According to a recent survey conducted by the European Network and Information Security Agency (ENISA), 78% of service providers in Europe have plans to deploy DNSSEC within the next 3 years.
On the other hand, the study also found 22% have no plans to deploy DNSSEC in the next 3 years. The main reasons, according to those surveyed, are:
- Lack of customer demand for the service
- Cost of deployment and the on-going costs for running the service
- Immaturity of the technology
- Lack of requirement set to operators by National regulators
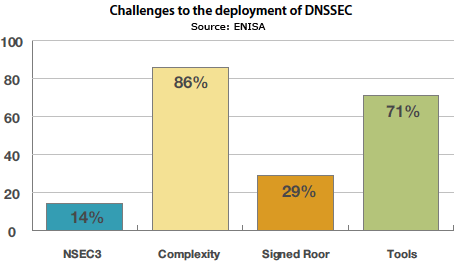
Additionally, service providers who are planning to deploy DNSSEC have expressed the following challenges as key barriers:
- Problems with the complexity of Key Management and Key Rollovers.
- Lack of supporting tools for Key Management as well as operational management of DNSSEC servers.
- Problems with increased system complexity of DNSSEC servers. In this respect, it has also been noted that in some cases equipment vendors deliver unstable products for DNSSEC support.
- Essential lack of key management policies as well as in a wider scope lack of information security policies with focus on DNSSEC and security management guidelines.
- Lack of end user awareness on the benefits provided by DNSSEC and the security it provides.
- There are no widely used applications that are supporting DNSSEC.
- The root of the DNS is not signed. This breaks the hierarchy of DNS and Trust Entry points (Trust anchors) have to be configured to the recursive resolvers.
- The distribution and update of the trust anchors is not standardised and there are no common policies and procedures yet in place.
- There is lack of standardisation in the transfer of the key material from the child domains to their parents.
- There is lack of tools notifying the user when the domain they are using is securely validated.
- The inherent feature of DNSSEC for authenticated denial of existence allows an abuser to enumerate the contents of a zone. The adoption of a variation of the protocol, named NSEC3, by the product vendors is required.
The full report can be downloaded here (PDF). Background information available here.
NORDVPN DISCOUNT - CircleID
x NordVPN
Get NordVPN
[74% +3 extra months, from $2.99/month]








