


|
||
|
||
Fox-IT and the NCC Group have conducted multiple incident response cases involving a Lazarus subgroup specifically targeting organizations in the financial and cryptocurrency sectors. The subgroup has been linked to AppleJeus, Citrine Sleet, UNC47363, and Gleaming Pisces and uses different remote access Trojans (RATs) known as “PondRAT5,” “ThemeForestRAT,” and “RemotePE.”
The researchers analyzed the three RATs in great depth in “Three Lazarus RATs Coming for Your Cheese.” They also identified 19 domains and two IP addresses as indicators of compromise (IoCs) in the process.
WhoisXML API dug deeper into the three RATs’ DNS infrastructure, which led to these discoveries:
One unique client IP address communicated with one distinct domain IoC based on sample traffic data from the Internet Abuse Signal Collective (IASC)
Two unique alleged victim IP addresses communicated with two distinct IP IoCs according to sample IASC traffic data
A sample of the additional artifacts obtained from our analysis is available for download from our website.
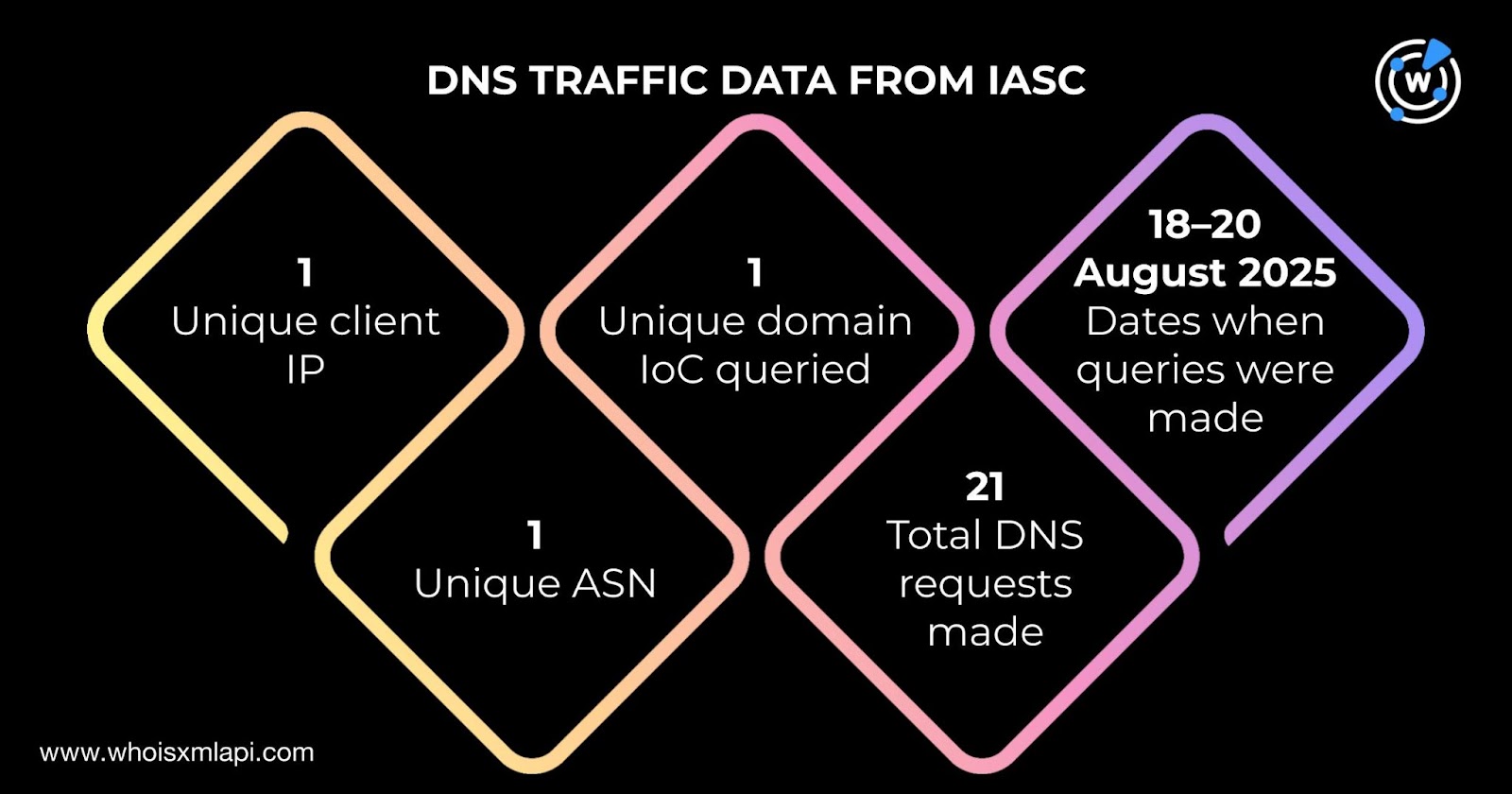
Sample network traffic data from IASC showed that one unique client IP address under one distinct Autonomous System number (ASN) queried one unique domain IoC via 21 DNS queries between 18 and 20 August 2025.
