


|
||
|
||
Koi Security recently dove into the widely executed and highly coordinated GreedyBear crypto theft attack that used 150 weaponized Firefox extensions. According to the company, it utilized close to 500 malicious executables and dozens of phishing sites. The result? The threat actors have amassed more than US$1 million to date.
The company identified 18 domains as indicators of compromise (IoCs) in “GreedyBear: 650 Attack Tools, One Coordinated Campaign.” WhoisXML API dove deeper into the attack in a bid to uncover more information and new artifacts. Our in-depth analysis of the IoCs led to these discoveries:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
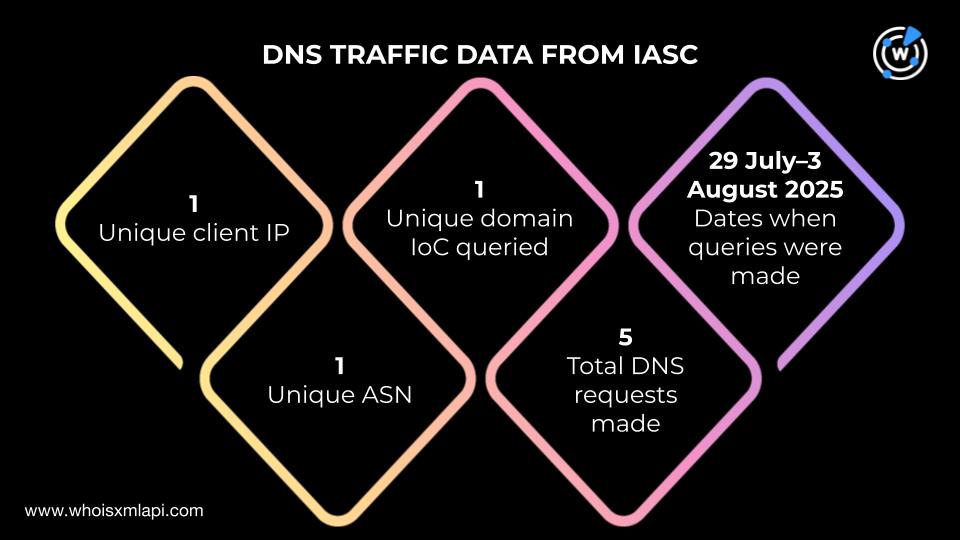
Sample DNS data obtained from IASC revealed that one unique client IP address under one unique Autonomous System number (ASN) communicated with one domain identified as an IoC via five DNS queries made between 29 July and 3 August 2025.
Meanwhile, First Watch Malicious Domains Data Feed files dated 18 May—6 July 2025 revealed that five domain IoCs were deemed likely to turn malicious 33—82 days before they were dubbed as IoCs on 8 August 2025. Take a look at more details below.
| DOMAIN IoC | DATE ADDED TO FIRST WATCH | NUMBER OF DAYS PRIOR TO REPORTING DATE |
|---|---|---|
| extprojectdev[.]top | 18 May 2025 | 82 |
| suirokboys[.]digital | 4 June 2025 | 65 |
| metahoper[.]digital | 11 June 2025 | 58 |
Now, on to a closer look at the WHOIS records of the 18 domains identified as IoCs. We queried them on Bulk WHOIS API and found out that:
The 11 active domains were administered by six different registrars led by PDR, which accounted for four IoCs. Two domains each, meanwhile, were registered with NiceNIC International Group and Web Commerce Communications. Finally, one domain each was handled by NameSilo, OwnRegistrar, and Tucows.

