


|
||
|
||
DNS abuse combined with redirection seems to be gaining popularity as a stealth mechanism. We’ve just seen Decoy Dog employ the same tactic. More recently, a still-unnamed JavaScript (JS) malware has been wreaking havoc among WordPress site owners by abusing Google Public DNS to redirect victims to tech support scam sites.
Sucuri published an in-depth analysis of the JS malware where it named 30 domains and five IP addresses as indicators of compromise (IoCs). Our research team then sought to find other related threat artifacts through an IoC expansion analysis. Our DNS deep dive uncovered:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our analysis by looking more closely at the IoCs that Sucuri already published.
First, we subjected the 30 domains identified as IoCs to a bulk WHOIS lookup that led to these discoveries:
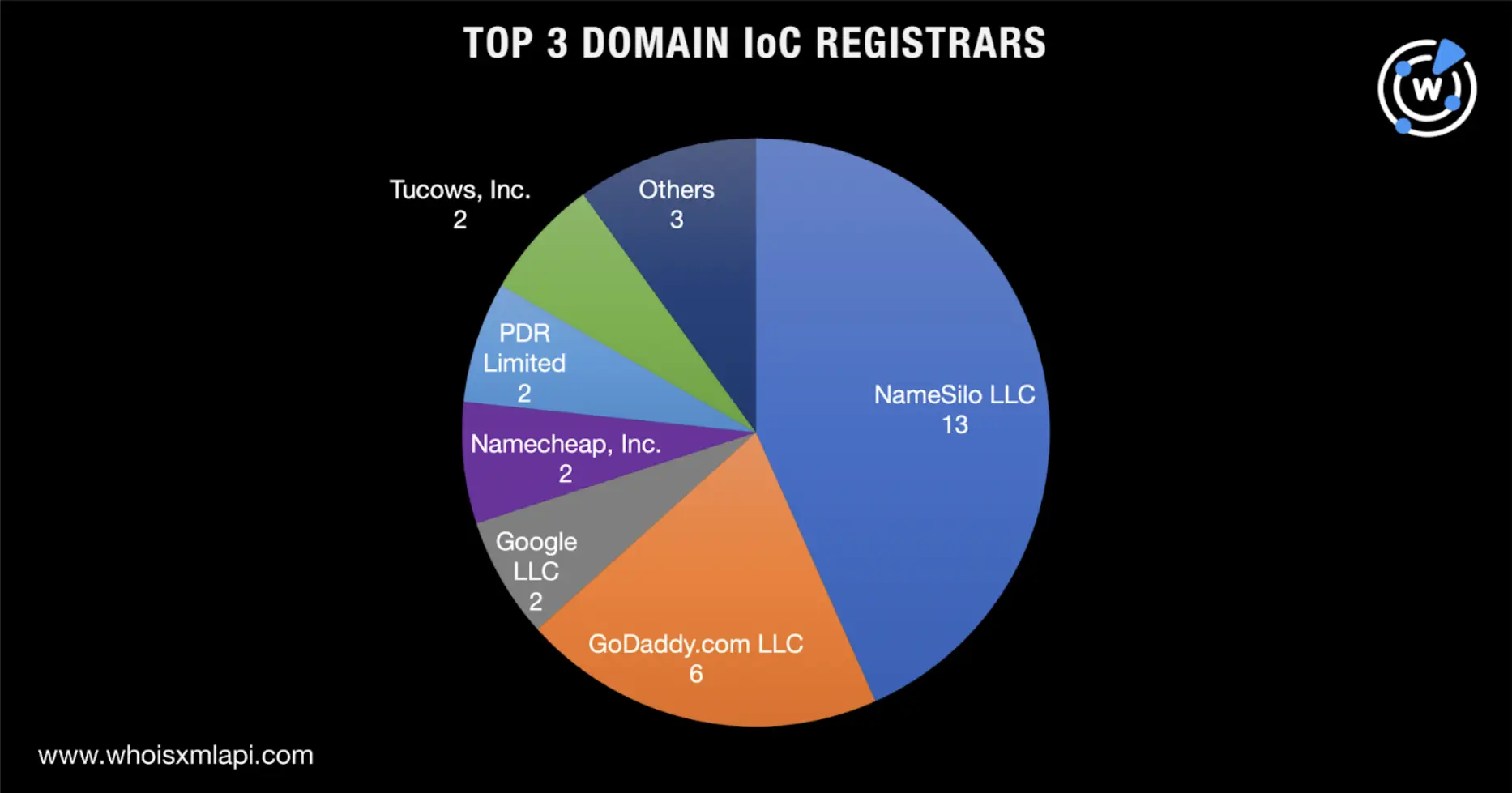
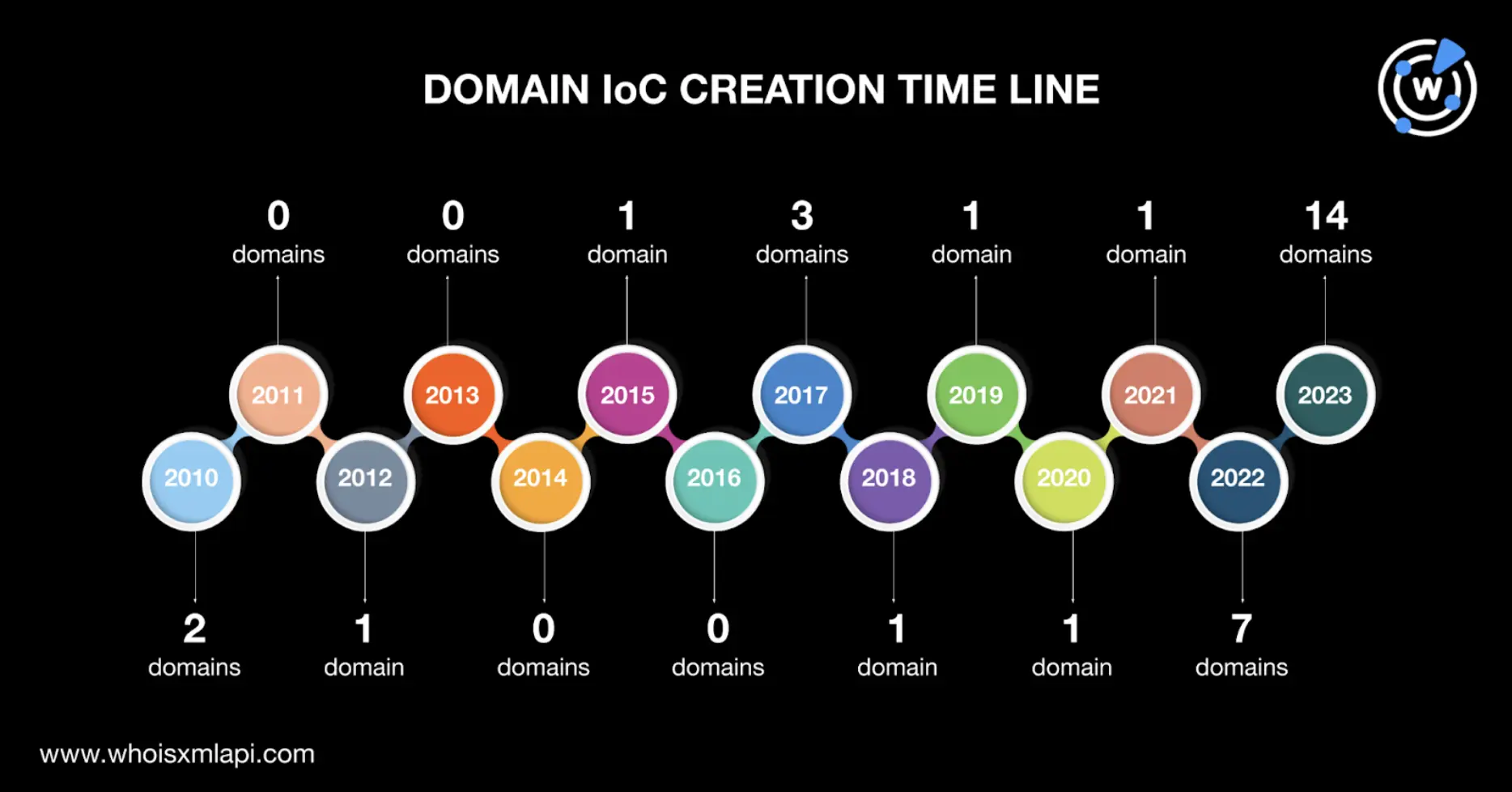
The IoCs were registered between 2010 and 2023. Further scrutiny revealed that a majority (14 domains) were created just this year. And since another seven IoCs were created in 2022, it’s possible that the threat actors favored using newly registered domains (NRDs) in their campaigns.
Next, we subjected the five IP addresses identified as IoCs to a bulk IP geolocation lookup that led to these findings:
Our bulk WHOIS lookup earlier also revealed that three of the domains identified as IoCs had public registrant email addresses. Through reverse WHOIS pivoting, we found that two of them were used to register two domains that weren’t part of Sucruri’s list. The first domain, agenciafleek[.]com led to an error page and shared IoC ojosclear[.]com’s registrant email address. The second, suffolktrackofficials[.]org, meanwhile, was unreachable at the time of writing but shared IoC look-alike suffolktrackofficials[.]com’s registrant email address.
