

Following rumors last week on the leading candidate for ICANN's new CEO position, an official announcement has been released by ICANN confirming that the board may indeed announce its selection during its meeting in Sydney next week. more
 Former New York City Mayor Edward I. Koch announced Thursday he is supporting dotNYC LLC's bid to operate the .NYC web address. City Council Speaker Christine Quinn disclosed during her State of the City speech in February that the City Council and Office of the Mayor will pursue the .NYC top-level domain. The city last month completed a Request for Information about .NYC and is expected to endorse a company to run the .NYC address this summer. more
Former New York City Mayor Edward I. Koch announced Thursday he is supporting dotNYC LLC's bid to operate the .NYC web address. City Council Speaker Christine Quinn disclosed during her State of the City speech in February that the City Council and Office of the Mayor will pursue the .NYC top-level domain. The city last month completed a Request for Information about .NYC and is expected to endorse a company to run the .NYC address this summer. more
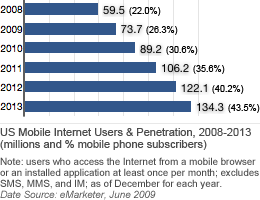 The total number of mobile internet users are expected to reach 134 million by 2013 as a result of increasing rise in smartphone popularity according to the research firm, eMerketer. Additionally Piper Jaffray, one of few organizations to project the extent of the growth, estimates that combined spending on consumer and business mobile applications will top $13 billion worldwide by 2012, a nearly fivefold increase over 2009," says eMarketer in a report released this week. more
The total number of mobile internet users are expected to reach 134 million by 2013 as a result of increasing rise in smartphone popularity according to the research firm, eMerketer. Additionally Piper Jaffray, one of few organizations to project the extent of the growth, estimates that combined spending on consumer and business mobile applications will top $13 billion worldwide by 2012, a nearly fivefold increase over 2009," says eMarketer in a report released this week. more
 Sources indicate former director of the US Homeland Security Department's National Cybersecurity Center (NCSC), Rod Beckstrom, will be replacing the current ICANN CEO, Paul Twomey, who announced his resignation earlier this year. Milton Mueller in a blog post on the IGP website writes: "This is still unconfirmed by ICANN but comes from well-informed sources. We also hear that David Eisner, the CEO of the Corporation for National and Community Service under G.W. Bush and former VP at AOL, was also in the running." Beckstrom recently made headlines for his sudden resignation from his post at NCSC, criticizing the lack of funding from the NSA and its move to try to "rule over" the NCSC. more
Sources indicate former director of the US Homeland Security Department's National Cybersecurity Center (NCSC), Rod Beckstrom, will be replacing the current ICANN CEO, Paul Twomey, who announced his resignation earlier this year. Milton Mueller in a blog post on the IGP website writes: "This is still unconfirmed by ICANN but comes from well-informed sources. We also hear that David Eisner, the CEO of the Corporation for National and Community Service under G.W. Bush and former VP at AOL, was also in the running." Beckstrom recently made headlines for his sudden resignation from his post at NCSC, criticizing the lack of funding from the NSA and its move to try to "rule over" the NCSC. more
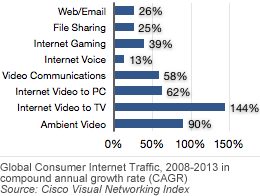 Annual global IP traffic will pass two-thirds of a zettabyte in four years according the Cisco's Visual Networking Index report. The economic downturn has only slightly tempered traffic growth and the global IP traffic is expected to quintuple from 2008 to 2013. Cisco predicts IP traffic to grow at a compound annual growth rate (CAGR) of 40%. more
Annual global IP traffic will pass two-thirds of a zettabyte in four years according the Cisco's Visual Networking Index report. The economic downturn has only slightly tempered traffic growth and the global IP traffic is expected to quintuple from 2008 to 2013. Cisco predicts IP traffic to grow at a compound annual growth rate (CAGR) of 40%. more
Source from Google have recently confirmed total number of YouTube video streams are above 1.2 billion per day worldwide according to Michael Arrington at TechCrunch. Previously reported numbers by comScore and other third party services appear to have been fairly under-estimated. more
According the the report, a survey of 1,000 consumers found that the majority believe the Internet will become full of pointless domain names (65% of those polled), messy and confusing (57%), too complex to navigate (46%) and out of control (41%). Two-thirds of the 100 UK businesses surveyed are still unaware that liberalization is happening, which is a concern, considering the opportunities and potential risks that it presents." more
In response to Canada's recent decision to keep a hands-off approach to distributed content over the Internet and through mobile devices, Jacob Glick, Google's Canada Policy Counsel has highly commended the decision. In a blog post today, Glick writes: "If you've ever wondered about the power and popularity of user-generated content in Canada, consider this: if all three Canadian television networks began broadcasting Canadian content 24 hours a day, seven days a week, YouTube would still have more Canadian content than those three networks combined." more
 According to the latest update from ICANN related to the introduction of new generic Top-Level Domains (gTLDs), Dr. Dennis Carlton has reiterated that the planned introduction of new gTLDs will not burden trademark owners with additional defensive registrations. Carlton writes: "I conclude that ICANN's proposed framework for introducing new gTLDs is likely to facilitate entry and create new competition to the major gTLDs such as .com, .net, and .org. Like other actions that remove artificial restrictions on entry, the likely effect of ICANN's proposal is to increase output, lower price and increase innovation. This conclusion is based on the fundamental principles that competition promotes consumer welfare and restrictions on entry impede competition." more
