


|
||
|
||
Malwarebytes Labs recently published a report on the latest Nitrogen malware campaign that has been targeting system administrators using fake ads in the guise of Google sponsored search results. According to the security analysts, the victims are currently limited to North America.
Nitrogen comes disguised as a PuTTY (a Secure Shell [SSH] and telnet client for Windows) or FileZilla (a File Transfer Protocol [FTP] solution) installer. When installed, the malware enables threat actors to gain initial access to target networks to steal data or install ransomware like BlackCat.
The Malwarebytes security analysts identified 13 indicators of compromise (IoCs) in their report comprising 11 domains and two IP addresses. The Threat Intelligence Platform (TIP) research team used these 13 IoCs as jump-off points for an expansion analysis that led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
Before we attempt to find other traces of the Nitrogen campaign’s infrastructure in the DNS, let us take a closer look at the 13 IoCs first.
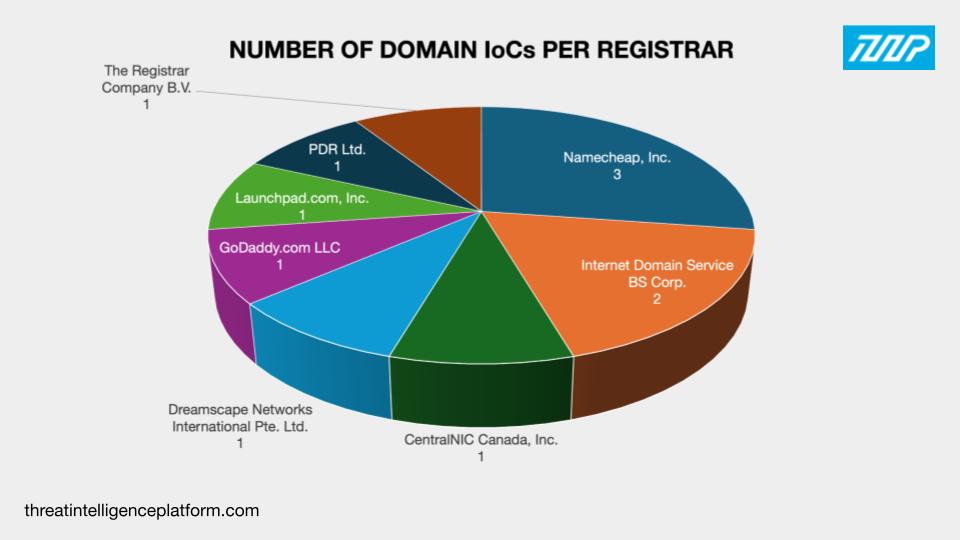
The WHOIS records of the 11 domains classified as IoCs revealed that:
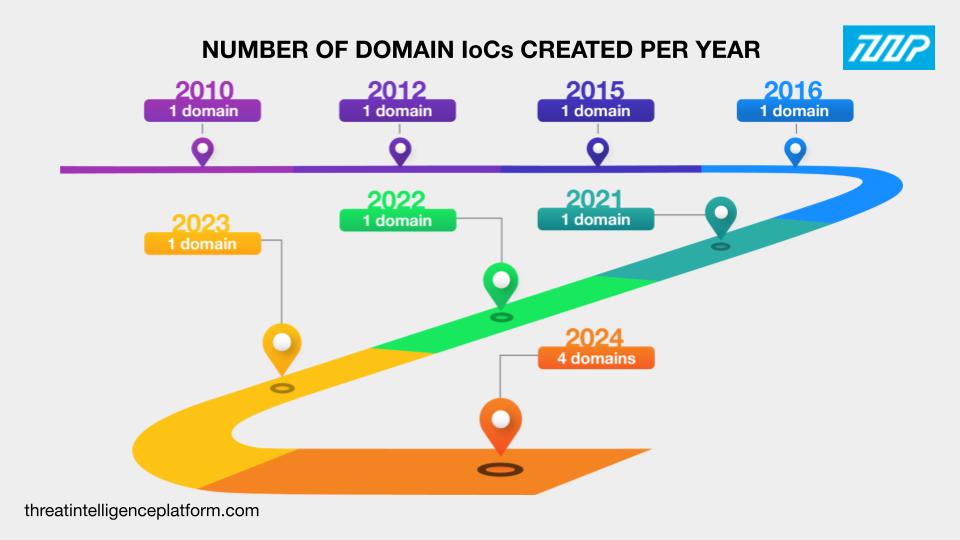
The Nitrogen campaign operators used a combination of old and new domains for their attacks. In fact, the 11 domain IoCs were created between 2010 and 2024. One domain IoC each was created in 2010, 2012, 2015, 2016, 2021, 2022, and 2023. Four domain IoCs were newly registered, created in 2024.
