


|
||
|
||
It’s not unusual for data stealers to target several browsers simultaneously. Zooming in on multiple platforms at once, including email clients, gaming portals, chat apps, crypto wallets, and even VPN-protected services, however, is quite novel. But that’s what WhiteSnake does—steal sensitive information from victims for a meager US$120 a month to US$1,500 for a lifetime license.
Researcher RussianPanda conducted an in-depth WhiteSnake analysis and identified 28 IP addresses as IoCs. WhoisXML API expanded the said list to identify other possible threat vectors via a DNS deep dive, which uncovered:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
WhiteSnake first reared its head on hacking forums in February 2022. It has gained popularity since then, primarily due to its capability to steal data across platforms and relatively low price tag. Its creators also boast of its capability to stay under the radar, given that all communications with the creators, sellers, and victims’ networks for command and control happen on Tor.
Threat Intelligence Platform (TIP) revealed that:
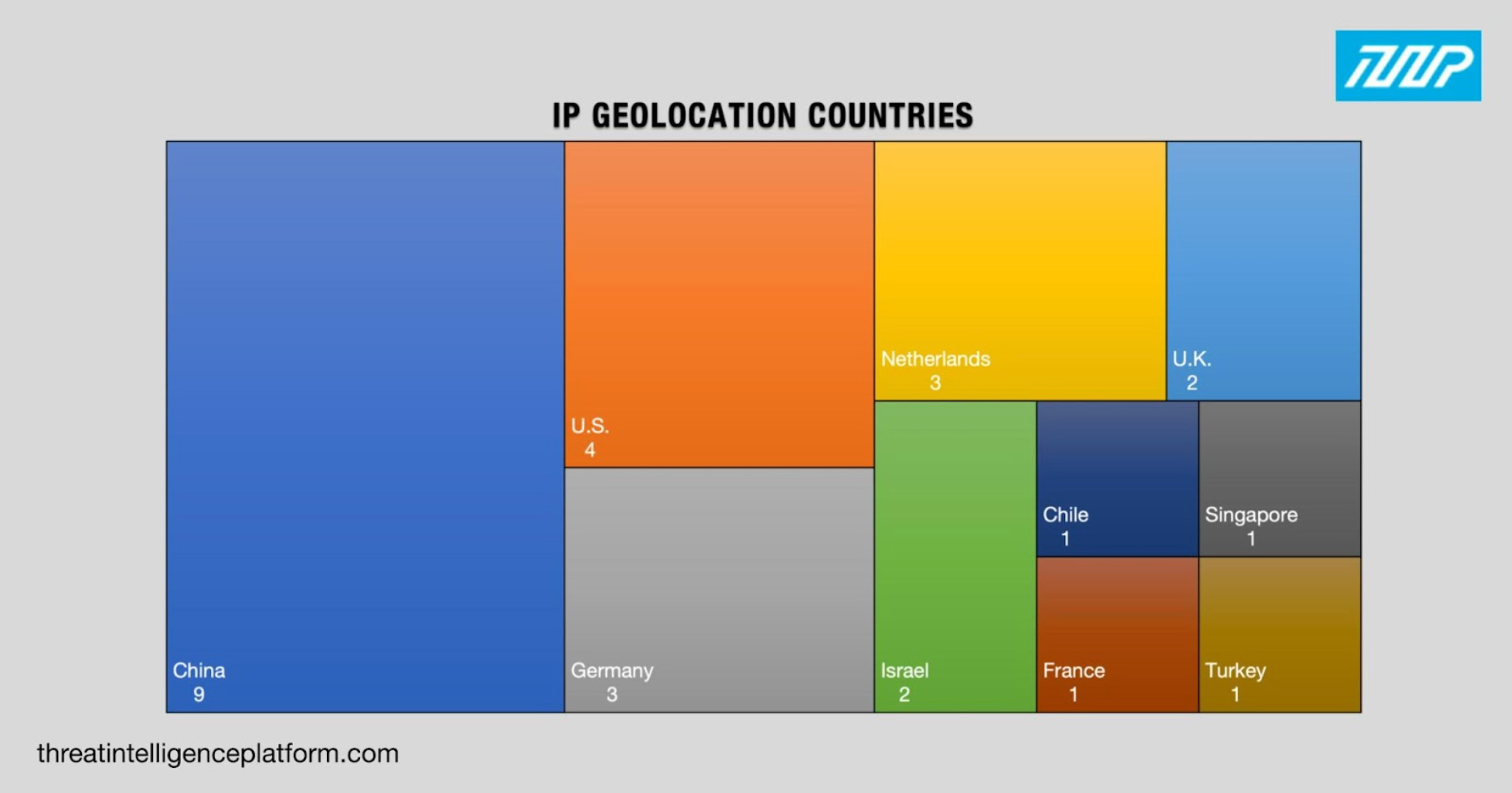
To identify other WhiteSnake stealer artifacts, we performed an IoC list expansion starting with reverse IP lookups for the five dedicated IP addresses that uncovered seven domains. While none of them were classified as malware hosts, two were noteworthy.
