

 In an article titled "A Cyber-Attack on an American City", Bruce Perens writes: "Just after midnight on Thursday, April 9, unidentified attackers climbed down four manholes serving the Northern California city of Morgan Hill and cut eight fiber cables in what appears to have been an organized attack on the electronic infrastructure of an American city. Its implications, though startling, have gone almost un-reported. That attack demonstrated a severe fault in American infrastructure: its centralization. The city of Morgan Hill and parts of three counties lost 911 service, cellular mobile telephone communications, land-line telephone, DSL internet and private networks, central station fire and burglar alarms, ATMs, credit card terminals, and monitoring of critical utilities..." more
In an article titled "A Cyber-Attack on an American City", Bruce Perens writes: "Just after midnight on Thursday, April 9, unidentified attackers climbed down four manholes serving the Northern California city of Morgan Hill and cut eight fiber cables in what appears to have been an organized attack on the electronic infrastructure of an American city. Its implications, though startling, have gone almost un-reported. That attack demonstrated a severe fault in American infrastructure: its centralization. The city of Morgan Hill and parts of three counties lost 911 service, cellular mobile telephone communications, land-line telephone, DSL internet and private networks, central station fire and burglar alarms, ATMs, credit card terminals, and monitoring of critical utilities..." more
 Brandon Bailey reporting on Mercury News: "In a surprising twist, Sun Microsystems announced this morning that it will be acquired by Oracle in a deal worth roughly $7.4 billion, or $5.6 billion net after accounting for Sun's cash and debt. The news comes just a few weeks after earlier talks for IBM to buy Sun [link] collapsed..." more
Brandon Bailey reporting on Mercury News: "In a surprising twist, Sun Microsystems announced this morning that it will be acquired by Oracle in a deal worth roughly $7.4 billion, or $5.6 billion net after accounting for Sun's cash and debt. The news comes just a few weeks after earlier talks for IBM to buy Sun [link] collapsed..." more
A Swedish court on Friday found all four defendants guilty in a copyright test case involving one of the world's biggest free file-sharing websites. "The Stockholm disctrict court has today found guilty the four individuals that were charged with accessory to breaching copyright laws," the court said in a statement. "The court has sentenced each of them to one year in prison." more
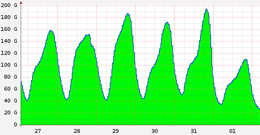 April 1st was the start of a new anti-piracy law in Sweden where, according to traffic data, an immediate and significant drop (over 30%) occurred in the nation's overall Internet traffic. Reported today by Royal Pingdom: "The combined traffic passing through Sweden's Internet Exchange Points usually peaks around 160 Gbit/s, but on Wednesday it peaked at around 110 Gbit/s. That's a huge drop in traffic, and is presumably a direct result of less file sharing taking place. ... Another interesting observation is that there was more traffic than usual during the last days before the law took effect. Were people hoarding films and music? On Tuesday (the day before the law went live) traffic peaked at nearly 200 GBit/s, roughly 25% above normal levels." more
April 1st was the start of a new anti-piracy law in Sweden where, according to traffic data, an immediate and significant drop (over 30%) occurred in the nation's overall Internet traffic. Reported today by Royal Pingdom: "The combined traffic passing through Sweden's Internet Exchange Points usually peaks around 160 Gbit/s, but on Wednesday it peaked at around 110 Gbit/s. That's a huge drop in traffic, and is presumably a direct result of less file sharing taking place. ... Another interesting observation is that there was more traffic than usual during the last days before the law took effect. Were people hoarding films and music? On Tuesday (the day before the law went live) traffic peaked at nearly 200 GBit/s, roughly 25% above normal levels." more
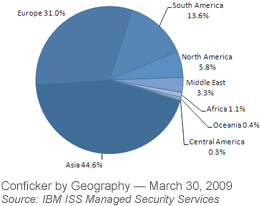 Amidst hype and anticipation of the Conficker worm which is expected to become active in millions of Windows system within the next few hours, IBM Internet Security Systems team reports they have been able to locate infected systems across the world by reverse-engineering the communications mechanisms. Holly Stewart, X-Force Product Manager at IBM Internet Security Systems, writes: "... the details are still unfolding, but we can tell you from a high level where most infections are as of today. Asia tops the charts so far. By this morning, it represented nearly 45% of all of the infections from our view. Europe was second at 31%. The rest of the geographies held a much smaller percentage overall." more
Amidst hype and anticipation of the Conficker worm which is expected to become active in millions of Windows system within the next few hours, IBM Internet Security Systems team reports they have been able to locate infected systems across the world by reverse-engineering the communications mechanisms. Holly Stewart, X-Force Product Manager at IBM Internet Security Systems, writes: "... the details are still unfolding, but we can tell you from a high level where most infections are as of today. Asia tops the charts so far. By this morning, it represented nearly 45% of all of the infections from our view. Europe was second at 31%. The rest of the geographies held a much smaller percentage overall." more
