


|
||
|
||
Financially motivated threat actors called “TA544” were first detected in 2017. TA544 is known for high-volume campaigns, sending hundreds of thousands of malicious messages daily.
While the threat actors used several malware payloads, they are widely known for distributing the URSNIF banking trojan. Proofpoint researchers1 also found TA544 using a new malware dubbed “WikiLoader,” which subsequently led to the installation of URSNIF into target systems.
WhoisXML API researchers gathered 21 domain names and 24 IP addresses publicly listed as indicators of compromise (IoCs)2,3,4,5 as part of recent URSNIF campaigns targeting companies in Italy. Our analysis and expansion of the IoCs led to these key findings.
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We sought to identify the registrars and Internet service providers (ISPs) administering the IoCs. To do that, we ran a bulk WHOIS lookup and found that most of the domains were managed by the American Registry for Internet Numbers (ARIN) and Réseaux IP Européens (RIPE). The top registrars, meanwhile, included Web Commerce Communications (WEBCC) and several Europe-based entities, such as OVH, Scaleway, and Aruba.
We also conducted a bulk IP geolocation lookup on the IoCs and found that about 37% of them were administered by Nice IT Services Group, Inc. and DigitalOcean LLC. The resolving IoCs were primarily geolocated in Europe (74%), with the rest in the U.S. (24%) and the Middle East (2%). The map below shows the breakdown per country.
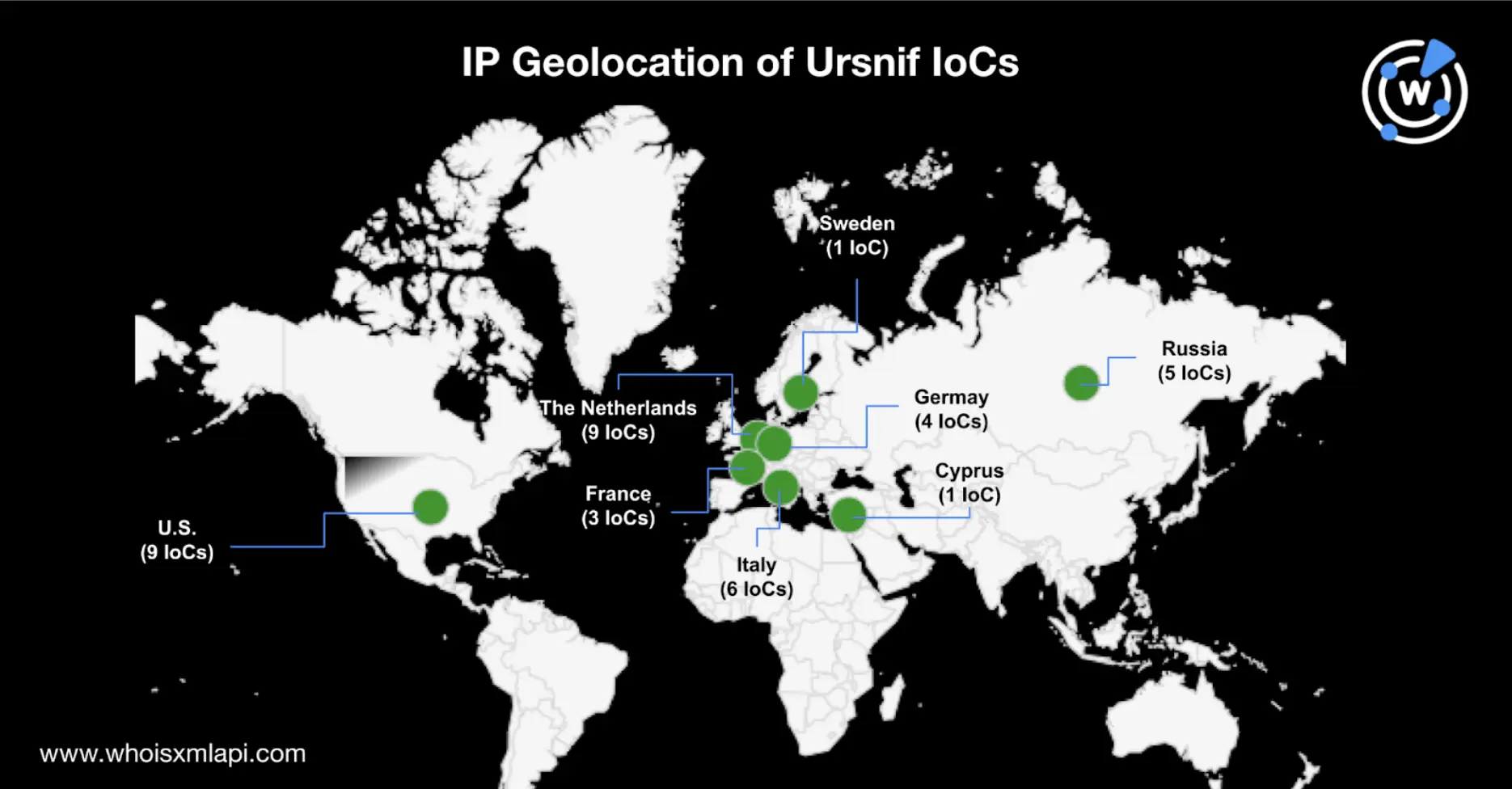
Threat actors use several web resources in their campaigns, and TA544 is no exception. As such, we analyzed the IoCs using DNS intelligence to retrieve domain connections.
First, we obtained their registrant email addresses by looking up the IoCs’ historical WHOIS records. We found 26 email addresses, but very few were unredacted. More than half had the email domain whoisprotection[.]cc. Still, reverse WHOIS searches for the remaining non-redacted email addresses yielded eight artifacts linked to the IoCs.
Reverse IP lookups for the IP addresses tagged as IoCs further revealed that only eight had resolving domains, which led us to 10 additional artifacts. In total, we found 18 IP- and email-connected domains, eight of which were already flagged as malicious.