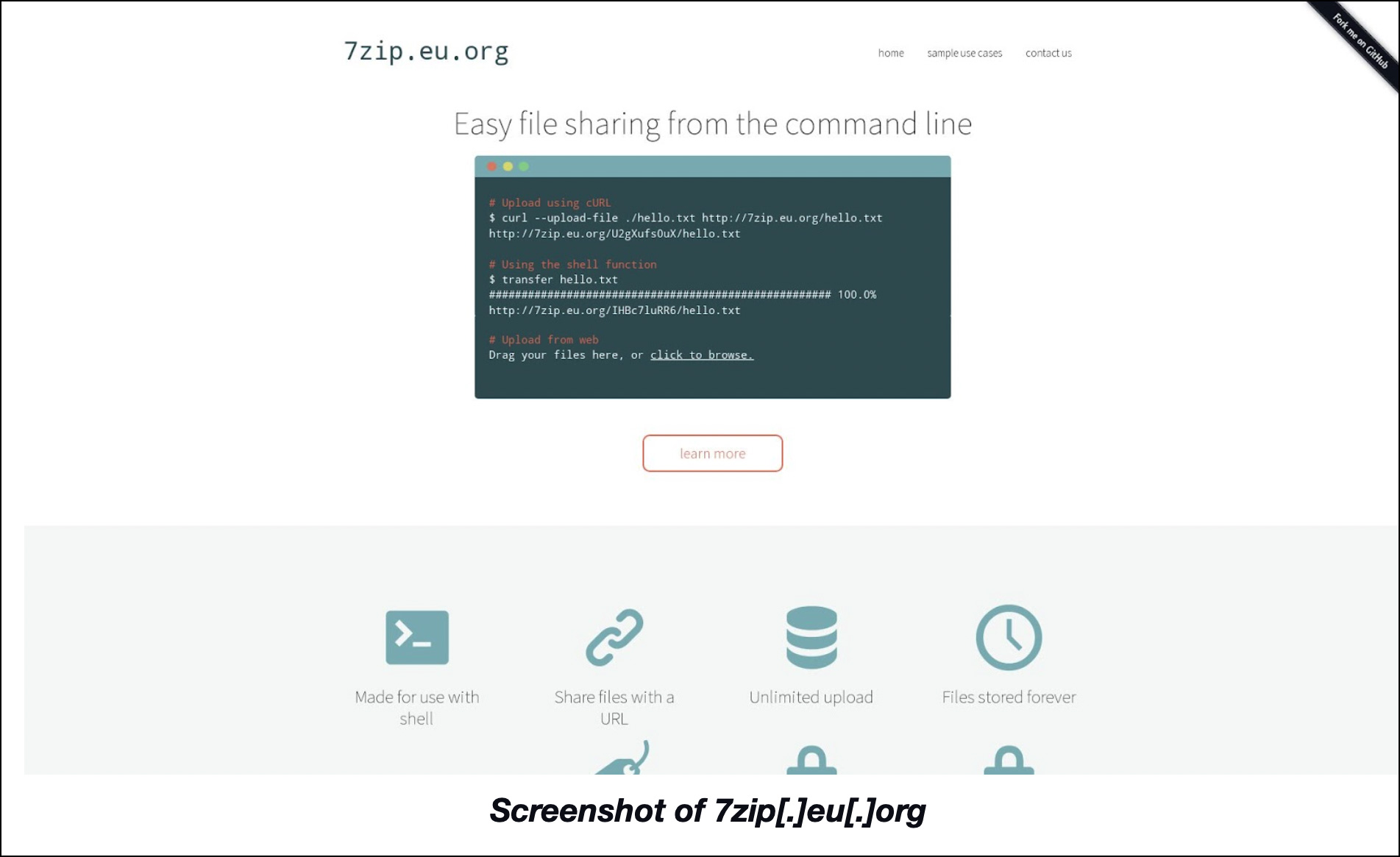
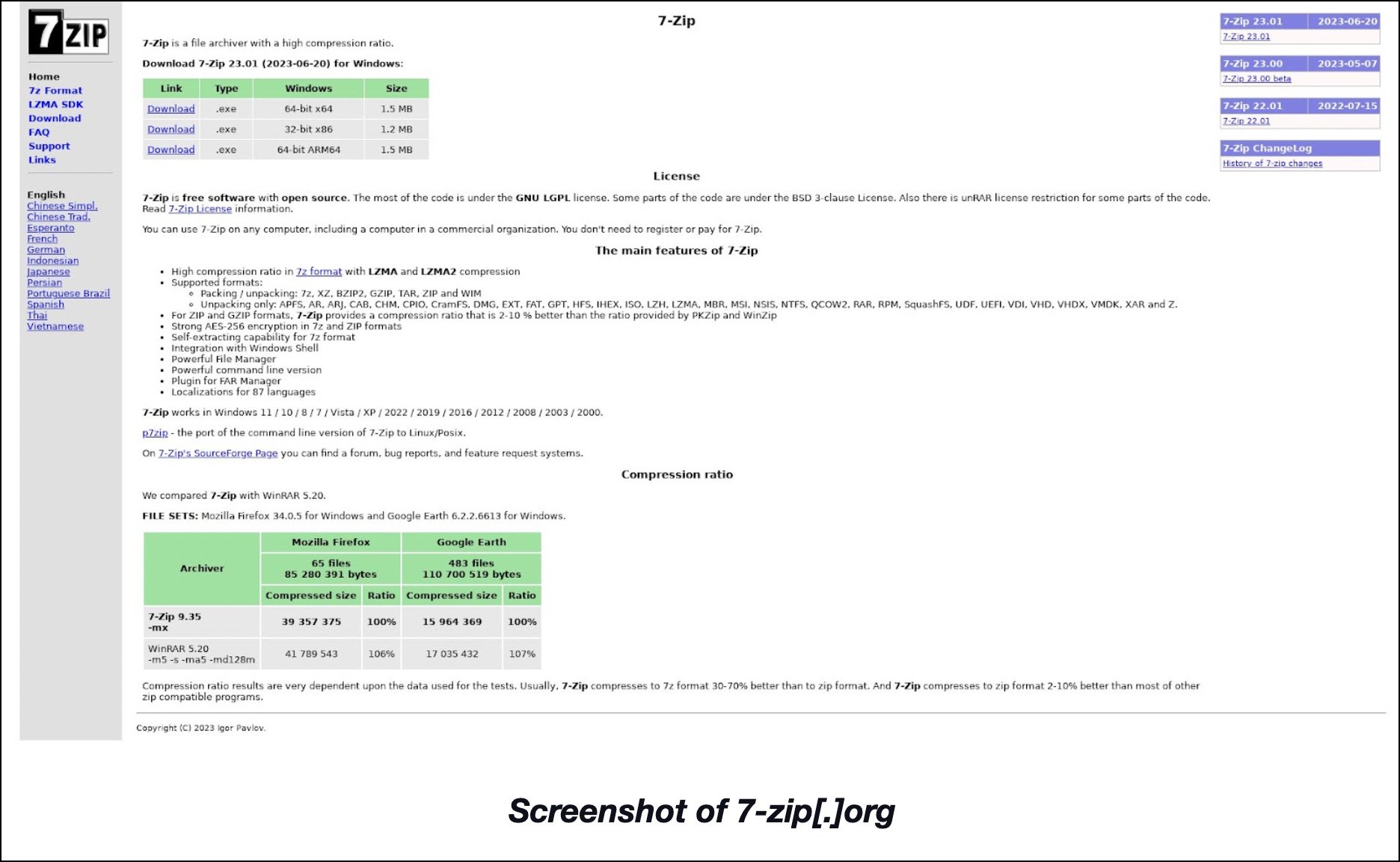
One of the IP-connected domains—7zip[.]eu[.]org—proved most interesting since it contained the name of a well-known open-source file archiver. Despite the presence of 7zip in the domain name, though, its WHOIS record details didn’t share any similarity with that of 7zip’s official domain—7-zip[.]org. 7zip[.]eu[.]org’s content also differed a lot from that of the legitimate website. Take