


|
||
|
||
Fortinet discovered a search engine optimization (SEO) poisoning campaign targeting Chinese-speaking users in August 2025. They investigated the threat and found out that the attackers manipulated search rankings with SEO plug-ins and registered look-alike domains that closely mimicked legitimate software sites. Victims ended up installing Hiddengh0st and Winos variants into their computers.
The researchers identified 13 indicators of compromise (IoCs)—five domains, four subdomains, and four IP addresses—in “SEO Poisoning Attack Targets Chinese-Speaking Users with Fake Software Sites.”
After further scrutiny (i.e., extracting the domains from the subdomains), we excluded the legitimate web properties from the original IoC list and ended up with nine IoCs—five domains and four IP addresses—for our DNS footprint investigation. Our analysis led to these discoveries:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
Before uncovering more information about the nine IoCs using our intelligence sources, we sought to learn more about the IoCs, specifically the two subdomains—bucket00716[.]s3[.]ap-southeast-2[.]amazonaws[.]com and znrce3z[.]oss-ap-southeast-1[.]aliyuncs[.]com—we excluded from our main analysis since their domains were legitimate and probably abused. According to Virus Total, both were indeed malicious.
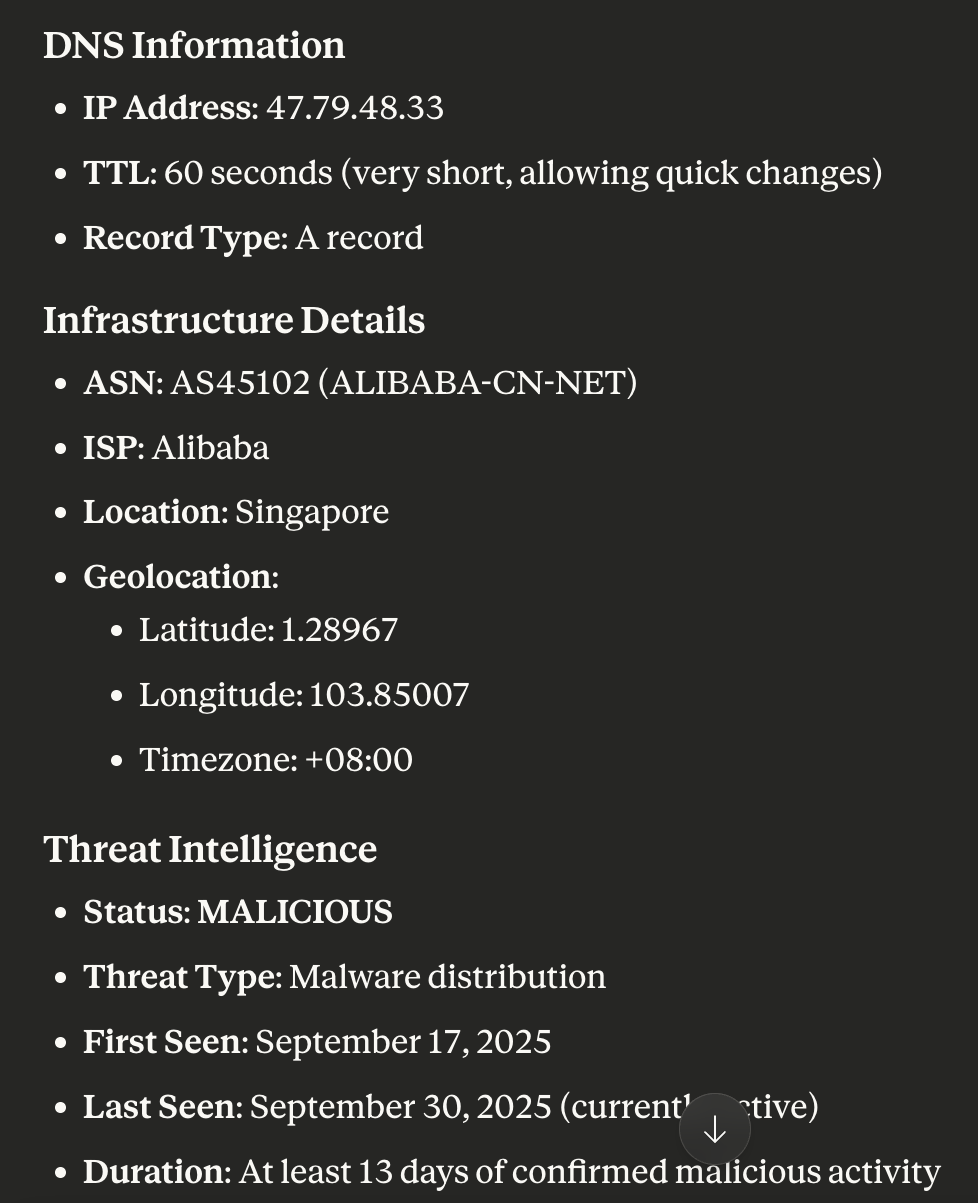
Our search for all the information our homegrown tools can find about bucket00716[.]s3[.]ap-southeast-2[.]amazonaws[.]com via the WhoisXML API MCP Server not only confirmed the subdomain’s malicious nature but also revealed that it was active between 17—30 September 2025.
