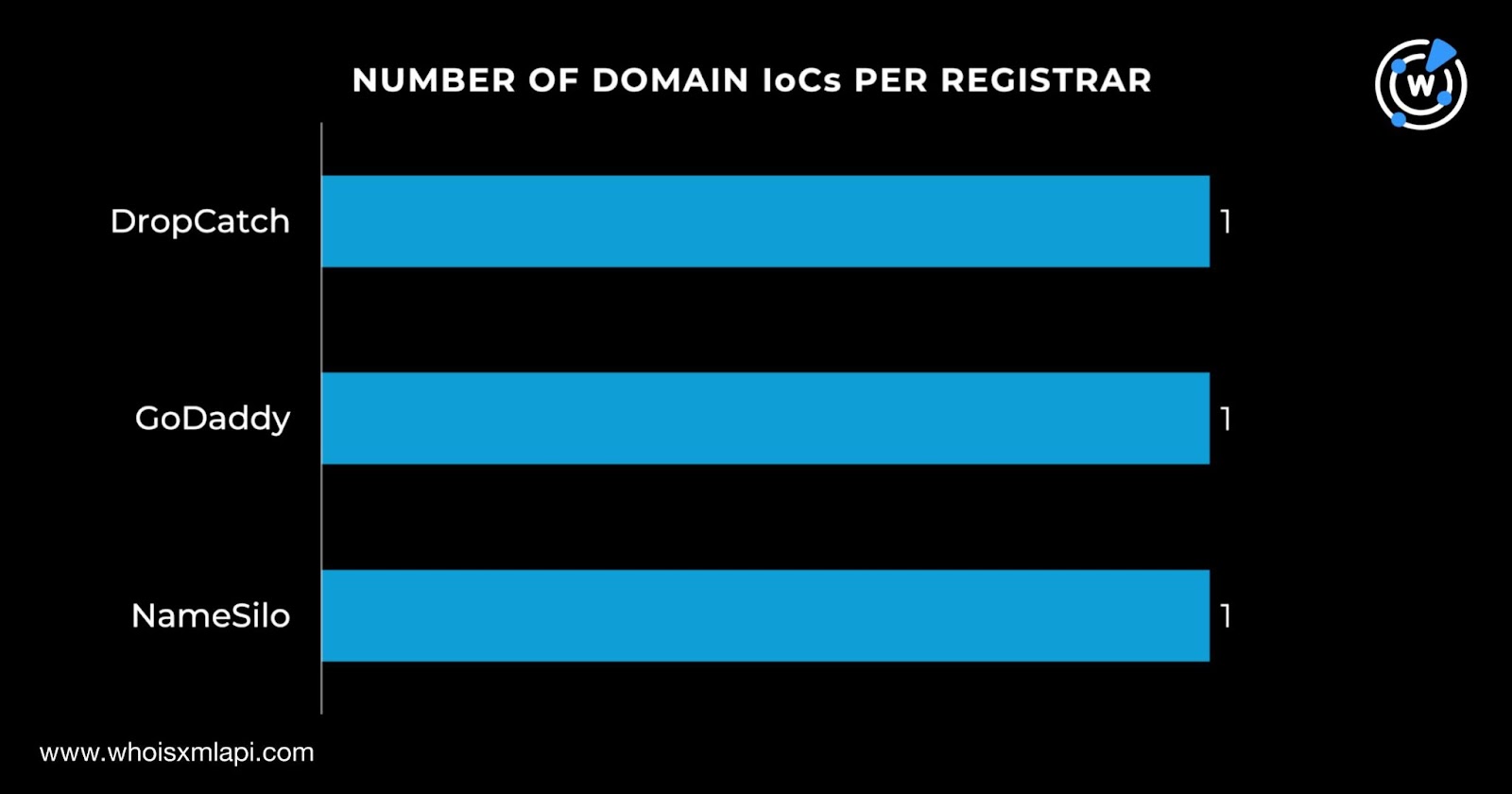
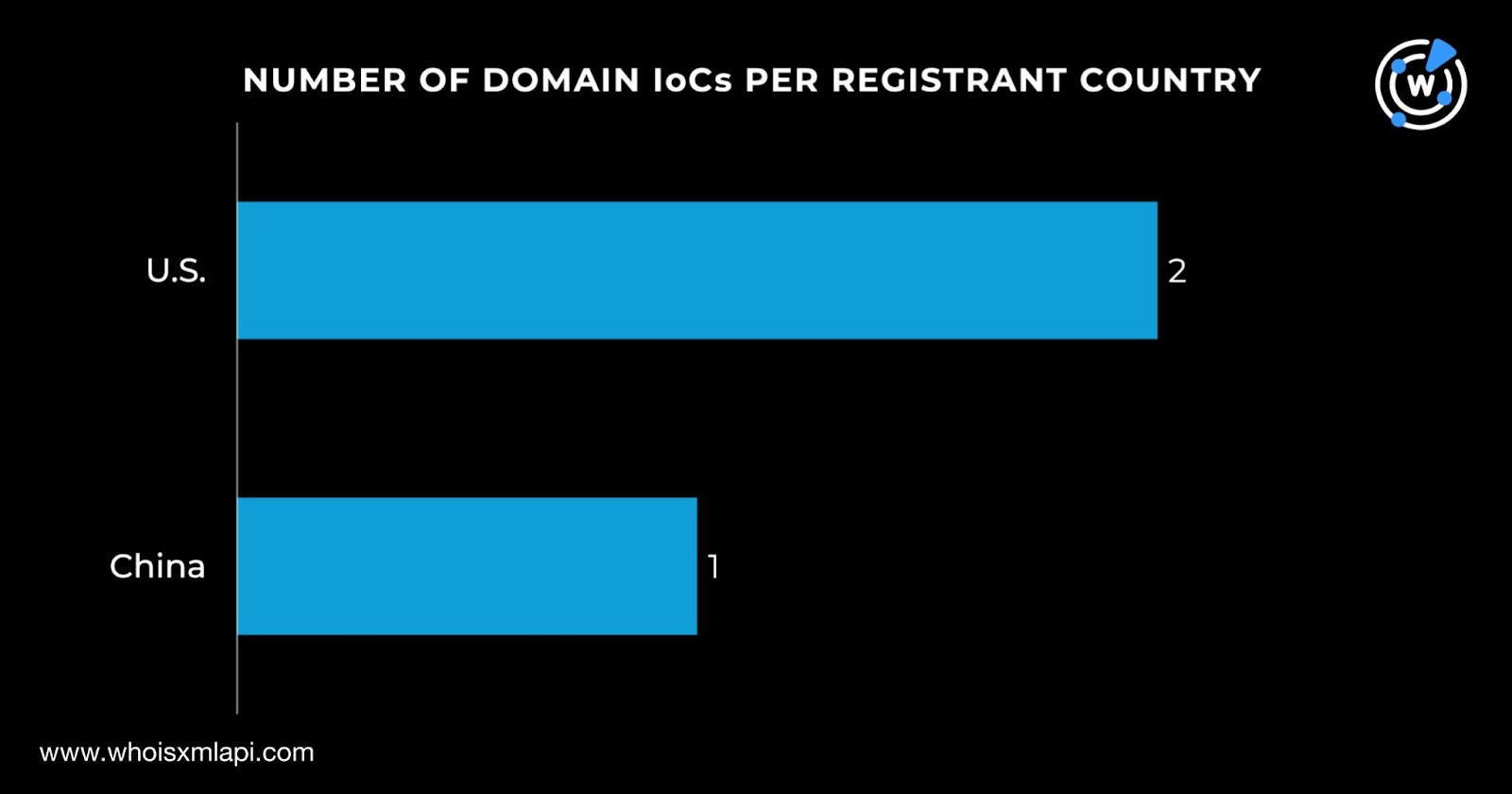
They were registered in two countries—two in the U.S. and one in China.
A DNS Chronicle API query for the three domains identified as IoCs showed that only two had DNS histories. Altogether, the two domains recorded 88 domain-to-IP resolutions over time starting on 11 August 2017 (i.e., the oldest resolution date). Take a look at the details for each domain below.
