


|
||
|
||
Organizations get bombarded with countless attacks from every direction, including via their supply chain. FortifyData’s recent record of the top third-party data breaches in 2023 brings to light how multidirectional threat sources can be.
In one of the data breaches on the list, AT&T disclosed in March 2023 that threat actors accessed the information of approximately 9 million wireless accounts through the telecommunication company’s marketing vendor. Building on this threat source, WhoisXML API researchers looked into domains impersonating marketing service providers that can serve as possible vehicles of third-party threats. Our key findings include:
The domains found in the study can be used to target employees and partners of the imitated marketing companies, creating a domino effect that can affect their clients, as in AT&T’s case.
A sample of the additional artifacts obtained from our analysis is available for download from our website.
Our research focused on 10 famous marketing service providers. We looked up their company names on Domains & Subdomains Discovery. In one case, we added crm as a search term to avoid false positives. The table below shows the marketing vendors, the search strings used, and the number of domains found as of 5 May 2023.
| Marketing Vendor | Official Domain | Search String Used | Number of Domains Found as of 5 May 2023 | Sample of Discovered Domain |
|---|---|---|---|---|
| ActiveCampaign | activecampaign[.]com | Containsactivecampaign | 450 | 101activecampaign[.]xyz |
| Aweber | aweber[.]com | Starts withaweber | 389 | aweber[.]click |
| Brevo (formerly Sendinblue) | brevo[.]com | Starts withbrevo | 512 | brevo[.]marketing |
