


|
||
|
||
Much of the discussion regarding mobile security revolves around the growing “pandemic” of mobile malware. It’s not uncommon to see headlines reporting the discovery of large numbers of new malware samples. However, as Google recently pointed out, with quite a bit of data to support them, there’s little discussion of real world impact of these discoveries. This raises a number of relevant questions. Is the average user likely to be infected? Where does this malware come from? These are questions that deserve analysis and thoughtful responses.
Analyzing Threats with Real World Data
To better understand the nature of the threat to mobile devices, it’s important to start with data that is representative of actual users. At Damballa, we are able to analyze passive DNS (pDNS) data from actual cellular and wired ISPs; we have visibility into 43% of wired and 33% of wireless traffic in North America. This allows us to leverage DNS reputation as well as other network insights to examine the threats encountered by mobile devices. Thus, using passive DNS (pDNS), Damballa is in a unique position to analyze the threats to mobile devices from the network perspective. This is important because network level analysis is device-agnostic and allows us to track the threat to mobile devices in general.
Mobile Insights from pDNS
Our analysis has yielded a number of interesting insights into the existing mobile landscape.
Analyzing both cellular and wired pDNS data, we observed that mobile devices reached out to the same hosting infrastructure as non-mobile devices 98.7% of the time. This is important because it means that existing network information can be used to help analyze the types of resources that mobile devices are contacting. In short, the mobile Internet is really just the Internet.
Additionally, we looked for numerous different types of malicious activity in pDNS data observed in a cellular ISP. For our observation periods, we saw a very small number of requests from mobile devices reaching out to domains known to facilitate mobile malware (MBL). In fact, our results indicated that only a tiny fraction of devices in the network—much smaller than 1%—appeared to be actively infected with mobile malware during our observation period.
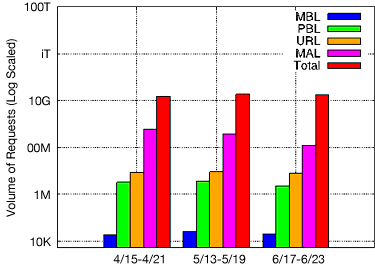 In contrast, there were a large number of requests to domains associated with traditional, desktop threats. These domains were associated with Public Blacklists (PBL), drive-by-downloads (URL), or known malicious desktop applications (MAL). Ongoing research is looking into being performed to evaluate whether there is a mobile threat component associated with these requests.
In contrast, there were a large number of requests to domains associated with traditional, desktop threats. These domains were associated with Public Blacklists (PBL), drive-by-downloads (URL), or known malicious desktop applications (MAL). Ongoing research is looking into being performed to evaluate whether there is a mobile threat component associated with these requests.
Understanding the Results
In light of our observations, it’s necessary to think about what might account for these results and how to make use of these results going forward.
One possible explanation for the small quantity of mobile malware seen is the difficulty of distribution. Google Play provides a strong first party market that offers over a million applications, and the iOS App Store offers over 750,000 applications. These markets provide users with a plethora of applications to choose from in addition to providing malware controls. Thus, in addition to getting applications approved, malware authors face the same discovery challenges as legitimate applications; this reduces the likelihood of a user encountering a malicious application.
Phishing is a threat that targets users of both mobile and traditional computing devices. In fact, security researchers have shown that traditional security indicators from desktop browsers are sometimes hidden or missing from mobile browsers. This means that mobile users may be even more susceptible to phishing attempts on mobile devices. Thus, phishing attempts are a likely explanation for some of the requests from mobile devices to malicious infrastructure associated with traditional, desktop threats. Ongoing research will provide better insights into this particular phenomenon.
Since the mobile Internet is really just the Internet, it is possible to leverage existing network analysis tools and techniques in the mobile space. This is extremely useful because network level analysis is device agnostic; therefore, these techniques should help better detect and mitigate threats going forward.
Despite the fact that the mobile malware problem is not as widespread as the community thinks, due to the inherit nature of the “open” mobile platforms (i.e., Android), we should not take our eyes off the mobile malware problem.
What we do know is that the bad actors are smart and motivated. In the past, they have found new and innovative ways to make their business models flourish. We do not expect them to stop now.
Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byCSC

Sponsored byDNIB.com

Sponsored byRadix
