


|
||
|
||
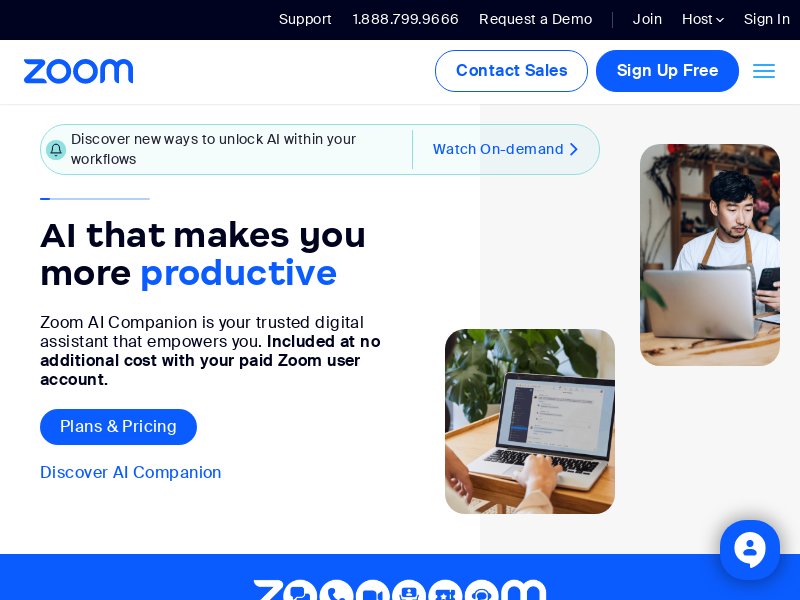
Threat actors have been abusing App Installer, a Windows 10 feature that makes installing applications more convenient. The abuse could lead to ransomware distribution and was likely carried out by financially motivated actors Storm-0569, Storm-1113, Sangria Tempest, and Storm-1674. These malicious actors imitated the landing pages of popular software, such as Zoom, Microsoft OneDrive, Microsoft SharePoint, and Microsoft Teams, to lure target victims into downloading malicious installers.
While Microsoft immediately responded by disabling the ms-appinstaller protocol handler by default, WhoisXML API researchers decided to look for traces of the attack in the DNS.