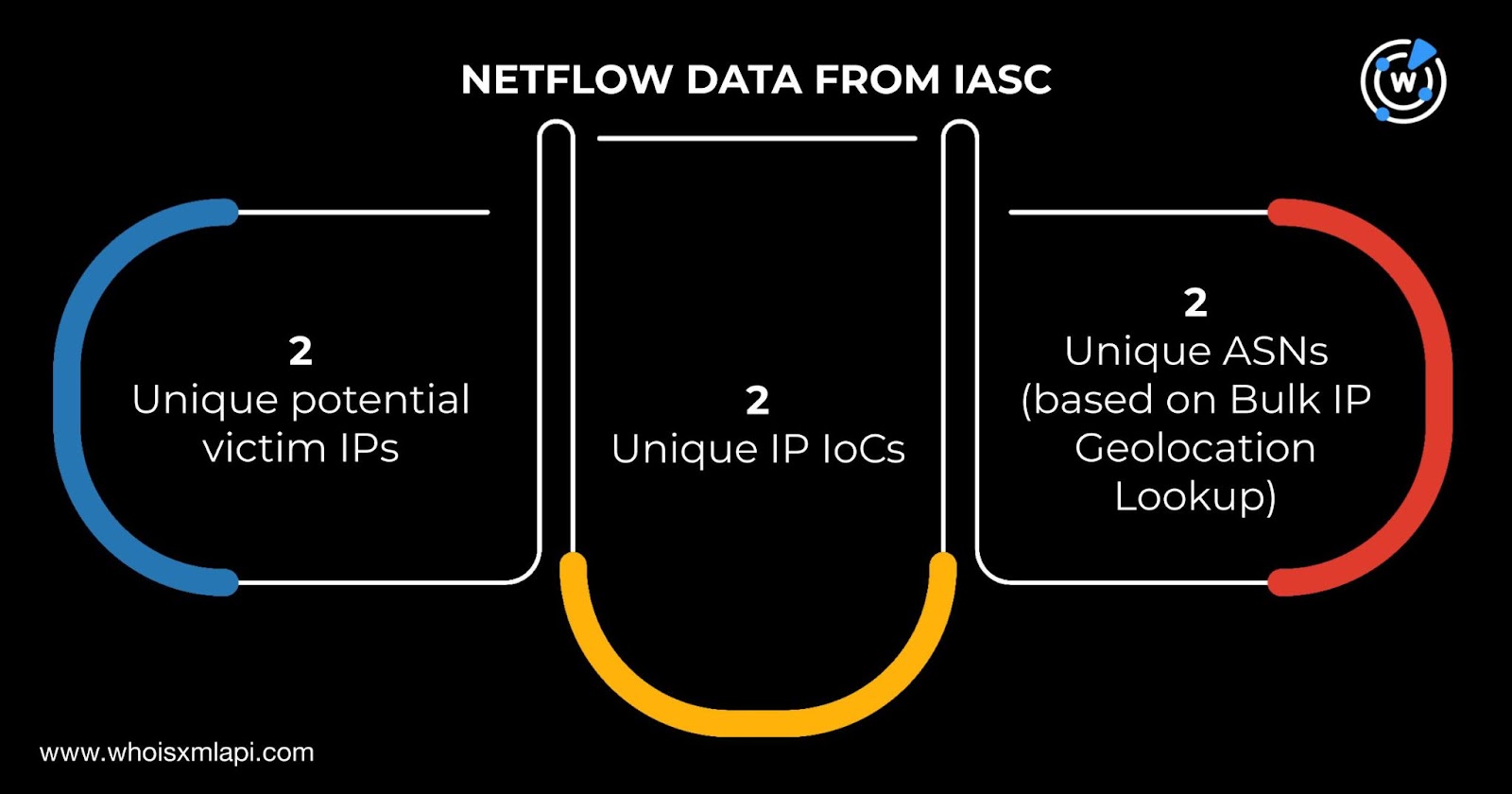
Sample network traffic IASC data also revealed that two unique alleged victim IP addresses communicated with two distinct IP IoCs under two unique ASNs based on the results of a Bulk IP Geolocation Lookup query.