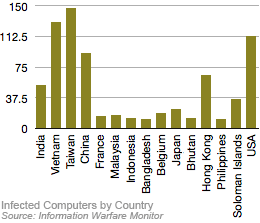 A report released over the weekend by Information Warfare Monitor along with an exclusive story by the New York Times, revealed a 10-month investigation of a suspected cyber espionage network (dubbed GhostNet) of over 1,295 infected computers in 103 countries. 30% of the infected computers are labeled as high-value targets, including ministries of foreign affairs, embassies, international organizations, news media, and NGOs. Greg Walton, editor of Information Warfare Monitor and a member of the Toronto academic research team that is reporting on the spying operation, writes... more
A report released over the weekend by Information Warfare Monitor along with an exclusive story by the New York Times, revealed a 10-month investigation of a suspected cyber espionage network (dubbed GhostNet) of over 1,295 infected computers in 103 countries. 30% of the infected computers are labeled as high-value targets, including ministries of foreign affairs, embassies, international organizations, news media, and NGOs. Greg Walton, editor of Information Warfare Monitor and a member of the Toronto academic research team that is reporting on the spying operation, writes... more
Google will be hosting a discussion on the future of cloud computing and technology policy tomorrow, March 20, in Washington, D.C. Participants include Jeffrey Rayport, principal at the Marketspace consulting group and a leading experts on digital strategy and marketing, and Andrew Heyward, former President of CBS News, who will be presenting the findings of their new study. "They will assess the possibilities, risks and returns of cloud computing; the next steps in moving forward; and potential implications for technology policy," says Dorothy Chou, Google's Global Communications and Public Affairs. Those unable to attend are invited to submit questions in advance via Google Moderator. more
The Technology Policy Institute (TPI), an IT and communications policy think tank, has just released a paper proposing that "ICANN's governance structure should be dramatically reformed to make it more accountable before the current tie with the U.S. Department of Commerce is allowed to expire." The paper titled "ICANN At a Crossroads: a Proposal for Better Governance and Performance" is written by Thomas M. Lenard, President and Senior Fellow at TPI, along with Lawrence J. White, Professor of Economics at the NYU Stern School of Business. The 52-page study also asserts that ICANN must have a clear focus on encouraging competition with minimal role as a regulator with respect to the creation of new generic Top-Level Domains (gTLDs). more
 StopBadware.org and Consumer Reports WebWatch have announced today the full launch of BadwareBusters.org, a new online community for people looking for help preventing and countering viruses, spyware, and other "badware" on their computers and websites. Maxim Weinstein, manager of StopBadware.org at Harvard University's Berkman Center for Internet & Society, says the site is not only a useful destination, but also a piece of a bigger puzzle. "BadwareBusters.org is part of StopBadware's strategy to bring together the people, the organizations, and the data that allow us to fight back against the spread of badware," Weinstein said. "The collective wisdom of the BadwareBusters community will inform not only individuals, but the entire technology industry." more
StopBadware.org and Consumer Reports WebWatch have announced today the full launch of BadwareBusters.org, a new online community for people looking for help preventing and countering viruses, spyware, and other "badware" on their computers and websites. Maxim Weinstein, manager of StopBadware.org at Harvard University's Berkman Center for Internet & Society, says the site is not only a useful destination, but also a piece of a bigger puzzle. "BadwareBusters.org is part of StopBadware's strategy to bring together the people, the organizations, and the data that allow us to fight back against the spread of badware," Weinstein said. "The collective wisdom of the BadwareBusters community will inform not only individuals, but the entire technology industry." more
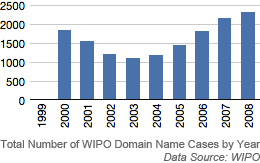 According to latest reports from the World Intellectual Property Organisation (WIPO), allegations of cybersquatting by trademark holders continued to rise in 2008, with a record 2,329 complaints filed under the Uniform Domain Name Dispute Resolution Policy (UDRP). This represented an 8% increase over 2007 in the number of generic and country code Top-Level Domain (gTLDs and ccTLDs) disputes handled and brings the total number of WIPO cases filed under the UDRP since it was launched ten years ago to over 14,000. To improve efficiency and respond to growing demand, WIPO has proposed an "eUDRP Initiative" to render the UDRP paperless... more
According to latest reports from the World Intellectual Property Organisation (WIPO), allegations of cybersquatting by trademark holders continued to rise in 2008, with a record 2,329 complaints filed under the Uniform Domain Name Dispute Resolution Policy (UDRP). This represented an 8% increase over 2007 in the number of generic and country code Top-Level Domain (gTLDs and ccTLDs) disputes handled and brings the total number of WIPO cases filed under the UDRP since it was launched ten years ago to over 14,000. To improve efficiency and respond to growing demand, WIPO has proposed an "eUDRP Initiative" to render the UDRP paperless... more