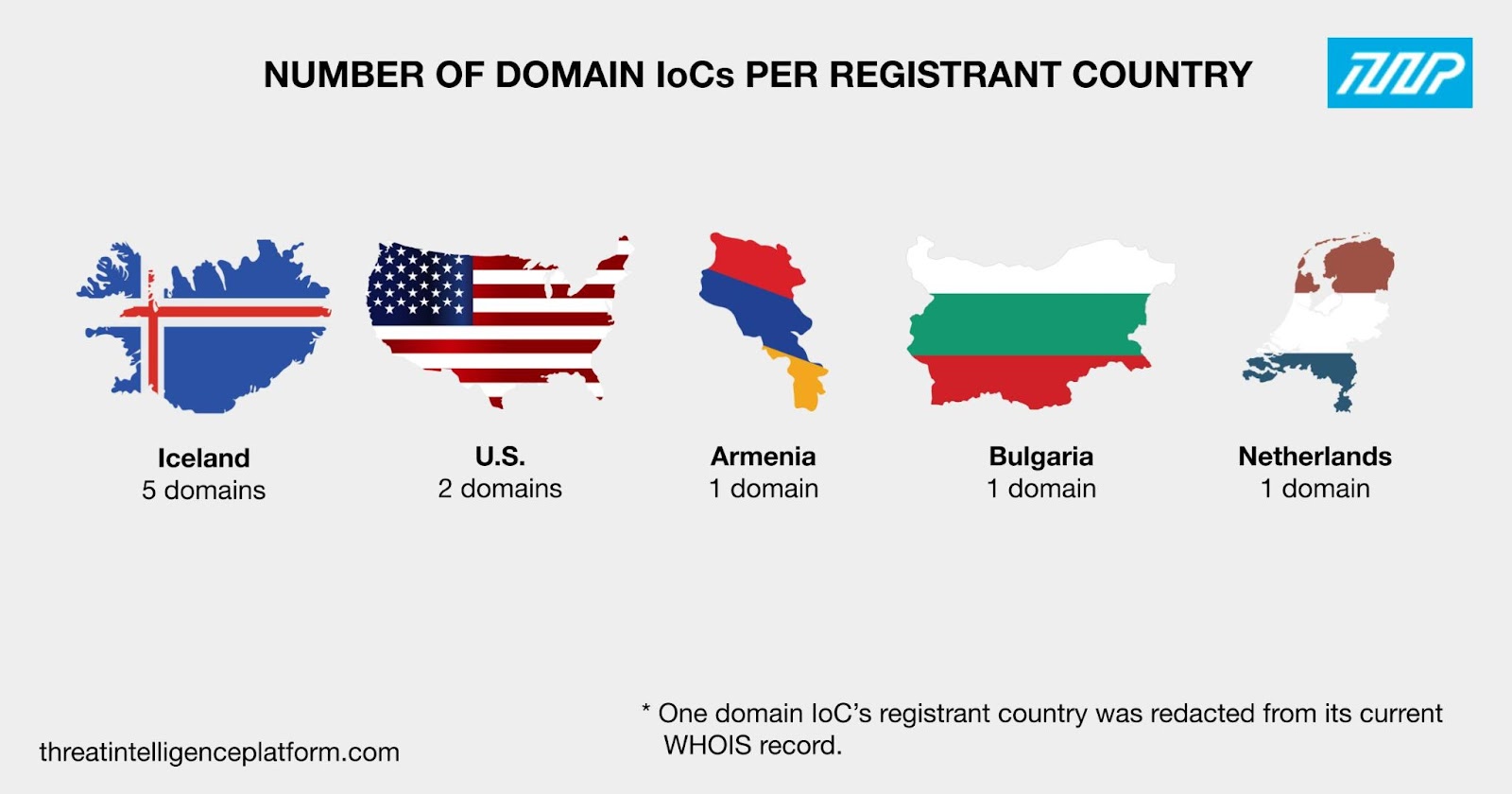
Iceland topped the list of registrant countries, accounting for five domain IoCs. The U.S. took the second spot with two domain IoCs. Armenia, Bulgaria, and the Netherlands accounted for one domain IoC each. Finally, one domain IoC’s registrant country was redacted from its current WHOIS record.
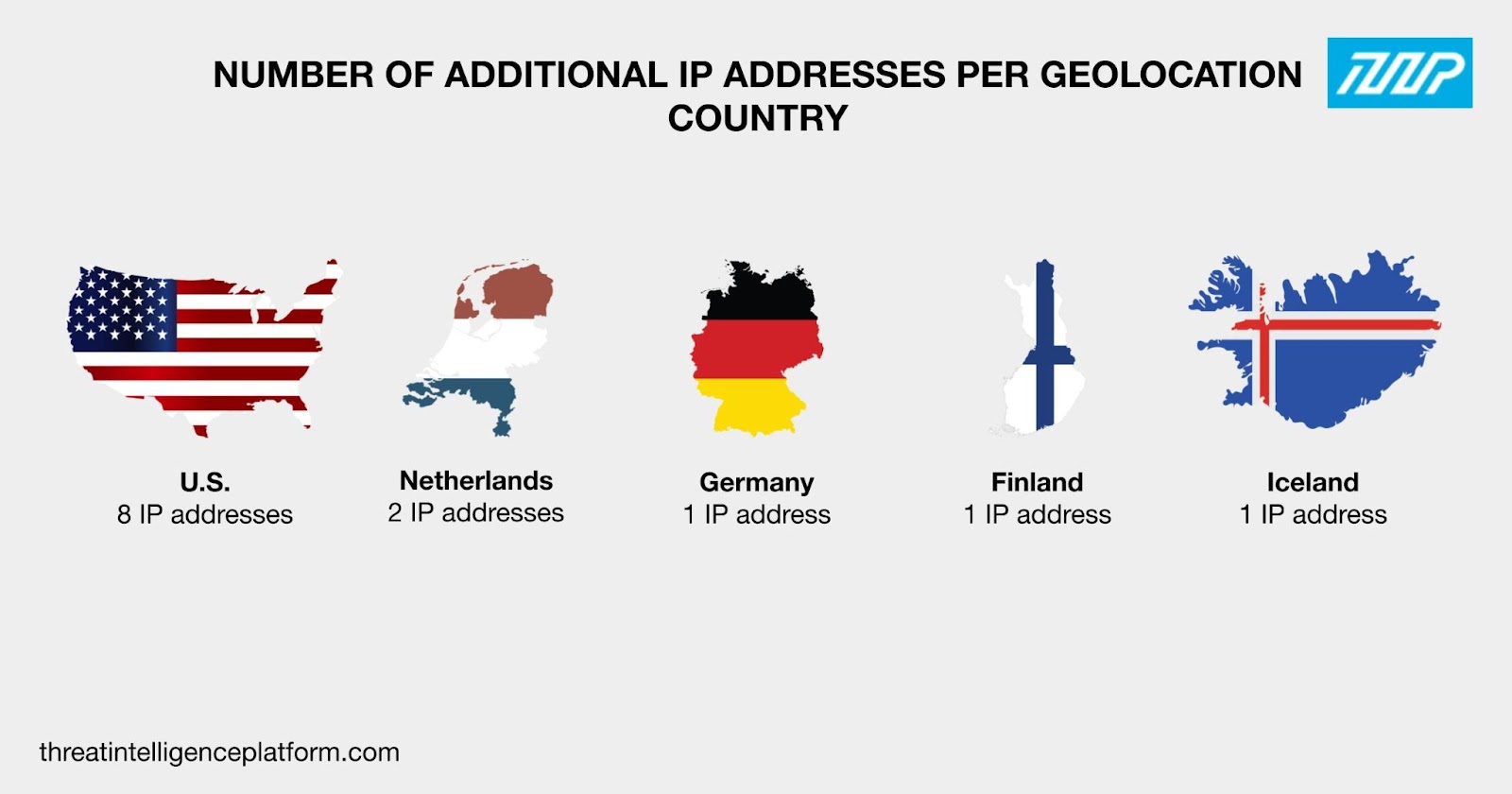
Next, we looked at the IP records of the two IP addresses named as IoCs and found that both were geolocated in the Netherlands and administered by Limenet.
An in-depth investigation of the historical WHOIS records of the 11 domains categorized as IoCs provided 41 unique email addresses, 10 of which turned out to be public. They also appeared in the current WHOIS records of 18 domains after duplicates and the IoCs were filtered out.