a closer look at the screenshots of 7zip[.]eu[.]org and 7-zip[.]org below.
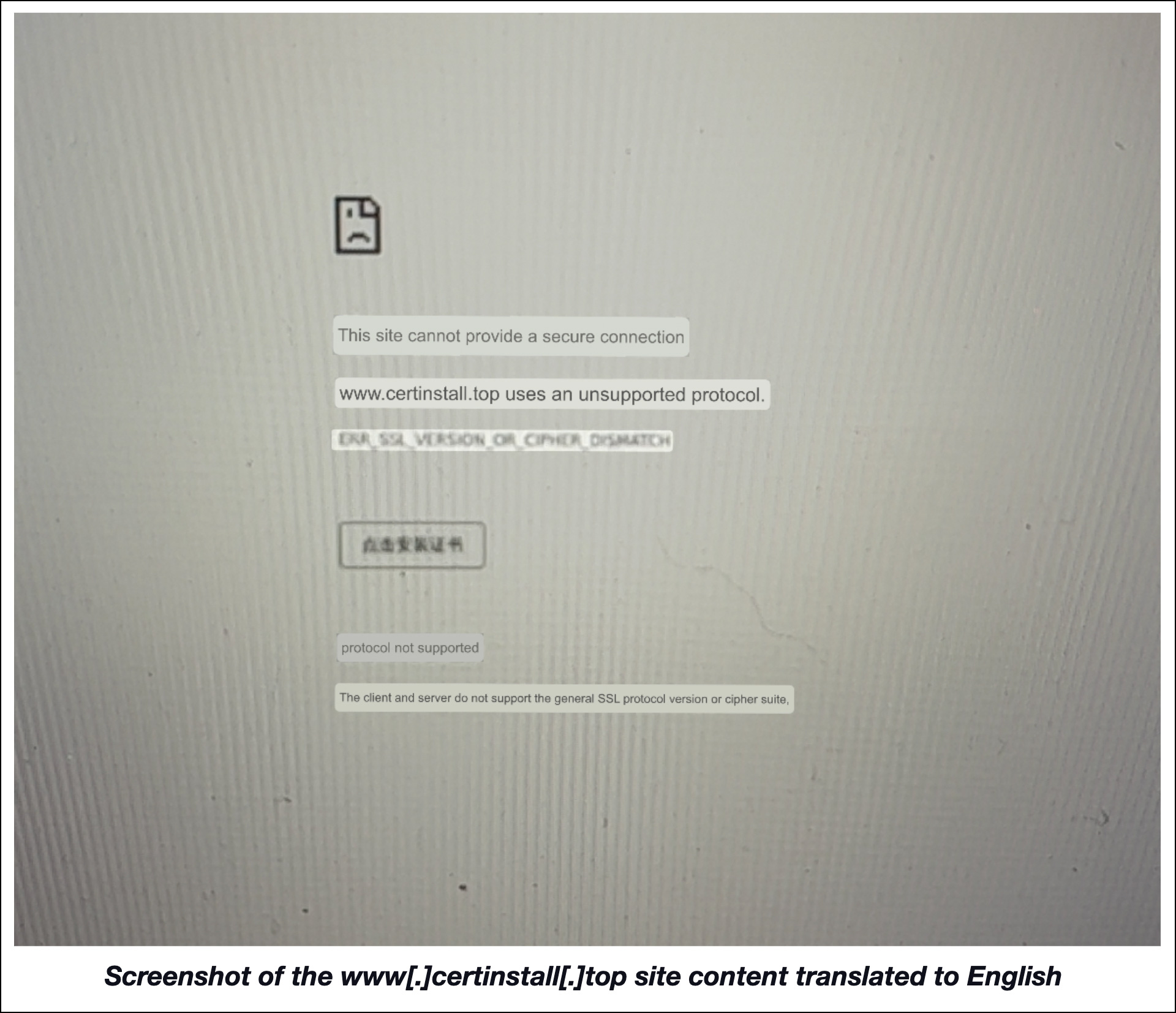
Another interesting IP-connected domain was www[.]certinstall[.]top since it contained the string certinstall. The site hosted on it seemingly offers SSL certificates albeit ones that don’t support general related protocols and some devices, based on the disclaimer. It’s also worth noting that the website doesn’t provide a secure connection.
