


|
||
|
||
Decoy Dog, a malware renowned for abusing the DNS, specifically by establishing command and control (C&C) via DNS queries, first reared its head most likely in early 2022. Given its sly nature, the DNS malware has been used to successfully steal data from organizations throughout Russia and other Eastern European nations.
Infoblox published its in-depth analysis of the Decoy Dog infrastructure in April 2023, revealing 23 indicators of compromise (IoCs) comprising 11 domains and 12 IP addresses. To identify currently unidentified potential Decoy Dog threat vectors, WhoisXML API used the 23 IoCs as jump-off points for a DNS deep dive that led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
As our first step, we subjected the 11 domains identified as IoCs to a bulk WHOIS lookup. Note that two of the IoCs—hsps[.]cc and rcmsf100[.]net—didn’t have active WHOIS records. We listed our findings for the nine remaining domains on our list.
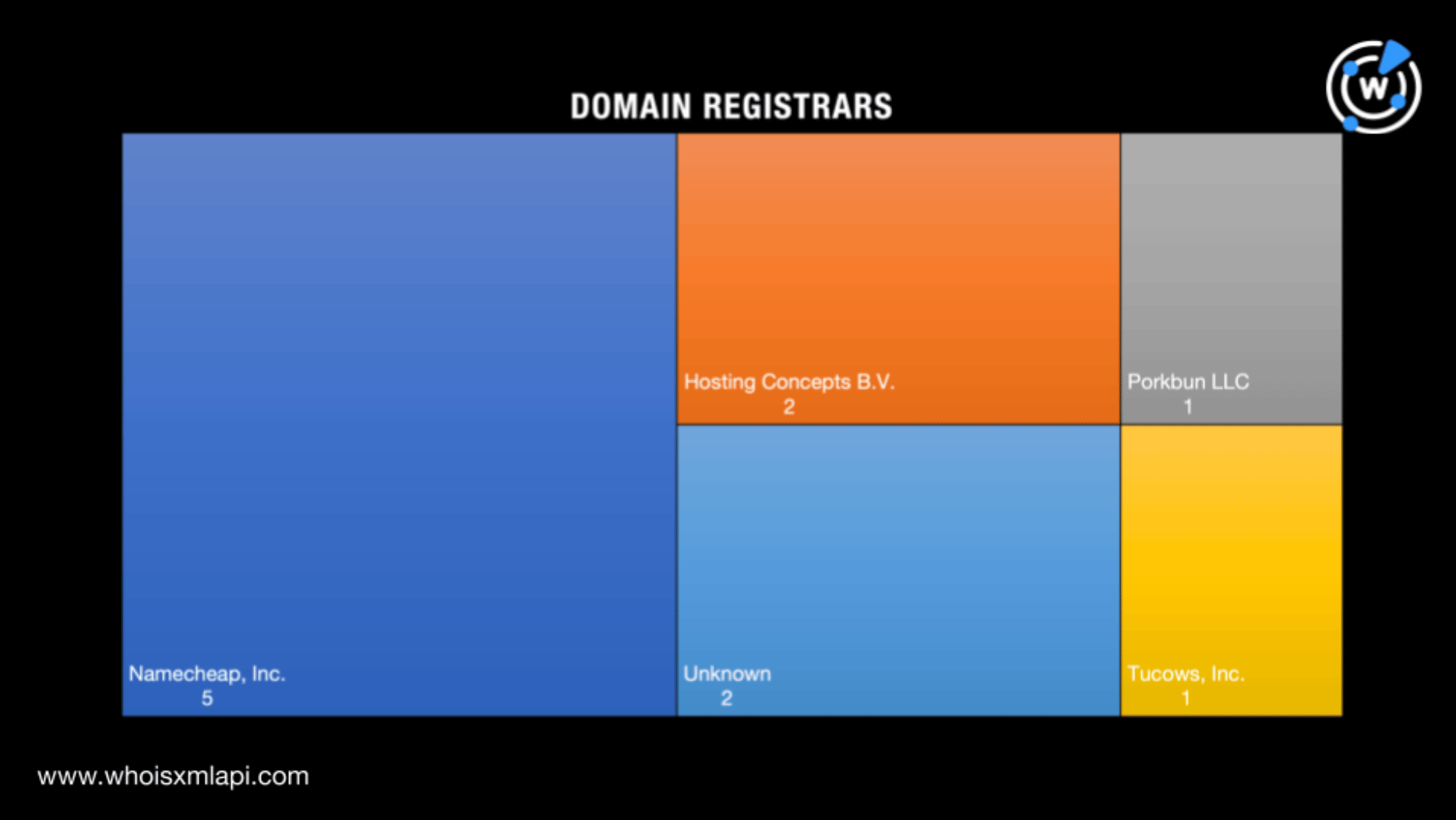
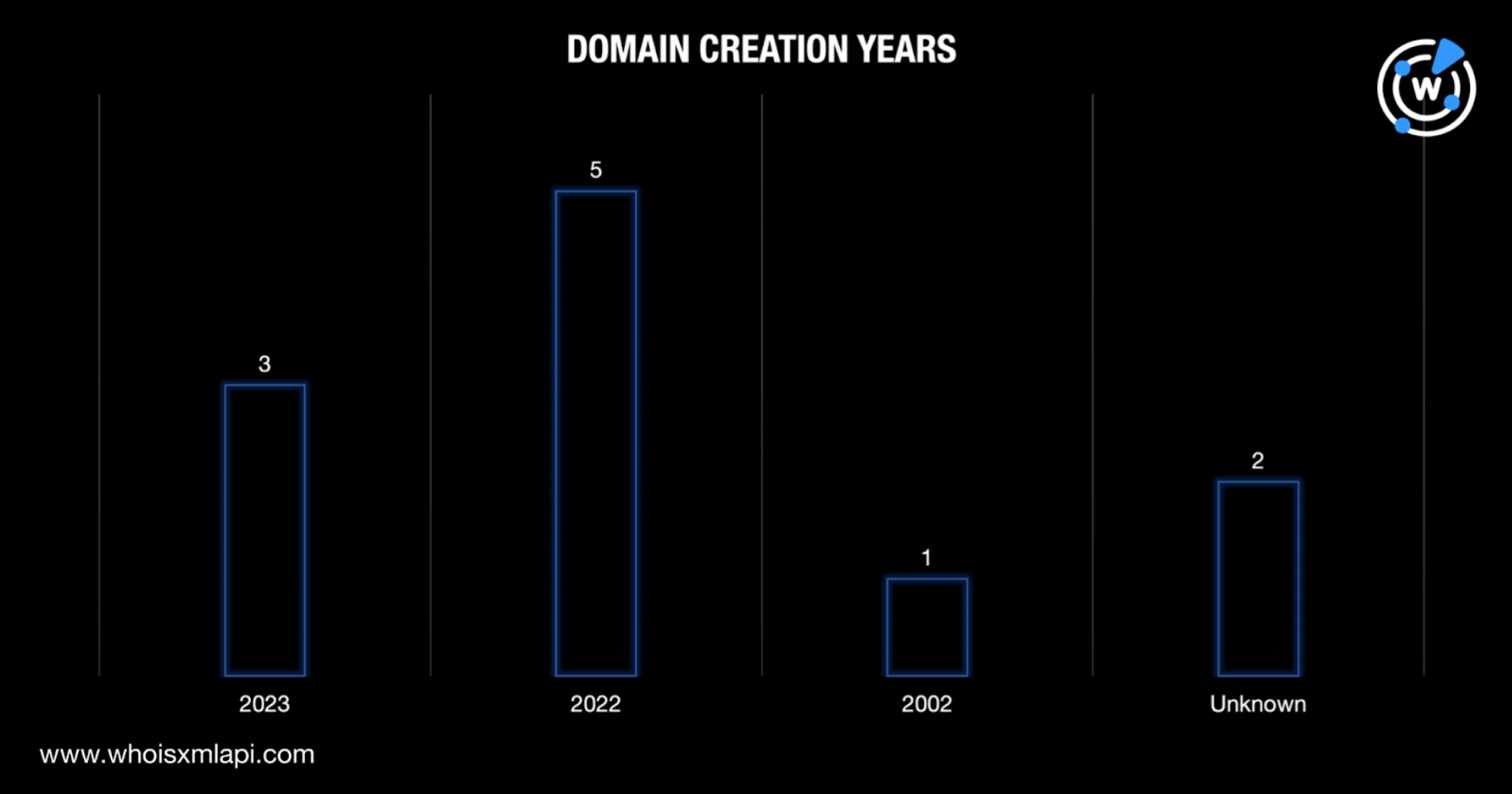
Five of the domains were created in 2022. They were probably used in the first Decoy Dog attacks. Three of the IoCs were created just this year, which could hint at forthcoming attacks. It’s also interesting to note that one of the domains was aged—created way back in 2002.
