


|
||
|
||
Threat researcher Dancho Danchev recently uncovered 130 domains that seemingly belong to fake cryptocurrency sellers. The WhoisXML API research team sought to find potential connections to the threat by expanding the current list of indicators of compromise (IoCs) using our vast array of DNS intelligence sources.
Our in-depth investigation led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
To learn more about the 130 domain names tagged as IoCs, we performed a bulk WHOIS lookup, which revealed that:
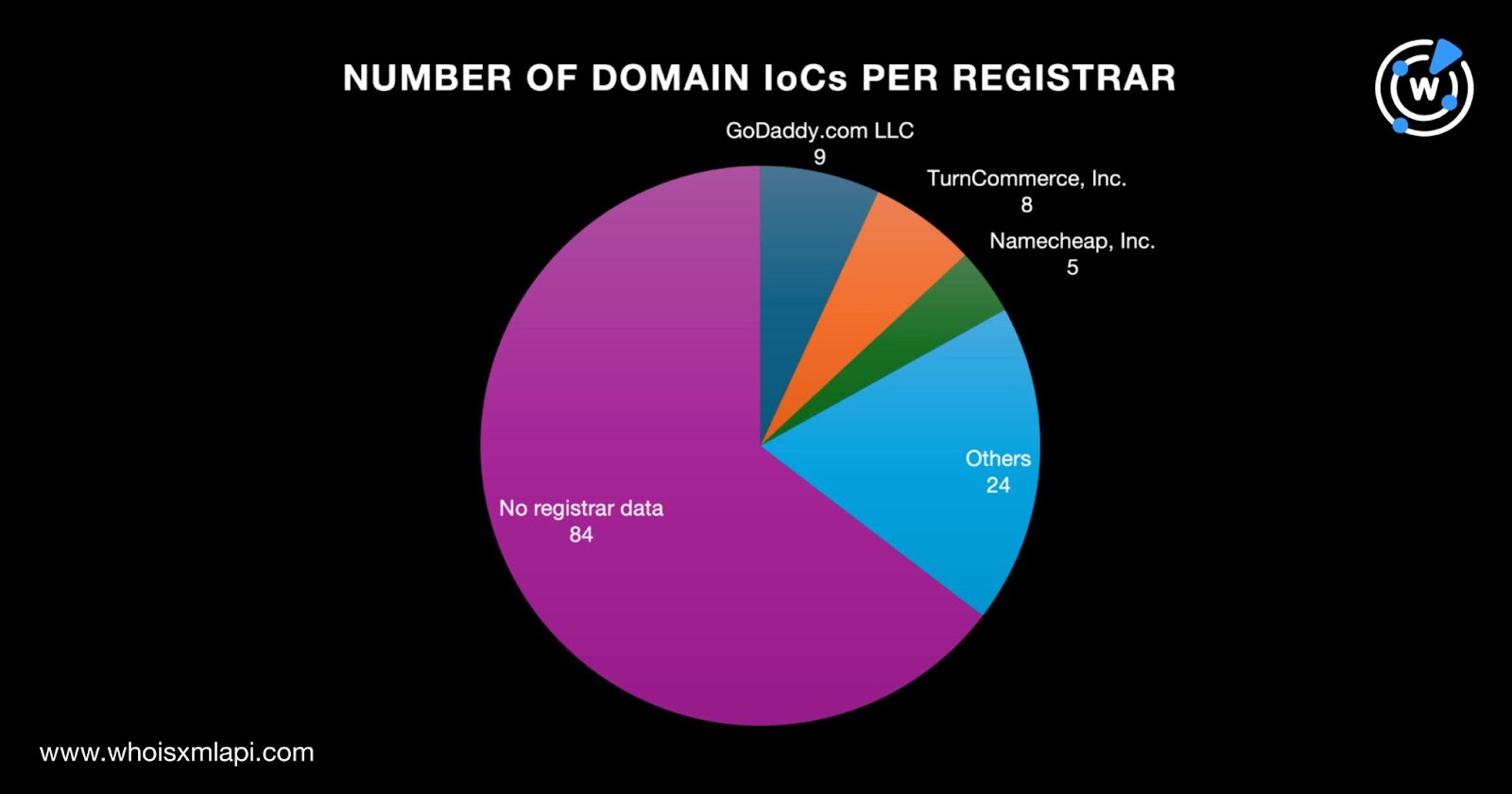
The actors behind the malicious fake cryptocurrency-selling campaigns used both old and new domain names. The oldest domain IoC was created in 2014, while the newest two domains were created in 2024. Eighteen domains were created in 2023; seven in 2021; six each in 2019, 2020, and 2022; two in 2024; and one each in 2014 and 2016. Finally, 83 domain IoCs did not have creation dates in their current WHOIS records.