With that in mind, our research team expanded the IoC lists Microsoft published, comprising 18 subdomains and 14 domains tagged as IoCs (three of which were extracted from the subdomains). The investigation led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download on our website.
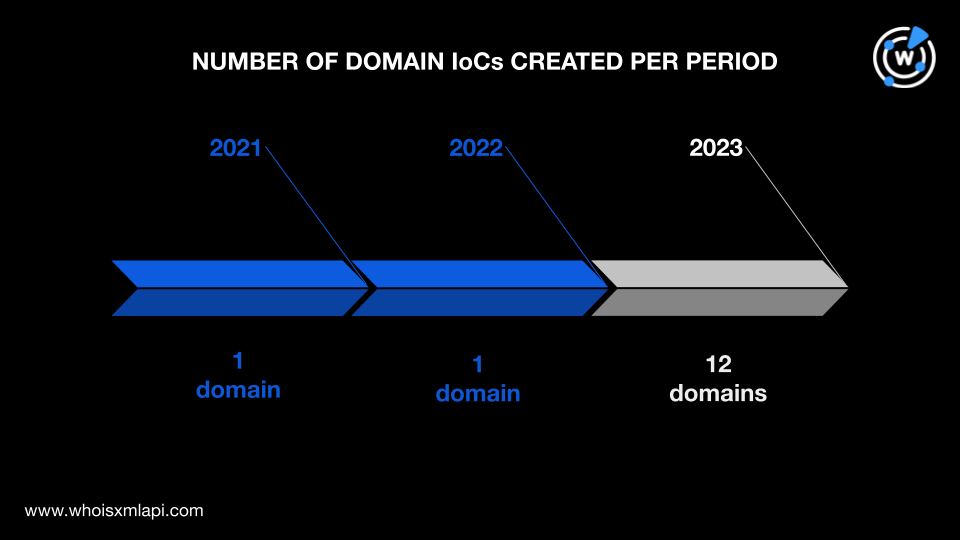
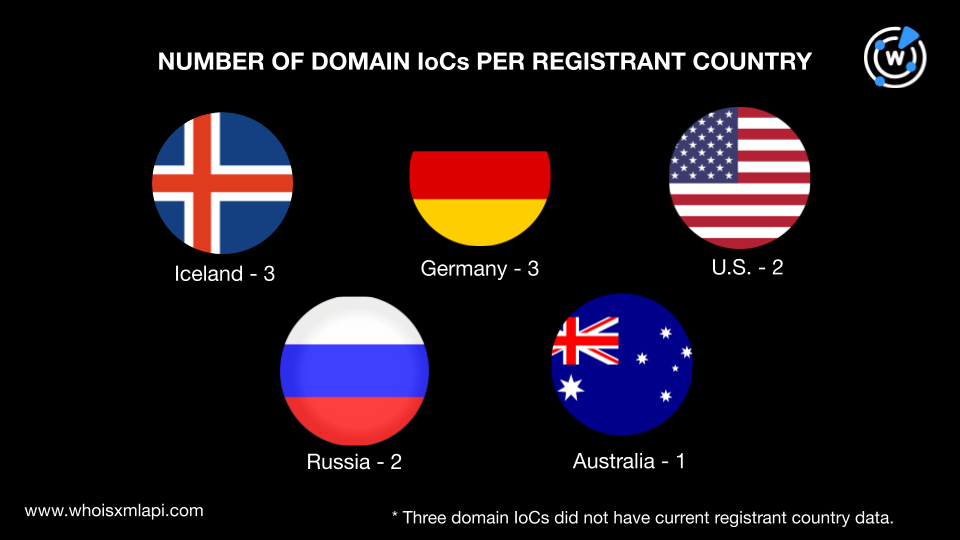
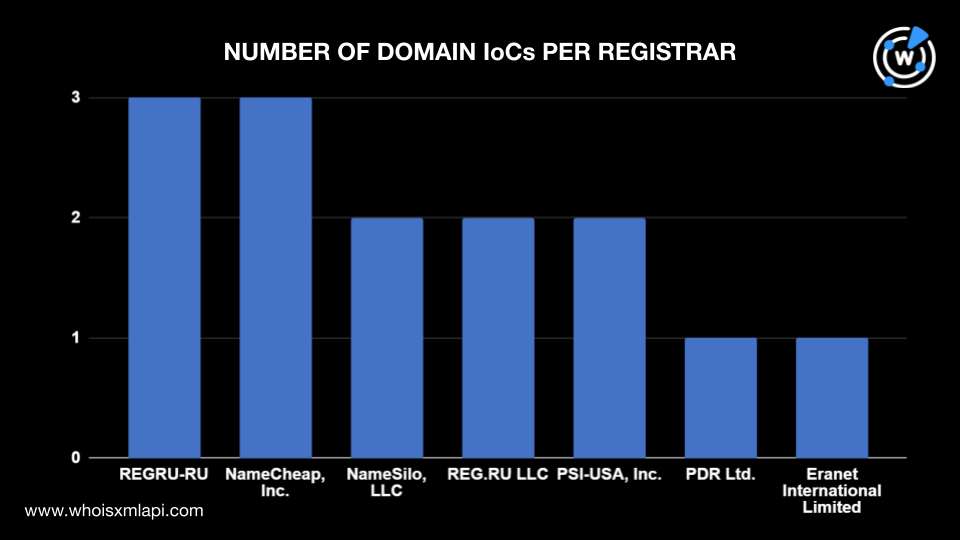
To begin understanding the attack infrastructure, we did a bulk WHOIS lookup for the 14 domains tagged as IoCs, three of which were extracted from the 18 subdomains found on the IoC lists. Their WHOIS records revealed that:
Most of the domains, 12 to be exact, were created in 2023, while one domain was registered in 2022 and another in 2021.