| HubSpot | hubspot[.]com | Containshubspot | 3,491 | hubspots[.]cloud |
| Klaviyo | klaviyo[.]com | Containsklaviyo | 330 | trkklaviyomail[.]com |
| Mailchimp | mailchimp[.]com | Containsmailchimp | 1,352 | us19-mailchimp[.]com |
| Marketing 360 | marketing360[.]com | Containsmarketing360 | 1,086 | appsmarketing360[.]com |
| Omnisend | omnisend[.]com | Containsomnisend | 106 | app-omnisend[.]top |
| Pardot | go[.]pardot[.]com | Containspardot | 558 | xpardotop[.]tk |
| Zoho CRM | zoho[.]com | Containszohoandcrm | 190 | zohocrm[.]org |
We found a total of 8,464 domains containing the marketing companies’ names. About 4.4% of them were registered this year.
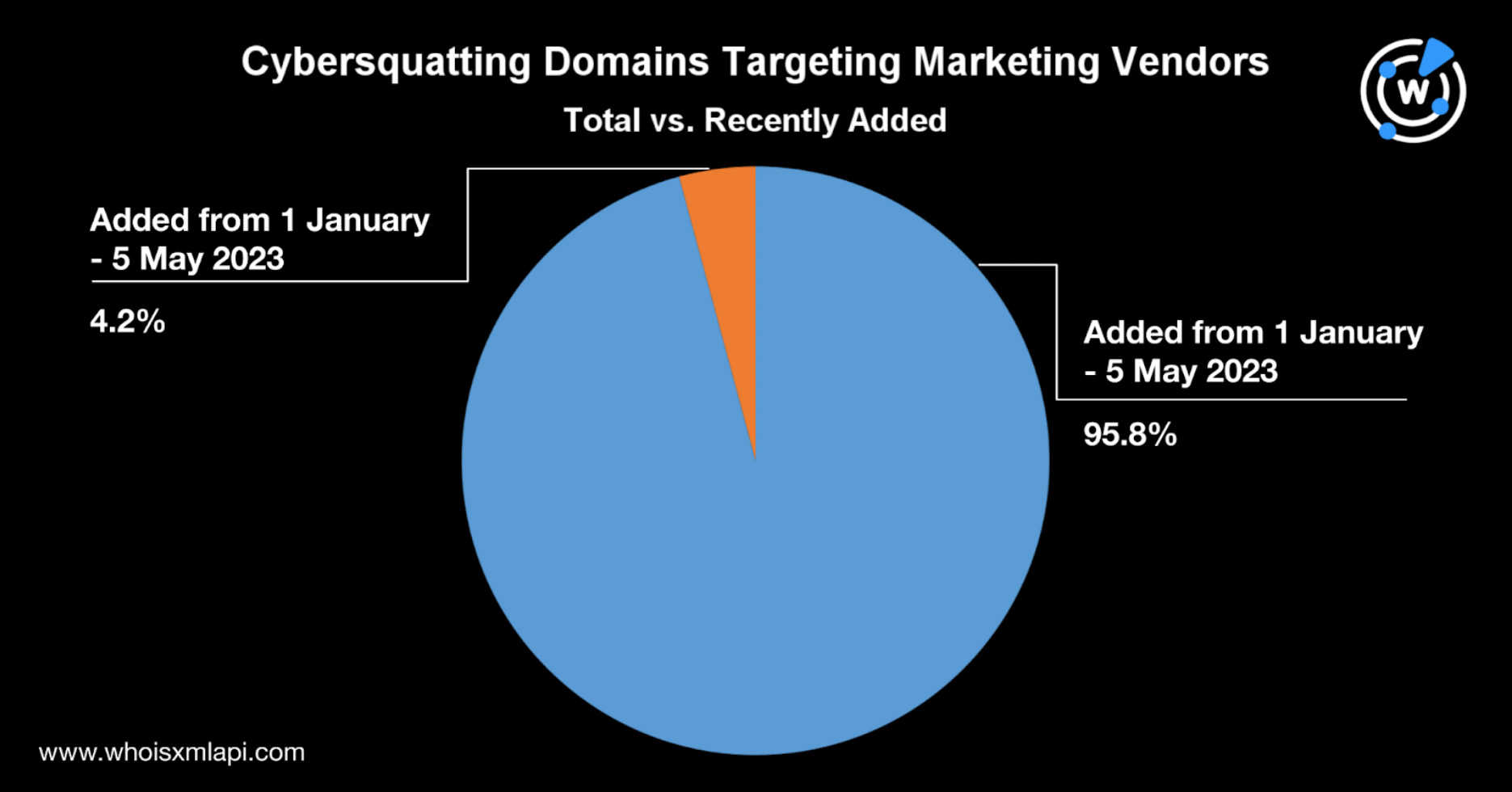
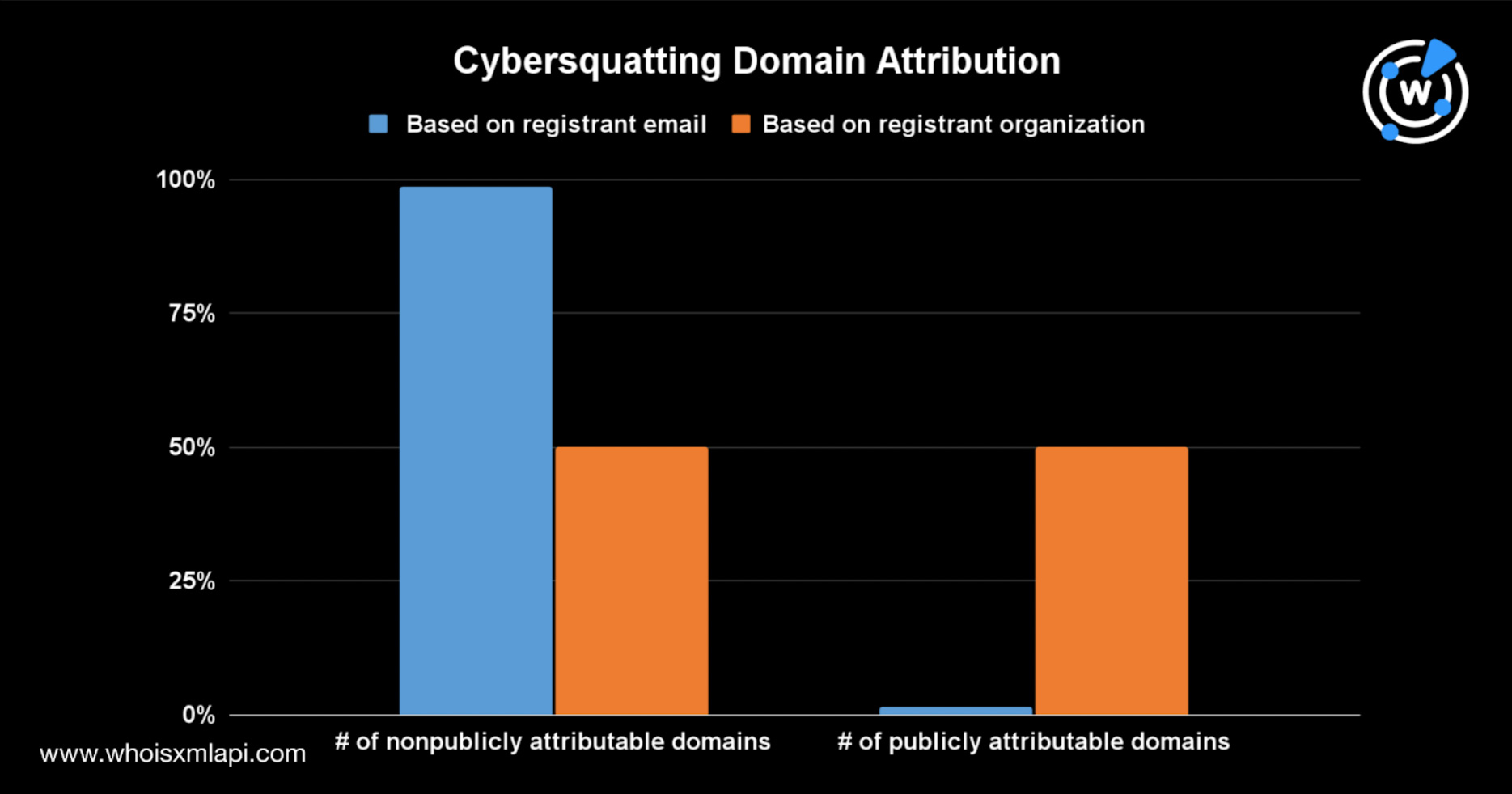
We then obtained the current WHOIS records of the cybersquatting domains using Bulk WHOIS Lookup to determine their ownership. Based on the registrant