


|
||
|
||
The email-image file attachment combo has been a well-utilized phishing vector over time. In a recent attack, however, threat actors distributed malware-laced Scalable Vector Graphics (SVG) in place of the typical Portable Network Graphics (PNG) or Joint Photographic Experts Group (JPEG/JPG) files. The malicious files allowed attackers to take remote control of victims’ devices to collect sensitive information, hijack computing resources, and deliver additional malware.
FortiGuard Labs identified 26 indicators of compromise (IoCs) comprising 25 domains and one IP address connected to the threat. Further investigation of the IoCs led to these discoveries:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
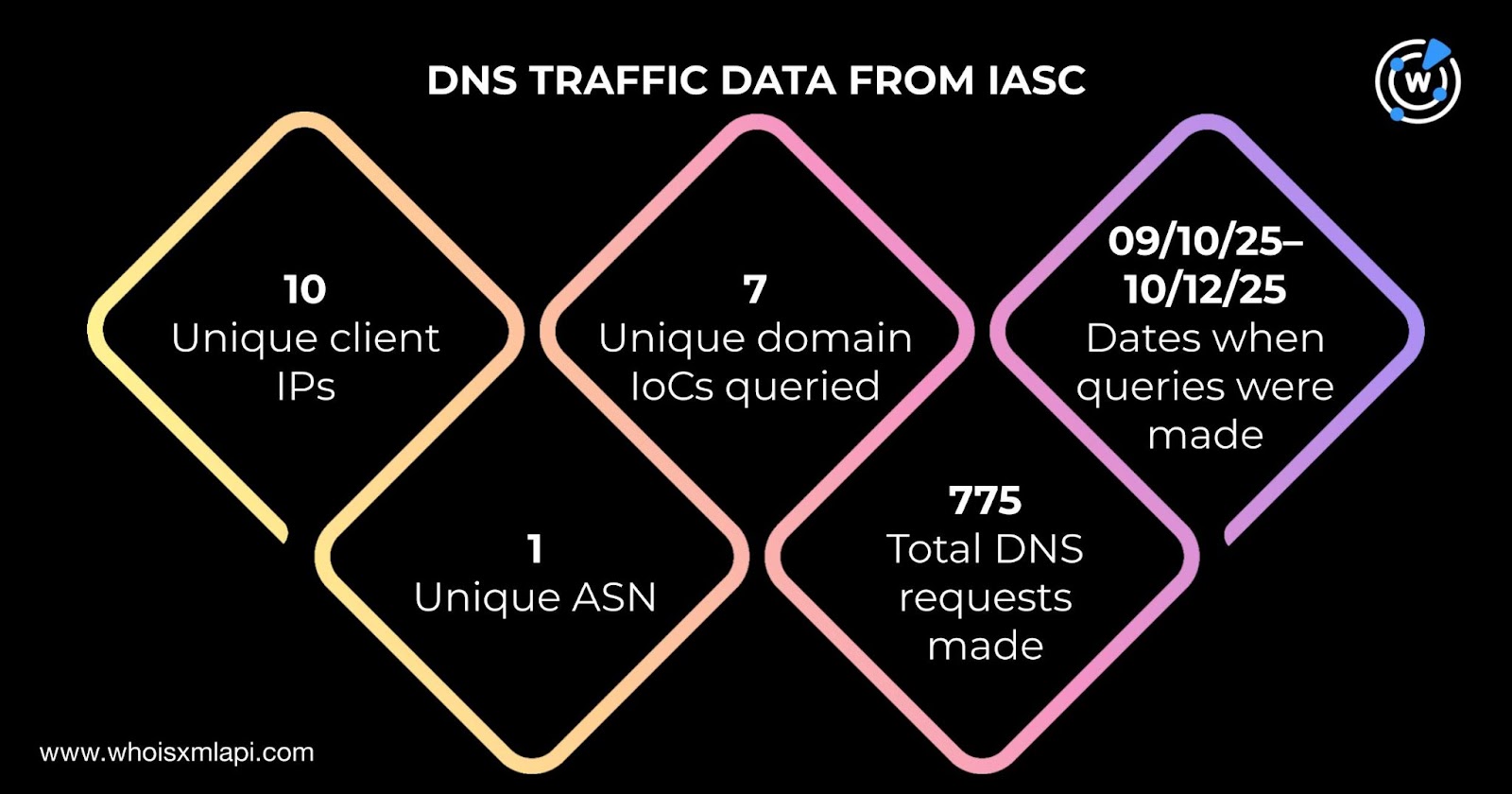
Sample network traffic data from the Internet Abuse Signal Collective (IASC) enabled us to discern that 10 unique client IP addresses communicated with seven distinct domains identified as IoCs via 775 DNS queries made on 10 September—12 October 2025. In addition, the 10 IP addresses fell under a single Autonomous System number (ASN).