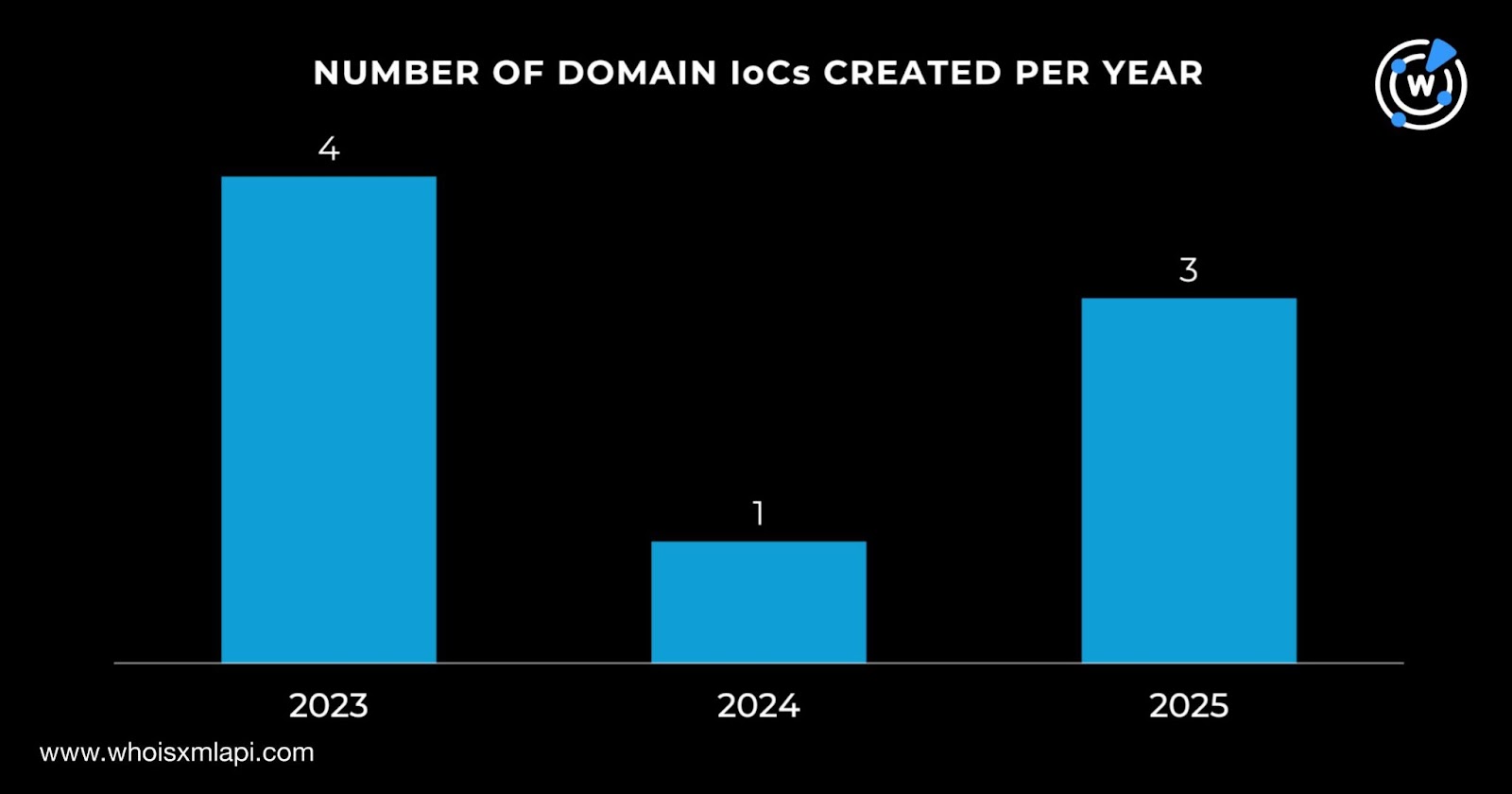
The First Watch Malicious Domains Data Feed query results for the 19 domains tagged as IoCs showed that one domain IoC—keondigital[.]com—was dubbed likely to turn malicious 189 days before it was identified as such on 1 September 2025. It was specifically added to First Watch on 24 February 2025.