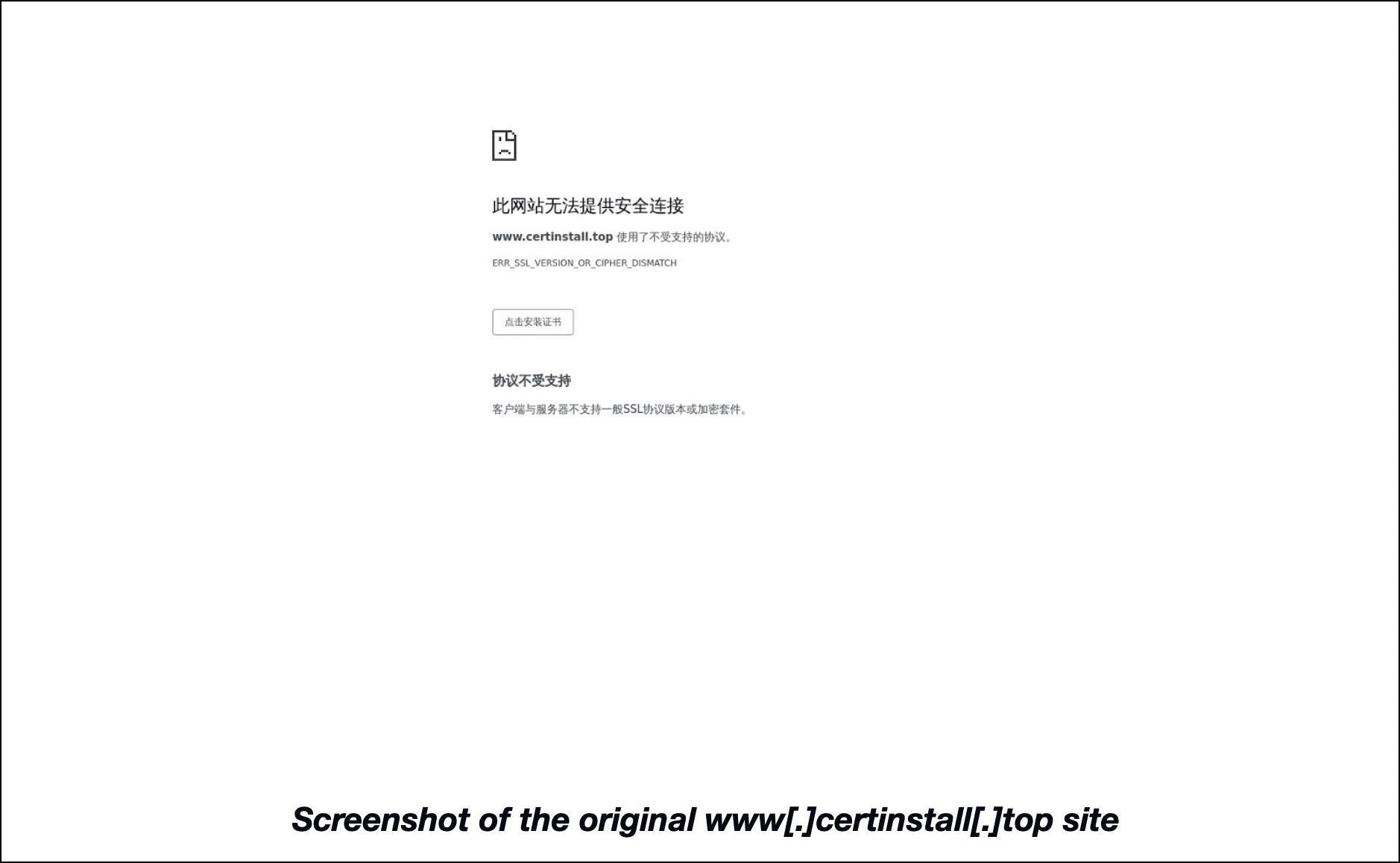
Here’s the text on the www[.]certinstall[.]top website when translated to English.