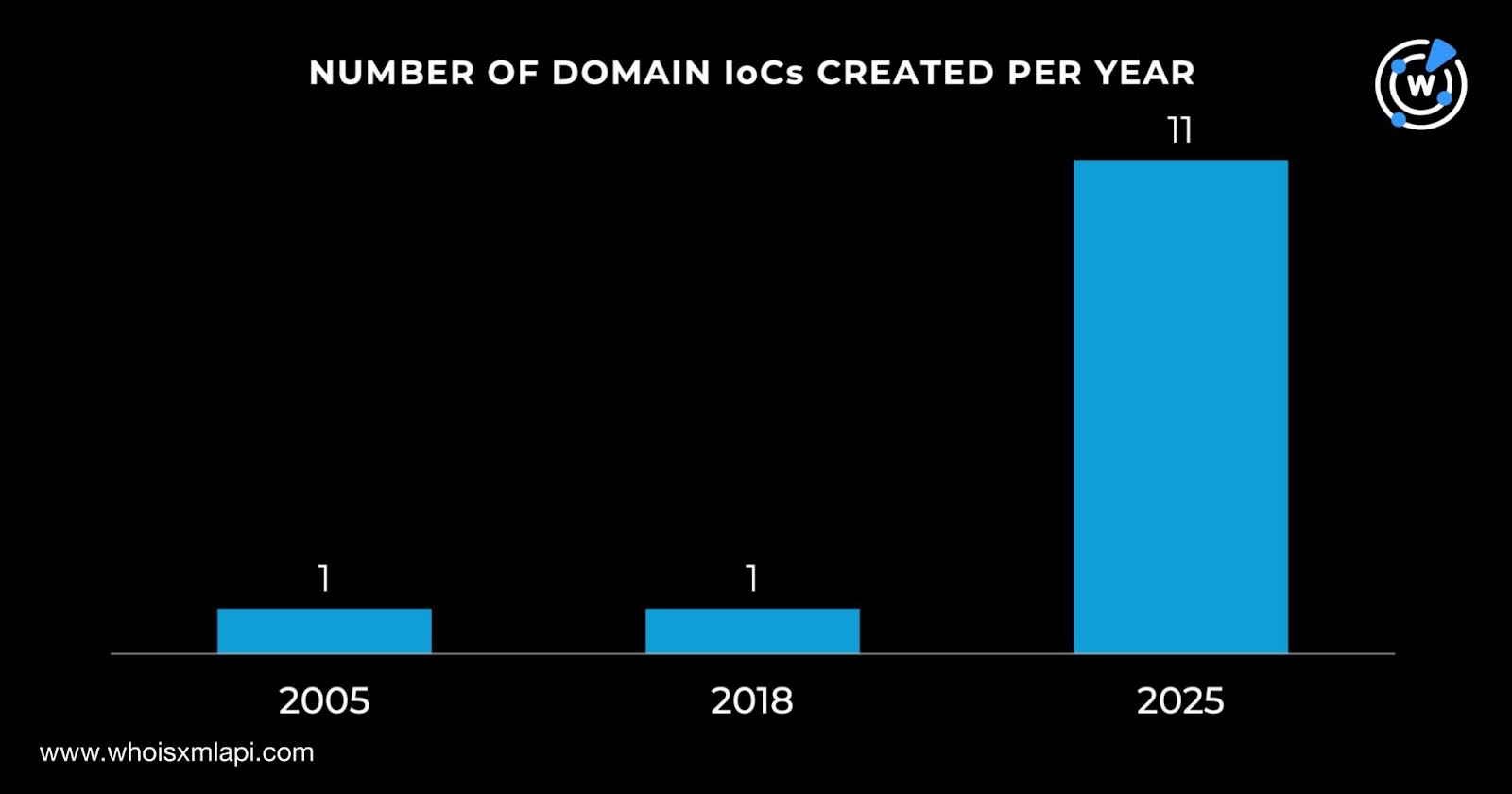
We used our diverse set of tools this time starting with a query for the 25 domains identified as IoCs on First Watch Malicious Domains Data Feed. We discovered that nine of them were deemed likely to turn malicious 14—105 days prior to being reported as such on 26 September 2025. Take a look at more details for five of the IoCs that appeared on the feed.