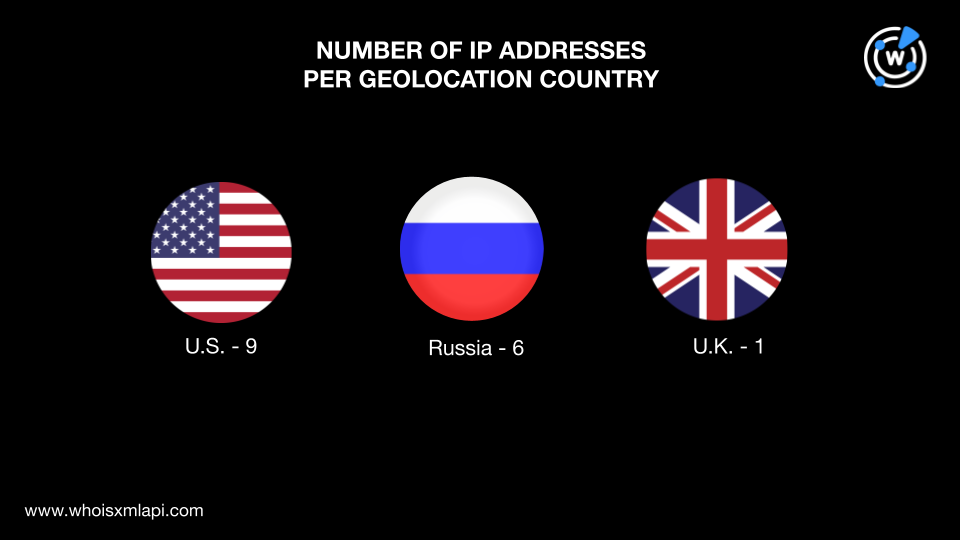
Their registrations were spread across five countries. Three domains each were registered in Iceland and Germany, two each in the U.S. and Russia, and one in Australia. Three domains did not have current registrant country data.
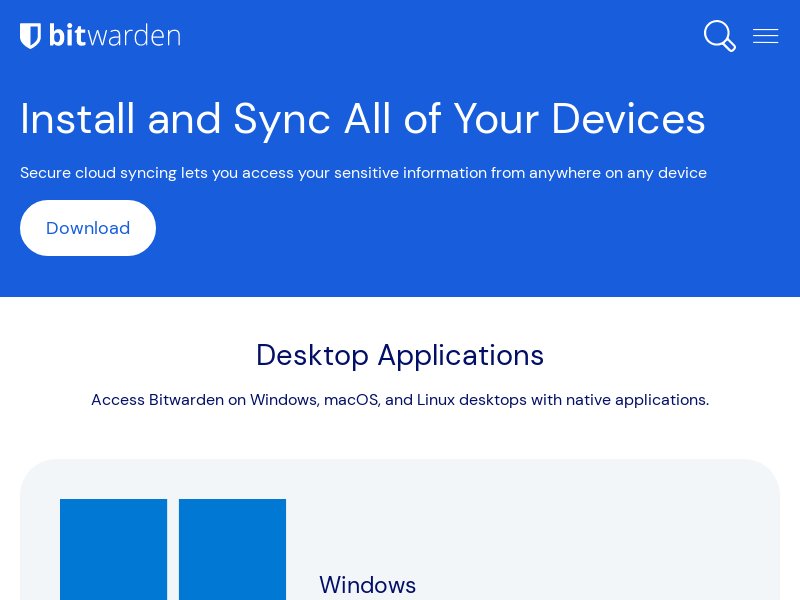
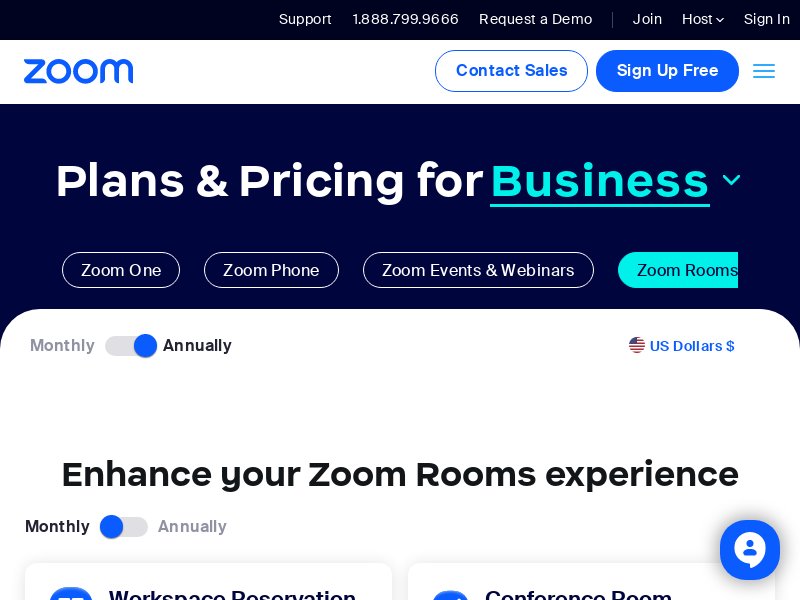
We then subjected the domain IoCs to a screenshot analysis. We found that some continued to host live content, including the websites below that show the Zoom and Microsoft landing pages.
As our next step, we traced the DNS footprints of the malicious domains and subdomains used in the campaigns.
WHOIS History API searches for the domain IoCs led to the discovery of 12 email addresses in their historical WHOIS records, five of which were public. Running these