The screenshots we obtained pushed us to dig even further. As such, we scoured the DNS for domains containing strings found among the IP-connected domains, namely:
We found 2,280 string-connected domains for five of the six strings, except obiwxpt, that is. 47 of them were categorized as malware hosts based on a bulk malware check.
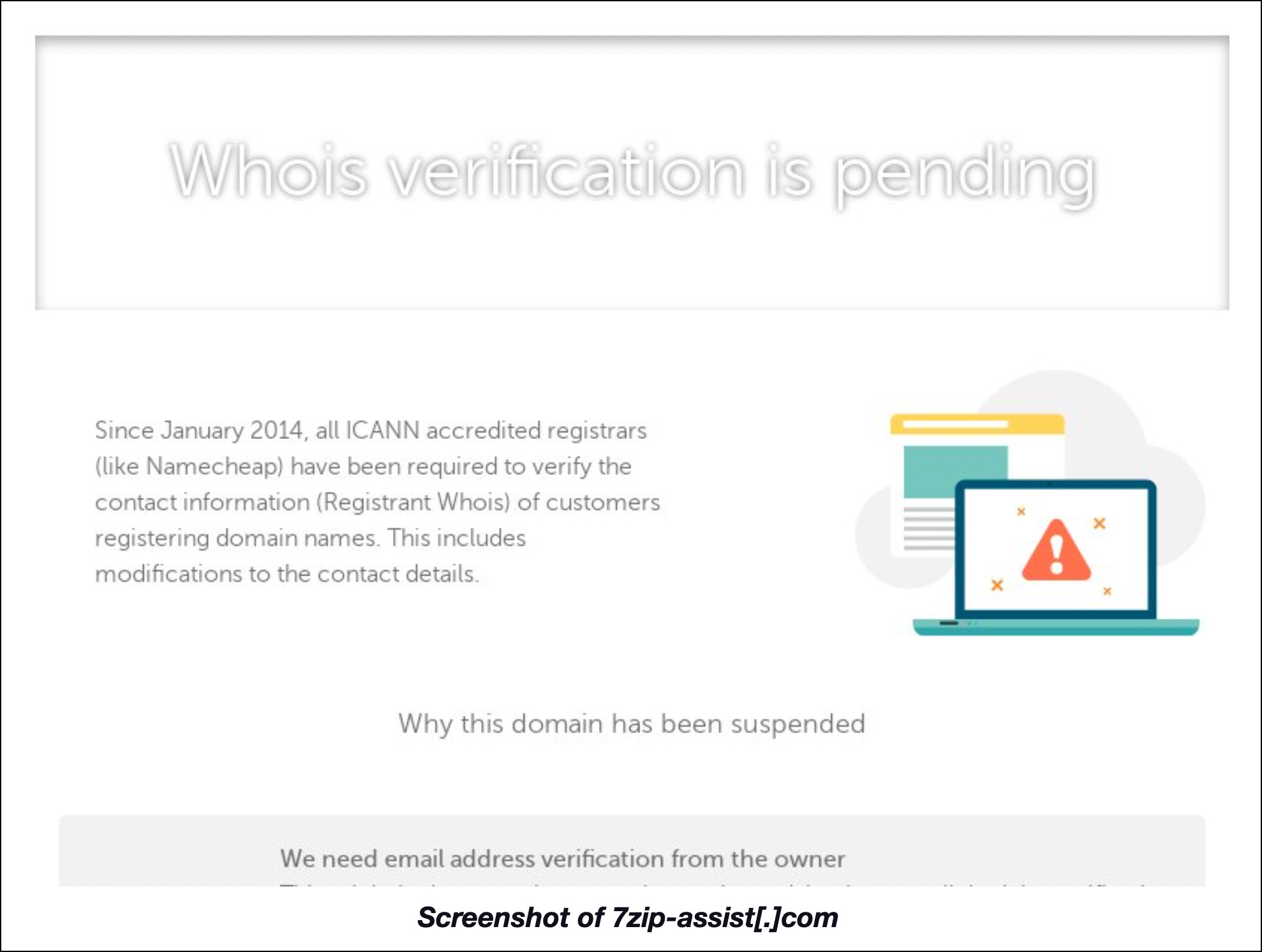
We then zoomed in on the domains containing 7zip and certinstall since many of them could be suspicious at least. Some of the 7zip domains could belong to cybersquatters. A number of the certinstall domains, meanwhile, could be hosting sites offering illegal SSL certificates. While none of the certinstall domains were dubbed malicious, 31 7zip domains turned out to be so. Here is a screenshot of the most notable.
Twelve other malicious 7zip domains continued to host live content to this day.