organization field, 50% of the cybersquatting domains could be publicly attributed to the marketing vendors. The legitimate companies may own or have some control over the domains.
However, when we based the attribution analysis on the more reliable registrant email field, we found that only 1% could be publicly attributed to the imitated companies. The rest either had redacted WHOIS records or were maintained by other entities.
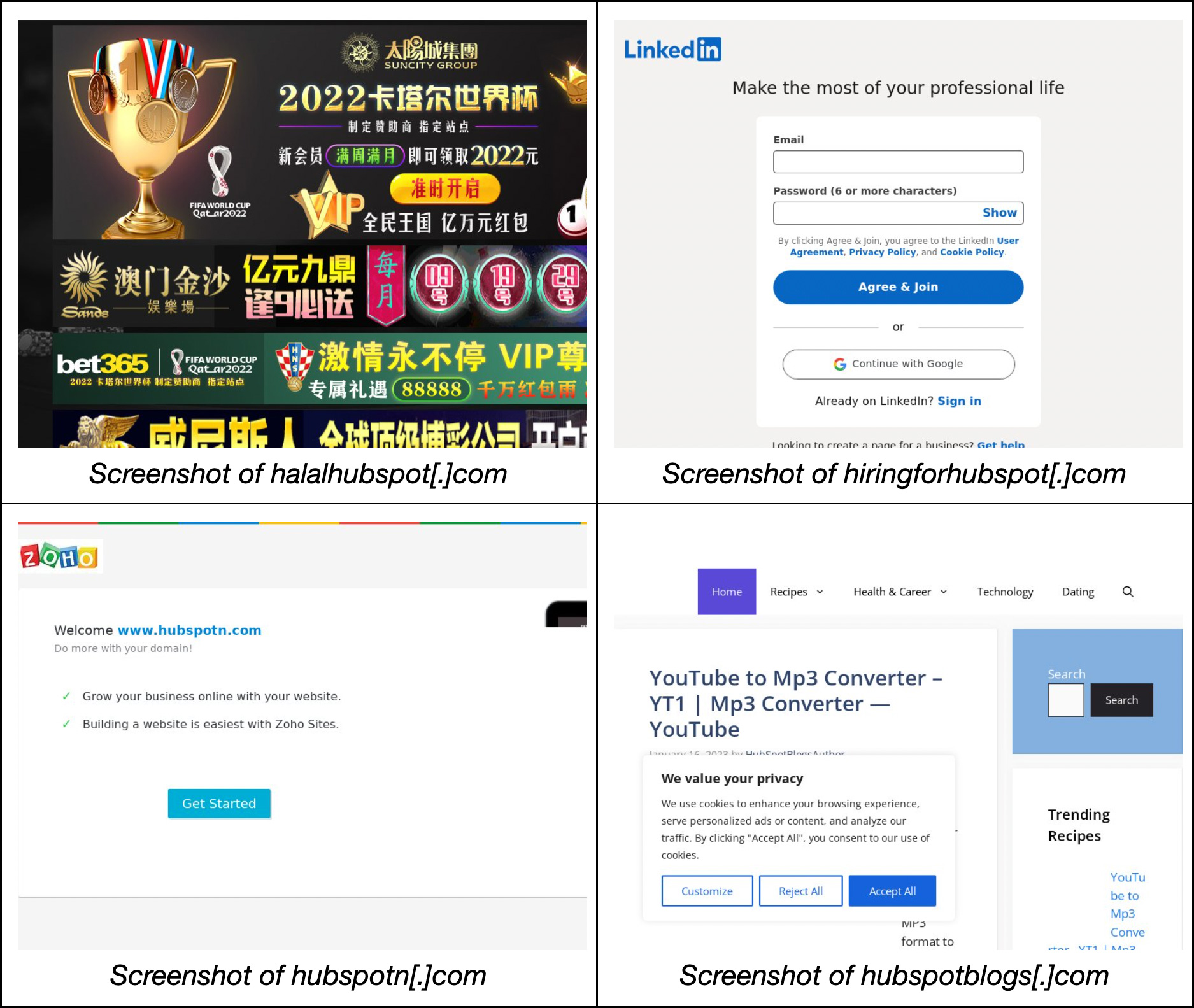
About 45% of the cybersquatting domains actively resolved to IP hosts. Most were parked, while several hosted or redirected to websites with questionable content. Below are some examples of domains whose content was not directly related to the imitated companies.
A bulk malware check on the domains revealed that dozens of them were malicious, with some still hosting active content, as shown below.
