

|
||
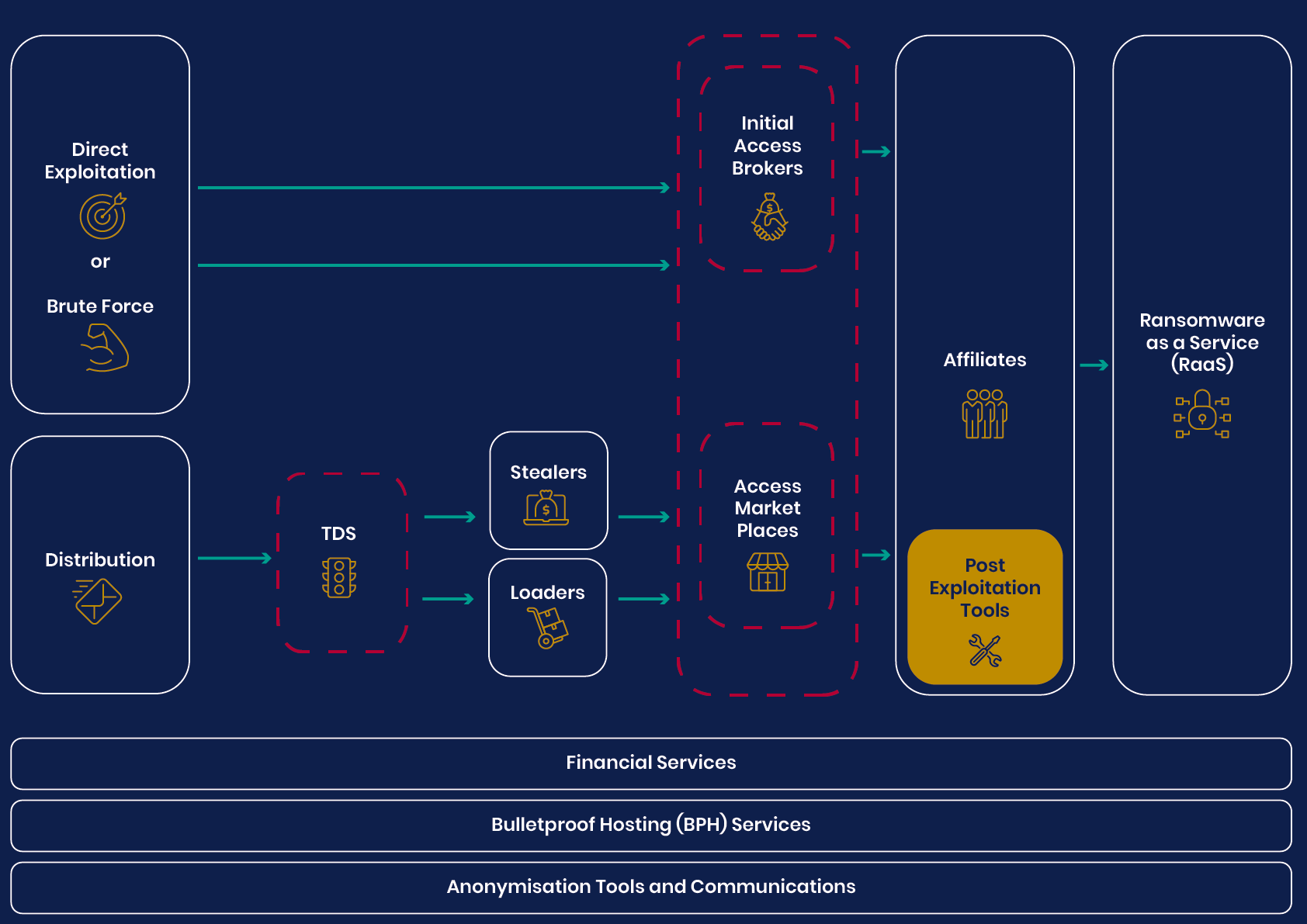
The UK’s National Cyber Security Center (NCSC) and National Crime Agency (NCA) have released a white paper on the rapidly evolving ecosystem of cybercrime, with a special emphasis on ransomware and extortion attacks. Here are the key takeaways:
High-profile attacks: Ransomware attacks have surged since the NCSC’s 2017 report, posing a significant threat to institutions worldwide. The malicious software encrypts files, preventing access to crucial data and often demanding a ransom in exchange for decryption. Recent high-profile attacks have crippled institutions, such as the Health Service Executive of Ireland and the Colonial Pipeline in Texas. In the UK, local councils’ critical care services and several educational institutions have been compromised.
Evolving threat landscape: The nature of ransomware attacks has evolved. Victims now grapple with the peril of sensitive data being exposed, leading to potential reputational damage. Moreover, there are concerns about repercussions from data protection authorities for failing to safeguard customer data. Some cyber criminals have opted for data theft and extortion without deploying ransomware, choosing their strategy based on the targeted institution’s nature and vulnerabilities.
Moral codes and complex supply chains: Certain criminal factions claim a ‘moral code,’ avoiding critical national infrastructure and healthcare services. Nevertheless, modern supply chains’ intricacy makes it almost impossible for them to ensure that their attacks don’t inadvertently affect these vital services.
The white paper underscores that ransomware and extortion attacks have become intricate business models, dependent on a complex supply chain. The paper cautions against exclusively focusing on specific ransomware strains, as most attacks result from poor cyber hygiene, rather than sophisticated techniques. Following the NCSC’s guidance could thwart most of these attacks.
The big picture: The rapidly shifting landscape indicates that cyber criminals will continue to exploit the most lucrative technologies or business models. The issue is deeper than any specific ransomware variant. Addressing individual variants is akin to treating disease symptoms. A comprehensive approach is needed to understand the vast ecosystem and target the root causes rather than playing a never-ending game of ‘whack-a-mole’ with the ransomware factions.
Sponsored byRadix

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byCSC

Sponsored byVerisign
