


|
||
|
||
WoofLocker tech support scams have been wreaking havoc since 2017 but the threat actors behind it don’t seem to be done yet. In fact, the threat may have become even more resilient. Apart from using compromised sites as distribution vectors, WoofLocker started employing a complex traffic direction scheme.
AlienVault OTX has identified 346 domains and 438 IP addresses as WoofLocker indicators of compromise (IoCs) to date. But given the threat’s eight years of existence, how sure are we that no other web properties have fallen through the cracks? We sought to find out.
Our DNS deep dive into WoofLocker revealed:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
With eight years of operation and running in its belt, you would expect WoofLocker to have employed various registrars, a good mix of aged and newly registered domains (NRDs), and a widely spread out infrastructure worldwide. Was that the case, though? We trooped to the DNS to find out.
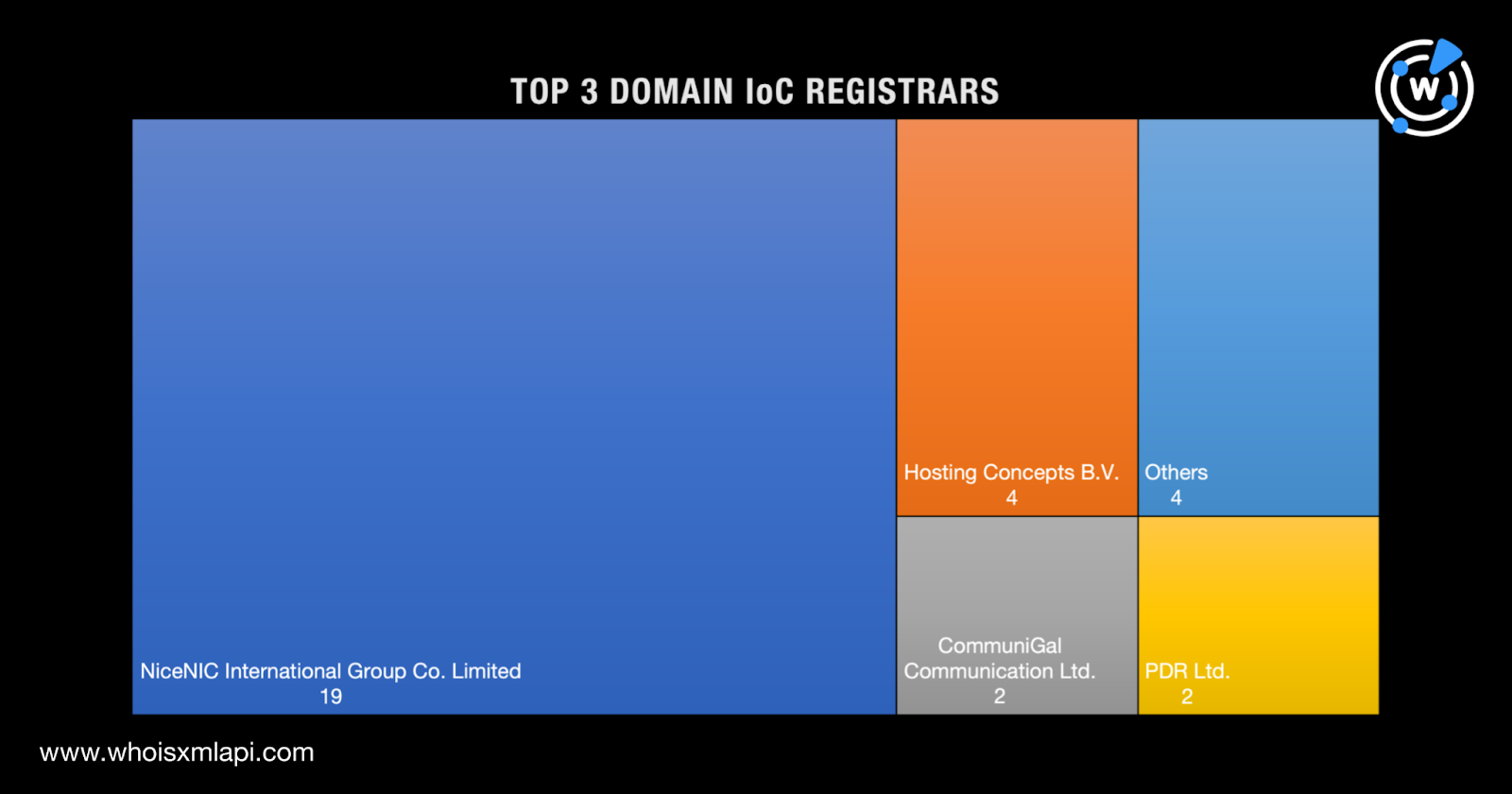
First off, we subjected the domains identified as IoCs to a bulk WHOIS lookup, which led to these discoveries:
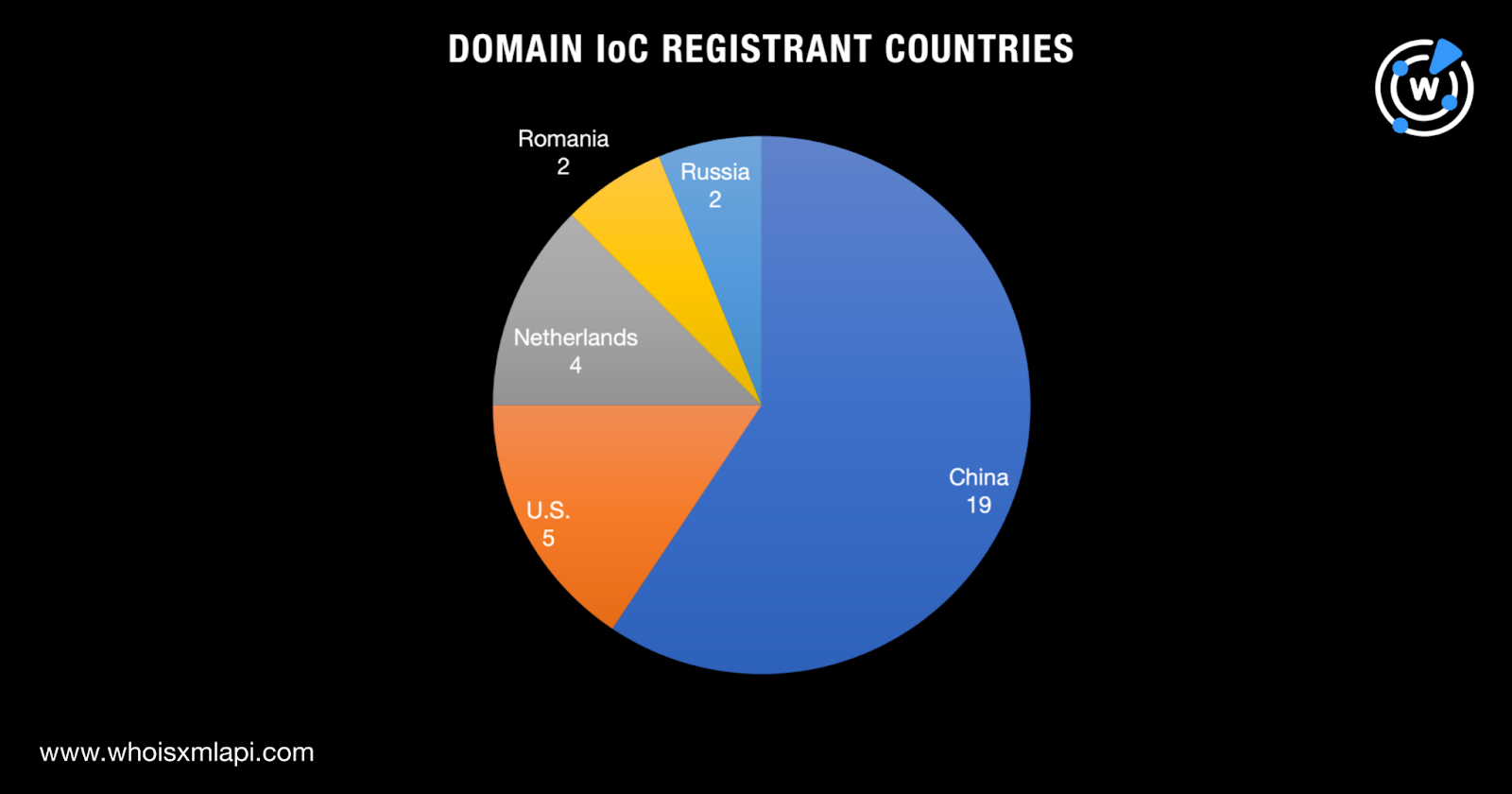
A majority of the IoCs (19 domains) were registered in China. The remaining were spread out across four other countries—five in the U.S., four in the Netherlands, and two each in Romania and Russia.
