


|
||
|
||
Given the ubiquity of mobile phone usage, you’d think we’d all know by now how to tell legitimate from scammy text messages. Then again, cybercriminals are always on top of their game—learning how the latest technologies work and finding ways to abuse them.
Take phishing as an example. It has gone on to extend its reach far beyond users’ computers at home and in the office to the mini computers they carry no matter where they go—their mobile phones. It’s only to be expected, therefore, for smishing—Short Message Service (SMS)-based phishing—to gain popularity.
The Smishing Triad, discovered by Resecurity researchers, that plagued users all over Europe and Asia are now trailing their sights on U.S. citizens. They were most recently seen sending potential victims parcel delivery failure text messages supposedly from USPS. Users who click the embedded link and log in to the supposed USPS page are at risk of having their personal data stolen.
Resecurity published 27 indicators of compromise (IoCs) related to the ongoing campaign—two email addresses and 25 domains. The WhoisXML API researchers expanded this list through a DNS deep dive and found:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our in-depth investigation by taking a closer look at the IoCs.
A bulk WHOIS lookup for the 25 domains identified revealed that:
We began our IoC list expansion analysis with DNS lookups for the 25 domains. We found that only 10 of them had active IP resolutions. Collectively, they resolved to 19 unique IP addresses, two of which—104[.]21[.]29[.]74 and 91[.]195[.]240[.]123—were already being detected as malicious based on malware checks.
A bulk IP geolocation lookup for the 19 IP addresses revealed that 95% originated from the U.S. and were under the purview of Cloudflare, Inc. The remaining IoC, geolocated in Germany, was administered by SEDO GmbH.
To hunt for potentially connected domains, we ran reverse IP lookups for the 19 IP addresses and found that they all appeared to be shared hosts.
Further scrutiny of the 25 domains identified as IoCs allowed us to identify six common strings, namely:
According to our Domains & Subdomains Discovery searches, the strings appeared in 124 other domains, as much as 27% of which may have already figured in malicious campaigns. The artifacts containing the strings wangduoyu. and poczta-polska. could have already been weaponized in attacks targeting users in Asia and Poland, respectively. Poczta Polska is, after all, Poland’s state postal administration. Those containing variants of usps, meanwhile, could be used for U.S.-based attacks, with the attackers possibly impersonating the U.S. Postal Service.
As a final step to find other artifacts possibly connected to the U.S. attacks, we looked for domains containing usps. We found 2,395 domains registered between 1 August and 13 September 2023. None of them were publicly attributable to the U.S. Postal Service based on their registrant email addresses.
It’s also interesting to note that 595 of the usps-containing domains were already being detected by various malware engines as malicious. Of these, 101 remained accessible according to screenshot lookups although 15 malicious domains proved noteworthy since they mimicked not just the U.S. Postal Service’s domain name but also its content.
Here’s a side-by-side comparison of the official USPS website and a sample fake one.
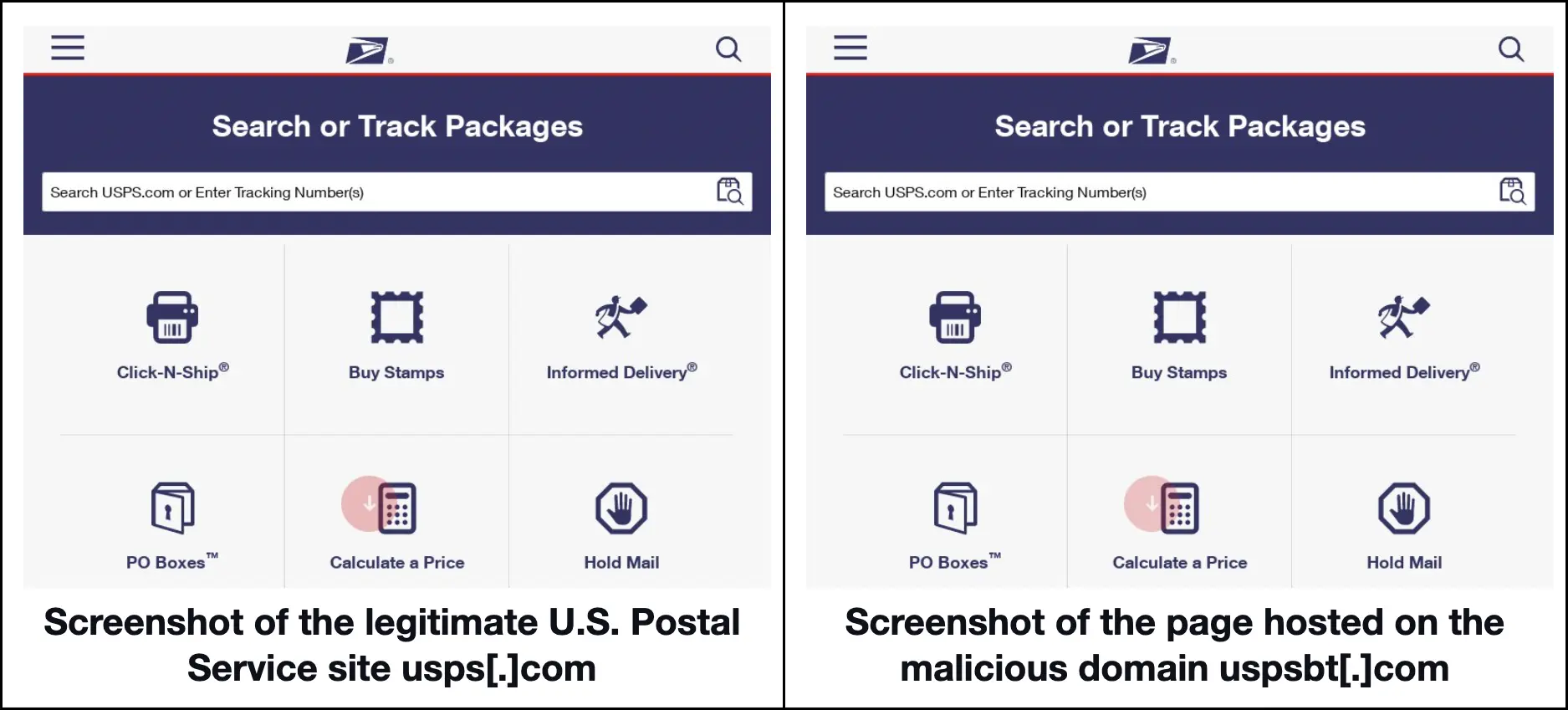
It’s also worth noting that 12 of the malicious domains hosting supposed USPS pages looked very similar. They all began with usps and one randomly chosen letter and used the .com TLD extension.
Our DNS deep dive into the Smishing Triad unveiled more than 2,500 potentially connected artifacts. Note, however, that the USPS look-alike domains and websites may not necessarily be part of the group’s infrastructure but when accessed could definitely put users at risk since none of them could be publicly attributed to the company.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byRadix

Sponsored byVerisign

Sponsored byCSC

Sponsored byWhoisXML API

Sponsored byDNIB.com