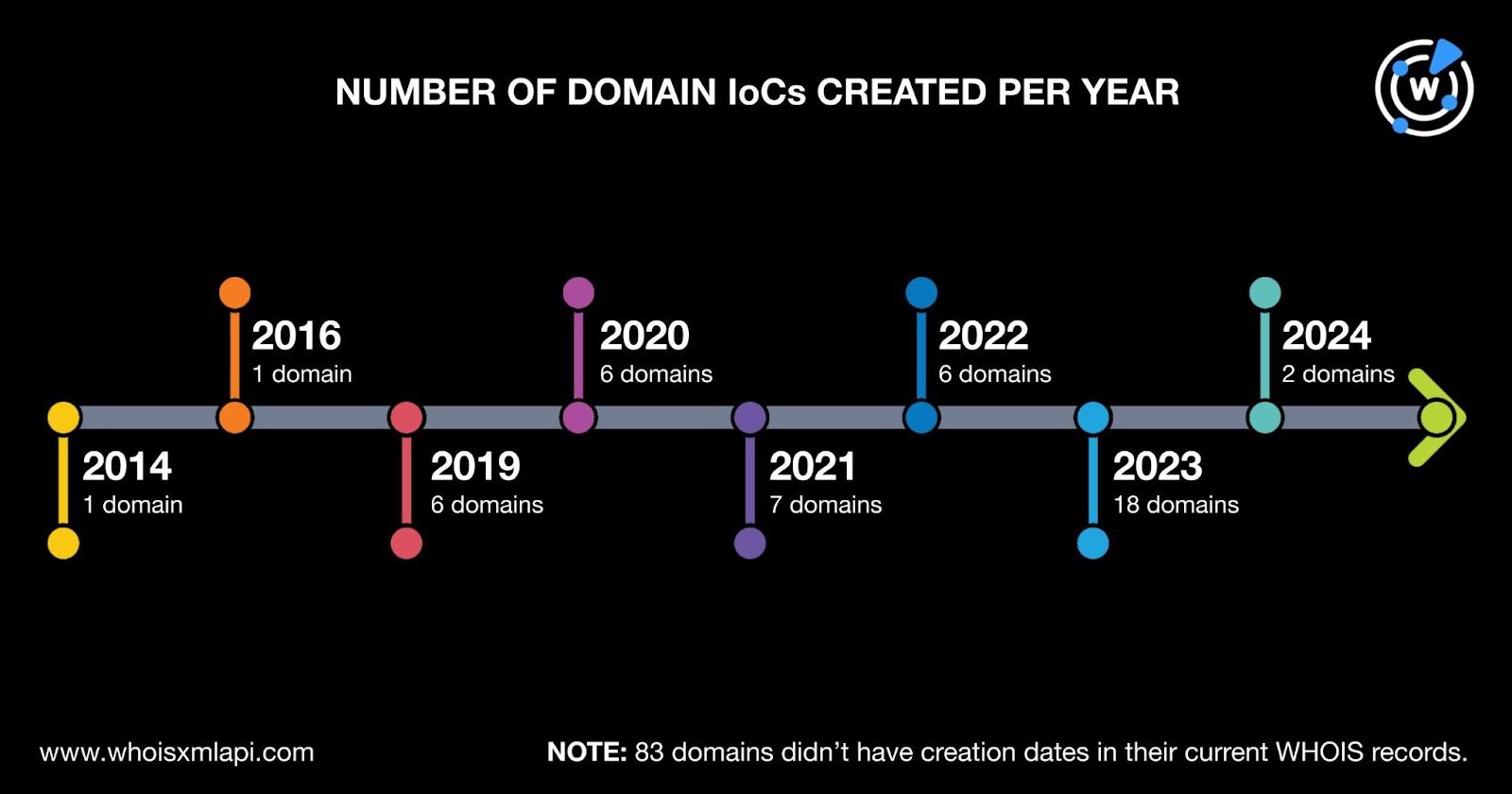
The domain IoCs were spread across 11 countries topped by the U.S., which accounted for 28 domains. Four domains were registered in Iceland. Austria, China, and the U.K. accounted for two domain IoCs each. One domain each was registered in Cyprus, Denmark, Germany, Kazakhstan, Switzerland, and Turkey. Finally, 86 domain IoCs did not have registrant countries in their current WHOIS records.
