

|
||
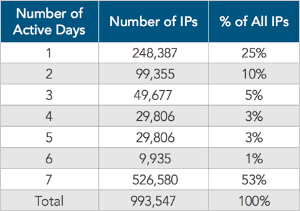 Nearly 1 million IP addresses participated in the attack campaign against a financial company. Source: AkamaiAccording to a recent report by Akamai, an analysis of massive Account Takeover (ATO) attack campaigns targeting two of its customers, revealed 1,127,818 different IPs were involved in the attacks. These IPs performed 744,361,093 login attempts and checked 220,758,340 distinct email addresses. In other words, “ATO campaigns are massively distributed and extremely persistent.”
Nearly 1 million IP addresses participated in the attack campaign against a financial company. Source: AkamaiAccording to a recent report by Akamai, an analysis of massive Account Takeover (ATO) attack campaigns targeting two of its customers, revealed 1,127,818 different IPs were involved in the attacks. These IPs performed 744,361,093 login attempts and checked 220,758,340 distinct email addresses. In other words, “ATO campaigns are massively distributed and extremely persistent.”
“In the repeated attacks against a customer in the financial services industry, 999,980 IPs were involved in the attacks against the customer’s login page. One campaign was responsible for more than 90% of the total attack volume.” Closer look at this particular attack revealed usage of 993,547 distinct IPs checking 427,444,261 email accounts at a steady attack rate as 75% of attackers participated for multiple days.
Sponsored byVerisign

Sponsored byWhoisXML API

Sponsored byCSC

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byIPv4.Global

Sponsored byRadix
