

Pew Internet reporting on the 10th anniversary of the Napster's launch: "As researchers look back on the first decade of the 21st Century, many will no doubt point to the formative impact of file-sharing and peer-to-peer exchange of music on the internet. Distributed networks of socially-driven music sharing helped lay the foundation for mainstream engagement with participatory media applications. Napster and other peer-to-peer services "schooled" users in the social practice of downloading, uploading, and sharing digital content, which, in turn, has contributed to increased demand for broadband, greater processing power, and mobile media devices." more
In a blog post by Google's Sitaram Iyer, Staff Software Engineer, and Matt Cutts, Principal Engineer, a "secret project" has been revealed in an effort where the company is aiming to enhance various key aspects of its web search technology including indexing speed, accuracy, and comprehensiveness. The company so far has released the new engine "under the hood," for testing and feedback only and says most users will not notice a difference in search results. more
A recent survey of US companies conducted by Proofpoint has found companies increasingly concerned over data leaks via emplyee misuse of email, blogs, social networks, multimedia channels and text messages. From the report: "[A]s more US companies reported their business was impacted by the exposure of sensitive or embarrassing information (34 percent, up from 23 percent in 2008), an increasing number say they employ staff to read or otherwise analyze the contents of outbound email (38 percent, up from 29 percent in 2008). The pain of data leakage has become so acute in 2009 that more US companies report they employ staff whose primary or exclusive job is to monitor the content of outbound email (33 percent, up from 15 percent in 2008)." more
Internet Systems Consortium (ISC) has announced that it is working with Afilias and Neustar, Inc. in the effort to support ISC's DNSSEC Look-aside Validation (DLV) registry by providing secondary DNS service for the DLV zone. DLV is a mechanism that provides many of the benefits of DNSSEC (short for DNS Security Extensions), enabling domain holders to secure their domain information today in advance of broader DNSSEC deployment and adoption. "Adding Afilias and Neustar as secondary DNS providers for the DLV zone demonstrates our collective understanding that DLV is a vitally important production service bigger than any single provider in the same way that there are 13 root server operators, not just one." more
US House officials have confirmed hackers breaching several websites belonging to House of Representatives members in the past week. Portions of the websites were replaced by digital graffiti which began earlier this month, according to zone-h. Brian Krebs of the Washington Post reports: "Rep. Spencer Bachus has sent a letter to the House's chief administrative officer, requesting more information about the attacks. Bachus cites information provided to him by Gary Warner, director of research in computer forensics at the University of Alabama at Birmingham. Warner suggested that the break-ins at the House sites were caused not by password guessing [as reported initially], but by 'SQL injection,' an attack that exploits security weaknesses in Web server configurations." more
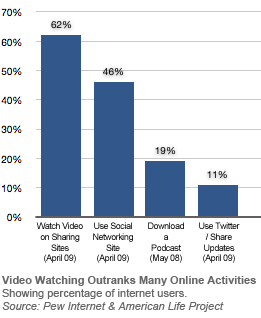 According to a study by Pew Internet, nine in ten (89%) of young adults aged 18-29 are now watching videos online in a regular basis. Additionally, the study indicates that the share of online adults who watch videos on sites such as YouTube and other video-sharing sites has nearly doubled since 2006. "Fully 62% of adult internet users have watched a video on these sites, up from just 33% who reported this in December 2006," according to the report. more
According to a study by Pew Internet, nine in ten (89%) of young adults aged 18-29 are now watching videos online in a regular basis. Additionally, the study indicates that the share of online adults who watch videos on sites such as YouTube and other video-sharing sites has nearly doubled since 2006. "Fully 62% of adult internet users have watched a video on these sites, up from just 33% who reported this in December 2006," according to the report. more
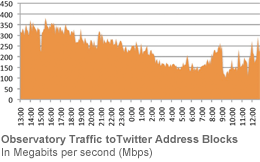 The Twitter micro-blogging service was knocked offline this morning for several hours as a result of a denial of service attack (DDoS). Twitter has confirmed and reported the attack in a post on its official blog earlier today: "We are defending against this [DDos] attack now and will continue to update our status blog as we continue to defend and later investigate." The company later reported that the service as been resumed but they are still continuing to defend against and recover from this attack. No further updates have been provided yet. more
The Twitter micro-blogging service was knocked offline this morning for several hours as a result of a denial of service attack (DDoS). Twitter has confirmed and reported the attack in a post on its official blog earlier today: "We are defending against this [DDos] attack now and will continue to update our status blog as we continue to defend and later investigate." The company later reported that the service as been resumed but they are still continuing to defend against and recover from this attack. No further updates have been provided yet. more
