


|
||
|
||
A phishing campaign is currently targeting Facebook business accounts with password-stealing malware. The attackers have been using a massive network of fake and compromised Facebook accounts to send out millions of Messenger phishing messages.
Dubbed a part of the MrTonyScam, the phishers typically cited copyright violations or requests for more information about business products. Victims who download the attached RAR or ZIP archive file trigger a malware dropper to fetch its payload from GitHub repositories that gets executed on the affected users’ systems. The malware then collects all the cookies and login data stored on victims’ web browsers, compiles them into a ZIP archive, and sends the archive to the attackers.
WhoisXML API researchers found a publicly available list of indicators of compromise (IoCs) related to the ongoing malicious campaign. We analyzed the digital infrastructure of 63 domains identified as IoCs and traced their DNS footprints that led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
Our analysis of the IoCs’ IP resolutions through a bulk IP geolocation lookup revealed that about 79% still resolved to 180 unique IP addresses. That means many of them have multiple resolutions, averaging 3—4 per domain. IP geolocation data pointed to Canada (51.5%) and the U.S. (48.5%) as their only locations and Cloudflare as their sole Internet service provider (ISP).
A bulk WHOIS lookup for the domains also revealed uniform WHOIS details. All of them were registered with NameSilo while PrivacyGuardian protected their WHOIS records. The domains all specified the U.S. as their registrant country.
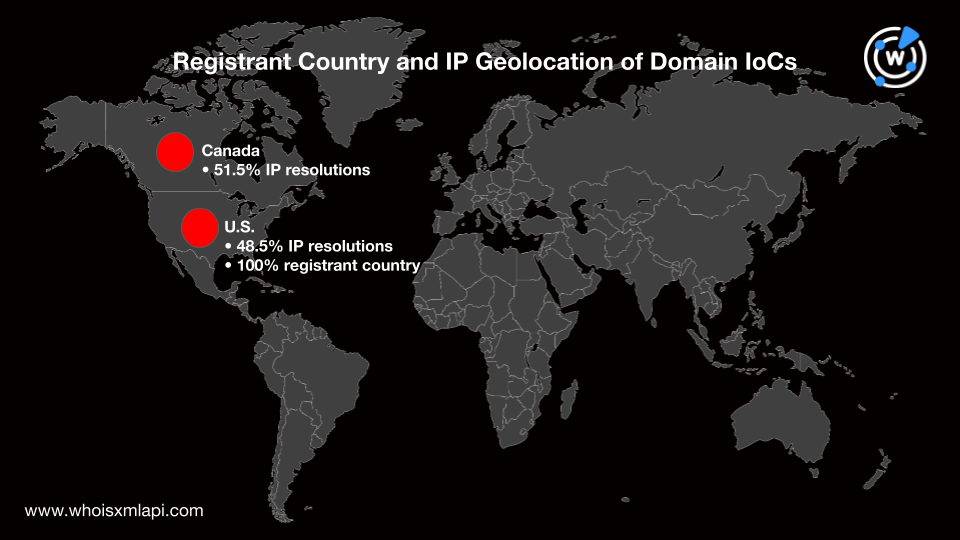
The glaring similarities among all of the domains suggest they could have been registered and controlled by the same entity. Alternatively, the domains’ registrar may have repossessed them after figuring in the Messenger phishing campaign.
While several IoCs have already been publicly named and possibly reported on various security platforms, the threat actors may have other domains in their arsenal just awaiting deployment. The IP-, email-, and string-connected domains we found and discussed in greater detail below could be considered potential artifacts of the Messenger phishing scam.
As a possible early threat detection effort, we examined the malicious domains’ historical WHOIS records, which led to the discovery of 73 publicly available registrant email addresses. Many of them were obtained from Gmail, Yahoo!, Naver, Live, and other commonly used email services.