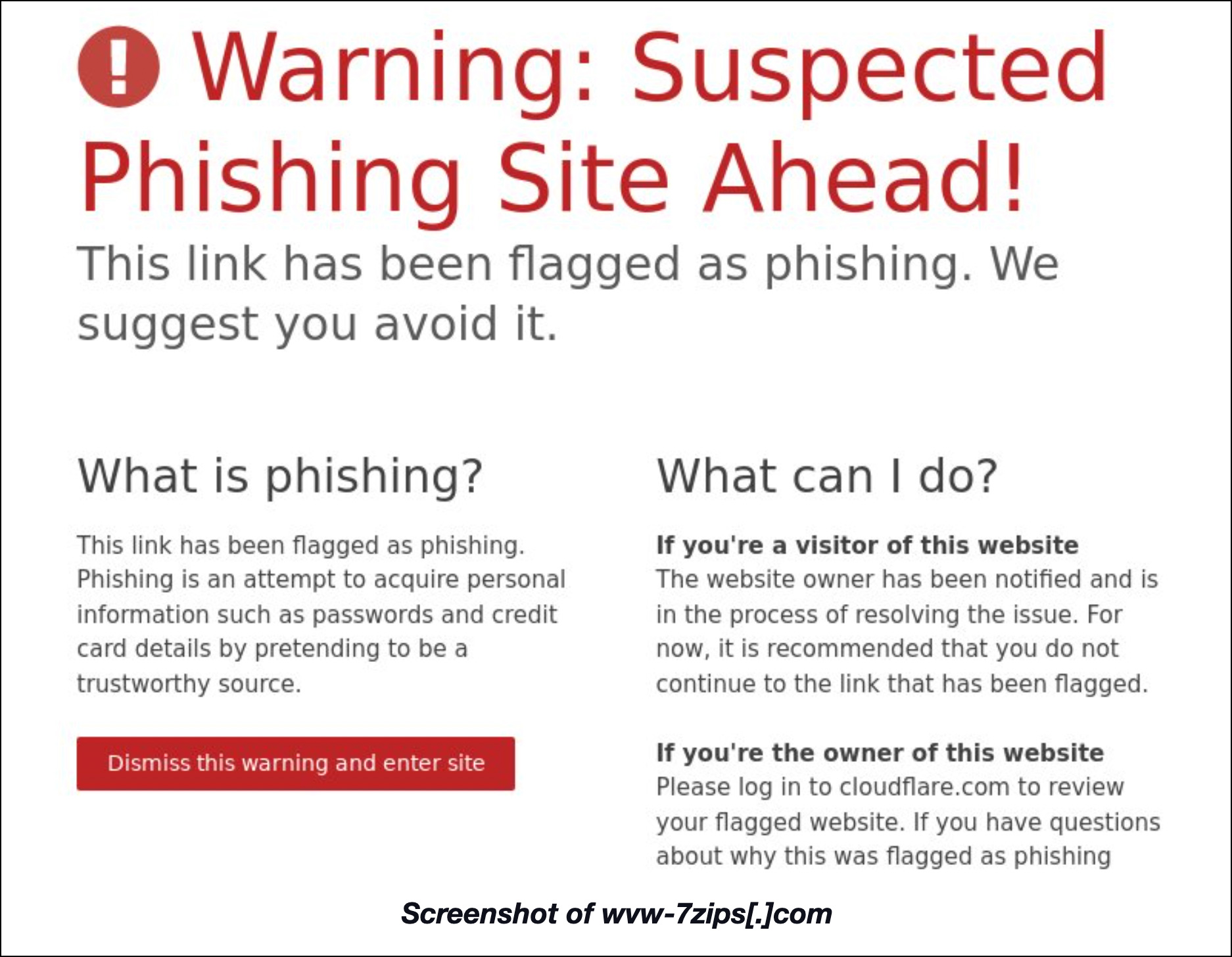
Another domain, wvw-7zips[.]com, also caught our attention in that even if malware engines aren’t currently detecting it as malicious, its screenshot showed this.
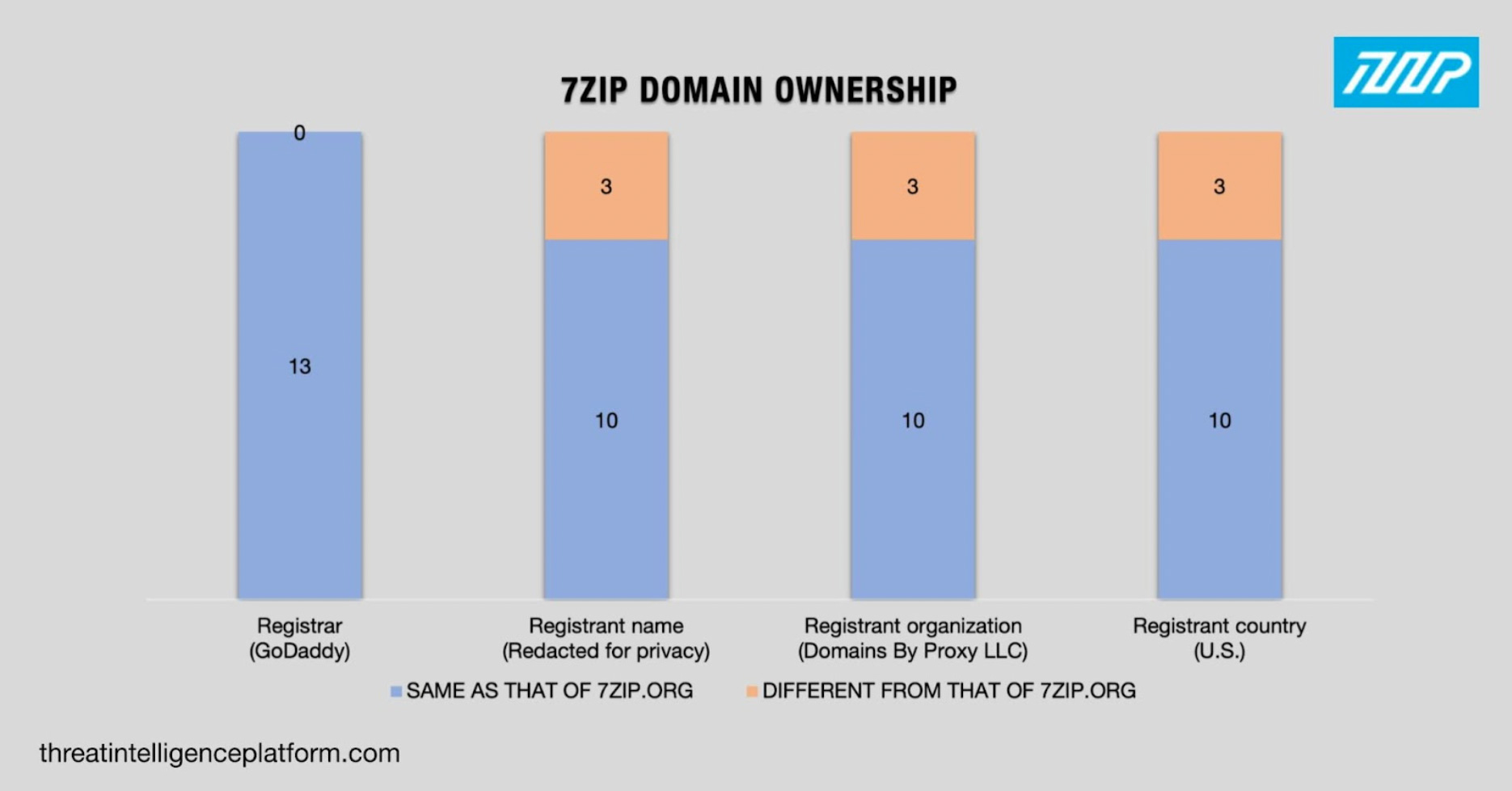
A bulk WHOIS lookup for the 7zip domains also showed that 13 of them shared commonalities with the official 7zip domain. Here’s a summary of our findings even if 7-zip[.]org’s WHOIS record has been redacted for privacy.
