
Messaging Anti-Abuse Working Group (MAAWG) has issued the first best practices aimed at helping the global ISP industry work more closely with consumers to recognize and remove bot infections on end-users' machines. The paper outlines a three-step approach with recommendations for detecting bots, notifying users that their computers have been compromised, and guiding them in removing the malware. more
A team of developers including .SE (The Internet Infrastructure Foundation), LNetLabs, Nominet, Kirei, SURFnet, SIDN and John Dickinson have come together to create open source software, called OpenDNSSEC, to make it easier to deploy DNSSEC. Patrik Wallström, responsible for DNSSEC at .SE comments: "In order to spread the use of DNSSEC to an increased number of domain names, the management surrounding this technology must be simplified. Together with a number of collaborators, we're developing OpenDNSSEC. Leveraging our deployment experience, we will produce a well-packaged, easy-to-use and flexible DNSSEC tool that eliminates all manual procedures. Those in charge of name servers no longer need detailed knowledge about the protocol in order to use it." more
A recent survey of security professionals by RSA Conference with regards to critical security threats and infrastructure issues currently faced, revealed budgetary constrains as the top challenge currently faced. According to reports, the study suggests that even though practitioners are most concerned about email phishing and securing mobile devices, technologies addressing these needs are at risk of being cut from IT budgets. 72% percent of respondents indicated a rise in email-borne malware and phishing attempts since Fall 2008, with 57% stating they have seen an increase in Web-borne malware. Concerns about zero-day attacks and rogue employees as a result of layoffs were cited by 28% and 26% of survey respondents, respectively. more
A research paper commissioned by the International Commission on Nuclear Non-proliferation and Disarmament (ICNND) suggests that nuclear command and control systems are vulnerable to cyber terrorism. "Despite claims that nuclear launch orders can only come from the highest authorities, numerous examples point towards an ability to sidestep the chain of command and insert orders at lower levels," says the report. more
 The IPv6 Act Now website, aimed at encouraging the adoption of IPv6, has featured a video today on Google's implementation of IPv6, which resulted in the launch of ipv6.google.com. In this video, Lorenzo Colitti, network engineer at Google, explains the planning, deployment, and future plans for making Google services available over IPv6. The best way to proceed with an IPv6 deployment, Colitti says is "to run everything on the same infrastructure." more
The IPv6 Act Now website, aimed at encouraging the adoption of IPv6, has featured a video today on Google's implementation of IPv6, which resulted in the launch of ipv6.google.com. In this video, Lorenzo Colitti, network engineer at Google, explains the planning, deployment, and future plans for making Google services available over IPv6. The best way to proceed with an IPv6 deployment, Colitti says is "to run everything on the same infrastructure." more
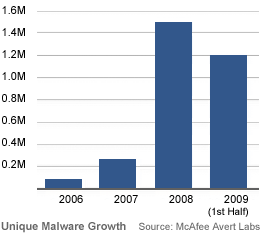 Security researches report seeing as much unique malware in the first half of 2009 as seen in all of 2008. "This is quite something when you consider that in 2008 we saw the greatest ever growth in malware," says David Marcus of McAfee Avert Labs. More specifically, Marcus in a blog post writes that the numbers add up to an average of 200,000 unique pieces malware monthly or more than 6,000 a day. "Bear in mind these are malware we consider unique (something we had to write a driver for) and does not count all the other malware we detect generically or heuristically... When you add in the generic and heuristic detections the number becomes truly mind boggling," writes Marucs. more
Security researches report seeing as much unique malware in the first half of 2009 as seen in all of 2008. "This is quite something when you consider that in 2008 we saw the greatest ever growth in malware," says David Marcus of McAfee Avert Labs. More specifically, Marcus in a blog post writes that the numbers add up to an average of 200,000 unique pieces malware monthly or more than 6,000 a day. "Bear in mind these are malware we consider unique (something we had to write a driver for) and does not count all the other malware we detect generically or heuristically... When you add in the generic and heuristic detections the number becomes truly mind boggling," writes Marucs. more
The SEACOM submarine cable, completed in the past 24 hours, is the first modern submarine cable connecting to eastern Africa, and the first of an unprecedented wave of new cable projects on both the eastern and western coasts of Africa. Approximately USD2.4 billion in new submarine cable projects are scheduled for completion by the end of 2011. The plans for so many new cables reflect both Africa's lack of international communications infrastructure, and soaring capacity requirements. more
In light of recent announcements regarding Cameroon's country code Top-Level Domain, .CM, being opened to public registration, Tresa Baldas reports on Law.com: "Trademark attorneys are warning companies about a new target for cybersquatters known as '.cm,' which is the country code -- or top level domain -- for the West African nation of Cameroon. The dot-cm domain is a hot target for scammers, they say, due to 'cm' being a common typographical error for 'com' in the popular dot-com domain. Attorneys say this is significant to brand owners because Internet users searching for brand owners' Web sites frequently mistype dot-com as dot-cm and wind up on a bogus site. Not only is Web traffic lost, they say, but a brand name can get diluted or tainted along the way." (Also see, Nation of Cameroon Typo-Squats the Entire .com Space from 2006) more