Philip Corwin of the Internet Commerce Associations reports: "In a stunning rebuke of ICANN's assertion that it had achieved sufficient accountability and professional stature to justify termination of its unique relationship with the U.S. government, the Chairman of the House Committee on Energy and Commerce as well as the Chairman of its Internet Subcommittee, along with eight other Committee members, dispatched a joint letter on August 4th to Commerce Secretary Gary Locke urging that the relationship between ICANN and the U.S. be made permanent and strengthened." more
A man from the northern New Jersey area was charged and arrested for stealing a domain name belonging to the owners of P2P.com. According to reports, he allegedly transferred the ownership of the domain name to himself and succeeded in reselling it on eBay to a professional basketball player Mark Madsen of the Los Angeles Clippers. more
Messaging Anti-Abuse Working Group (MAAWG) has issued the first best practices aimed at helping the global ISP industry work more closely with consumers to recognize and remove bot infections on end-users' machines. The paper outlines a three-step approach with recommendations for detecting bots, notifying users that their computers have been compromised, and guiding them in removing the malware. more
A team of developers including .SE (The Internet Infrastructure Foundation), LNetLabs, Nominet, Kirei, SURFnet, SIDN and John Dickinson have come together to create open source software, called OpenDNSSEC, to make it easier to deploy DNSSEC. Patrik Wallström, responsible for DNSSEC at .SE comments: "In order to spread the use of DNSSEC to an increased number of domain names, the management surrounding this technology must be simplified. Together with a number of collaborators, we're developing OpenDNSSEC. Leveraging our deployment experience, we will produce a well-packaged, easy-to-use and flexible DNSSEC tool that eliminates all manual procedures. Those in charge of name servers no longer need detailed knowledge about the protocol in order to use it." more
A recent survey of security professionals by RSA Conference with regards to critical security threats and infrastructure issues currently faced, revealed budgetary constrains as the top challenge currently faced. According to reports, the study suggests that even though practitioners are most concerned about email phishing and securing mobile devices, technologies addressing these needs are at risk of being cut from IT budgets. 72% percent of respondents indicated a rise in email-borne malware and phishing attempts since Fall 2008, with 57% stating they have seen an increase in Web-borne malware. Concerns about zero-day attacks and rogue employees as a result of layoffs were cited by 28% and 26% of survey respondents, respectively. more
A research paper commissioned by the International Commission on Nuclear Non-proliferation and Disarmament (ICNND) suggests that nuclear command and control systems are vulnerable to cyber terrorism. "Despite claims that nuclear launch orders can only come from the highest authorities, numerous examples point towards an ability to sidestep the chain of command and insert orders at lower levels," says the report. more
 The IPv6 Act Now website, aimed at encouraging the adoption of IPv6, has featured a video today on Google's implementation of IPv6, which resulted in the launch of ipv6.google.com. In this video, Lorenzo Colitti, network engineer at Google, explains the planning, deployment, and future plans for making Google services available over IPv6. The best way to proceed with an IPv6 deployment, Colitti says is "to run everything on the same infrastructure." more
The IPv6 Act Now website, aimed at encouraging the adoption of IPv6, has featured a video today on Google's implementation of IPv6, which resulted in the launch of ipv6.google.com. In this video, Lorenzo Colitti, network engineer at Google, explains the planning, deployment, and future plans for making Google services available over IPv6. The best way to proceed with an IPv6 deployment, Colitti says is "to run everything on the same infrastructure." more
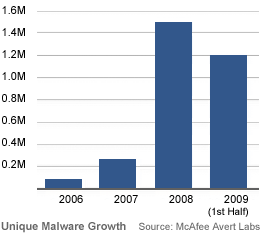 Security researches report seeing as much unique malware in the first half of 2009 as seen in all of 2008. "This is quite something when you consider that in 2008 we saw the greatest ever growth in malware," says David Marcus of McAfee Avert Labs. More specifically, Marcus in a blog post writes that the numbers add up to an average of 200,000 unique pieces malware monthly or more than 6,000 a day. "Bear in mind these are malware we consider unique (something we had to write a driver for) and does not count all the other malware we detect generically or heuristically... When you add in the generic and heuristic detections the number becomes truly mind boggling," writes Marucs. more
Security researches report seeing as much unique malware in the first half of 2009 as seen in all of 2008. "This is quite something when you consider that in 2008 we saw the greatest ever growth in malware," says David Marcus of McAfee Avert Labs. More specifically, Marcus in a blog post writes that the numbers add up to an average of 200,000 unique pieces malware monthly or more than 6,000 a day. "Bear in mind these are malware we consider unique (something we had to write a driver for) and does not count all the other malware we detect generically or heuristically... When you add in the generic and heuristic detections the number becomes truly mind boggling," writes Marucs. more
Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byRadix

Sponsored byVerisign

Sponsored byCSC

Sponsored byIPv4.Global

Sponsored byWhoisXML API