 Computer scientists, engineers and journalists gathered today on the CERN particle physics lab in the suburbs of Geneva, Switzerland, to pay homage to the a 1989 proposal by Tim Berners-Lee that would later come to be the blueprint for the World Wide Web. In March 1989, Tim Berners-Lee submitted a proposal for an information management system to his boss, Mike Sendall. 'Vague, but exciting', were the words that Sendall wrote on the proposal, allowing Berners-Lee to continue... more
Computer scientists, engineers and journalists gathered today on the CERN particle physics lab in the suburbs of Geneva, Switzerland, to pay homage to the a 1989 proposal by Tim Berners-Lee that would later come to be the blueprint for the World Wide Web. In March 1989, Tim Berners-Lee submitted a proposal for an information management system to his boss, Mike Sendall. 'Vague, but exciting', were the words that Sendall wrote on the proposal, allowing Berners-Lee to continue... more
 Nominet, the national registry for .uk domain names, has announced that ENUM, a registry service combining UK telephone numbers and the Domain Name System (DNS) for VoIP calls, is live. ENUM, also known as Telephone Number Mapping, is expected to allow companies and their customers and suppliers to make free or cheaper calls. In addition to the cost savings, other value-added features that ENUM is expected to provide for corporate communications include 'follow me' type function that will allow an individual to choose how (voice, fax, mobile, email, text messaging, location-based services and websites), and when they would like to be contacted throughout the day. more
Nominet, the national registry for .uk domain names, has announced that ENUM, a registry service combining UK telephone numbers and the Domain Name System (DNS) for VoIP calls, is live. ENUM, also known as Telephone Number Mapping, is expected to allow companies and their customers and suppliers to make free or cheaper calls. In addition to the cost savings, other value-added features that ENUM is expected to provide for corporate communications include 'follow me' type function that will allow an individual to choose how (voice, fax, mobile, email, text messaging, location-based services and websites), and when they would like to be contacted throughout the day. more
The National Arbitration Forum today announced that a total of 1,770 cases were filed in its domain name dispute resolution program in 2008. The National Arbitration Forum, approved by ICANN, provides domain name dispute resolution services under policies like the Uniform Domain Name Dispute Resolution Policy (UDRP). Nearly all 1,770 cases filed (98%) in 2008 involved UDRP domain names, like .com and .org and the rest involved usDRP domain names with the .us extension, according to the announcement... more
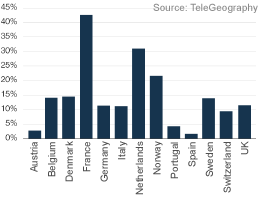 According to a new study, VoIP services are having a significant impact on the fixed line market in Europe. By mid-2008, just under 30 million consumer VoIP lines were in service in Western Europe, up from 20 million only a year earlier. TeleGeography, a research division of PriMetrica, estimates that the number of VoIP lines in Europe topped 35 million at end-2008... more
According to a new study, VoIP services are having a significant impact on the fixed line market in Europe. By mid-2008, just under 30 million consumer VoIP lines were in service in Western Europe, up from 20 million only a year earlier. TeleGeography, a research division of PriMetrica, estimates that the number of VoIP lines in Europe topped 35 million at end-2008... more
 The former US vice president, Al Gore, is backing the creation of a new green .eco domain name. Dot Eco LLC, the applicant for the new .eco Top-Level Domain (TLD), announced during the ICANN meetings in Mexico City that it has entered into an integrated partnership with former Vice President Al Gore and his philanthropy, the Alliance for Climate Protection, to secure and promote the .eco TLD. "We fully support Dot Eco LLC in its efforts to secure the .eco top level domain through the ICANN application process and look forward to working with Dot Eco LLC to promote .eco. This is a truly exciting opportunity for the environmental movement and for the internet as a whole," said Al Gore. more
The former US vice president, Al Gore, is backing the creation of a new green .eco domain name. Dot Eco LLC, the applicant for the new .eco Top-Level Domain (TLD), announced during the ICANN meetings in Mexico City that it has entered into an integrated partnership with former Vice President Al Gore and his philanthropy, the Alliance for Climate Protection, to secure and promote the .eco TLD. "We fully support Dot Eco LLC in its efforts to secure the .eco top level domain through the ICANN application process and look forward to working with Dot Eco LLC to promote .eco. This is a truly exciting opportunity for the environmental movement and for the internet as a whole," said Al Gore. more
Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byRadix

Sponsored byCSC

Sponsored byWhoisXML API