| DOMAIN IoC | NUMBER OF RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE |
|---|---|---|---|
| auth-web[.]com | 72 | 11 August 2017 | 27 July 2023 |
| sogouzhuyin[.]com | 16 | 1 August 2023 | 5 September 2024 |
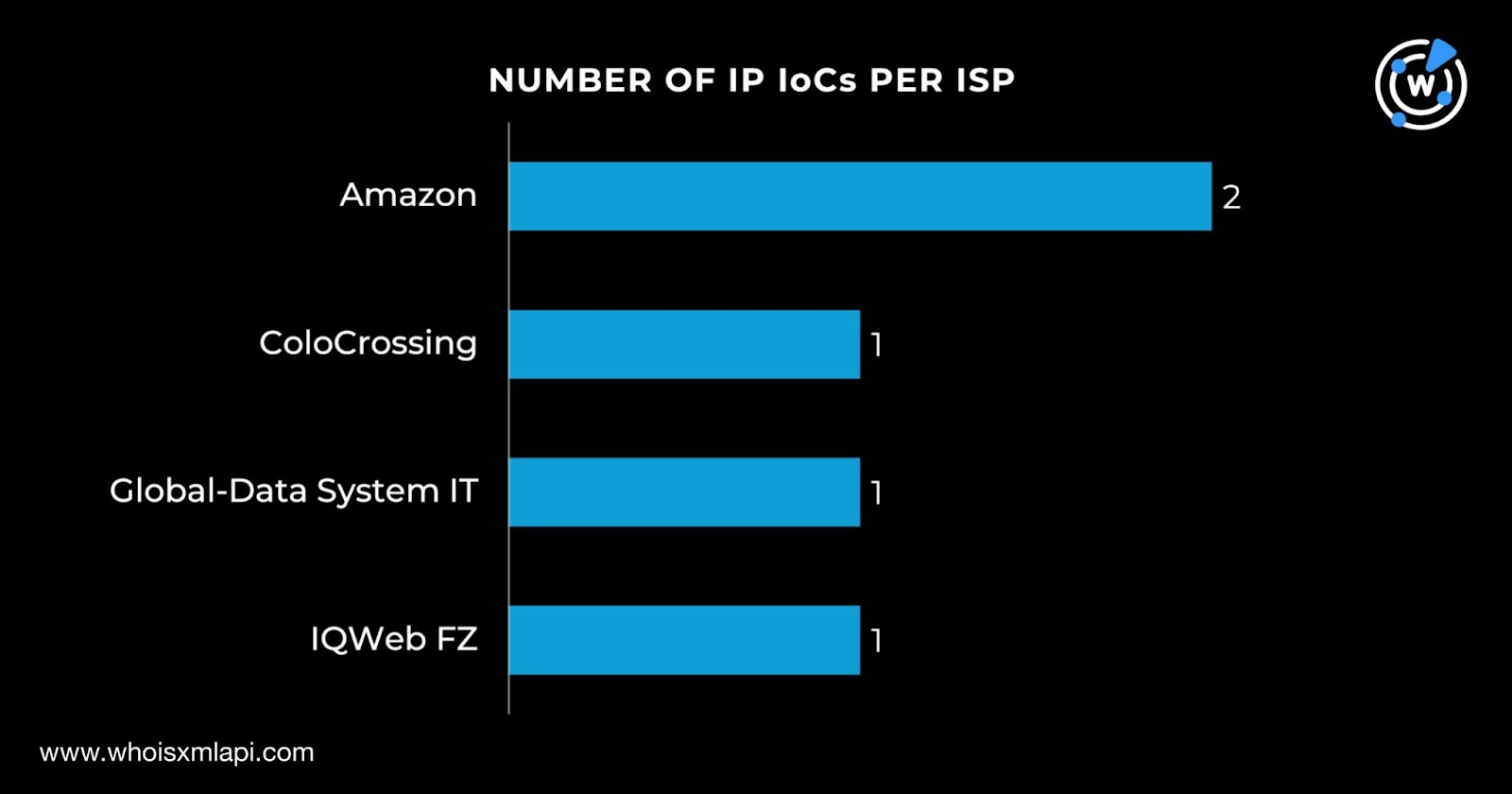
We then queried the five IP addresses on Bulk IP Geolocation Lookup and discovered that:
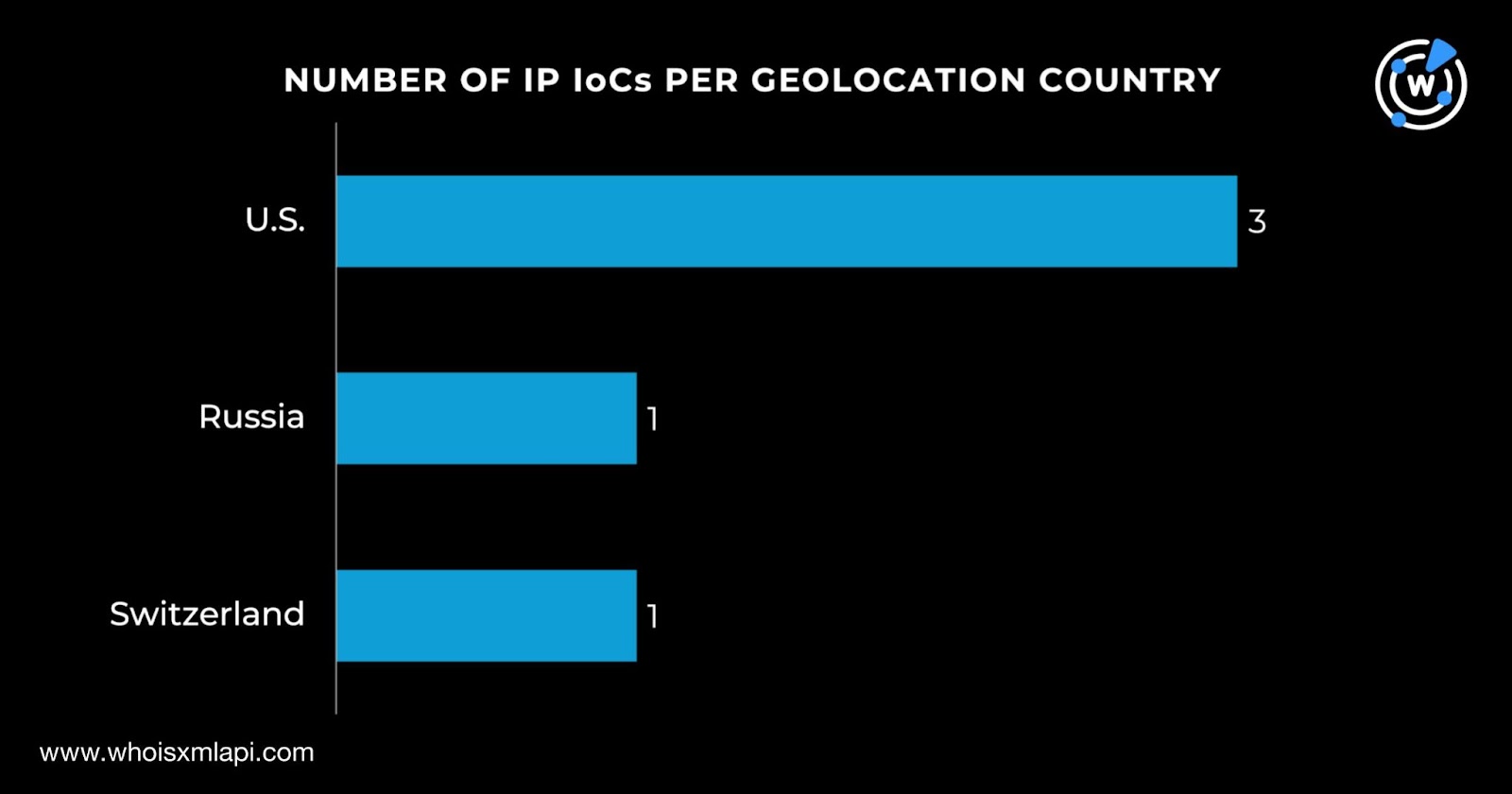
They were administered by four ISPs—two by Amazon and one each by ColoCrossing, Global-Data System IT, and IQWeb FZ.
A DNS Chronicle API query for the five IP addresses identified as IoCs revealed that all of them had rich DNS histories. Altogether, they posted 447 IP-to-domain resolutions over time. The IP address 45[.]32[.]117[.]177 recorded 91 resolutions starting on 22 April 2017 (i.e., the oldest resolution date). Here are more details about other IoCs.
| IP IoC | NUMBER OF RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE |
|---|---|---|---|
| 45[.]32[.]117[.]177 | 91 | 22 April 2017 | 7 May 2023 |
| 154[.]90[.]62[.]210 | 235 | 10 January 2020 | 14 November 2022 |
| 192[.]124[.]176[.]51 | 28 | 31 July 2020 | 5 August 2025 |
As the next step, we searched for new artifacts that may be connected to the TAOTH campaign. We began by querying the three domains identified as IoCs on WHOIS History API. Only two of the domains had email addresses in their historical WHOIS records. Specifically, they had 47 unique email addresses. Further scrutiny allowed us to collate five public email addresses from the list.
While none of the five public email addresses appeared in the current WHOIS records of domains, two of them did so in historical WHOIS records according to the results of our Reverse WHOIS API queries. The results led to the discovery of 303 email-connected domains after duplicates and those already identified as IoCs were filtered out.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byIPv4.Global

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byRadix

Sponsored byCSC

Sponsored byVerisign
