


|
||
|
||
Threat researcher Dancho Danchev recently discovered a phishing operation that seemed to be abusing .top domains for which he collated 89 email addresses that served as indicators of compromise (IoCs). To amass more information and other potentially connected web properties, the WhoisXML API research team took a DNS deep dive that led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
We began our analysis by looking closer into the 89 email addresses Danchev identified as IoCs and found that:
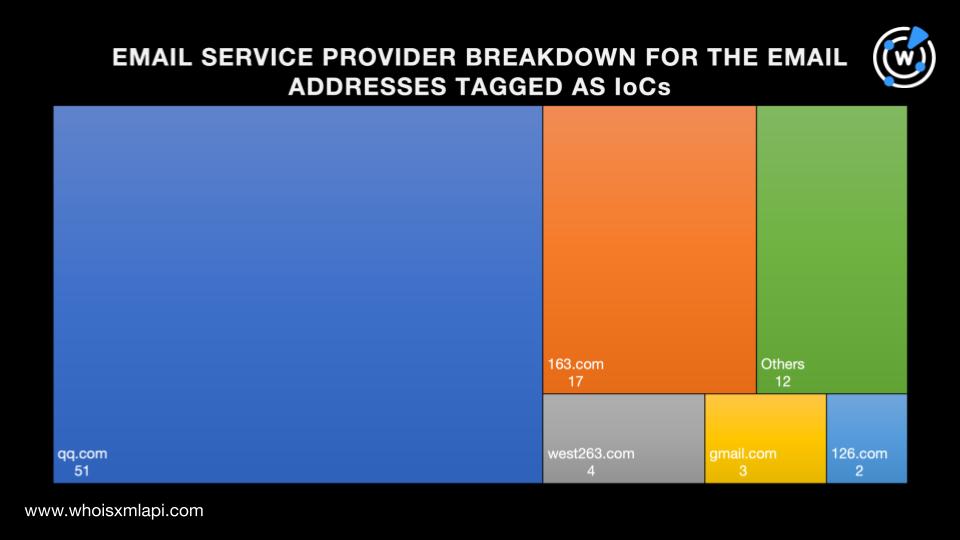
To begin our hunt for unreported possible connections, we first needed to limit the scope of this study.
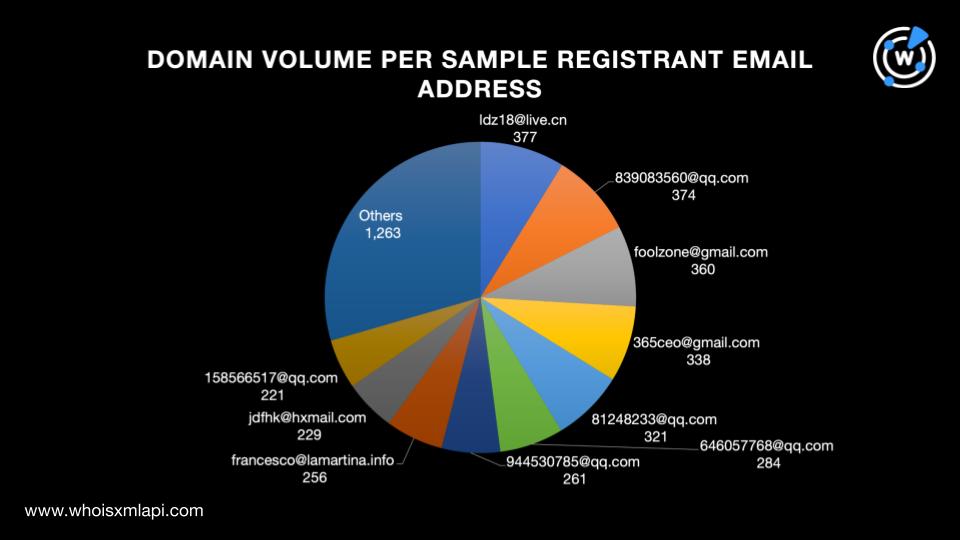
We ran reverse WHOIS searches on the 79 email addresses identified as IoCs. We then chose to focus only on those that served as registrant email addresses to 500 or fewer domains registered recently. That left us with a sample of 35 email addresses that were used to register 4,284 potentially connected domains in total. Take a look at the number of domains registered using each email address in the chart below.