A report released today by Public Knowledge points out that their recent analysis indicates filtering Internet content, as advocated by media companies, will not be effective and in fact harmful to the Internet. An accompanying 60-page whitepaper contains the full report including a number of reasons why the user of copyright filters should not be allowed, encouraged or mandated on U.S. Internet Service Provider (ISP) networks. more
According to a recent study, broadband Internet access is now considered by many US households a necessity and they turn to broadband Internet during recession. The study released by Jonathan Orszag, Robert Willig, and Mark Dutz suggests that with $32 billion gains in 2008, consumers increasingly benefit from using broadband at home. "Once people get a taste of the entertainment, educational opportunities, social networking and everyday services that broadband access facilitates, they grasp the immense value it can add to their lives as a powerful tool, regardless of where they come from," said Co-Chairman of the Internet Innovation Alliance Bruce Mehlman. "Once a broadband user, always a broadband user." more
The Canadian Press reports: "Most Canadians support the idea of Internet traffic management as long as all users are treated fairly, a new poll suggests. The Canadian Press Harris-Decima poll found only about one in five of those surveyed had heard of Internet traffic management or "traffic shaping," a contentious issue now before the federal regulator... Sixty per cent of survey respondents said they found the practice reasonable as long as customers are treated fairly, while 22 per cent said Internet management is unreasonable regardless." more
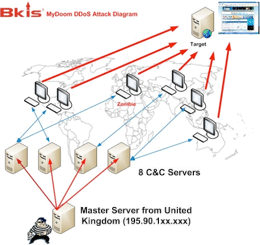 Nguyen Minh Duc, senior security director at Bach Khoa Internetwork Security (Bkis), says that the source of recent cyberattack against US and South Korean government websites was not North Korea -- as widely reported -- but UK. Based on Bkis analysis, a report today by Nguyen Minh Duc says that a master server located in UK was found to control the 8 Command and Control servers responsible for the series of cyberattacks last week.
Nguyen Minh Duc, senior security director at Bach Khoa Internetwork Security (Bkis), says that the source of recent cyberattack against US and South Korean government websites was not North Korea -- as widely reported -- but UK. Based on Bkis analysis, a report today by Nguyen Minh Duc says that a master server located in UK was found to control the 8 Command and Control servers responsible for the series of cyberattacks last week.
more
Andrew Colley of Australian IT reports the AusRegistry, the operator of Australia's Top-Level Domain (.au), has revealed that it has been approached by various groups planning to submit applications to ICANN for the creation of adult-themed generic Top-Level Domains (gTLDs) such as .xxx and .sex. According to the report, the Australian Communications Minister Stephen Conroy has opposed the idea syaing: "The government does not support the creation of the .xxx TLD." As it has been reported extensively on CircleID, previous attempts to create adult related TLDs (such as .xxx) have so far been rejected by ICANN. more
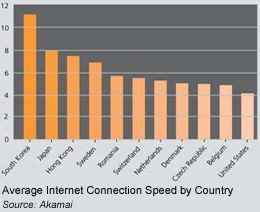 In the "Sate of the Internet Report" released by Akamai for the first quarter of 2009, the company reports that, on a global basis, the average connection speed increased by approximately 11% and more than 120 countries had average connection speeds under 1 Mbps (report based on date Q4 2008 through Q1 2009). Through Akamai's view of the Internet traffic (reported at approximately 1 billion users per day), the company also notes that in the first quarter of 2009, Japan had the highest percentage of connections (57%) at speeds above 5 Mbps while South Korea fell to second place for high broadband connectivity in the first quarter. more
In the "Sate of the Internet Report" released by Akamai for the first quarter of 2009, the company reports that, on a global basis, the average connection speed increased by approximately 11% and more than 120 countries had average connection speeds under 1 Mbps (report based on date Q4 2008 through Q1 2009). Through Akamai's view of the Internet traffic (reported at approximately 1 billion users per day), the company also notes that in the first quarter of 2009, Japan had the highest percentage of connections (57%) at speeds above 5 Mbps while South Korea fell to second place for high broadband connectivity in the first quarter. more
In a post today on Comcast's blog, Chris Griffiths, DNS Engineering Manger, has informed customers that they have begun to role a DNS redirection service -- a controversial service offered by several other ISPs over the years to redirect mistyped URLs to ad-based pages instead of a typical 404 error page. The service called "Domain Name Helper Service" is being launched as a market trial in Arizona, Colorado, New Mexico, Oregon, Texas, Utah, and Washington according to the company. more
Sponsored byCSC

Sponsored byWhoisXML API

Sponsored byDNIB.com

Sponsored byRadix

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byVerisign
