


|
||
|
||
The WIRTE advanced persistent threat (APT) group has been active since at least August 2018. It has targeted government, diplomatic, financial, military, legal, and technology organizations in the Middle East and Europe.
While the group has been quiet for some time, it has resurfaced, trailing its sights on Middle Eastern entities, specifically the Palestinian Authority, Jordan, Egypt, and Saudi Arabia. According to reports, the group has been using custom loaders like IronWind in recent attacks.
Check Point Research published an in-depth analysis of WIRTE’s attacks from late 2023 to the present and identified 56 indicators of compromise (IoCs) comprising 30 domains, 23 IP addresses, and three subdomains.
The WhoisXML API research team expanded the original list of 56 IoCs to uncover more connected artifacts and found:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
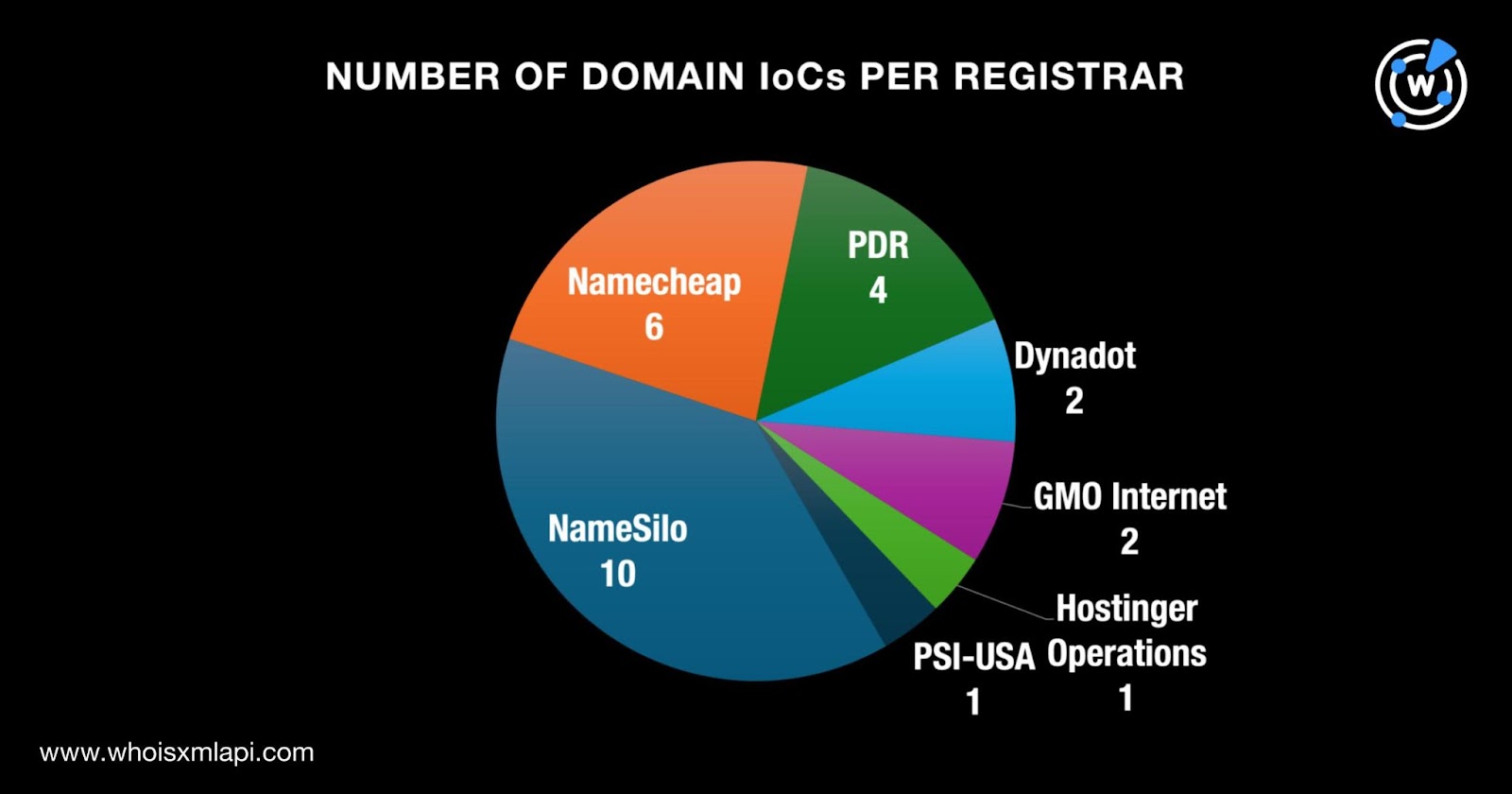
We first took a closer look at the 56 WIRTE attack IoCs beginning with the 30 domains. We queried the domain IoCs on Bulk WHOIS Lookup and found that only 26 of them had current WHOIS records. The results revealed that:
They were created between 2022 and 2024. Specifically, one domain in 2022, six in 2023, and 19 in 2024.