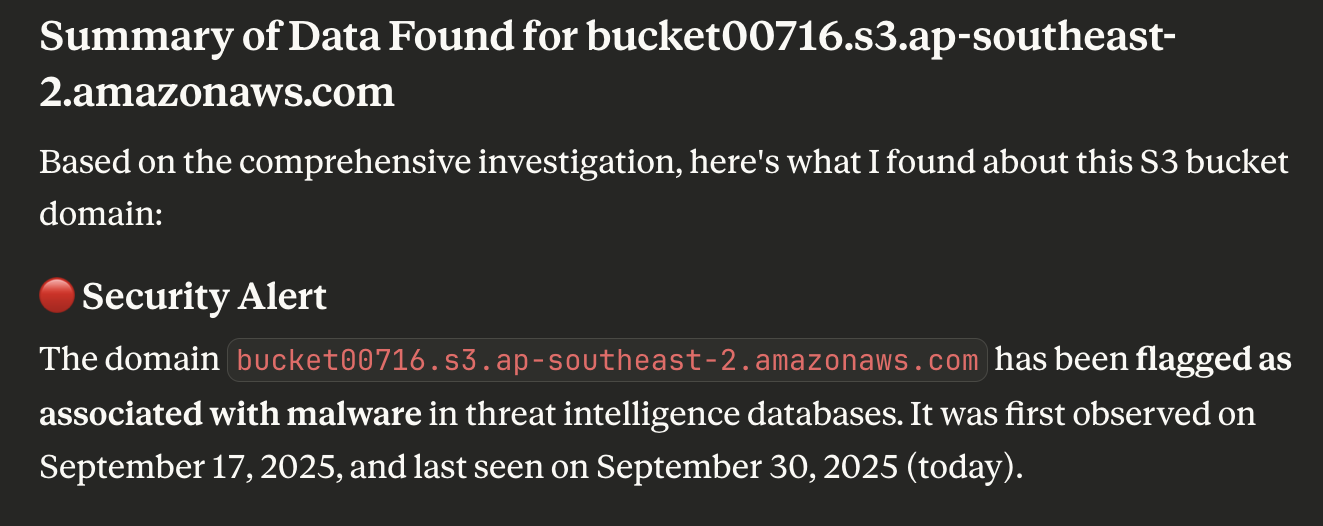
The WhoisXML API MCP Server told us that znrce3z[.]oss-ap-southeast-1[.]aliyuncs[.]com was also indeed malicious, has been active since 17 September 2025 to date, and has a short time-to-live (TTL) value—60 seconds.
We began by querying the five domains identified as IoCs via the WhoisXML API MCP Server using the prompt “Get the createdDate, registrarName, registrant_country of aisizhushou.com, c4p11.shop, deepl-fanyi.com, telegramni.com, wps1.com using WHOIS API.”