Next up, we scrutinized the IP addresses classified as IoCs via a bulk IP geolocation lookup, which uncovered:
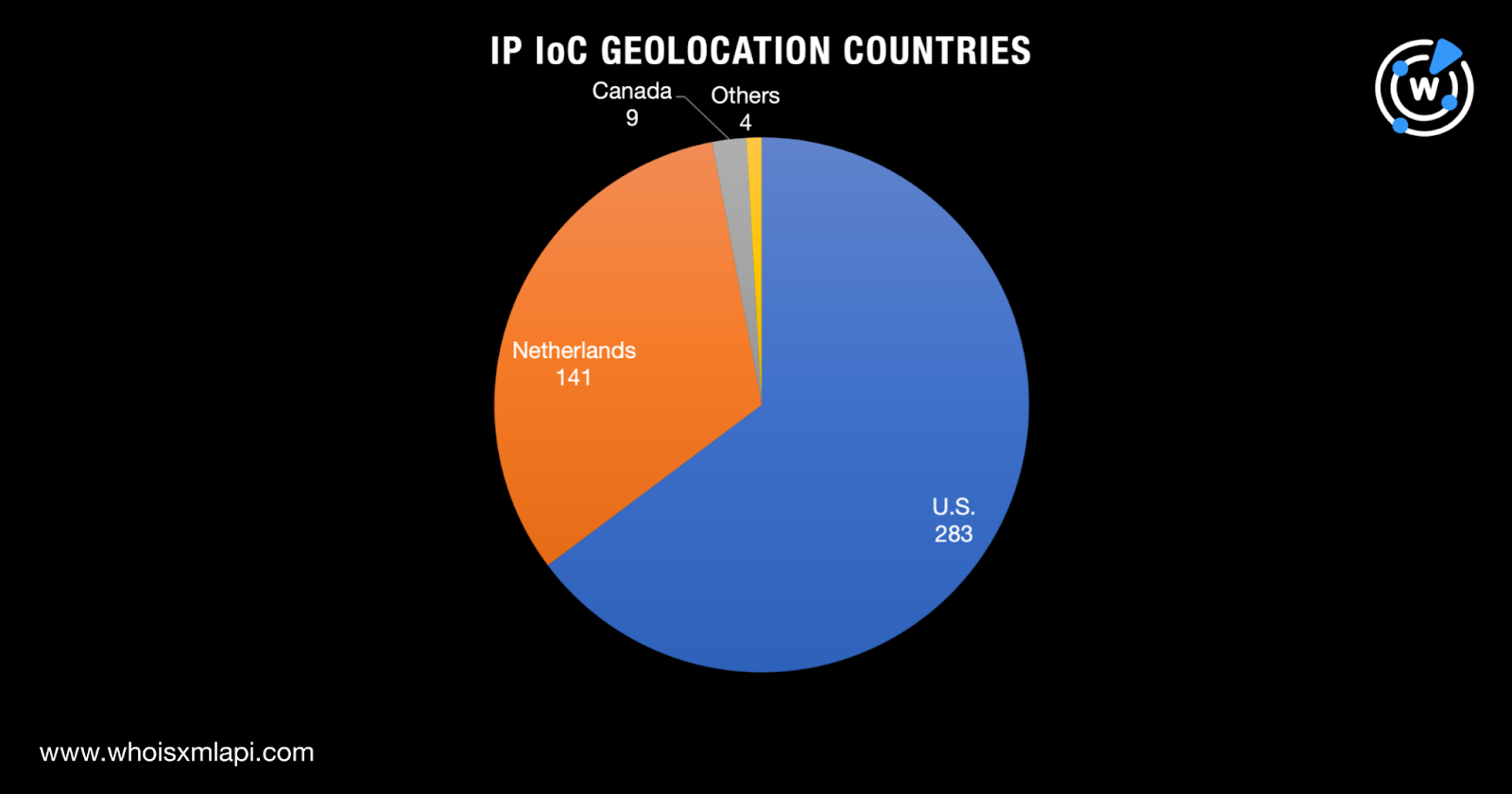
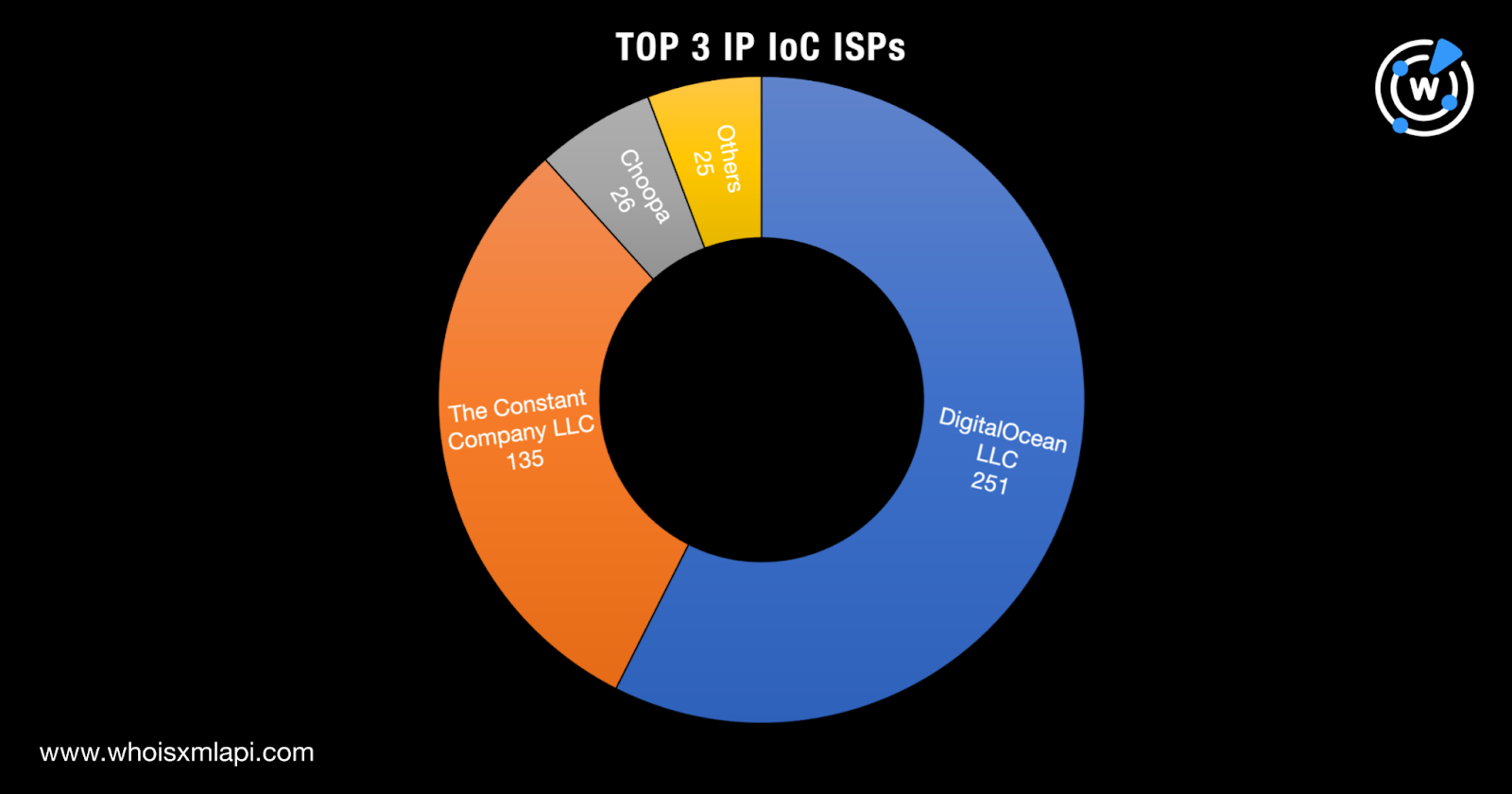
Our domain and IP IoC analyses provided a few answers to the questions we posed earlier. Despite WoofLocker’s long-running tech support ruse, the threat actors employed a limited number of registrars (nine) and ISPs (12). Seemingly, they also showed a preference for NRDs, as only 32 out of 346 domains had current WHOIS records. It’s possible that the domains without current WHOIS records were deliberately left to expire or taken down.
And finally, their infrastructure seemed to span only a few countries distributed across the world’s continents—five current registrant countries and eight IP geolocation countries.
We also posed other questions regarding the inner workings of WoofLocker.
First, we wanted to find out if given the threat’s years-long existence we could uncover unpublicized artifacts. DNS lookups for the domains identified as IoCs led to the discovery of 17 additional IP addresses—12 IPv4 and five IPv6 addresses.