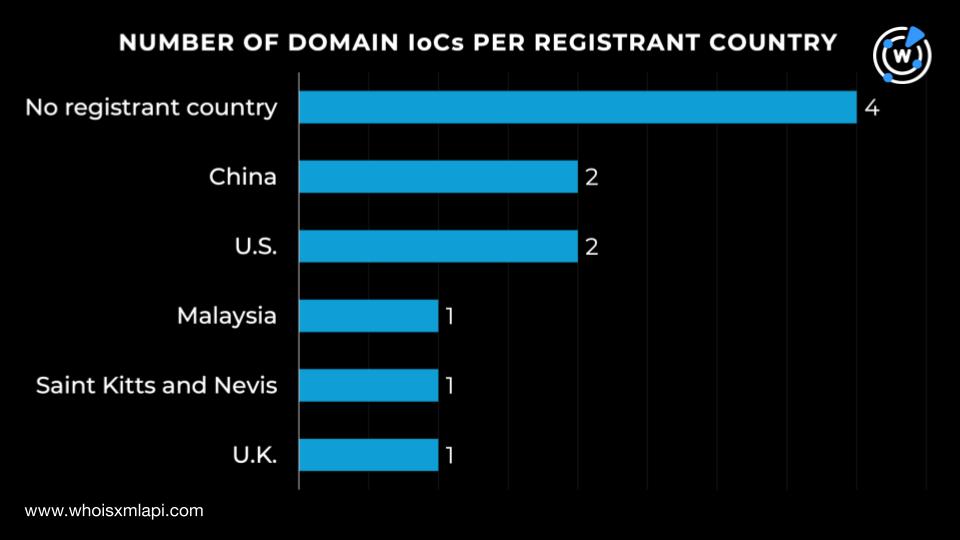
While four of the 11 domains with current WHOIS records did not have registrant countries on record, the remaining seven were registered in five different countries. China and the U.S. led the pack of countries, accounting for two IoCs each. Finally, Malaysia, Saint Kitts and Nevis, and the U.K. accounted for one each.
After that, we took a closer look at the DNS histories of the 18 domains identified as IoCs. DNS Chronicle API showed that 13 had 255 domain-to-IP resolutions over time. The IoC snipersol[.]com recorded 178 resolutions from 29 April 2017 to date. Take a look at the DNS histories of five other domains below.
| DOMAIN IoC | NUMBER OF DOMAIN-TO-IP RESOLUTIONS | FIRST DOMAIN-TO-IP RESOLUTION DATE |
|---|---|---|
| ventroxibnk[.]com | 28 | 24 June 2025 |
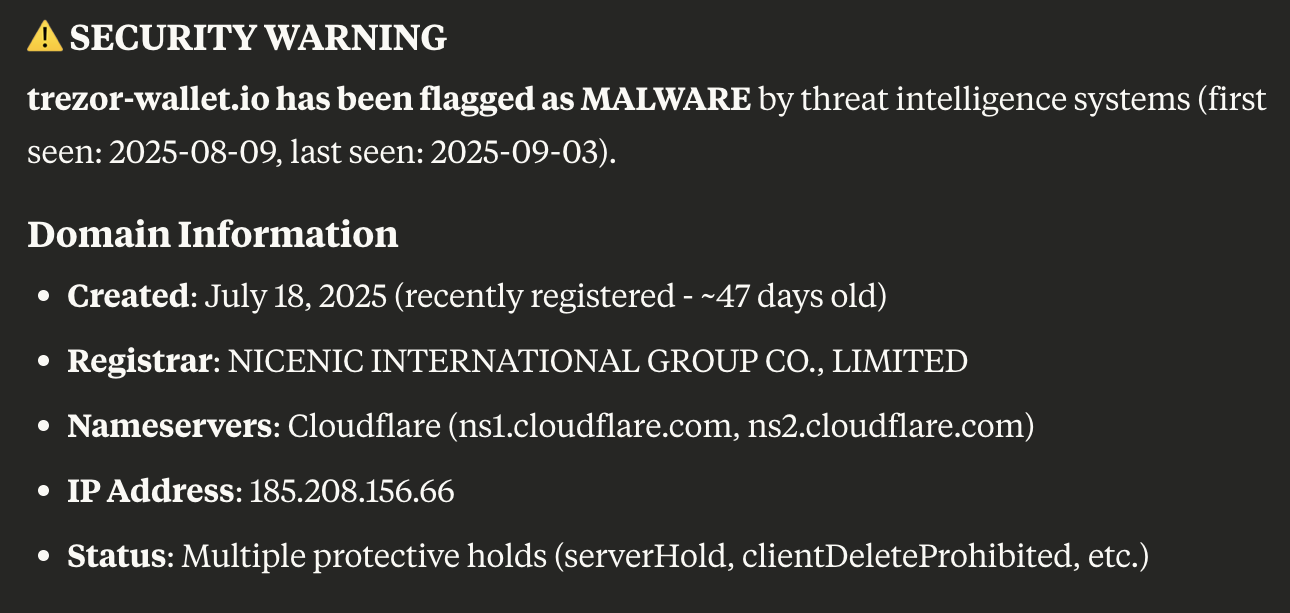
| trezor-wallet[.]io | 19 | 1 December 2018 |
| filecoinwallet[.]net | 9 | 19 November 2021 |
| avalancheproject[.]digital | 5 | 10 April 2025 |
| exodlinkbase[.]digital | 4 | 12 June 2025 |
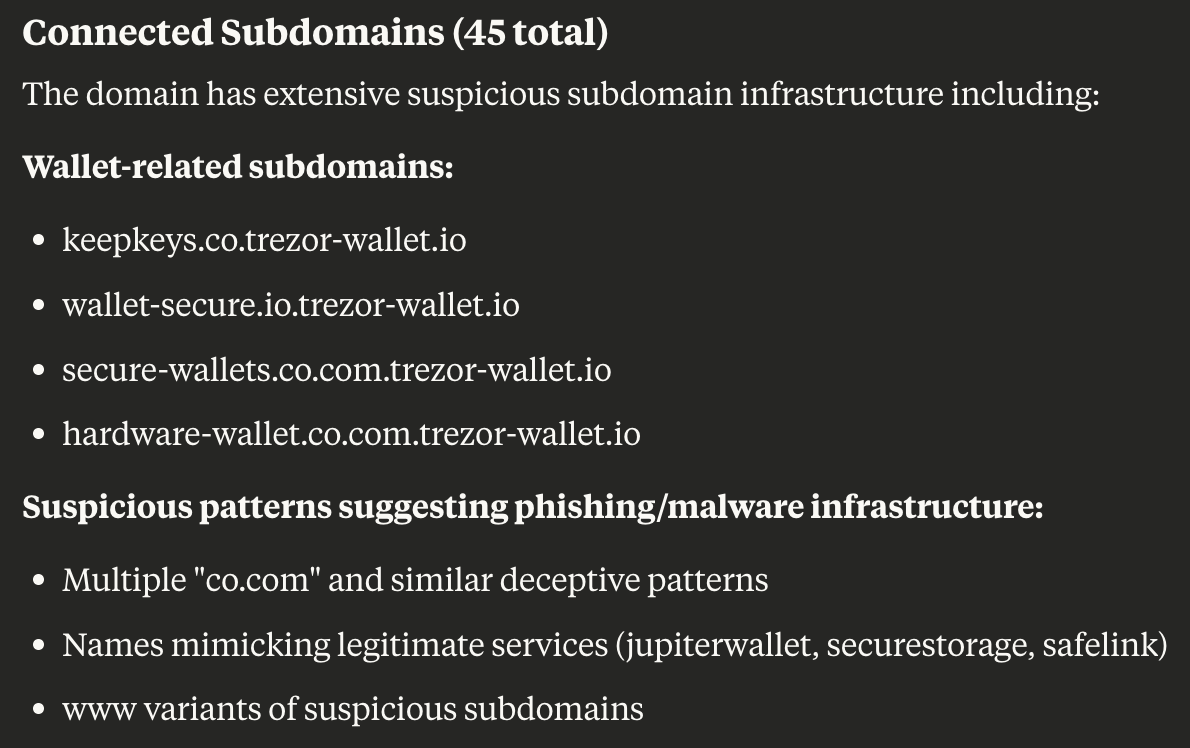
We further zoomed in on the domain trezor-wallet[.]io, which could be riding on the popularity of legitimate domain trezor[.]io via the WhoisXML API MCP Server. The prompt “find all assets connected to trezor-wallet[.]io” revealed these interesting nuggets:
The site has 45 subdomains, many of which were crypto wallet-related. The subdomains were, however, suspicious in that they could be mimicking the names of other popular wallets.
We began our search for new artifacts by querying the 18 domains identified as IoCs on WHOIS History API. Three of them had email addresses in their historical WHOIS records. Specifically, three IoCs had nine unique email addresses, one of which was public.
A Reverse WHOIS API query for the public email address enabled us to uncover one email-connected domain—bonkpunk[.]com—after duplicates and those already identified as IoCs were filtered out.
Next, we queried the 18 domains identified as IoCs on DNS Lookup API and discovered that 10 actively resolved to four unique IP addresses.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byRadix

Sponsored byVerisign

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byCSC

Sponsored byIPv4.Global

Sponsored byWhoisXML API