Next, we performed DNS lookups for the 30 domains identified as IoCs and found two IP address resolutions not on the current IoC list. While both 165[.]232[.]94[.]190 and 192[.]124[.]180[.]195 originated from the Netherlands, they had different Internet service providers (ISPs). 165[.]232[.]94[.]190 was under DigitalOcean, LLC management while 192[.]124[.]180[.]195 fell under Teknology SA’s purview.
We then subjected the seven IP addresses (five IoCs and two newly discovered artifacts) to reverse IP lookups, which revealed that five of them were seemingly dedicated hosts. They were shared by 330 other domains that weren’t part of the existing IoC list. A bulk malware check showed that nearly half of them (157 to be exact) were classified as malicious.
As the last step, we used Domains & Subdomains Discovery to determine if other domain names containing some of the strings present in the 30 domains identified as IoCs were present in the DNS. We found that 11 strings in some of the IoCs also appeared in 101 other domain names. These strings were:
While none of the 101 string-connected domains have been dubbed malicious to date, some did bear other similarities with the IoCs, such as:
Our deep dive found hundreds of malicious domains that shared the IoCs’ dedicated IP hosts. As threat actors behind the JS malware intend to hide behind traffic redirection in the DNS, those breadcrumbs could help further study and understand the technique.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byDNIB.com

Sponsored byWhoisXML API

Sponsored byVerisign

Sponsored byCSC

Sponsored byVerisign