We then queried the 19 domains tagged as IoCs on WHOIS API and discovered that only eight had current WHOIS records. Of these:
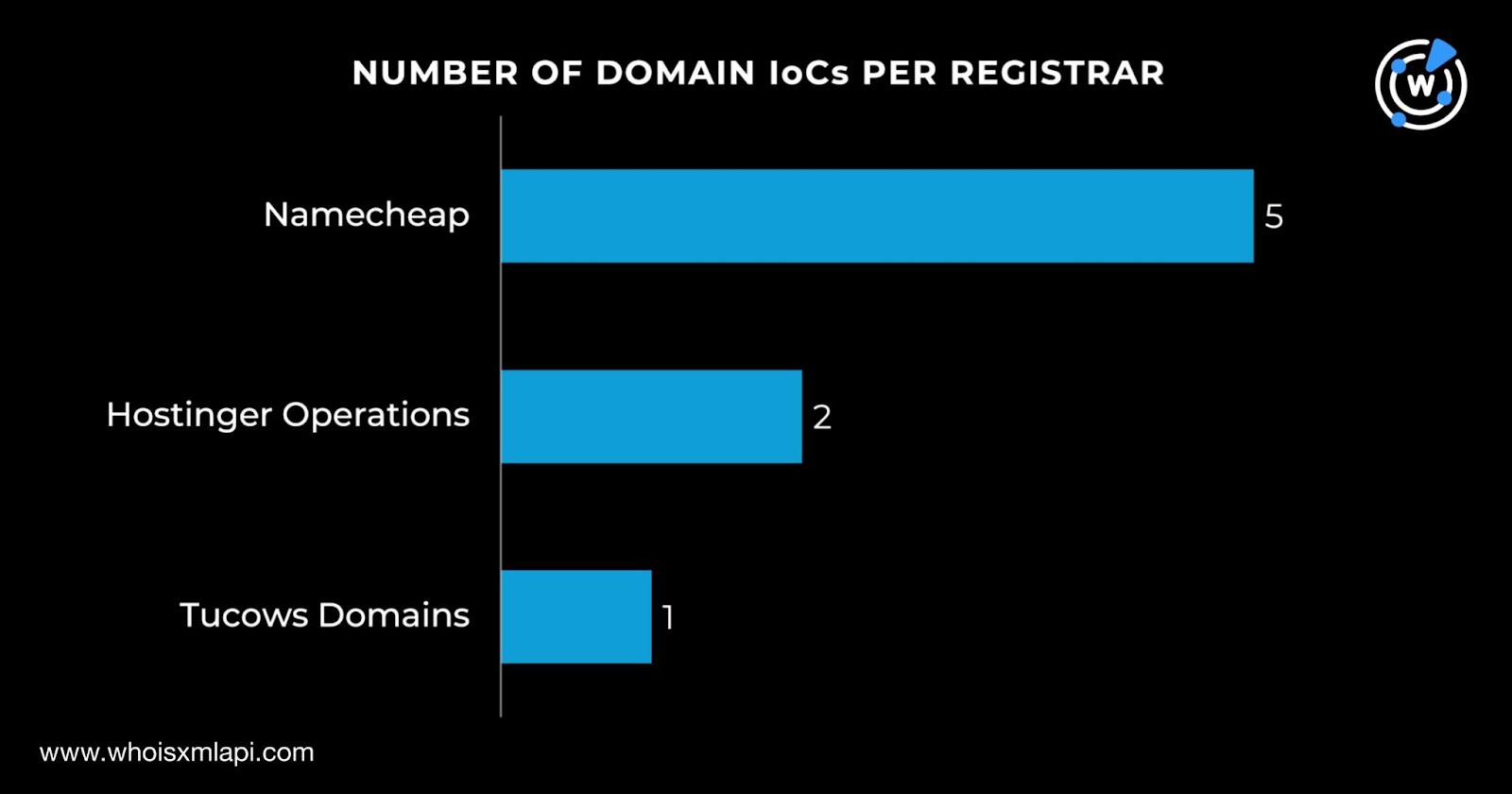
They were administered by three different registrars led by Namecheap, which accounted for five domain IoCs. Hostinger Operations took the second spot with two domains, followed by Tucows Domains with one domain in third place.