A closer look at the DNS records of the 11 domains tagged as IoCs showed that they resolved to 13 unique IP addresses after duplicates and the IoCs were removed.
Further investigations into the DNS records of the 13 additional IP addresses revealed that:
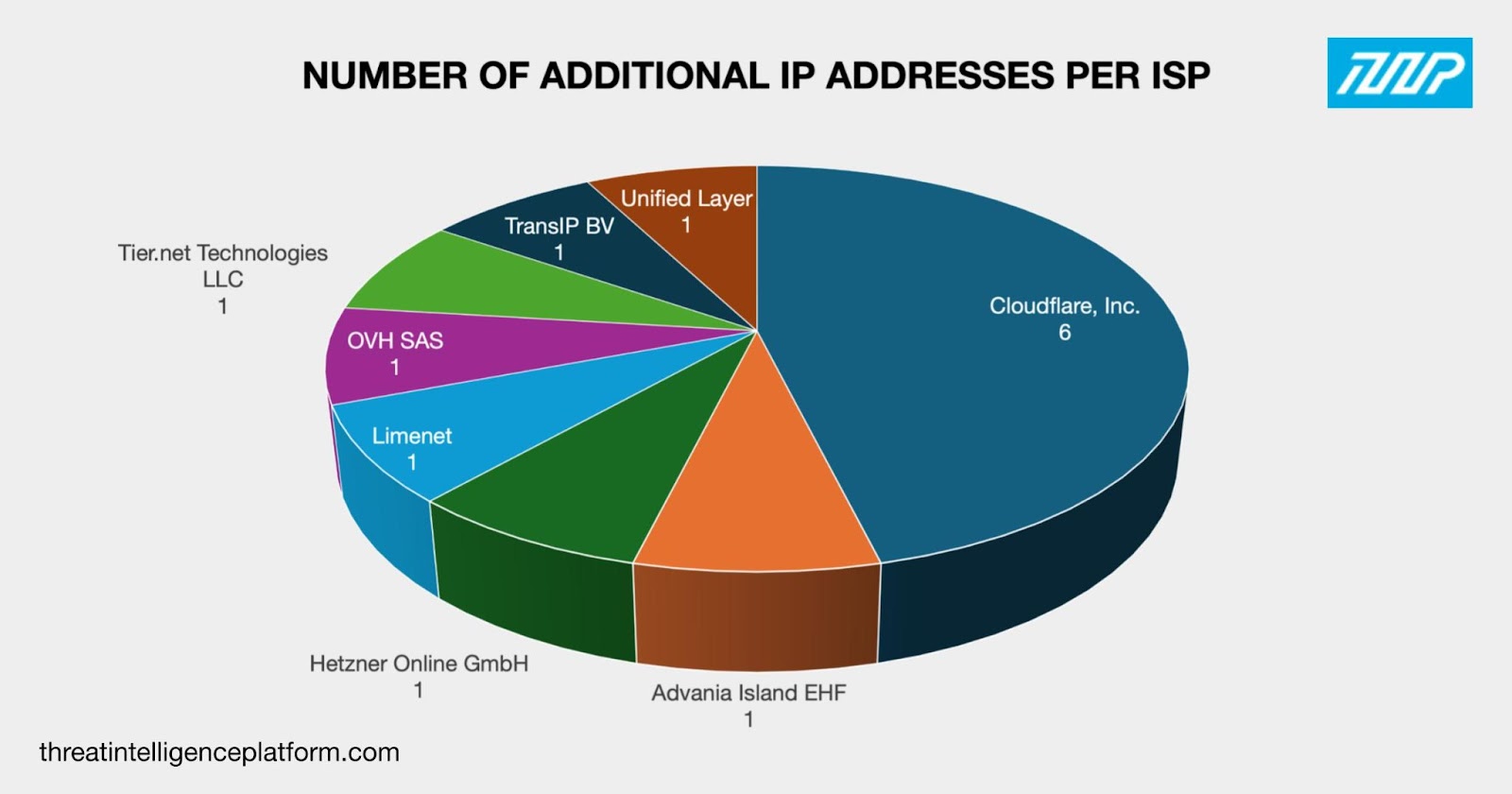
Cloudflare, Inc. led the list of ISPs, accounting for six IP addresses. Finally, one IP address each was administered by Advania Island EHF, Hetzner Online GmbH, Limenet, OVH SAS, Tier.net Technologies LLC, TransIP BV, and Unified Layer. One of the additional IP addresses had the same ISP as the two IP address IoCs.
We then scoured the DNS for domains starting with the same text strings found among the 11 domains classified as IoCs and found that six strings—hosting-hero., kunalicon., pputy., puttyy., puuty., and recovernj.—also appeared in 12 other domains after removing duplicates, the domain IoCs, and the email- and IP-connected domains.