Further scrutiny of the 4,284 domains showed that a majority of them, 2,237 to be exact, sported the .top top-level domain (TLD) extension as Danchev pointed out. The .wang (282), .xyz (268), .pub (261), .bid (236), .mobi (202), .xin (129), .com (116), .cn (109), and .gift (91) TLD extensions completed the top 10. The remaining 354 domains were spread across 27 other TLD extensions. The number of domains per TLD extension is shown in the chart below.
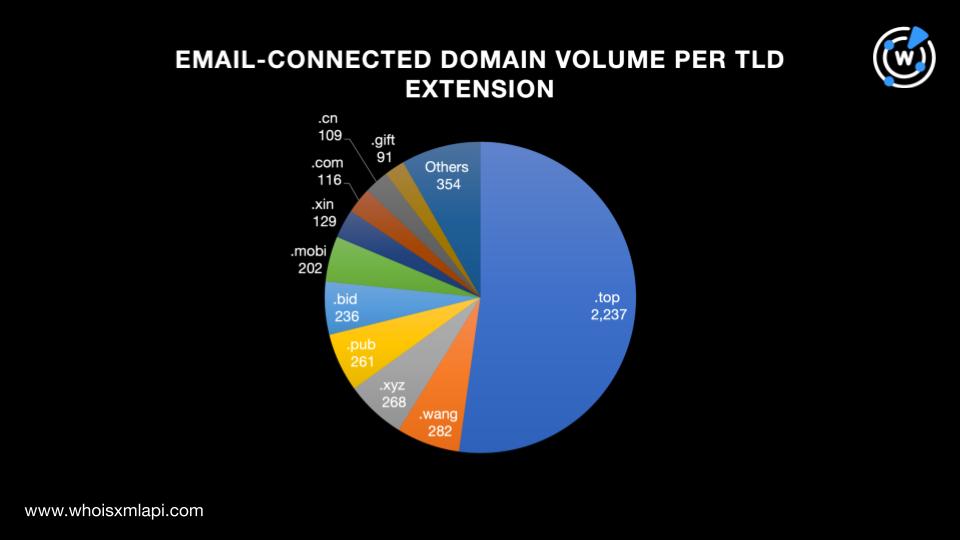
We can thus infer that the phishers mostly favored using domains under gTLD extensions, specifically .top, based on the top 10 list above. That, however, didn’t mean they didn’t weaponize domains sporting ccTLD extensions, as evidenced by the inclusion of .cn in the top 10, as well.
A bulk WHOIS lookup for the 4,284 email-connected domains revealed that:
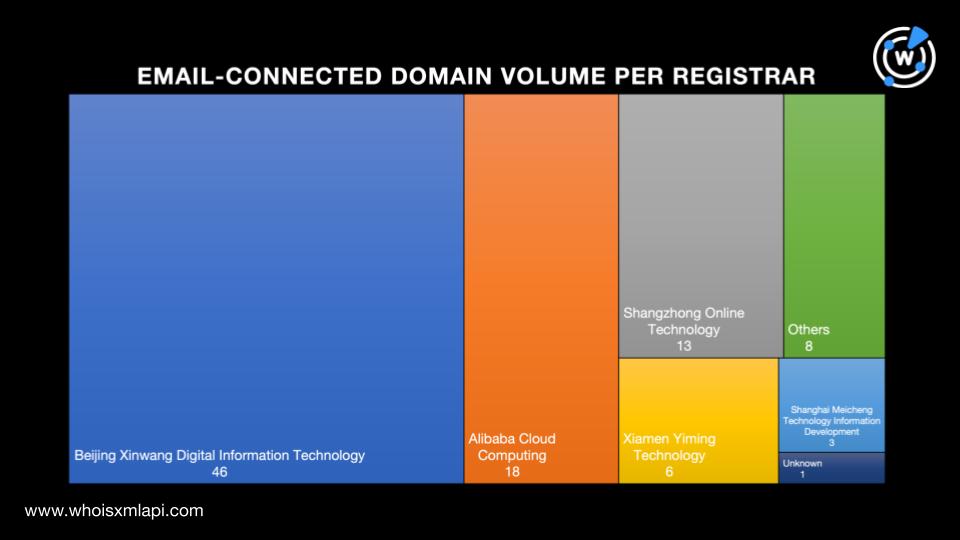
The highest number of email-connected domains with retrievable WHOIS records, 14 to be exact, were registered in 2021. One didn’t have a publicly viewable creation date. Take a look at the domain breakdown by creation period below.
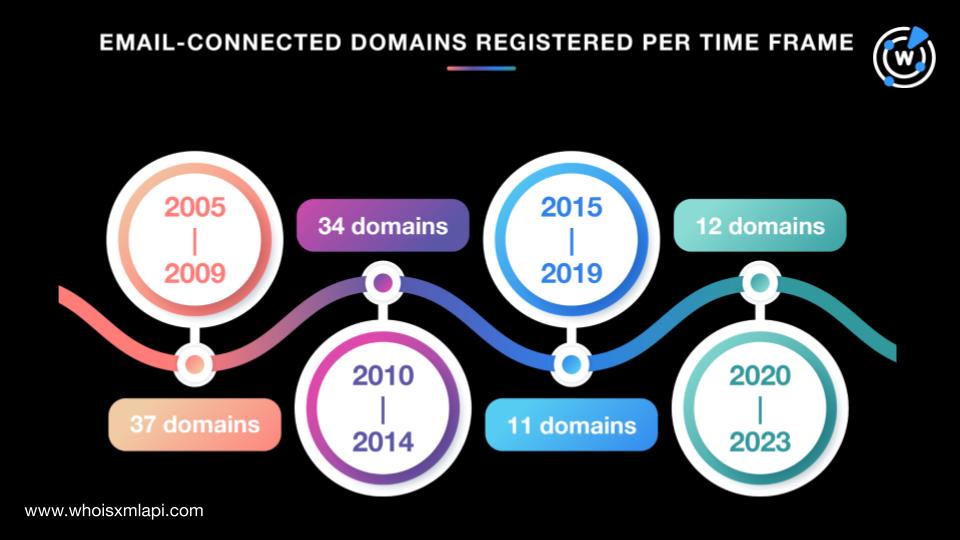
Only one domain—cnlegaldata[.]com—had a visible registrant country—the U.S.
Next, we subjected the 4,284 email-connected domains to DNS lookups, which revealed that:
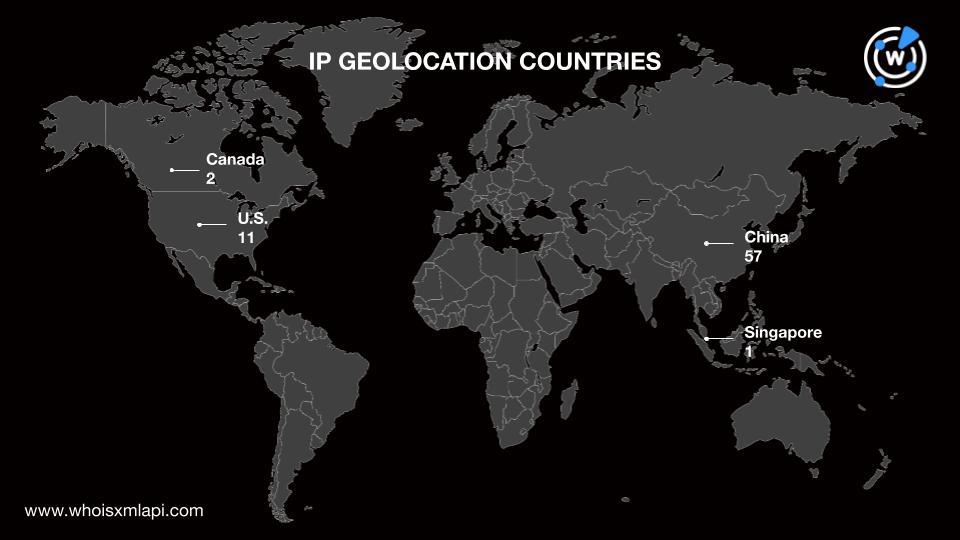
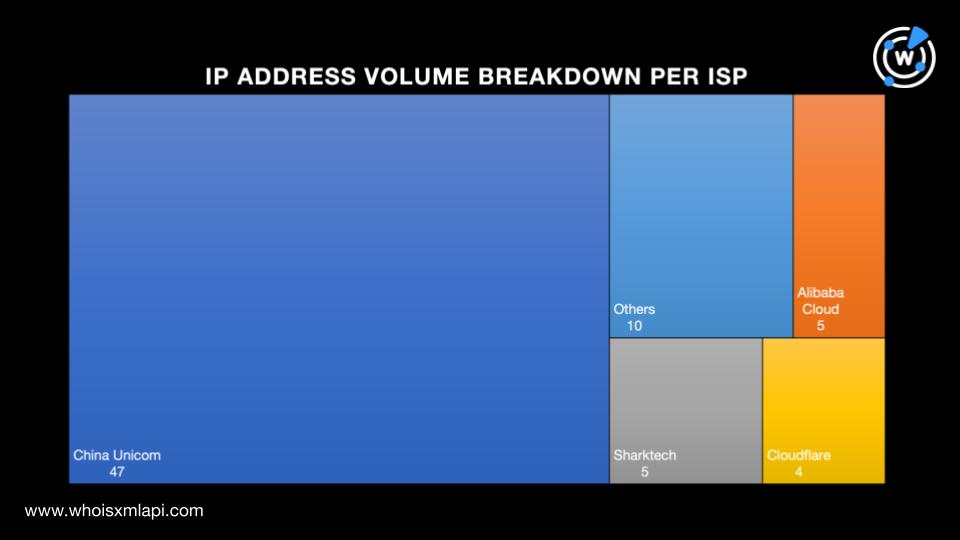
Additional open-source intelligence (OSINT) research on the IP addresses found that one—208[.]91[.]197[.]46—was reported on AbuseIPDB five times as of this writing.
As a final step, we ran reverse IP lookups for the 71 IP addresses in search of IP-connected domains and found that:
While none of the IP-connected domains were dubbed malicious, at least two may be suspicious. Asicskids[.]com and tomfordeyewear[.]com, which bear popular fashion brand names, couldn’t be publicly attributed to ASICS and Tom Ford, respectively, based on WHOIS record comparisons with the legitimate companies’ official domains.
We also noticed the appearance of the string bank in five of the IP-connected domains. While only three seem to be mimicking legitimate banks—grandbank[.]cn, nanjingbank[.]com[.]cn, and ruifengbank[.]com—all five could be weaponized for phishing.
Our DNS deep dive into the phishing campaign led to the discovery of 5,245 unreported potentially connected threat artifacts, a majority of which were .top domains.
If you wish to perform a similar investigation or learn more about the products used in this research, please don’t hesitate to contact us.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byRadix

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byCSC

Sponsored byIPv4.Global

Sponsored byWhoisXML API

Sponsored byVerisign