We then ran reverse WHOIS searches for the email addresses. We focused on 15 email addresses that were used to register less than 50 domains each. The other addresses were used to register hundreds or even thousands of domains and may once have belonged to domain name investors. Despite the sample reduction, we still found 155 email-connected domains, only 15 of which had active resolutions.
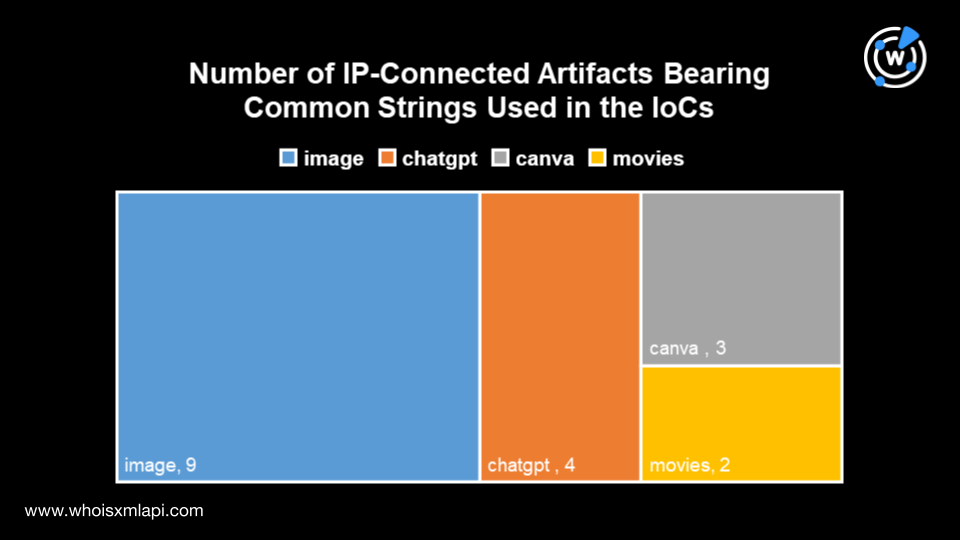
Next, we retrieved domains that contained text strings that repeatedly appeared among the IoCs. We used Domains & Subdomains Discovery to uncover domains that started with the strings:
We also looked for domains that:
Our searches yielded 924 domains added from 1 January to 18 September 2023. About 94% of them still have active resolutions. While these connected domains may not necessarily be related to the Messenger phishing campaign, it’s important to note that some of them have already been classified as malicious by a malware check, including movies-shows-more[.]com, which continued to host or redirect to this page:
The use of brand names like Canva, Office, and ChatGPT by the identified domains also raises suspicion.
We then traced the IoCs’ DNS footprints by performing reverse DNS searches to find other domains sharing their IP resolutions. We found that they were primarily hosted on shared infrastructures since each IP address hosted more than 300 domains. As such, they may not be part of malicious IP networks and instead are just public IP addresses that multiple domains share.
However, we discovered several IP-connected domains also containing strings that appeared in some of the IoCs.
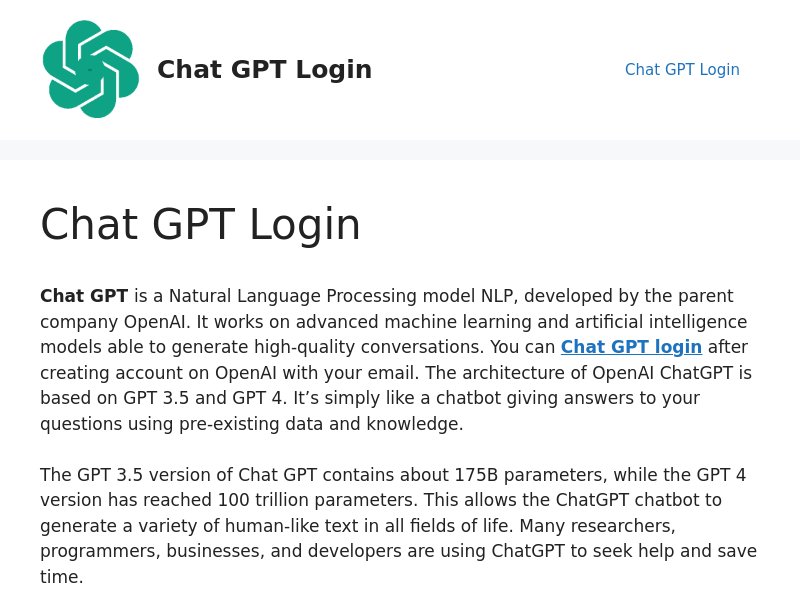
Some of these IP- and string-connected domains hosted suspicious content. For example, a screenshot of chatgptlogn[.]com shows that the domain hosted a page with several login links and contained the ChatGPT logo.
Our DNS deep dive into the recently reported Messenger phishing campaign allowed us to catch some suspicious and malicious properties related to known IoCs via WHOIS, DNS, and string usage. What started as an IoC expansion exercise led us to find other potential malicious campaigns likely targeting Canva and ChatGPT users and people browsing for movies online.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byRadix

Sponsored byIPv4.Global

Sponsored byCSC

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byWhoisXML API