| DOMAIN IoC | DATE DEEMED LIKELY TO TURN MALICIOUS | NUMBER OF DAYS BETWEEN FEED APPEARANCE AND REPORTING DATES |
|---|---|---|
| ms-team-ping2[.]com | 13 June 2025 | 105 |
| ms-team-ping3[.]com | 9 July 2025 | 79 |
| ms-team-ping4[.]com | 21 July 2025 | 67 |
| npulvivgov[.]cfd | 4 August 2025 | 53 |
| amaprox[.]click | 7 August 2025 | 50 |
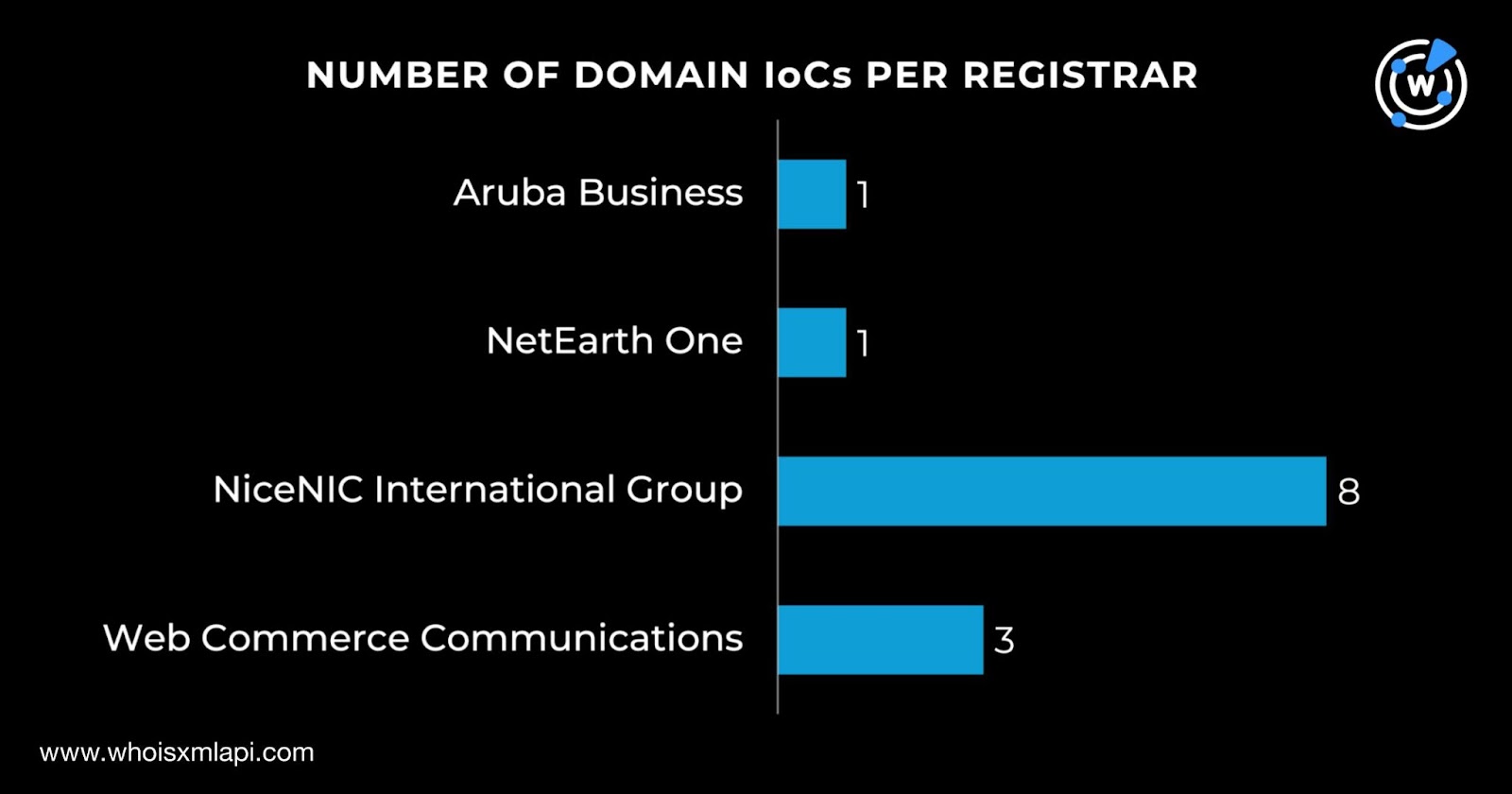
Next, we queried the 25 domains identified as IoCs on WHOIS API and found out that 13 had current WHOIS records. We discovered that:
NiceNIC International Group topped the list of registrars, accounting for eight of the domains tagged as IoCs. Web Commerce Communications administered three domains while one domain each fell under the purview of Aruba Business and NetEarth One.
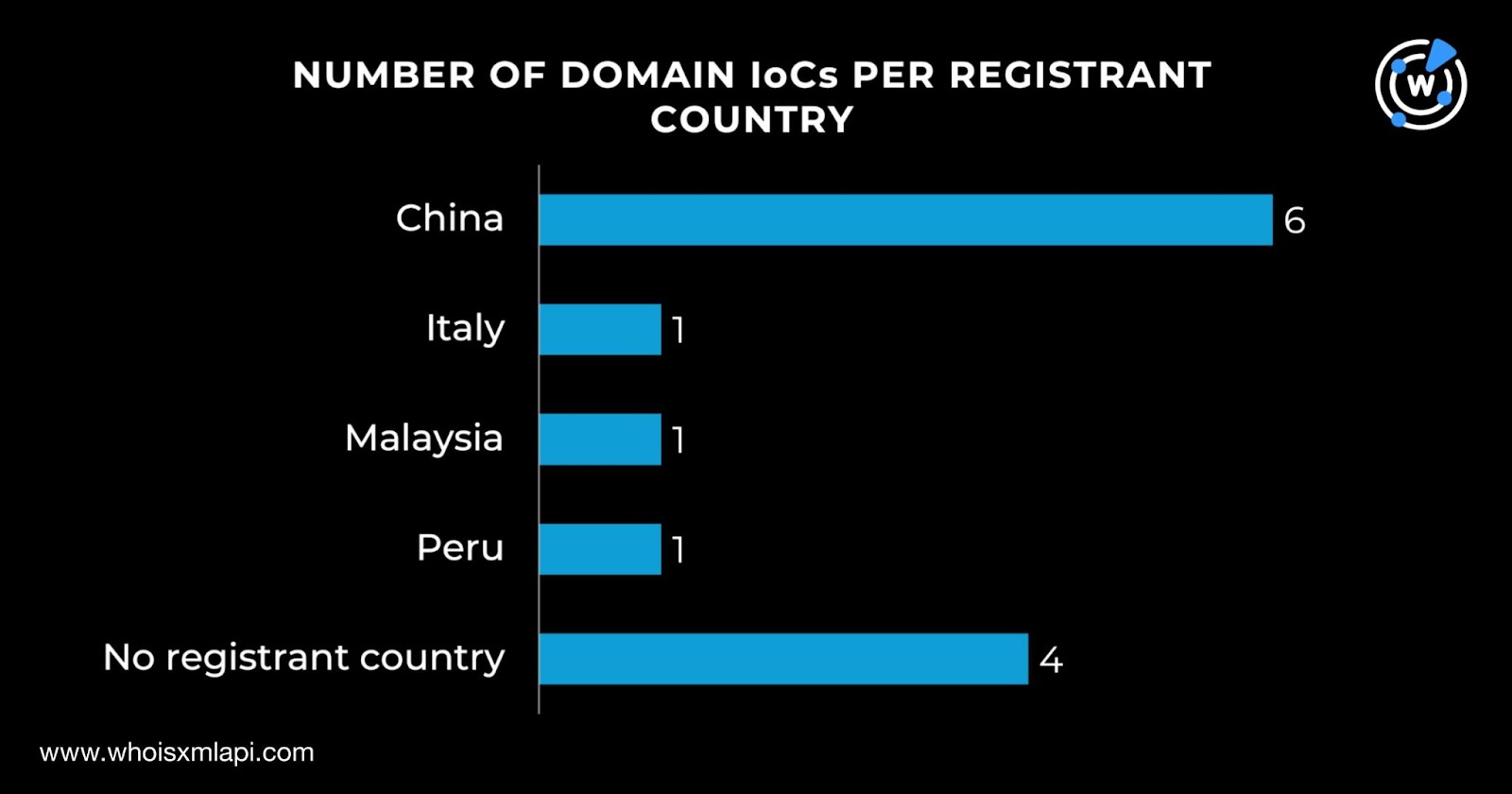
Finally, while four of the 13 domains did not have registrant countries on record, six were registered in China. One domain each was registered in Italy, Malaysia, and Peru.