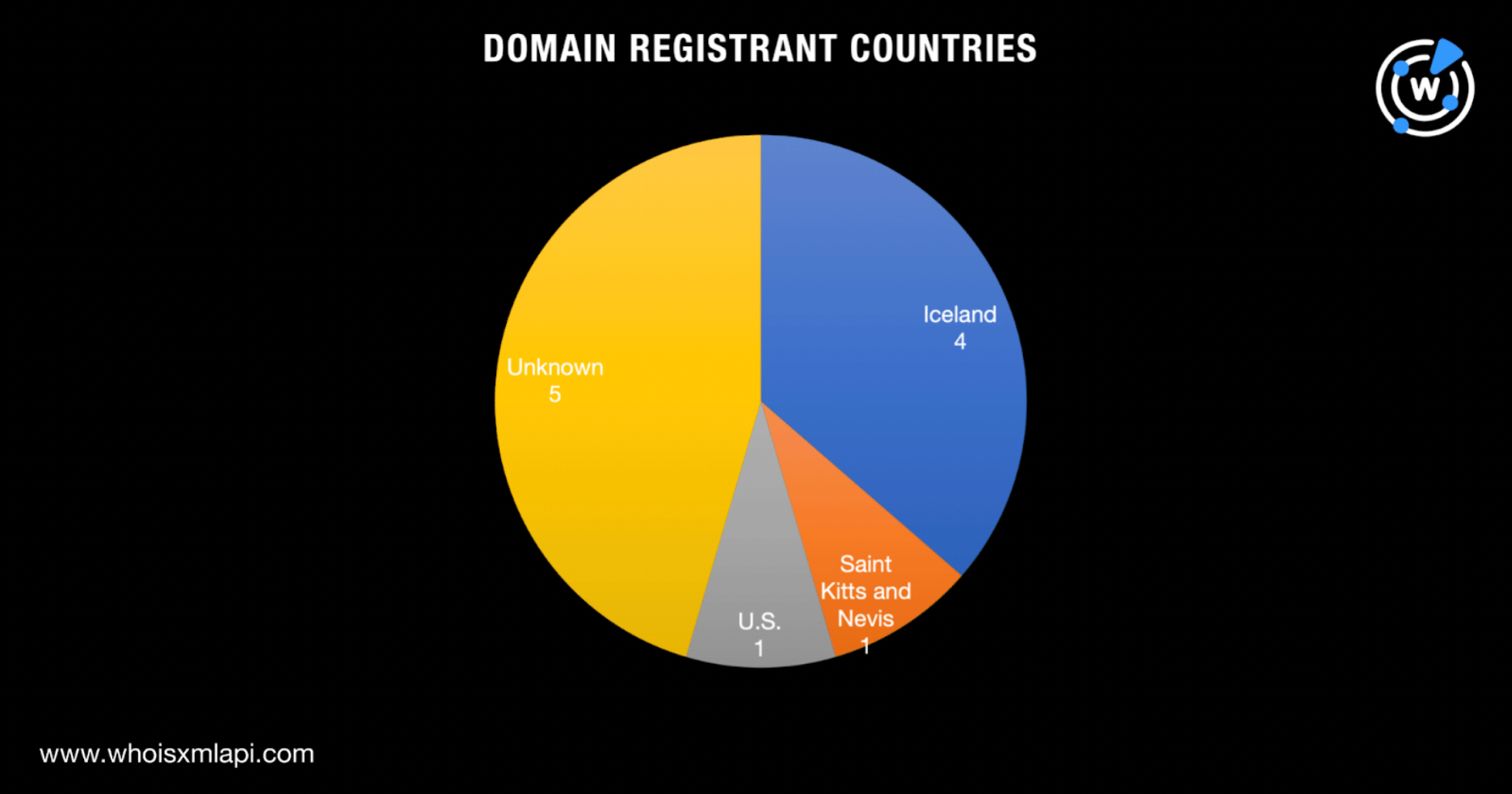
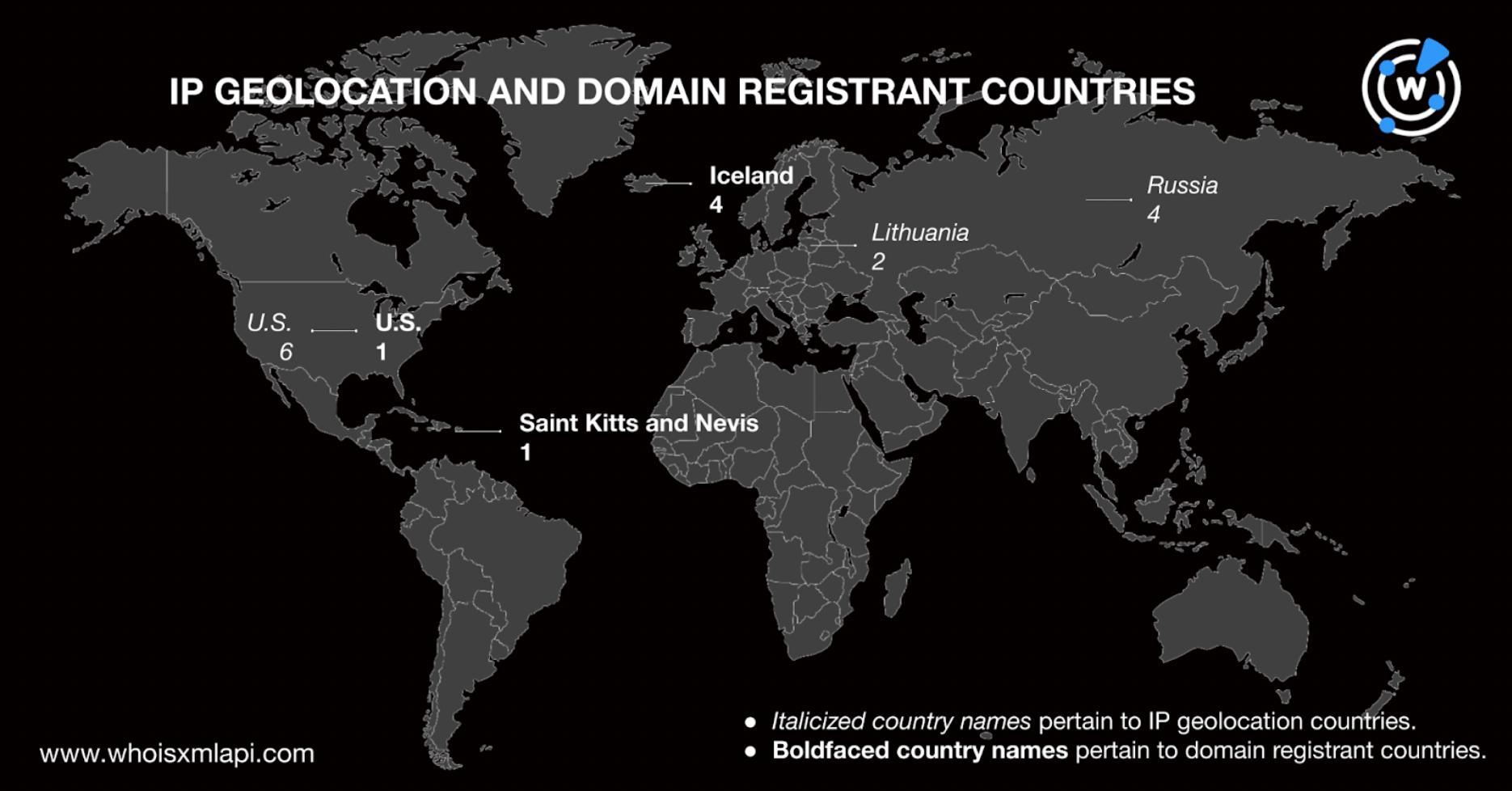
Six of the IoCs were registered across three countries—four in Iceland and one each in Saint Kitts and Nevis and the U.S. Apart from hsps[.]cc and rcmsf100[.]net that we noted earlier for not having active WHOIS records, the owners of the three other domains—hsdps[.]cc, j2update[.]cc, and nsdps[.]cc—had redacted countries.
