

Jared Newman reporting in PC World: "Wounded from a court decision that stopped the government from regulating Internet service providers, the Federal Communications Commission has announced a new way to gain some control over the broadband industry. The proposal would let the FCC treat Internet transmissions like telephone communications, entailing more oversight, but would prevent government control over Web services, applications and e-commerce sites." more
 Announced in a blog post today, ICANN's Manager of Root Zone Services, Kim Davies, reports: "Today the first three production non-Latin top-level domains were placed in the DNS root zone. ... The three new top-level domains are ????????. (“Al-Saudiah”), ??????. ( “Emarat”) and ???. (“Misr”). All three are Arabic script domains, and will enable domain names written fully right-to-left. Expect more as we continue to process other applications using the “fast track” methodology." more
Announced in a blog post today, ICANN's Manager of Root Zone Services, Kim Davies, reports: "Today the first three production non-Latin top-level domains were placed in the DNS root zone. ... The three new top-level domains are ????????. (“Al-Saudiah”), ??????. ( “Emarat”) and ???. (“Misr”). All three are Arabic script domains, and will enable domain names written fully right-to-left. Expect more as we continue to process other applications using the “fast track” methodology." more
 CNN Live interviews ICANN Senior Director of Internationalized Domain Names (IDNs) on issues related to new IDN developments. The interview includes overview of extending top-level domains to enable TLDs such as .com, .cn (for China), and .gr (for Greece) available in their native languages and scripts. more
CNN Live interviews ICANN Senior Director of Internationalized Domain Names (IDNs) on issues related to new IDN developments. The interview includes overview of extending top-level domains to enable TLDs such as .com, .cn (for China), and .gr (for Greece) available in their native languages and scripts. more
The EU's 'cyber security' Agency ENISA (The European Network and Information Security Agency) has launched a new report concluding that the EU should focus its future IT security research on five areas: cloud computing, real-time detection and diagnosis systems, future wireless networks, sensor networks, and supply chain integrity. more
The month-long series of coordinated attacks against Estonia's Internet in 2007 that shutdown websites of Estonia's government, those of its officials, banks and news agencies are believed to be based by various physiological principles including anonymity and contagion. more
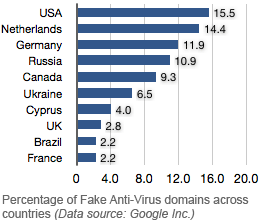 Over at Krebs on Secrity blog, Brian Krebs reports: "Purveyors of fake anti-virus or 'scareware' programs have aggressively stepped up their game to evade detection by legitimate anti-virus programs, according to new data from Google. In a report being released today, Google said that between January 2009 and the end of January 2010, its malware detection infrastructure found some 11,000 malicious or hacked Web pages that attempted to foist fake anti-virus on visitors." more
Over at Krebs on Secrity blog, Brian Krebs reports: "Purveyors of fake anti-virus or 'scareware' programs have aggressively stepped up their game to evade detection by legitimate anti-virus programs, according to new data from Google. In a report being released today, Google said that between January 2009 and the end of January 2010, its malware detection infrastructure found some 11,000 malicious or hacked Web pages that attempted to foist fake anti-virus on visitors." more
ICANN has given Jordan preliminary approval for its IDN (Internationalized Domain Name) ccTLD. "At this time ICANN has received a total of 21 requests for IDN ccTLD(s) through the String Evaluation process, representing 11 languages. A total of 13 requests have successfully passed through the String Evaluation and are hence ready for the requesting country or territory to initiate the application for String Delegation." more
A new report issued by the Number Resource Organization (NRO) has found that demand for both IPv4 and IPv6 address space is continuing to grow. The Internet Number Resource Status Report for the first quarter of 2010 is based on data collected by the five Regional Internet Registries (RIRs) that oversee the allocation of all Internet number resources, and outlines RIR allocation of IP address space (IPv4 and IPv6), as well as AS number assignments. In the report, the NRO notes that allocations of IPv4 addresses in Q1 have reduced the IANA free pool of IPv4 addresses to 8.5 percent. more