According to the latest update from ICANN related to the introduction of new generic Top-Level Domains (gTLDs), Dr. Dennis Carlton has reiterated that the planned introduction of new gTLDs will not burden trademark owners with additional defensive registrations. Carlton writes: "I conclude that ICANN's proposed framework for introducing new gTLDs is likely to facilitate entry and create new competition to the major gTLDs such as .com, .net, and .org. Like other actions that remove artificial restrictions on entry, the likely effect of ICANN's proposal is to increase output, lower price and increase innovation. This conclusion is based on the fundamental principles that competition promotes consumer welfare and restrictions on entry impede competition." more
The Electronic Frontier Foundation (EFF) has launched a new site to keep track of 'Terms of Service' for major websites such as Google, Facebook, eBay and others. The new website called TOSBack has been created to help users easily find privacy policies of various websites and to alert them when those policies are changed. "Some changes to terms of service are good for consumers, and some are bad," says EFF Senior Staff Attorney Fred von Lohmann. "But Internet users are increasingly trusting websites with everything from their photos to their 'friends lists' to their calendar -- and sometimes even their medical information. TOSBack will help consumers flag changes in the websites they use every day and trust with their personal information." more
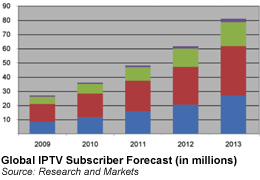 The number of global IPTV subscribers will grow from 26.7 million in 2009 to 81 million in 2013, a compound annual growth rate of 32%, according to the latest Research and Markets IPTV Global Forecast Report. Regarding service revenue, the Global IPTV market is $6.7 billion in 2009 and growing to $19.9 billion in 2013, a compound annual growth rate of 31%. By 2013, the report forecasts Europe and North America will generate a larger share of global revenue, due to very low ARPUs (average revenue per user) in China and India, the fastest growing (and ultimately, the biggest markets) in Asia. more
The number of global IPTV subscribers will grow from 26.7 million in 2009 to 81 million in 2013, a compound annual growth rate of 32%, according to the latest Research and Markets IPTV Global Forecast Report. Regarding service revenue, the Global IPTV market is $6.7 billion in 2009 and growing to $19.9 billion in 2013, a compound annual growth rate of 31%. By 2013, the report forecasts Europe and North America will generate a larger share of global revenue, due to very low ARPUs (average revenue per user) in China and India, the fastest growing (and ultimately, the biggest markets) in Asia. more
 While scanning its index, Google in the last two months reports to have found more than 4,000 different websites suspected of distributing malware by massively compromising popular websites. "Of these domains more than 1,400 were hosted in the .cn TLD. Several contained plays on the name of Google such as goooogleadsence.biz, etc.," says Google's security team member, Niels Provos, in a blog post today. more
While scanning its index, Google in the last two months reports to have found more than 4,000 different websites suspected of distributing malware by massively compromising popular websites. "Of these domains more than 1,400 were hosted in the .cn TLD. Several contained plays on the name of Google such as goooogleadsence.biz, etc.," says Google's security team member, Niels Provos, in a blog post today. more
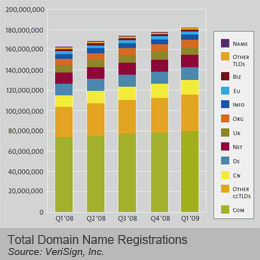 The total number of domain names have grown to 180 million world wide, according to the first quarter 2009 Domain Name Industry Brief published by VeriSign. The first quarter of 2009 reached a base of 183 million domain name registrations across all of the Top Level Domain Names (TLDs) -- a 3% increase over the fourth quarter of 2008 and a 12% increase over the same quarter from last year. Country Code TLDs (ccTLDs) rose to 74.1 million domain names during the first quarter, a four percent jump from the previous quarter and an 18 percent increase year over year. Gauged by total registrations, .com remains the most popular TLD category, followed by .cn (China), .de (Germany) and .net. This composition remains unchanged from Q4 2008. more
The total number of domain names have grown to 180 million world wide, according to the first quarter 2009 Domain Name Industry Brief published by VeriSign. The first quarter of 2009 reached a base of 183 million domain name registrations across all of the Top Level Domain Names (TLDs) -- a 3% increase over the fourth quarter of 2008 and a 12% increase over the same quarter from last year. Country Code TLDs (ccTLDs) rose to 74.1 million domain names during the first quarter, a four percent jump from the previous quarter and an 18 percent increase year over year. Gauged by total registrations, .com remains the most popular TLD category, followed by .cn (China), .de (Germany) and .net. This composition remains unchanged from Q4 2008. more
 Researchers at the University of California, Berkeley's School of Information have released a report raising concern over website monitoring practices which appear to be taking advantage of critical loopholes in privacy protection. According to the study, most popular websites in the United States "all share data with their corporate affiliates and allow third parties to collect information directly by using tracking beacons known as 'Web bugs' -- despite the sites' claims that they don't share user data with third parties." more
Researchers at the University of California, Berkeley's School of Information have released a report raising concern over website monitoring practices which appear to be taking advantage of critical loopholes in privacy protection. According to the study, most popular websites in the United States "all share data with their corporate affiliates and allow third parties to collect information directly by using tracking beacons known as 'Web bugs' -- despite the sites' claims that they don't share user data with third parties." more
Various sources are reporting that the Chinese authorities have blocked internet access to popular social networking and email sites such as Twitter, Flickr reviews, Bing, Live.com, Hotmail.com and several others. According to the Telegraph, "[T]he measures came as the authorities tried to close all avenues of dissent ahead of Thursday's anniversary, placing prominent critics under house arrest and banning newspaper from making any mention of the pro-democracy protests." This latest co-ordinated internet 'blackout' was initiated at 5 P.M. local time as various websites suddenly became unavailable to Chinese internet users. more
Sponsored byIPv4.Global

Sponsored byRadix

Sponsored byVerisign

Sponsored byCSC

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byWhoisXML API