The registrant email address, name, and organizations obtained from the current WHOIS records of four of the domains named as IoCs also appeared in the historical WHOIS records of 9,999 other domains, 273 of which were associated with various threats, such as phishing, attacks, malware, spamming, command and control (C&C), generic threats, and suspicious activities. Specifically:
The Malwarebytes report mentioned that the threat actors utilized fake PuTTY and FileZilla installers in their attacks. We searched for domains that could be typosquatting on the popularity of the two open-source applications, which led to the discovery of 292 domains. Note that we filtered out a good number of putty.-containing domains, particularly those that may be related to wall putty and similar products. Five of them turned out to be associated with threats. Specifically, four brand-containing domains were connected to malware, while one was related to generic threats.
Our deep dive into the most recent Nitrogen malware attack using 13 IoCs as starting points allowed us to uncover 10,499 artifacts comprising 18 email-connected domains, 13 additional IP addresses, 457 IP-connected domains, 12 string-connected domains, and 9,999 registrant-connected domains. We also discovered that 283 of the web properties, specifically 10 IP addresses and 273 registrant-connected domains were malicious.
Our investigation also led to the discovery of domains that could figure in other attacks banking on the popularity of PuTTY and FileZilla. We already found five that have already been weaponized.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byCSC

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byRadix

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byWhoisXML API