public email addresses on Reverse WHOIS API allowed us to determine that they appeared in the current WHOIS records of 8,434 domains. However, one email address was likely owned by a domainer since it was used to register 8,429 domains. After removing the domains the domainer possibly owns and the IoCs, we were left with four email-connected domains.
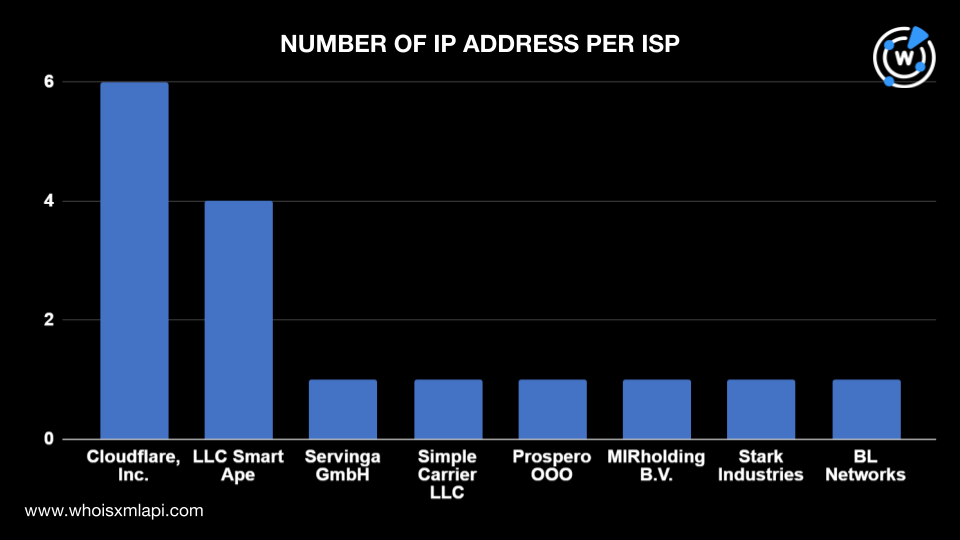
We then performed DNS lookups for the IoCs and obtained 16 IP addresses to which the 14 domains and 18 subdomains tagged as IoCs resolved. Subjecting these IP addresses to IP geolocation lookups, we found that:
They were managed by eight ISPs—Cloudflare, Inc. administered six IP addresses; LLC Smart Ape, four; and Serving GmbH, Simple Carrier LLC, Prospero OOO, MIRholding B.V., Stark Industries, and BL Networks, one each.