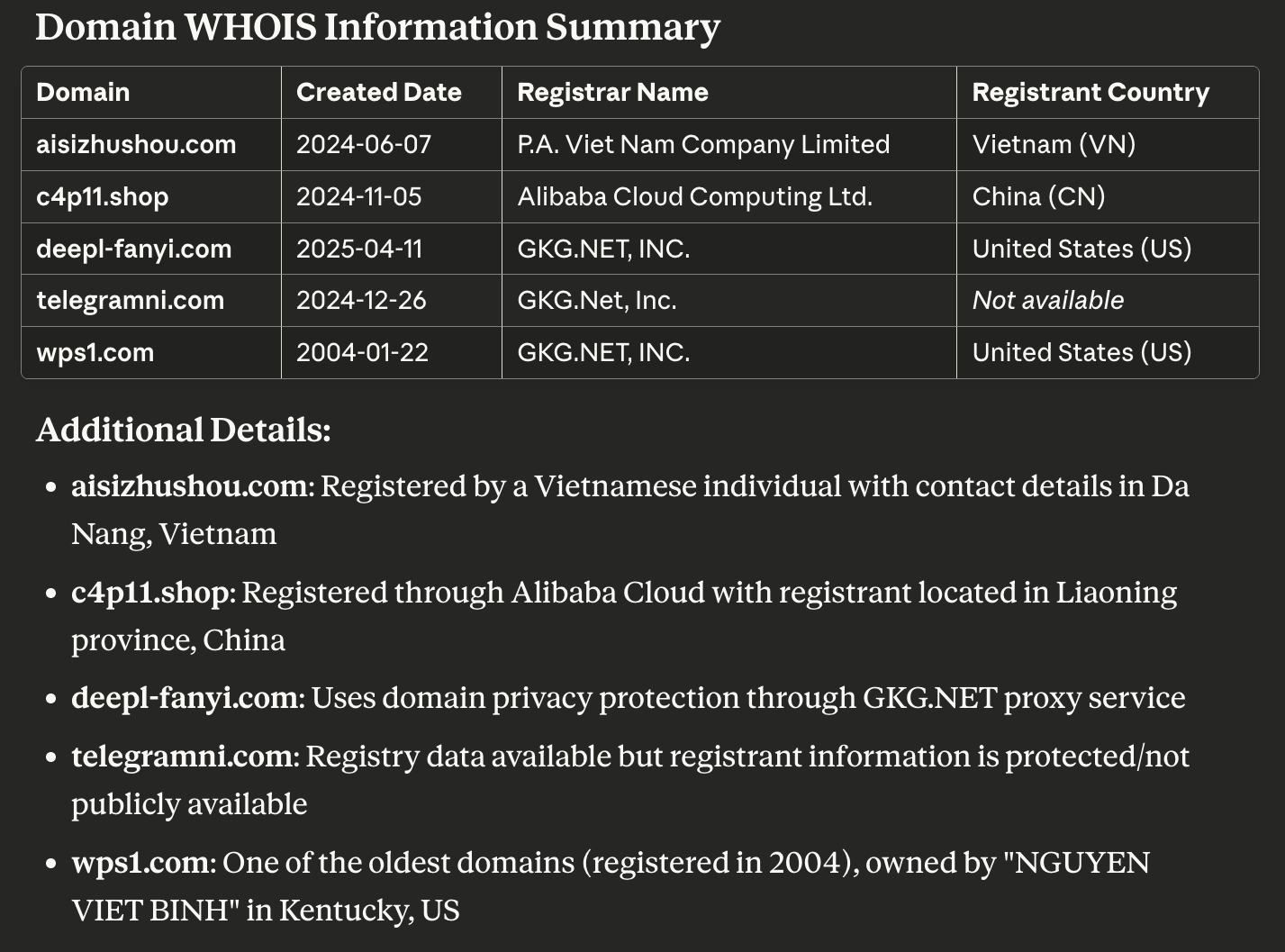
We discovered that:
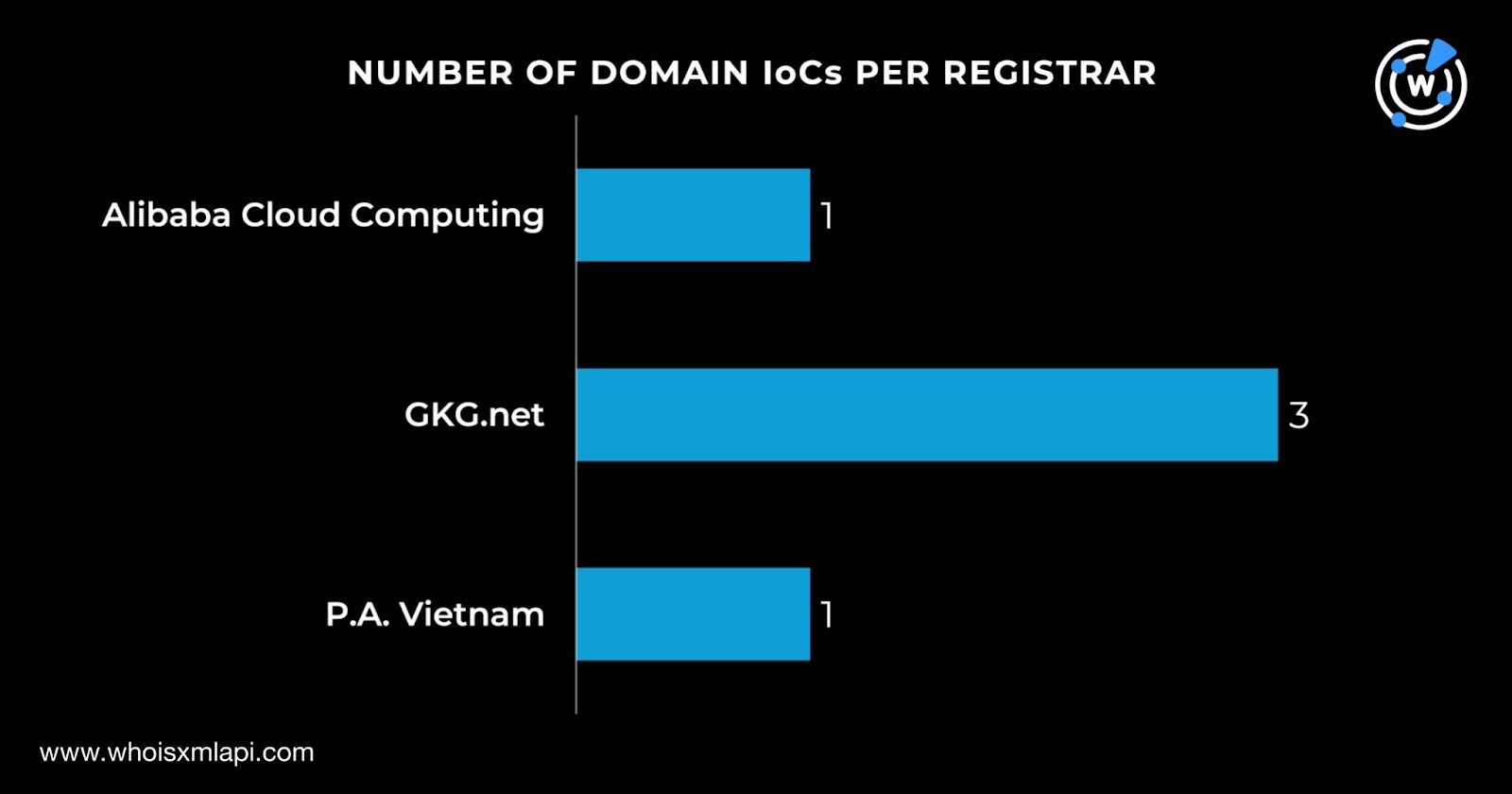
They were administered by three registrars—one by Alibaba Cloud Computing, three by GKG.net, and one by P.A. Vietnam.
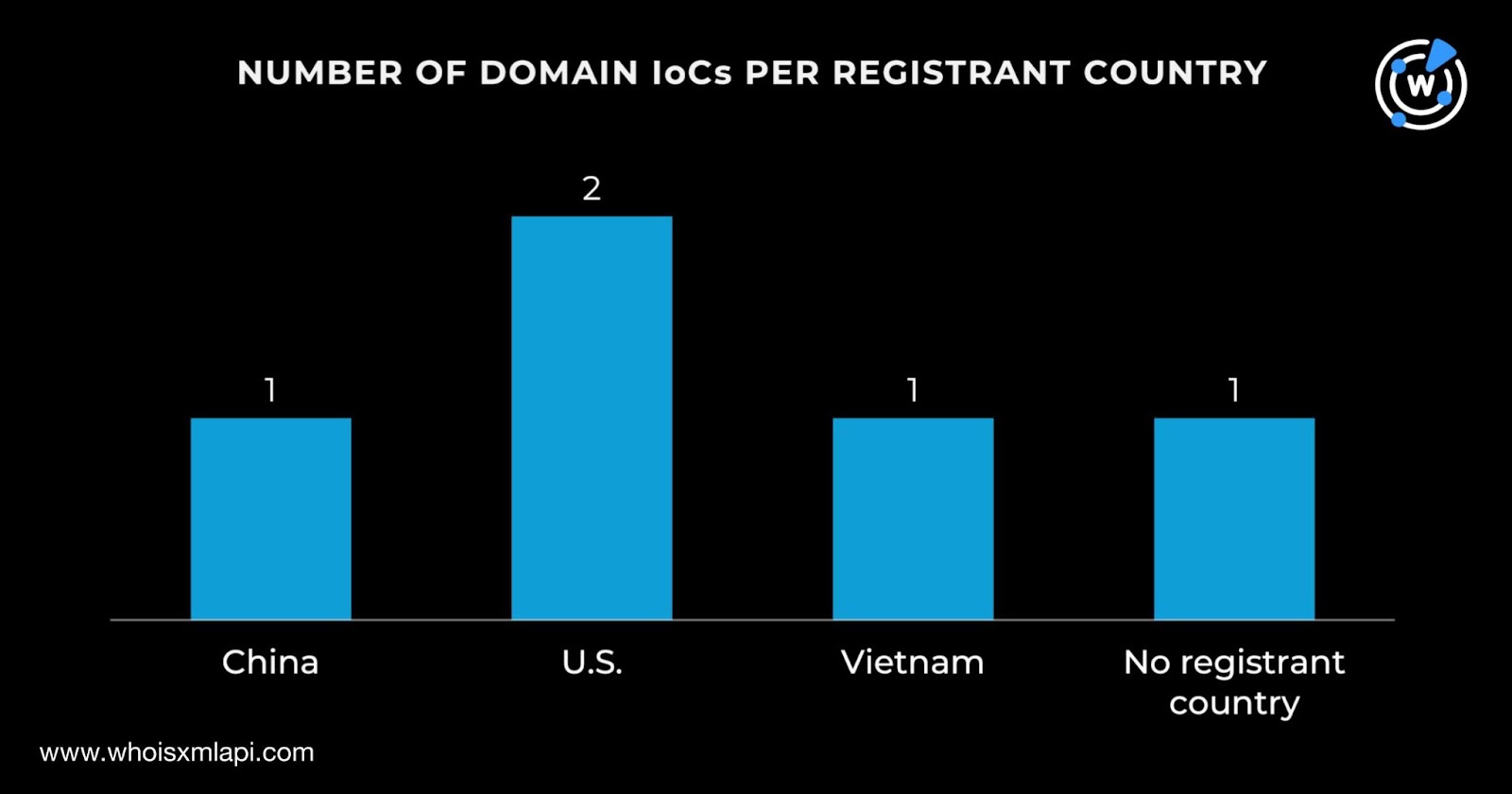
While one domain did not have a registrant country on record, the remaining four were registered in three countries—one in China, two in the U.S., and one in Vietnam.
A DNS Chronicle API query for the five domains identified as IoCs revealed that only four had DNS histories. They had 494 historical domain-to-IP resolutions. The domain aisizhushou[.]com posted the oldest resolution on 5 February 2017. Take a look at more information below.