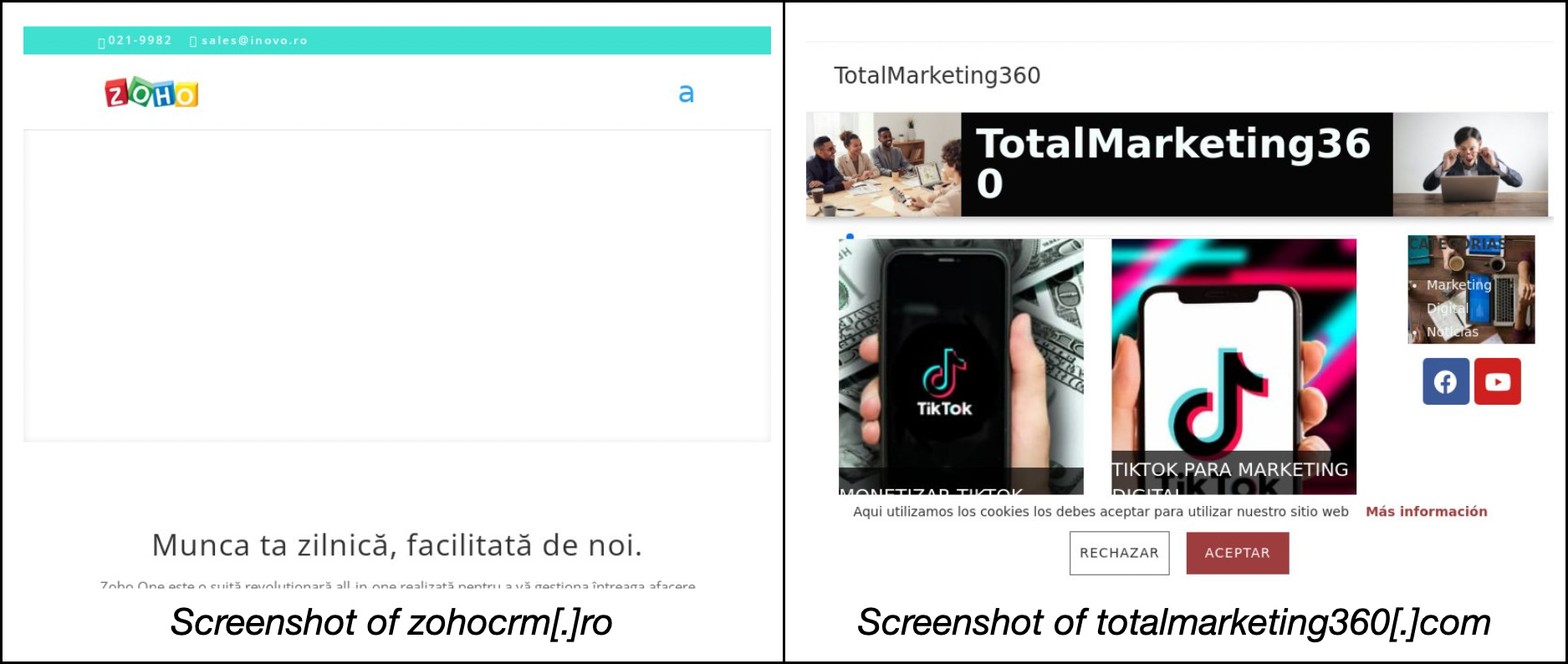
Note the similarity between the content of zohocrm[.]ro and hubspotn[.]com from the previous section.
Several malicious cybersquatting domains hinted at a possible campaign tactic where threat actors use domains starting with the string us followed by a number and a dash, such as us1-mailchimp[.]com and us2mailchimp[.]com.
Expanding our threat discovery to include this pattern, we turned to Domains & Subdomains Discovery again and searched for domains that began with the same suspicious strings. We found 575 such web properties added from 1 January to 5 May 2023. The table below shows the breakdown per search string.
| Beginning Text String | Number of Domains Added from 1 January to 7 May 2023 |
|---|---|
| us1 | 97 |
| us2 | 101 |
| us3 | 63 |
| us4 | 72 |
| us5 | 40 |
| us6 | 54 |
| us7 | 44 |
| us8 | 56 |
| us9 | 48 |
We ran a bulk malware check on these properties and found that 4% of the domains were malicious.
The suspicious and malicious domains found in this study can help organizations avoid third-party threats riding on cybersquatting domains. A deeper look into the usage of these properties led us to a suspicious domain pattern, which uncovered hundreds of malicious us-containing domains.
The findings of this study further highlight the multidimensional nature of the current threat landscape. Threat actors could use various threat vectors from different sources, making proactive and extensive threat discovery essential.
If you wish to perform a similar investigation or get access to the full data behind this research, please don’t hesitate to contact us.
Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byRadix

Sponsored byWhoisXML API

Sponsored byCSC

Sponsored byVerisign

Sponsored byIPv4.Global
