


|
||
|
||
Early in September 2025, a coordinated effort between Cloudflare and Microsoft disrupted RaccoonO365, a Phishing-as-a-Service (PhaaS) criminal group. Cybercriminals had been paying to use the service since last year, racking up an estimated $100,000 in cryptocurrency for the threat group.
RaccoonO365 makes phishing easier, as cybercriminals use it to create fake emails and launch phishing websites—effectively eliminating the need for advanced technical skills and enabling them to steal more than 5,000 user credentials worldwide.
Hundreds of domains related to Raccoono365 had already been taken down, according to a threat brief published by Cloudflare. The brief also listed many indicators of compromise (IoCs), including three cryptocurrency addresses, 21 subdomains, and 77 domain names.
Our research team analyzed the domains tagged as IoCs, leading to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
First, we sought to learn more about the 77 domains tagged as RaccoonO365 IoCs by querying all of them on Bulk WHOIS API. We discovered that:
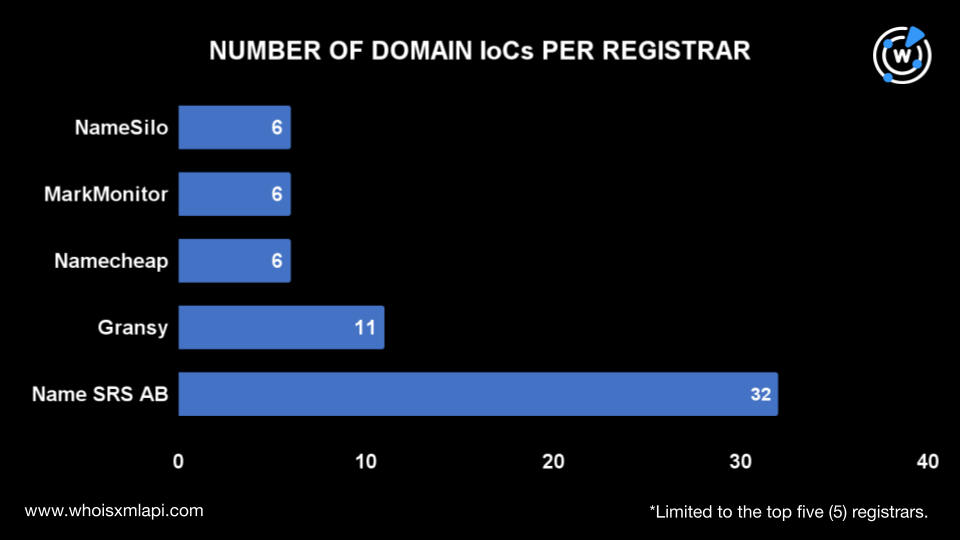
The top 5 registrars were Name SRS AB (32 domains), Gransy (11 domains), Namecheap (6 domains), MarkMonitor (6 domains), and NameSilo (6 domains). The remaining 15 domain IoCs were distributed across 11 other registrars. This includes GMO Internet (3 domains), PDR (2 domains), and Gname.com (2 domains). The registrars Enom, Nicenic International Group, Internet Domain Service, Tucows Domains, Hostinger, Key-Systems, OwnRegistrar, and Nordreg each accounted for one domain.
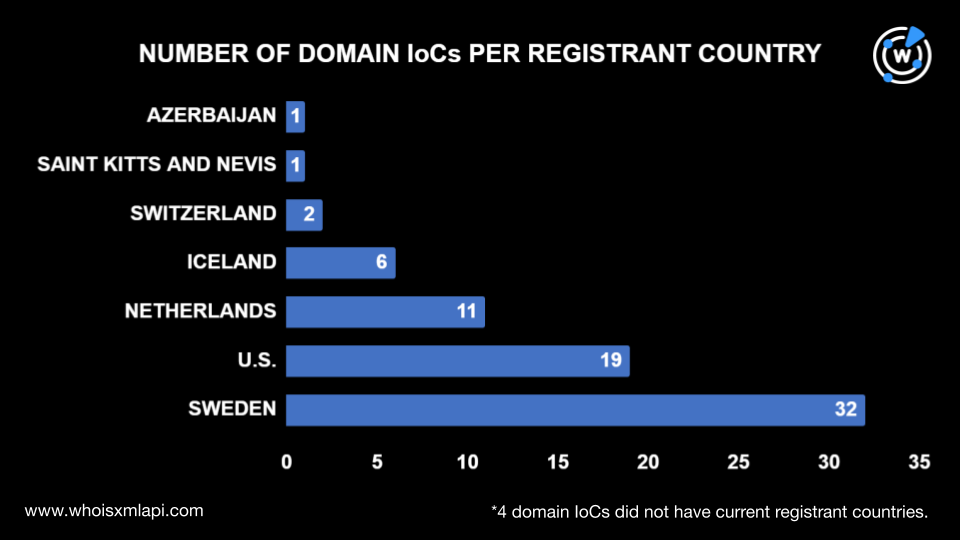
While four domains did not have registrant countries on record, 72 were spread out among seven nations. Sweden had the most number of domains, 32 to be exact, followed by the U.S., with 19 domains; the Netherlands, with 11; Iceland, with six; Switzerland, with two; and Saint Kitts and Nevis and Azerbaijan, each with one domain.
After scrutinizing their WHOIS details, we then examined the historical DNS resolutions of the domains flagged as RaccoonO365 IoCs.
A DNS Chronicle API query for the 77 domains revealed that 65 had 1,461 historical domain-to-IP resolutions. Five of the domains recorded resolutions that date back before their current WHOIS creation dates, indicating that the domains had been registered and dropped before the threat actors reregistered them for the RaccoonO365 campaign. Take a look at the DNS histories of the five domains below.
| DOMAIN IoC | NUMBER OF DOMAIN-TO-IP RESOLUTIONS | FIRST DOMAIN-TO-IP RESOLUTION DATE |
|---|---|---|
| bravoservicesnc[.]com | 294 | 5 February 2017 |