| DOMAIN IoC | NUMBER OF RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE |
|---|---|---|---|
| aisizhushou[.]com | 161 | 5 February 2017 | 26 September 2025 |
| wps1[.]com | 272 | 7 February 2017 | 27 August 2025 |
| telegramni[.]com | 46 | 17 April 2023 | 1 September 2025 |
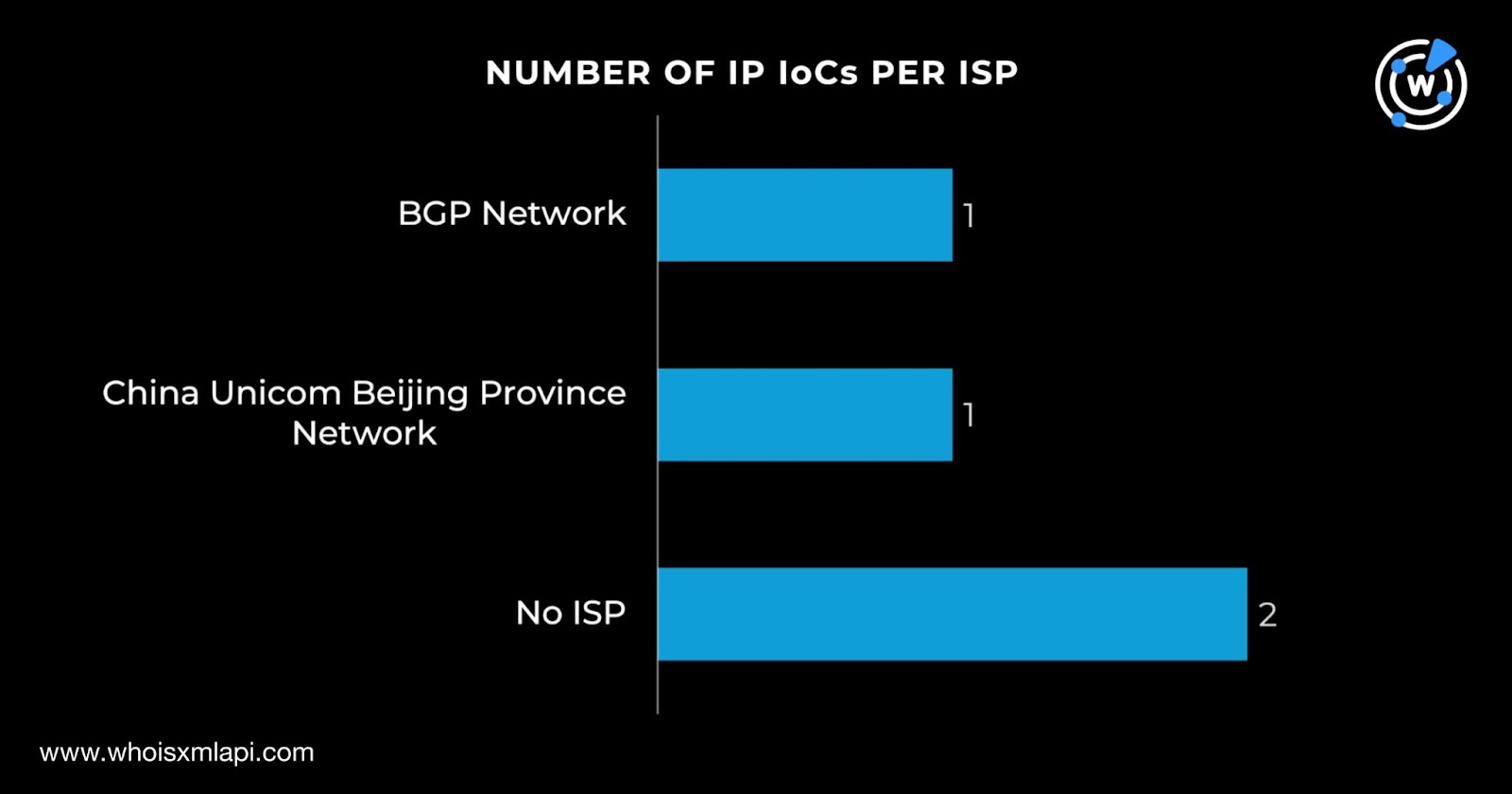
Next, we queried the four IP addresses identified as IoCs on Bulk IP Geolocation Lookup and discovered that:
A DNS Chronicle API query for the four IP addresses identified as IoCs revealed that only three had DNS histories. They had 1,593 historical IP-to-domain resolutions over time. The IP address 137[.]220[.]152[.]99 posted the oldest resolution on 4 December 2019. Take a look at more information for each IP address below.
| IP IoC | NUMBER OF RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE |
|---|---|---|---|
| 137[.]220[.]152[.]99 | 418 | 4 December 2019 | 22 November 2020 |
| 202[.]95[.]8[.]47 | 1,000 | 22 August 2020 | 19 January 2023 |
| 27[.]124[.]13[.]32 | 525 | 22 August 2020 | 27 October 2021 |
To uncover more connected artifacts, we began by querying the five domains identified as IoCs on WHOIS History API. They had 17 unique email addresses in their historical WHOIS records, six of which were public.
A Reverse WHOIS API query for the six public email addresses revealed none of them appeared in current WHOIS records although all did so in historical records. It is worth noting, however, that two could belong to domainers so we excluded their connections from our findings. This query led to the discovery of 7,741 email-connected domains after duplicates and those already identified as IoCs were filtered out.
Next, we queried the five domains identified as IoCs on DNS Lookup API. We found out that they actively resolved to eight unique IP addresses, none of which were on the IoC list.
A Threat Intelligence API query for the eight additional IP addresses showed that seven were malicious.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byCSC