Some of the artifacts continued to host or redirect to live pages, including what appeared to be an e-commerce website and an Apache test page.
From the list of IoCs and artifacts, we noticed domain names that seemed to spoof Avast and Debian (i.e., avas1t[.]de and debian-package[.]center). Both domains have been reported as malicious on several security databases, prompting us to find out what other similar-looking domains are currently out in the wild.
To do that, we used Domains & Subdomains Discovery and retrieved all domains starting with avast and containing debian that were added from the beginning of this year to 28 August 2023. We found 476 and 591 cybersquatting domains, respectively.
We ran a bulk IP geolocation lookup to see which ones resolved to IP addresses. We found 1,462 resolutions attributed to 805 string-connected artifacts. Ranking the IP addresses based on their number of resolutions, 13 stood out since they each had more than a dozen resolutions.
While that may not be suspicious under normal circumstances, the fact that they were cybersquatting domains may hint at possible malicious or suspicious IP networks. An even more alarming finding is that various security engines flagged a few of the IP addresses as malicious.
| Malicious IP Address | Number of Resolutions | Sample Resolving Domains and Subdomains |
|---|---|---|
| 54[.]153[.]56[.]183 | 31 | avastone[.]com[.]de avast2014win81[.]com[.]de duchangzuidebianhucijisilu[.]se[.]net |
| 34[.]102[.]136[.]180 | 24 | avasthome[.]site avastargallery[.]com debianns[.]com |
| 91[.]216[.]248[.]22 | 21 | avastwin81[.]clan[.]rip avastwin81[.]webspace[.]rocks agenda-debian-test[.]2ix[.]de |
| 91[.]216[.]248[.]21 | 20 | avast-free-antivirus[.]2ix[.]de debian4[.]clan[.]rip debian6[.]4lima[.]ch |
| 91[.]216[.]248[.]20 | 18 | avast2014pojie[.]4lima[.]de debianpcjjos[.]lima-city[.]de httpd-debian[.]lima-city[.]de |
| 45[.]79[.]222[.]138 | 9 | avastwin81[.]com[.]ph debian6[.]org[.]ph debianvm[.]mil[.]ph |
| 162[.]55[.]0[.]137 | 9 | avast-free-antivirus[.]square7[.]de debian3[.]bplaced[.]net debianhelp[.]square7[.]de |
| 15[.]197[.]142[.]173 | 8 | avastgalaxy[.]com avastlog[.]com avastore2023[.]com |
Some of the cybersquatting domains and subdomains also hosted or redirected to questionable live pages. For example, these showed very similar login pages.
