


|
||
|
||
Silent Push has been monitoring the FUNULL content delivery network (CDN) for two years now. They believe the network has played host to various cybercriminal campaigns, including investment scams, fake trading app distribution, suspect gambling networks, and the Polyfill supply chain attack.
The researchers discovered that FUNULL currently hosts a malicious domain cluster made up of more than 200,000 hostnames, 95% of which appear to have been created using a domain generation algorithm (DGA), that they have dubbed “Triad Nexus.”
Their study identified 21 subdomains and 42 domains as suspicious indicators, which the WhoisXML API research team expanded. Our analysis led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our analysis of Triad Nexus with a bulk WHOIS lookup for the 42 domains identified as suspicious indicators. We found out that:
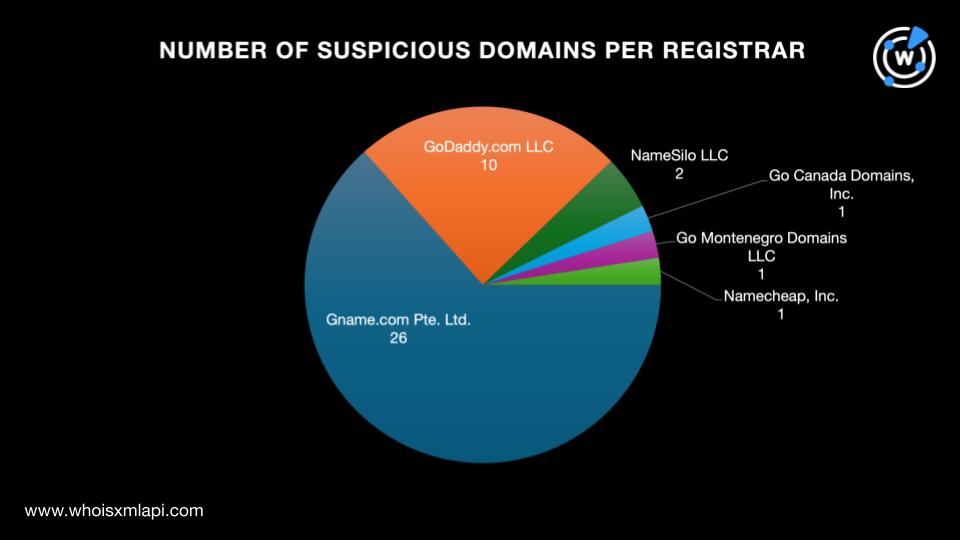
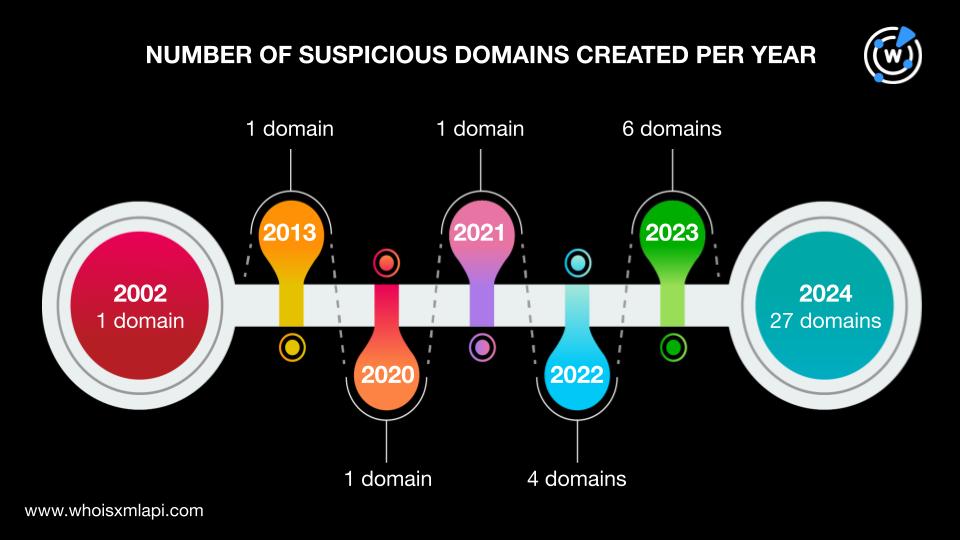
They were registered between 2002 and 2024, implying that the threat actors did not discriminate in terms of domain age. Note, though, that more than half of the suspicious domains, 27 to be exact, were newly registered.
They were spread across five registrant countries led by Malaysia, which accounted for 20 domains. The U.S. came in second place with 14 domains. Croatia bagged third place with five domains. China and Iceland completed the list with one domain each.