A DNS Chronicle API query for the 25 domains identified as IoCs revealed that 13 had 1,124 domain-to-IP resolutions. The domain acqua-tecnica[.]it, with 297 records, posted the oldest resolution on 5 February 2017. Here are details for five other domains.
| DOMAIN IoC | NUMBER OF DOMAIN-TO-IP RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE |
|---|---|---|---|
| phuyufact[.]com | 240 | 16 August 2019 | 23 September 2025 |
| ms-team-ping3[.]com | 182 | 10 July 2025 | 28 September 2025 |
| ms-team-ping6[.]com | 107 | 25 August 2025 | 28 September 2025 |
| ms-team-ping4[.]com | 62 | 21 July 2025 | 28 September 2025 |
| ms-team-ping2[.]com | 56 | 14 June 2025 | 28 September 2025 |
Next, we queried the sole IP address identified as an IoC on the WhoisXML API MCP Server using the prompt “Use IP Geolocation API to determine the geolocation country and ISP of 109.176.207.110.” The result revealed that it was geolocated in the Netherlands under the administration of Nasstar.

According to a DNS Chronicle API query, meanwhile, the sole IP address identified as an IoC had 100 IP-to-domain resolutions from 7 July 2024 to 20 September 2025.
We began our search for connected artifacts by querying the 25 domains identified as IoCs on WHOIS History API. That allowed us to uncover one public email address in the historical WHOIS record of one domain.
A Reverse WHOIS API query for the sole public email address led to the discovery of 22 email-connected domains after filtering out duplicates and those already identified as IoCs.
Next, we queried the 25 domains identified as IoCs on DNS Lookup API and found out that 10 resolved to 18 unique IP addresses on top of that already tagged as an IoC.
A Threat Intelligence API query for the 18 additional IP addresses revealed that all of them have already figured in various malicious campaigns.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byDNIB.com

Sponsored byRadix

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byCSC

Sponsored byVerisign

Sponsored byWhoisXML API