To uncover other artifacts potentially connected to the fake cryptocurrency-selling campaigns, we first performed WHOIS History API queries for the 130 domains tagged as IoCs. Their historical WHOIS records contained 336 email addresses after duplicates were removed, 57 of which were public.
We then used the 57 public email addresses as reverse WHOIS API search terms and found 522 email-connected domains after duplicates and the IoCs were filtered out. Twenty-one of the email-connected domains were associated with 1—2 threats according to Threat Intelligence API. Take a look at five examples below.
| MALICIOUS EMAIL-CONNECTED DOMAIN | ASSOCIATED THREATS |
|---|---|
| brainiac[.]net | PhishingGeneric |
| couponmafia[.]com | Phishing Generic |
| escrow-peer[.]com | Attack Phishing |
| escrow-trades[.]com | Attack Phishing |
| escrow-verify[.]com | Attack Phishing |
Next, DNS lookups for the 130 domains tagged as IoCs revealed that 91 of them did not actively resolve to any IP address. The remaining 39 domain IoCs, meanwhile, resolved to 41 IP addresses after duplicates were removed. Threat Intelligence Lookup showed that 39 of them were associated with various threats. Take a look at five examples below.
| MALICIOUS IP ADDRESS | ASSOCIATED THREATS |
|---|---|
| 104[.]247[.]81[.]54 | Malware |
| 104[.]247[.]81[.]51 | AttackMalware |
| 104[.]21[.]63[.]32 | Generic PhishingAttack |
| 81[.]19[.]154[.]98 | Malware Generic Phishing Attack |
| 103[.]224[.]182[.]253 | Spam Phishing Generic Malware Command and control (C&C) Attack Suspicious |
A bulk IP geolocation lookup for the 41 IP addresses showed that:
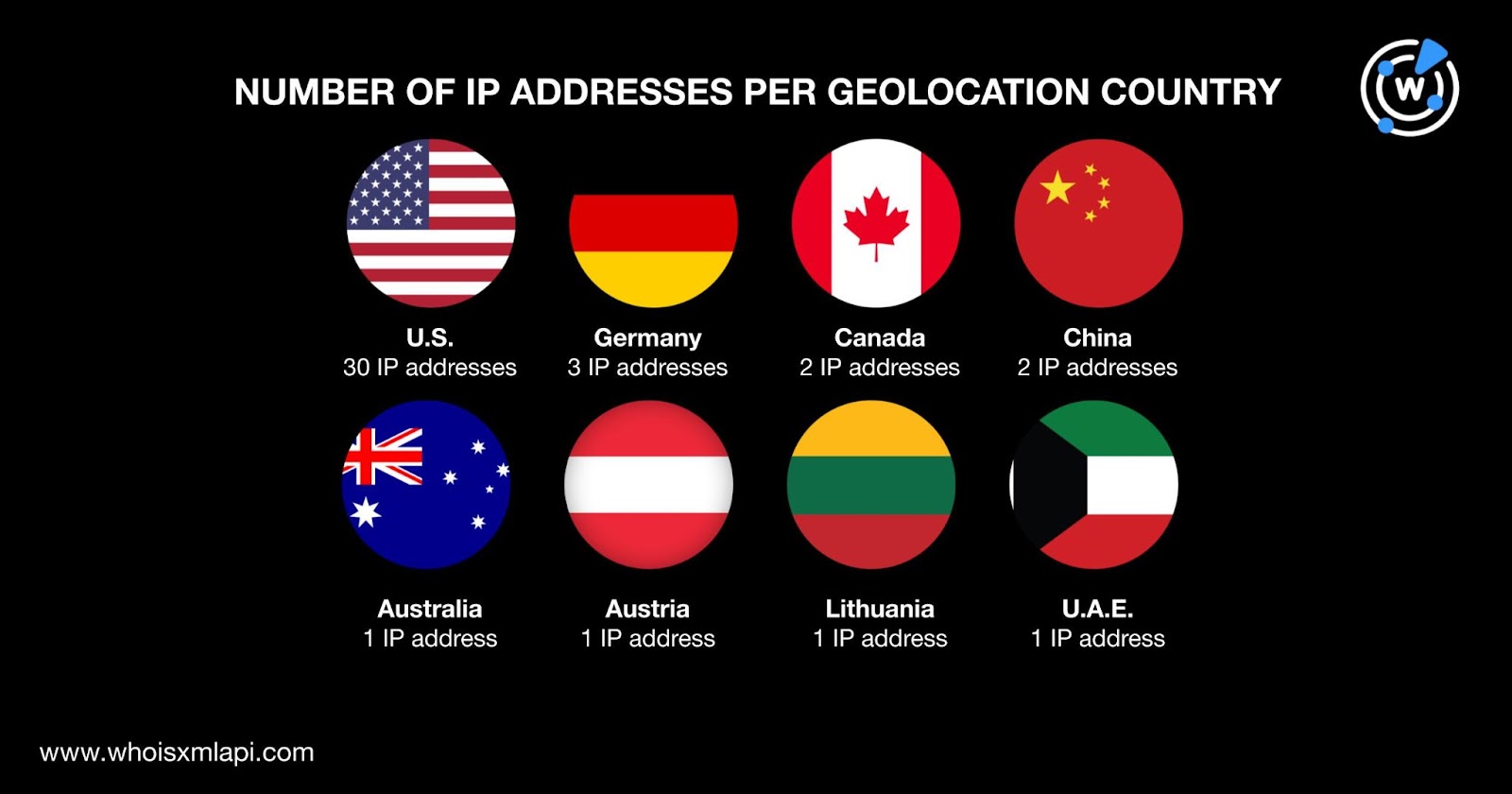
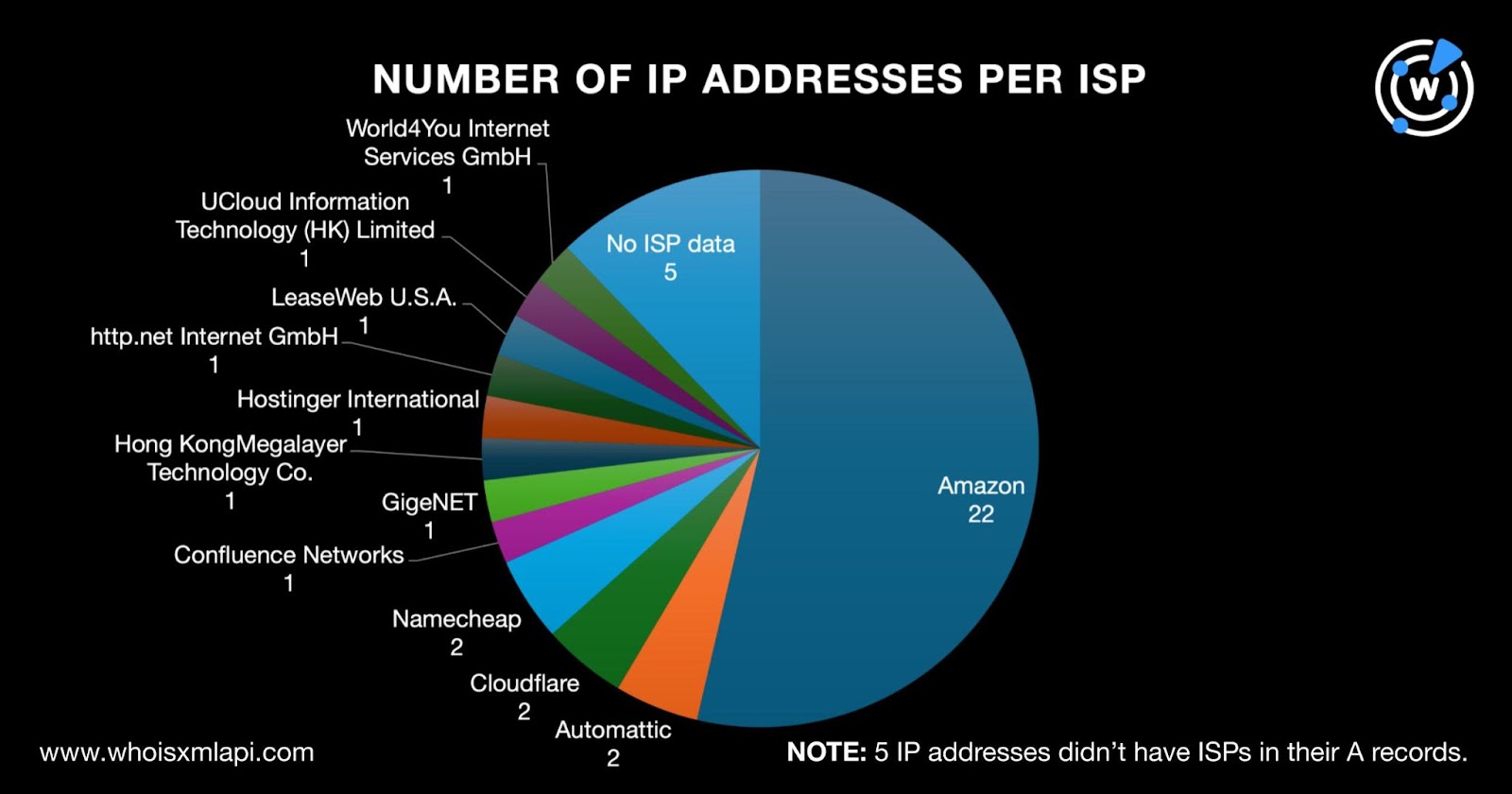
They were also spread across 12 ISPs topped by Amazon, which accounted for 22 IP address IoCs. Automattic, Cloudflare, and Namecheap tied in second place with two IP IoCs each. One IP address IoC each was administered by Confluence Networks, GigeNET, Hong KongMegalayer Technology Co., Hostinger International, http.net Internet GmbH, LeaseWeb U.S.A., UCloud Information Technology (HK) Limited, and World4You Internet Services GmbH. Finally, five IP addresses did not have ISPs in their A records.
We also subjected the 41 IP addresses to reverse IP lookups and found that only two of them could be dedicated. Altogether, they hosted 259 domains after duplicates, the IoCs, and the email-connected domains were filtered out.
To cover all bases, we looked for domains that started with the same text strings as the IoCs. They only used different topTLD extensions. Eighty-four text strings also appeared in 1,947 string-connected domains. They were:
Threat Intelligence API found that 15 of them were associated with various threats. Take a look at five examples below.
| MALICIOUS STRING-CONNECTED DOMAIN | ASSOCIATED THREATS |
|---|---|
| coinswallet[.]info | Generic Attack |
| paxful-trade[.]info | Attack Phishing |
| paxful-trade[.]link | Attack Phishing |
| paxful-trade[.]pro | Attack Phishing |
| yobit[.]press | Malware |
Our DNS deep dive into the fake cryptocurrency-selling campaigns led to the discovery of 2,769 potentially connected artifacts. Many of them, 75 to be exact, seem to have already been weaponized. As cryptocurrency usage becomes more popular, we are bound to see more threats targeting them, making staying ahead of the curve critical.
Download a sample of the threat research materials now or contact sales to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byRadix

Sponsored byCSC

Sponsored byDNIB.com

Sponsored byVerisign