All that said, while we can’t definitively say the 10 string-connected domains are publicly attributable to 7zip, they could be.
Screenshot lookups for the 10 string-connected domains showed that a majority, five to be exact, were up for sale; two were live but seemed unrelated to the file archiver; another two were live but didn’t have content; and one pointed to a possibly related product page.
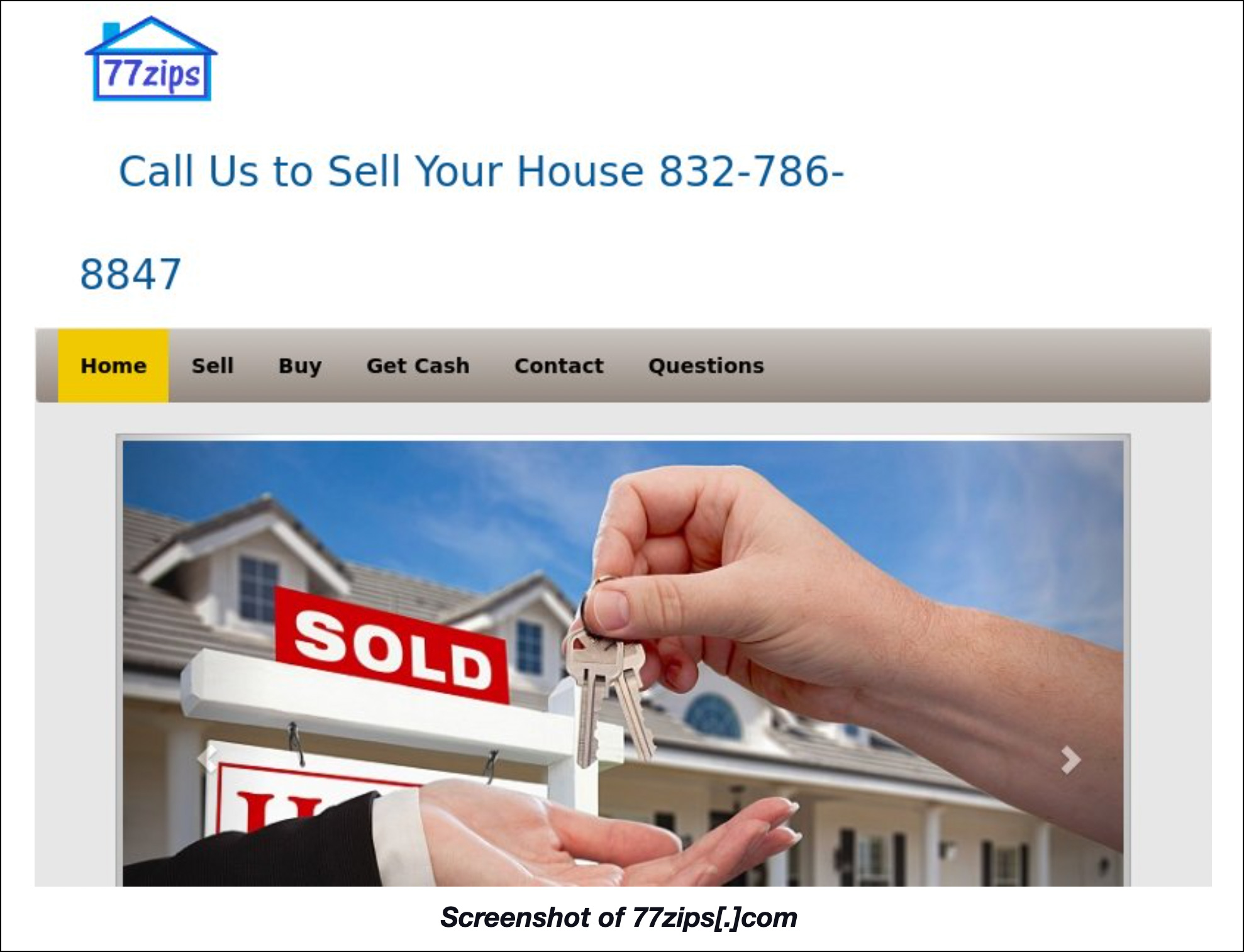
One of the live sites—77zips[.]com—hosted what looked like a real estate site.