Next, a bulk IP geolocation lookup for the 12 IP addresses identified as IoCs showed that:
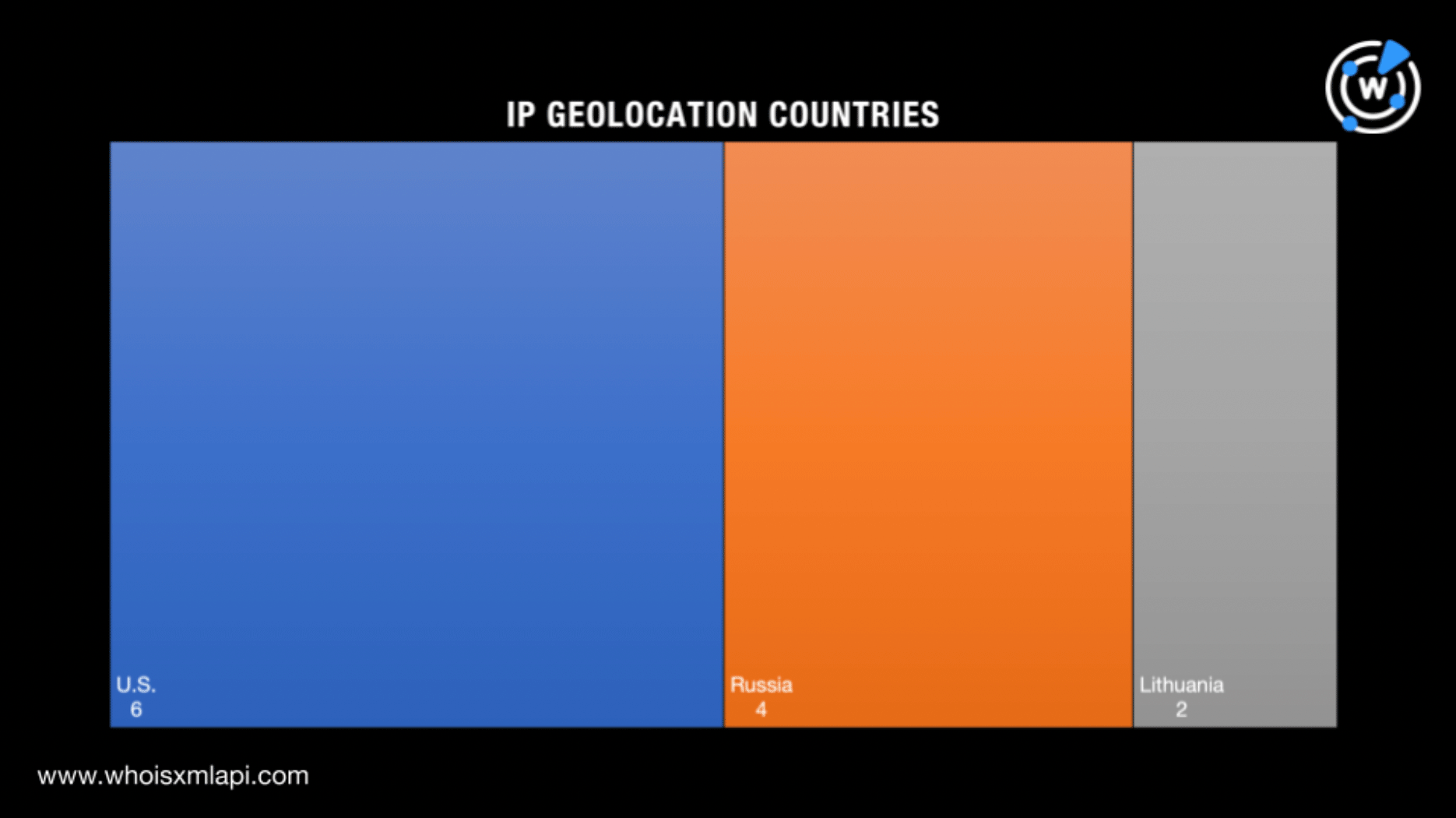
The IP addresses were scattered across nine Internet service providers (ISPs) led by MivoCloud SRL, which accounted for three of the IoCs. GigeNET with two IP addresses took second place.
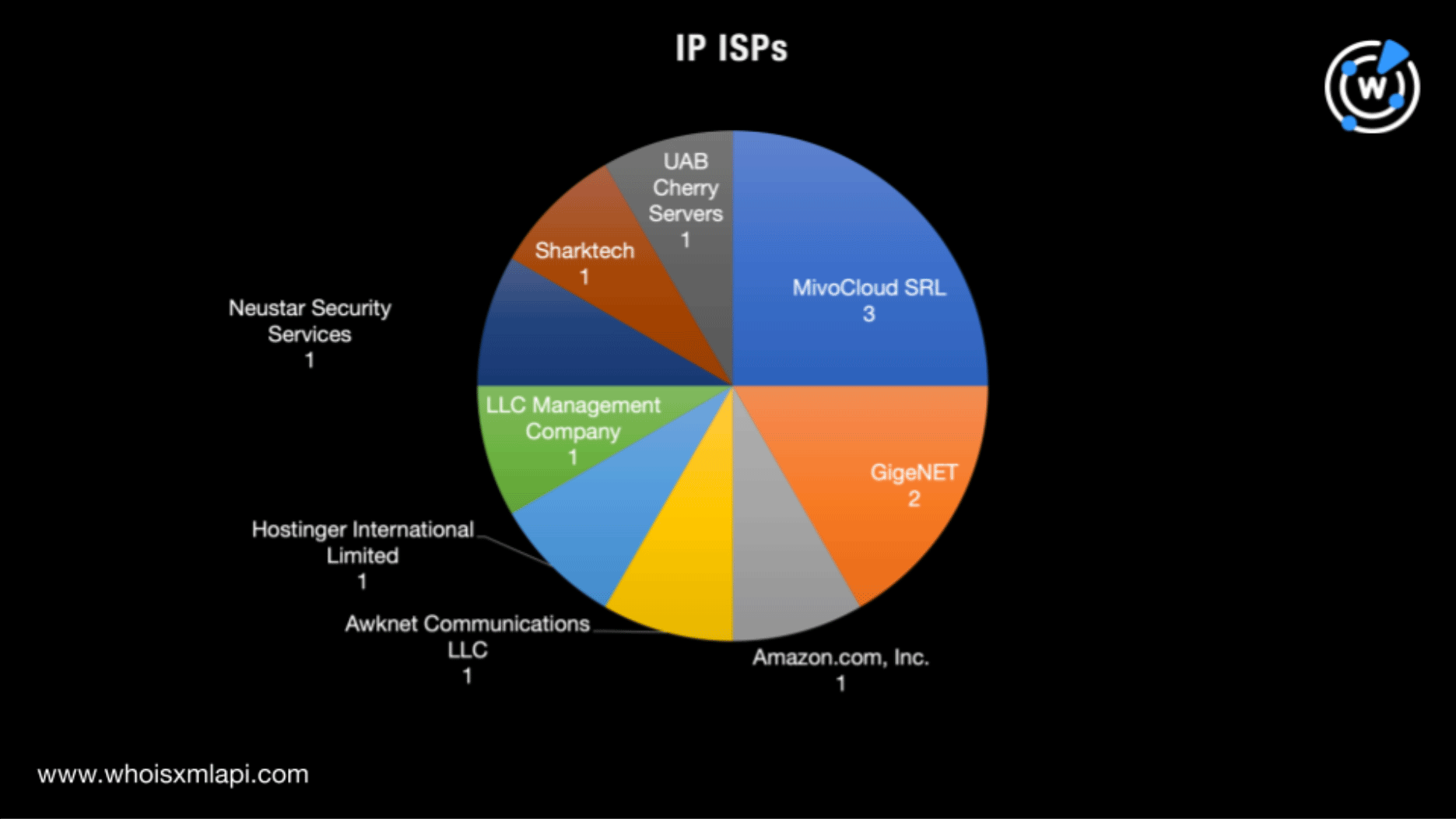
Interestingly, a comparison of the registrant and IP geolocation countries revealed that the IoCs only had the U.S. in common.
To determine if the domains identified as IoCs resolved to IP addresses that weren’t part of the Infoblox list yet, we subjected them to DNS lookups, which led to the discovery of two web properties—192[.]64[.]119[.]51 and 15[.]197[.]130[.]221 that turned out to be malicious according to malware checks.
IP geolocation lookups for the two IP addresses further revealed they hailed from the U.S., similar to six of the IoCs. One of them—15[.]197[.]130[.]221—was administered by Amazon.com, Inc. like the IoC 13[.]248[.]169[.]48.
We then performed reverse IP lookups for the 14 IP addresses in total—12 from the Infoblox IoC list and the two we obtained from our DNS lookups earlier. We found that five of them were dedicated, altogether hosting 90 unique domains. A bulk malware check revealed that four of the IP-connected domains were classified as malicious.