They were scattered across four registrant countries led by the U.S., which accounted for 15 domains. Iceland came in second place with five domains, while one domain each was registered in Canada and Switzerland. Four domains did not have current registrant country data.

Next, we queried the 30 domain IoCs on DNS Chronicle API and found that they recorded a total of 1,692 IP resolutions between 4 October 2019 and 29 November 2024. Take a look at the DNS history of five domain IoCs below.
| DOMAIN | START DATE | LAST DATE | NUMBER OF IP RESOLUTIONS |
|---|---|---|---|
| ainiaiwo2025[.]com | 4 October 2019 | 9 November 2024 | 40 |
| gagatour2025[.]com | 6 November 2022 | 30 August 2024 | 54 |
| vegaskickoffclassic2025[.]com | 13 December 2023 | 21 December 2024 | 42 |
| www222025[.]com | 29 December 2023 | 1 January 2025 | 11 |
| theelection2025[.]com | 3 March 2024 | 9 November 2024 | 16 |
After that, we looked more closely at the 23 IP addresses tagged as IoCs by querying them first on Bulk IP Geolocation Lookup, which revealed that:

They were distributed among nine ISPs led by M247, which accounted for five IP addresses. FlokiNET and Latitude.sh administered three IP addresses each; Servinga, two; and AlexHost, BlueVPS, Host Africa, Nano IT, and NET23VNet, one each. Five IP addresses had no ISP data.

Like the domains tagged as IoCs, we also queried the 23 IP address IoCs on DNS Chronicle API. We found that they historically resolved 981 domains between 4 October 2019 and 29 November 2024. Take a look at the DNS history of five examples below.
| IP ADDRESS IoC | START DATE | LAST DATE | NUMBER OF DOMAIN RESOLUTIONS |
|---|---|---|---|
| 185[.]158[.]248[.]161 | 06/07/22 | 06/19/24 | 26 |
| 213[.]252[.]244[.]234 | 11/19/21 | 11/02/24 | 131 |
| 37[.]120[.]247[.]22 | 03/24/23 | 09/14/23 | 4 |
| 45[.]59[.]118[.]145 | 09/05/21 | 11/11/24 | 102 |
| 5[.]42[.]221[.]151 | 05/06/23 | 11/18/23 | 6 |
Our search for WIRTE-connected artifacts took off with a WHOIS History API query for the 30 domains tagged as IoCs, which uncovered 88 email addresses from their historical WHOIS records after duplicates were filtered out. A total of 31 of them turned out to be public email addresses.
A Reverse WHOIS API query for the 31 public email addresses returned 360 email-connected domains after duplicates and the IoCs were filtered out.
Next, we queried the 30 domains tagged as IoCs on DNS Lookup API and found that they resolved to 36 IP addresses after duplicates and the IP address IoCs were filtered out.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byWhoisXML API

Sponsored byCSC

Sponsored byVerisign

Sponsored byRadix