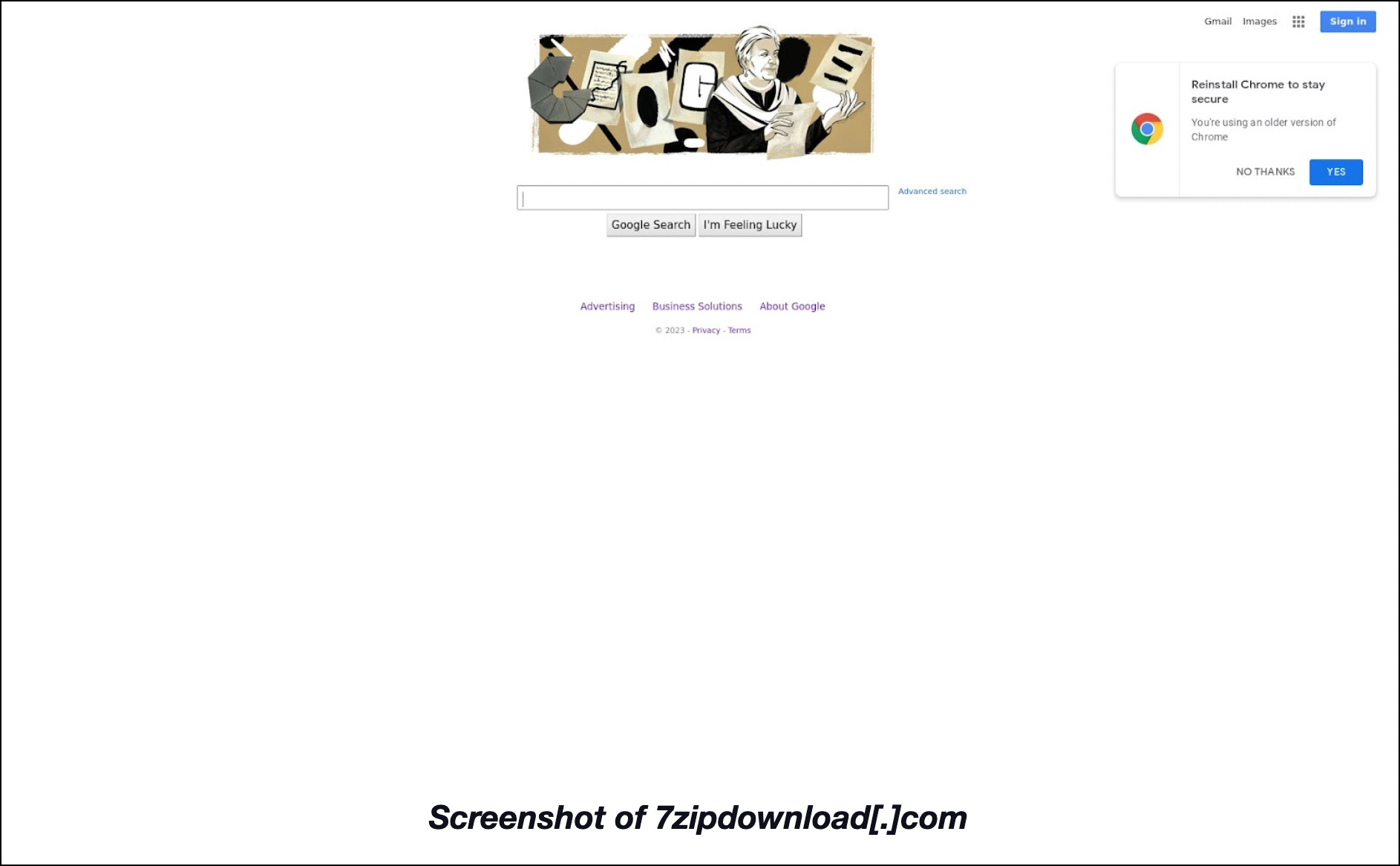
The second—7zipdownload[.]com—sported what looked like a Chrome update page prompting users to download a newer version of the browser.
The third one—7zippasswordrecovery[.]com—showed a software users can utilize to unlock password-protected 7zip-archived files.

Our DNS deep dive into WhiteSnake stealer led to the discovery of more than 2,200 connected domains that remained unreported until today. Close to 50 of them also turned out to be malicious, highlighting the importance of IoC expansion in identifying closely related potential threat vectors before they could wreak havoc on corporate and personal networks alike.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byRadix

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byCSC