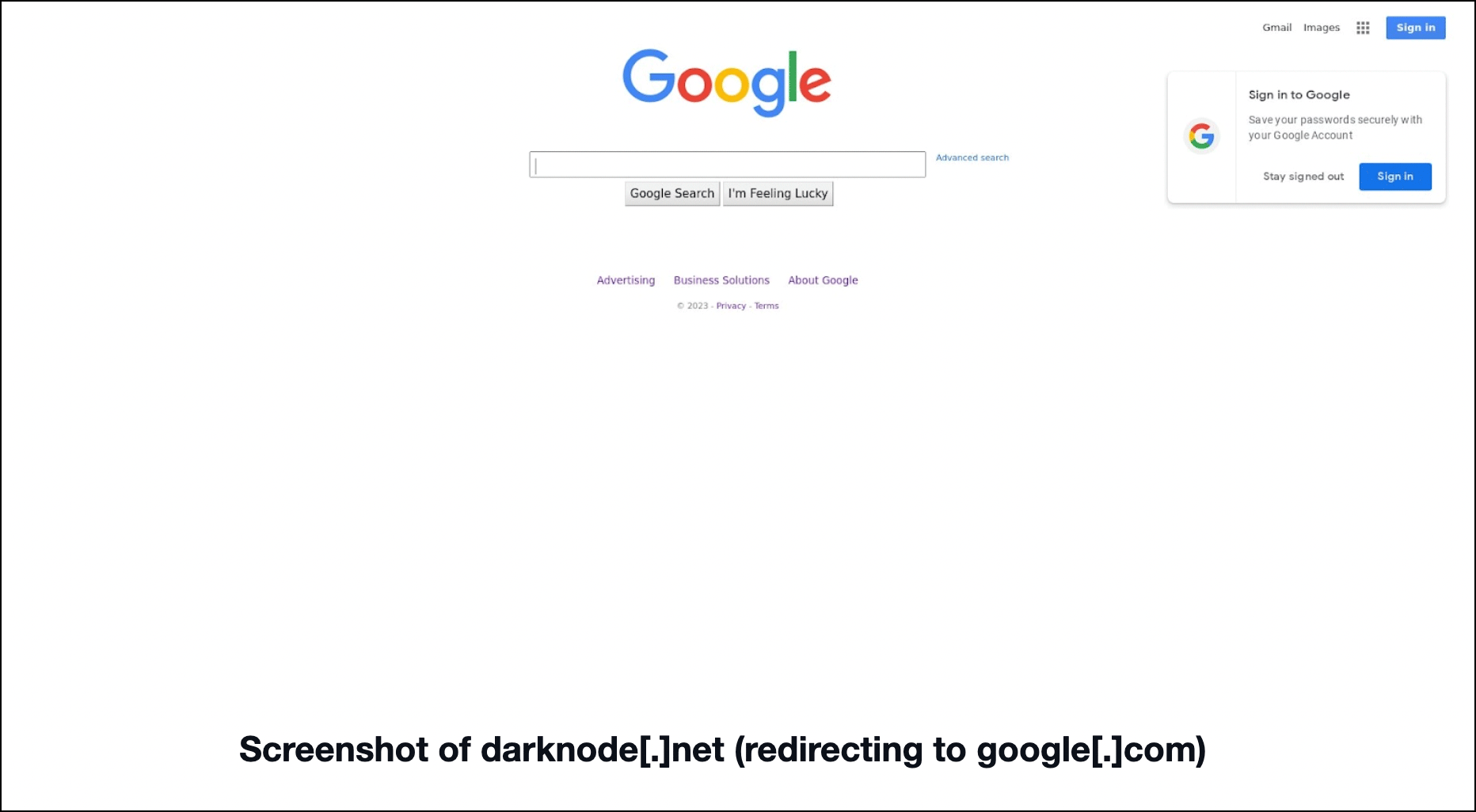
Two of the four malicious IP-connected domains—darknode[.]net and settepani[.]net—continued to point to live content. Darknode[.]net proved noteworthy in that it redirected to a Google search page.
A bulk WHOIS lookup for the IP-connected domains allowed us to see some similarities between them and the IoCs as well, including:
A closer look at the domains identified as IoCs allowed us to identify these 10 strings that appeared in 2,295 other possibly connected artifacts based on Domains & Subdomains Discovery searches:
A bulk malware check for the string-connected domains categorized five of them as malicious.
Our in-depth analysis of the Decoy Dog IoCs uncovered more than 3,000 possibly connected web properties, a couple of which may have already figured in malicious campaigns. It also showed a number of similarities between the newly discovered artifacts and the IoCs Infoblox already made public.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byRadix

Sponsored byCSC