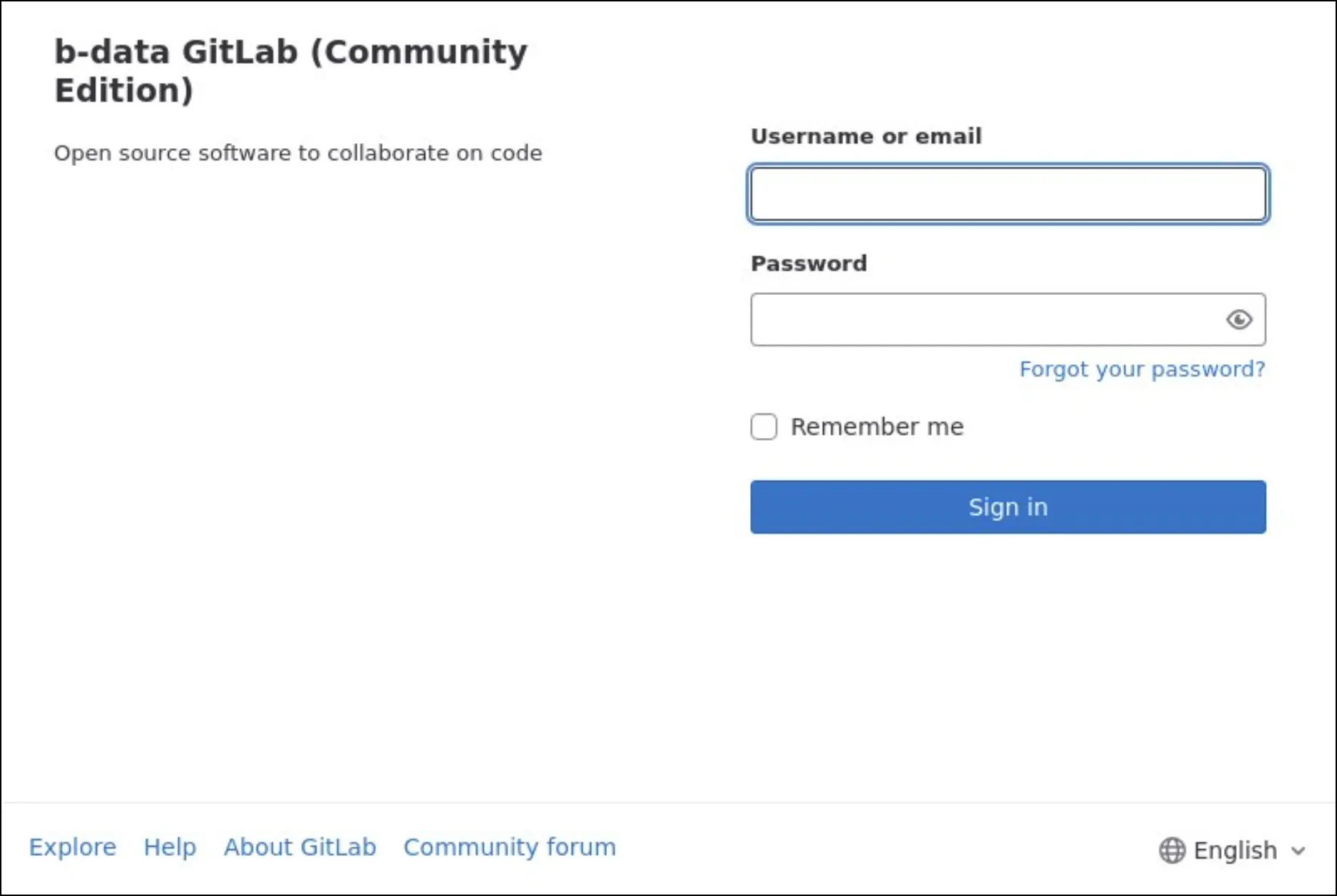
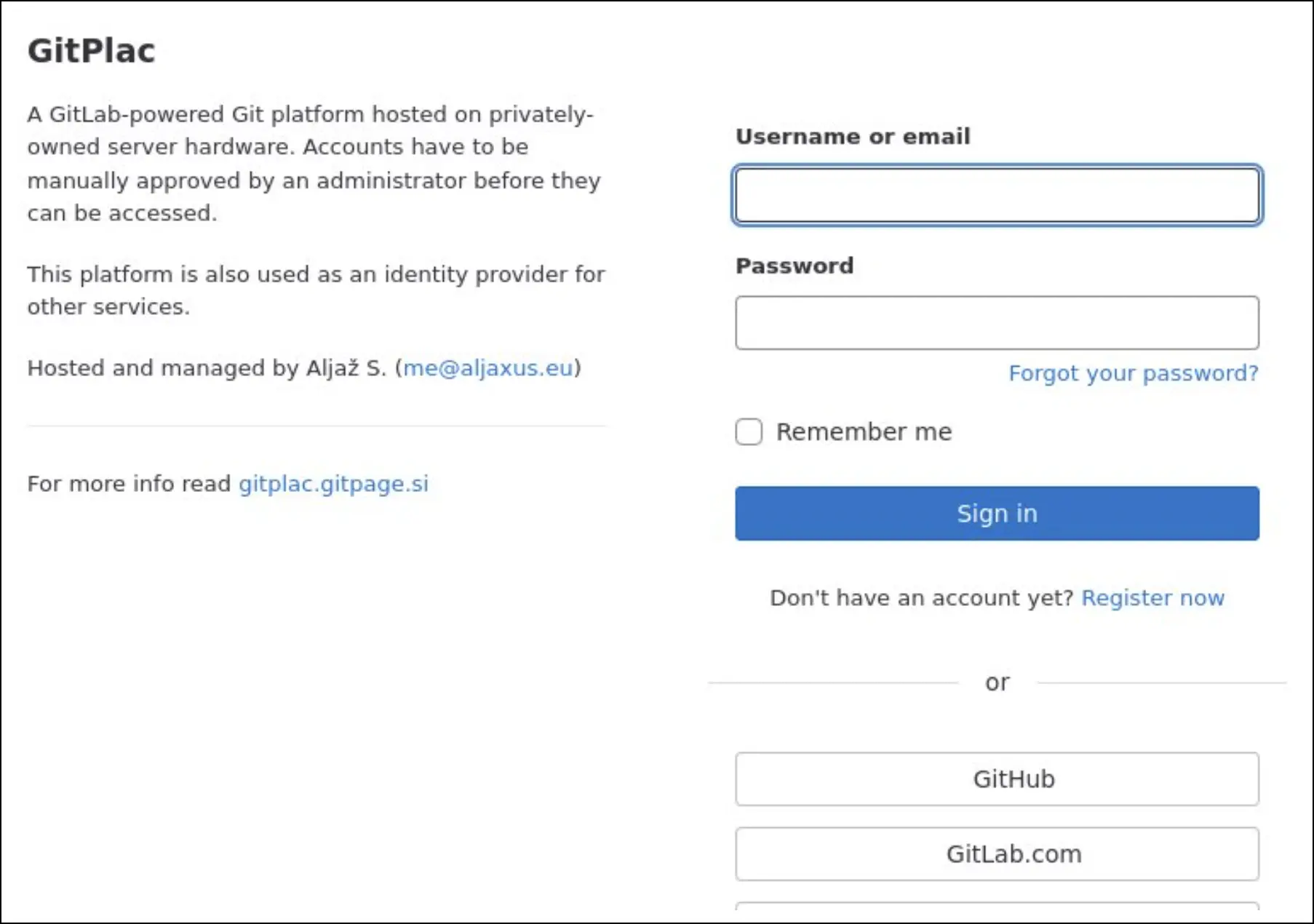
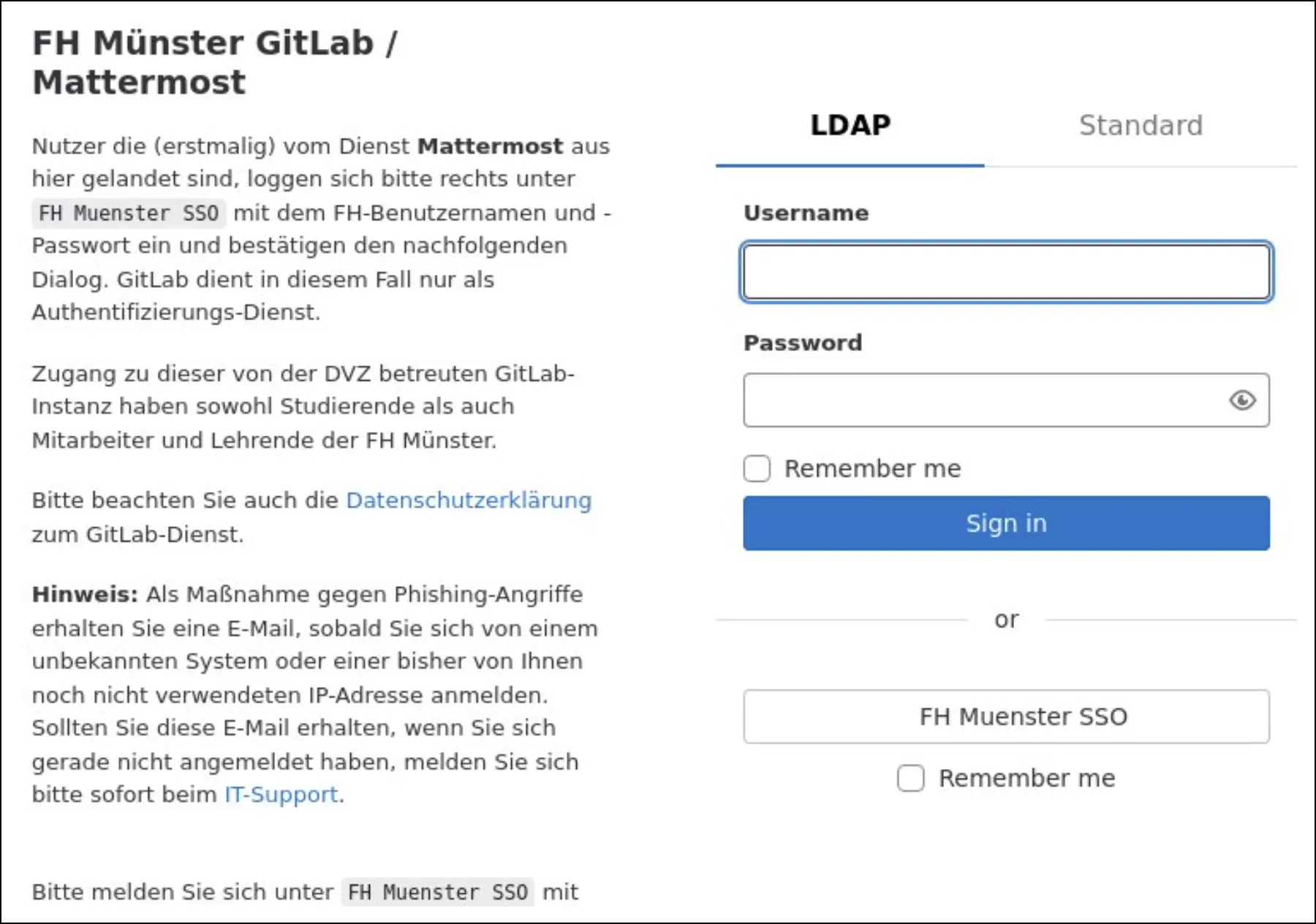
Whether or not these cybersquatting domains were directly related to URSNIF and TA544, they still raised suspicion because of their connection to malicious IP addresses and their impersonation of widely used systems.
URSNIF has consistently evolved and remained persistent over the years, with threat actors using the Trojan to target hundreds of banks and steal thousands of sensitive credentials. The cybersecurity community can benefit from any insight that can help prevent the threat it poses. As such, the artifacts we discovered in this research may aid security investigators in tackling URSNIF and the threat actors behind it.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byCSC

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byIPv4.Global

Sponsored byRadix