| keymedla[.]com | 121 | 6 September 2022 |
| lawsent[.]com | 29 | 5 November 2019 |
| man-ex[.]com | 34 | 6 February 2017 |
| winredirect[.]com | 186 | 28 April 2020 |
Aside from checking the WHOIS records and DNS activity of the IoCs, we also turned our attention to a subgroup of the domain IoCs published by Cloudflare that stood out for the presence of the text strings “o365” and “cloud.”
We found that all 10 domain IoCs containing the string “o365” appeared in the First Watch Malicious Domains Data Feed and were predicted to turn malicious 10—355 days before Cloudflare reported them as RaccoonO365 IoCs on 10 September 2025. Here are some details about five of the “o365” IoC subgroup below.
| DOMAIN IoCs | FIRST WATCH ADDITION DATE | NUMBER OF DAYS DEEMED LIKELY TO TURN MALICIOUS BEFORE REPORTING DATE |
|---|---|---|
| filesoo365cloudocxs[.]com | 31 August 2025 | 10 |
| priorityclouddrive365files[.]com | 20 August 2025 | 21 |
| fileso365clloudoccs[.]com | 18 August 2025 | 23 |
| o365cloudfilesstoragedcs[.]com | 17 August 2025 | 24 |
| o365microsoftsecurecloud[.]com | 6 August 2025 | 35 |
Our next endeavor was to find more artifacts—domains that are related to the RaccoonO365 IoCs, either through their WHOIS or DNS connections.
We queried the 77 domains identified as IoCs on WHOIS History API and found 150 unique email addresses from their historical WHOIS records. After filtering out anonymized email addresses, we were left with 17 public email addresses.
Five of those public email addresses didn’t appear in the historical WHOIS record of any domain based on the results of our Historical Reverse WHOIS API query, while four had more than 50 connected domains (an indication that the email address could be owned by a domainer or similar entity). That left us with eight public email addresses that appeared in the historical WHOIS record of 121 domains, after duplicates and IoCs were filtered out.
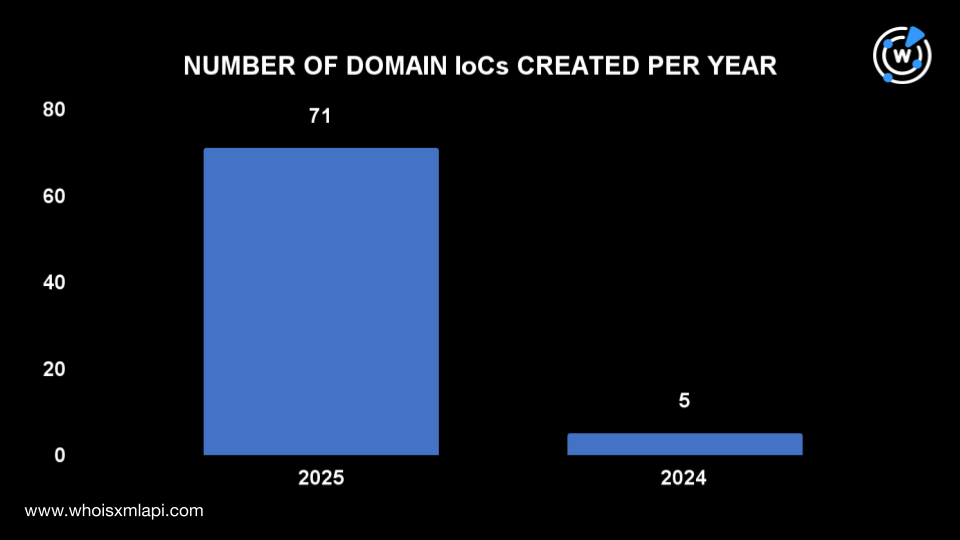
Earlier, we mentioned that 65 of the 77 domains tagged as RaccoonO365 IoCs had 1,461 historical domain-to-IP resolutions. Given that the PhaaS was mostly active just this year (71 of the domain IoCs were registered in 2025), we extracted the IP resolutions dated 1 January to 31 August 2025 using DNS Chronicle API.
This gave us a total of 88 IPv4 addresses and 75 IPv6 addresses, or a total of 163 IP addresses. Only four of those IP addresses were not flagged as malicious when we queried all 163 IPs on Threat Intelligence API.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byRadix

Sponsored byVerisign

Sponsored byCSC

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byIPv4.Global