As the first step in our suspicious indicators expansion, we queried the 41 suspicious domains on WHOIS History API. They led to the discovery of seven email addresses, four of which were public.
Using the four public email addresses as search strings for Reverse WHOIS API allowed us to obtain 113 email-connected domains after filtering out duplicates and the suspicious domains.
Next, we performed DNS lookups for the 41 suspicious domains and found that 34 of them actively resolved to 33 IP addresses to date after removing duplicates.
Threat Intelligence API queries for the 33 IP addresses showed that four were associated with various threats. The IP address 76[.]223[.]67[.]189, for instance, has been involved in command and control (C&C), generic threats, malware distribution, phishing, spam campaigns, and suspicious activities.
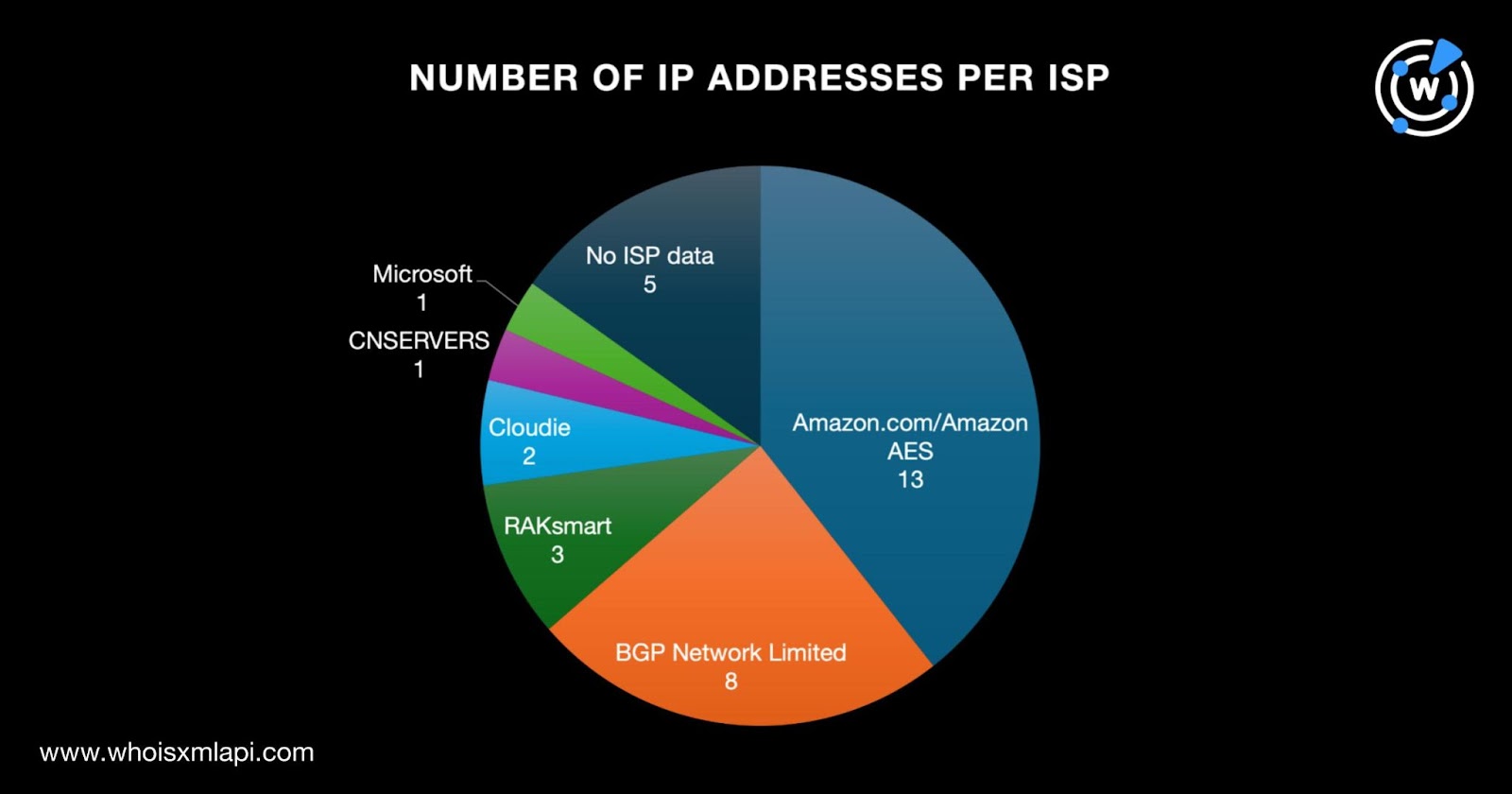
A bulk IP geolocation lookup for the 33 IP addresses revealed that:
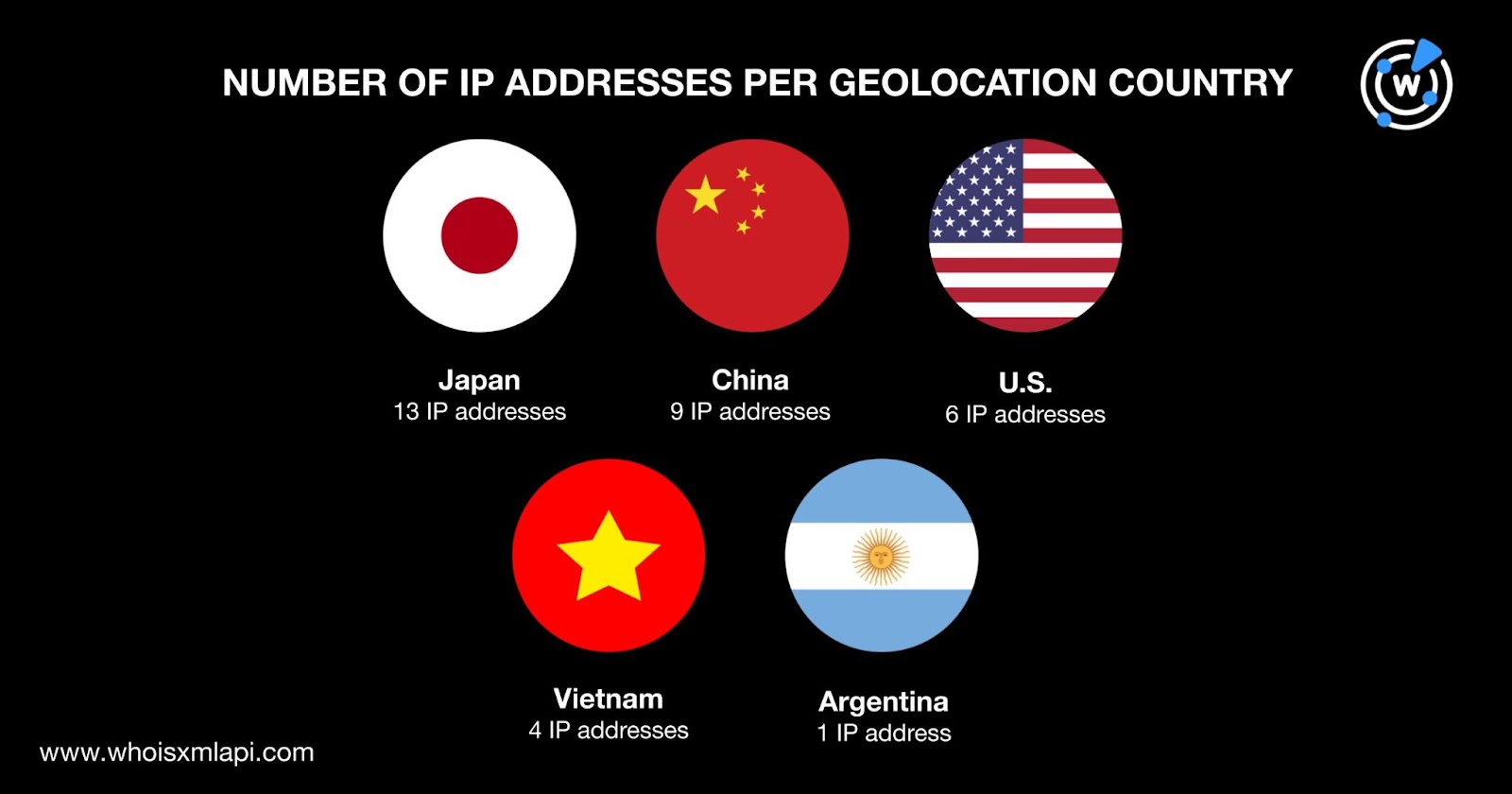
They were distributed among six different ISPs topped by Amazon.com/Amazon AES, which accounted for 13 IP addresses. BGP Network Limited followed with eight IP addresses. RAKsmart accounted for three IP addresses while Cloudie accounted for two. CNSERVERS and Microsoft accounted for one IP address each. Finally, five IP addresses did not have ISP information.
Additionally, we determined the historical IP resolutions of the 41 suspicious domains using DNS Chronicle Lookup. Thirty-six had historical A record data. In particular:
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byRadix

Sponsored byWhoisXML API

Sponsored byIPv4.Global

Sponsored byCSC

Sponsored byDNIB.com

Sponsored byVerisign