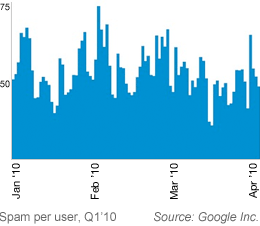 Google, which through its Postini email security and archiving service processes over 3 billion email connections a day, reports that despite recent series of major botnet takedowns, spam levels during the first quarter of 2010 have held fairly steady. "This suggests that there's no shortage of botnets out there for spammers to use. If one botnet goes offline, spammers simply buy, rent, or deploy another, making it difficult for the anti-spam community to make significant inroads in the fight against spam with individual botnet takedowns." more
Google, which through its Postini email security and archiving service processes over 3 billion email connections a day, reports that despite recent series of major botnet takedowns, spam levels during the first quarter of 2010 have held fairly steady. "This suggests that there's no shortage of botnets out there for spammers to use. If one botnet goes offline, spammers simply buy, rent, or deploy another, making it difficult for the anti-spam community to make significant inroads in the fight against spam with individual botnet takedowns." more
At a recent shareholders' meeting in Stockholm, Ericsson's CEO has reaffirmed company's vision of having 50 billion internet-connected devices by 2020: "Today we already see laptops and advanced handsets connected, but in the future everything that will benefit from being connected will be connected." As an example of connected devices, a research engineer showed real life mobile health applications and how heart monitoring can be done remotely over mobile networks. more
Every public tweet since Twitter's inception in March 2006 will be acquired and archived digitally by the U.S Library of Congress, according to announcements made today. The Library has been harvesting data from the web since 2000 and currently holds "more than 167 terabytes of web-based information, including legal blogs, websites of candidates for national office, and websites of Members of Congress". While an official press release has not been issued yet, the Library says "[e]xpect to see an emphasis on the scholarly and research implications of the acquisition". The Library chose to make its first mention of the Acquisition via its official Twitter account @librarycongress. more
Leading Internet content distribution service provider, Akamai, has announced that its global network is now serving as much as 3.45 Terabits per second (Tbps) of content per day. "The traffic peak of 3.45 Tbps is roughly equivalent to the capacity needed to download the entire printed contents of the U.S. Library of Congress in less than a minute," says the company. Paul Sagan, Akamai's President and CEO, says increasing demand for high definition video streaming is a key factor in these recent delivery milestones. more
OECD, Organization for Economic Co-Operation and Development, has released a report for policy makers assessing the level of IPv6 deployment around the world. "[T]he timely deployment of IPv6 by network operators and content/application providers is an increasing priority for all Internet stakeholders. In terms of public policy, IPv6 plays an important role in enabling growth of the Internet to support further innovation. In addition, security, interoperability and competition issues are involved with the depletion of IPv4." more
Loic Damilaville writes to report: Today AFNIC is publishing its new issue paper on the secondary market in domain names. The paper -- written to inform individuals as well as businesses -- gives a detailed account of the concept of "secondary market", the valuation mechanisms used, and the main players involved. The secondary market covers over-the-counter sales of already registered domain names, as well as the market in "second-hand domain names" and the ecosystem made up of the various players involved in these matters. more
The Coalition Against Domain Name Abuse (CADNA) has released a report today suggesting that the Internet Corporation for Assigned Names and Numbers' (ICANN) anticipated launch of 400 generic top-level domains (gTLDs) could cost brand owners worldwide over $746 million. "CADNA's findings are based off a document released by ICANN last month regarding the expected number of gTLDs, or the letters found after the last dot of a domain name like .COM or .ORG, that will be created during the first round of the TLD launch." On the other hand, Earlier this year, Minds + Machines reported on an analysis predicting new gTLDs will only cost $.10 per trademark worldwide. more
Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byCSC

Sponsored byDNIB.com