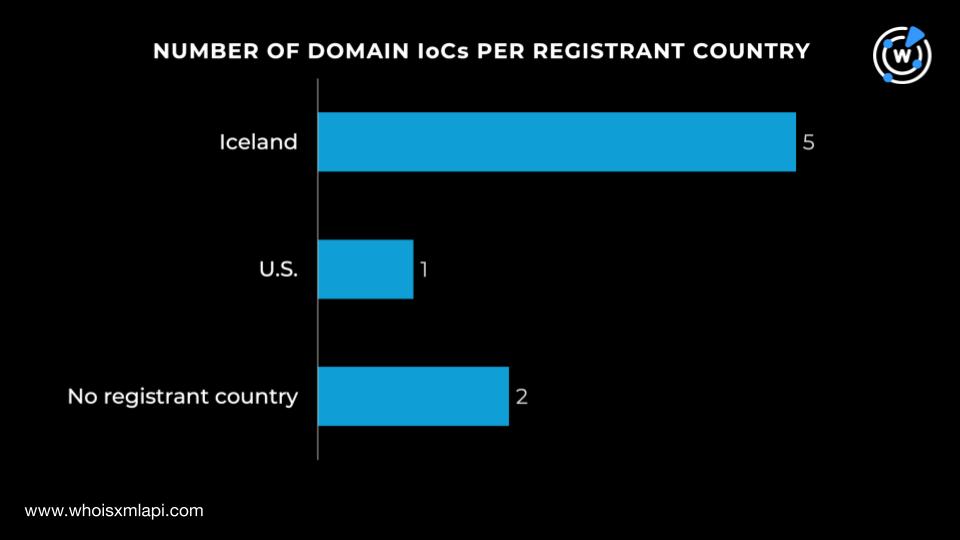
While two domain IoCs did not have registrant countries on record, the remaining six were registered in two countries. Five were registered in Iceland while one was registered in the U.S.
A query for the 19 domains tagged as IoCs on DNS Chronicle API revealed that all had rich DNS histories. They had 665 domain-to-IP resolutions over time since 5 February 2017. This indicates possible use for malicious campaigns between 2017 and 2025. Take a look at specific examples below.
| DOMAIN IoC | TOTAL NUMBER OF DOMAIN-TO-IP RESOLUTIONS | FIRST RESOLUTION DATE | LAST RESOLUTION DATE(prior to data gathering) |
|---|---|---|---|
| arcashop[.]org | 125 | 5 February 2017 | 23 July 2025 |
| plexisco[.]com | 92 | 6 February 2017 | 9 January 2023 |
| oncehub[.]co | 130 | 7 May 2020 | 2 September 2024 |
| lmaxtrd[.]com | 8 | 25 November 2020 | 13 August 2021 |
| calendly[.]live | 74 | 5 March 2021 | 18 May 2025 |
From the table above, we can discern that while the domain IoCs lmaxtrd[.]com, oncehub[.]co, and plexisco[.]com may not be in active use as of this writing, they were certainly so between 2020 and 2021, 2020 and 2024, and 2017 and 2023, respectively. These dates could potentially be connected to their weaponization for attacks.
Next, we queried the two IP addresses tagged as IoCs on Bulk IP Geolocation Lookup and found out that while they were both geolocated in the U.S. (consistent with the list of registrant countries), only one had an ISP on record—GWY IT.

A DNS Chronicle API query for the two IP addresses tagged as IoCs showed that both had DNS histories. Together, they had 685 IP-to-domain resolutions over time. Specifically, the IP address 192[.]52[.]166[.]253 posted 682 resolutions from 6 February 2017 to 4 September 2025. Note the similarity in timing, spanning 2017 to 2025, with some of the domain IoCs.
We began our search for new artifacts by querying the 19 domains tagged as IoCs on WHOIS History API. We found out that 14 had 24 unique email addresses in their historical WHOIS records. Only one of the email addresses was public.
We then queried the public email address on Reverse WHOIS API and discovered that while it did not appear in any other domain’s current WHOIS record, it was found in the historical WHOIS record of one email-connected domain—kmc-ksa[.]com—after duplicates and those already identified as IoCs were filtered out.
Next, a DNS Lookup API query for the 19 domains tagged as IoCs revealed that nine actively resolved to nine unique additional IP addresses after duplicates and those already identified as IoCs were filtered out.
A Threat Intelligence API query for the nine additional IP addresses showed that eight have already been flagged as malicious in connection to various threats.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byCSC

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byVerisign

Sponsored byRadix

Sponsored byDNIB.com

Sponsored byWhoisXML API