Threat Intelligence API also revealed that nine of the 16 IP addresses were associated with various threats. A few examples are shown in the table below.
| IP ADDRESSES | ASSOCIATED THREAT TYPES |
|---|---|
| 185[.]196[.]8[.]246 | Attack Command-and-control (C2) Malware |
| 91[.]215[.]85[.]199 | Attack Malware Spam |
| 172[.]67[.]147[.]29 | Generic Phishing |
| 172[.]67[.]209[.]46 | Generic Malware Phishing |
We also subjected the 16 IP addresses to reverse IP lookups, which showed that nine were potentially dedicated. They led to 127 IP-connected domains after removing duplicates, the IoCs, and the email-connected domains.
We also performed a screenshot analysis for the IP-connected domains, which revealed that many hosted installation pages like the malicious resources involved in the App Installer abuse as of this writing.
Finally, we looked for string-connected domains using Domains & Subdomains Discovery. We used the following search parameters and text strings leading to the discovery of 401 domains.
Meanwhile, subdomain searches using the text strings that appeared among the subdomain IoCs unveiled 596 string-connected subdomains for these parameters:
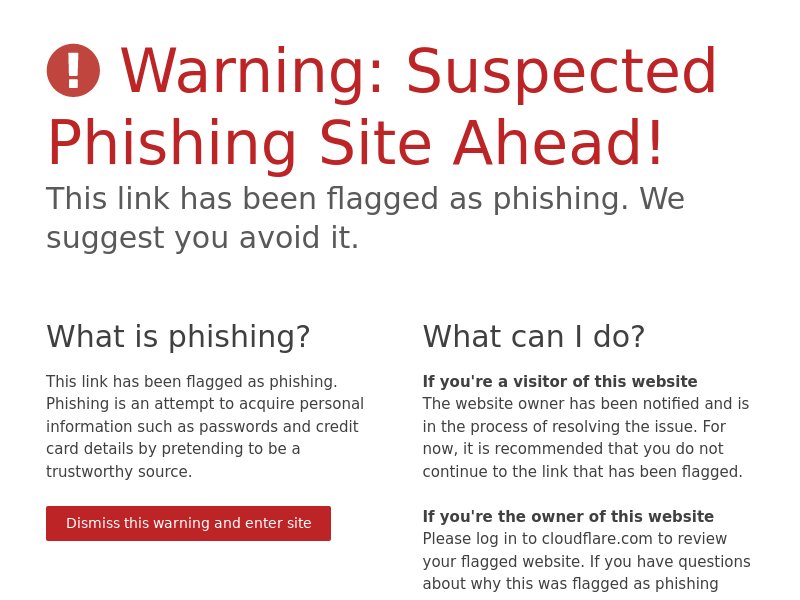
A screenshot analysis for the string-connected resources showed that several hosted suspicious content, including a page that was flagged for phishing as of this writing.
We started the investigation with 18 subdomains and 14 domains (three of which were extracted from the subdomains) tagged as IoCs for the App Installer abuse that could potentially lead to ransomware installation. It led us to discover more than 1,100 connected artifacts comprising four email-connected domains, 16 IP addresses, 127 IP-connected domains, 401 string-connected domains, and 596 string-connected subdomains.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byCSC

Sponsored byWhoisXML API

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byRadix