That brought our total number of IP addresses (IoCs and artifacts combined) to 451. To limit false positives, we decided to focus only on those that were dedicated. That left us with 104 IP addresses to further analyze.
Reverse IP lookups for the 104 IP addresses led to the discovery of 1,194 connected domains. A bulk malware check showed that 19 of them were malicious. Two of the dangerous properties continue to host live content to this day, one looks to be a news site while the other appears to be a blog.
One tidbit about WoofLocker also caught our attention—the operators’ penchant for compromising adult sites to serve as scam vehicles. Does that mean the owners of non-adult websites need not worry about becoming unwitting fraud participants?
To find out, we subjected the domains identified as IoCs to a closer examination. We sought to identify recurring text strings that appeared more than once among the IoCs. We named 52 strings led by official, which appeared in 51 domains. Zone closely followed in second place, appearing in 50 IoCs. Fun, seen in 41 domains, rounded out the top 3. Take a look at a visual representation of our text string analysis below.

The domains containing top 3 strings official, error, and help, such as errorhelpline24x7msofficialsoftwareerrorcodex16[.]monster, errorhelpline24x7msofficialsoftwareerrorgh001[.]monster, and errorhelpline24x7msofficialsoftwareerrornew06[.]monster, all seemed to point to supposed Microsoft helpline sites in support of WoofLocker’s chosen tactic—tech support scams. Most of them (123 domains to be exact) also sported the .monster TLD.
Also, possibly in connection to WoofLocker’s preference for adult sites, around 200 domains appeared to point to dating sites. That doesn’t mean the owners of non-adult-related websites would remain safe, though. We also found other strings like cloud, design, logo, recipe, and storage.
Our WoofLocker IoC expansion analysis allowed us to answer questions that piqued our curious minds about the threat. Despite its age, the scammers limited their infrastructure components to a few providers and locations. They also seemingly favored employing NRDs and new gTLDs as campaign vehicles. Last but definitely not least, though they’ve been known to prefer compromising adult-related sites, they could also be trailing their sights on cloud, design, storage services, and cooking websites.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byCSC

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byRadix

Sponsored byIPv4.Global
